
2024-9-27 21:0:21 Author: www.sentinelone.com(查看原文) 阅读量:5 收藏
The Good | Feds Indict Russian Money Launderer & Sanction Two Illegal Virtual Exchanges Linked to Ransomware Operations
The U.S. government doled out a heavy helping of sanctions this week in a coordinated effort against two illicit virtual currency exchanges and Sergey Sergeevich Ivanov, an alleged money launderer.
From the Treasury’s Financial Crimes Enforcement Network (FinCEN), a Russian exchange known as PM2BTC and associated launderer Ivanov were officially identified in connection with a network of illicit finances. At the same time, the Office of Foreign Assets Control (OFAC) sanctioned Ivanov and Cryptex, a second virtual currency exchange based in St. Vincent and the Grenadines but operated out of Russia. PM2BTC, Cryptex, and Ivanov are all linked to ransomware operations and other threat actors, initial access brokers, darknet vendors, and more.

PM2BTC has longstanding ties with Russia and Russian-affiliated financial institutions, many of which are also sanctioned. It provides convertible virtual currency (CVC)-to-ruble exchange services with no anti-money laundering or Know Your Customer (KYC) programs in place, allowing cybercriminals to process their ill-gotten funds and continue their activities. Cryptex was found to have processed $51.2 million in ransomware-derived funds and handled over $720 million in suspicious transactions tied to Russian cybercriminals.
Alongside FinCEN and OFAC, the Department of State has issued a $10 million reward for information leading to Ivanov’s arrest. The Russian national has reportedly facilitated hundreds of millions in virtual transactions, using various payment processors to do business with malicious parties for roughly two decades.
All of these recent actions taken were done in partnership with Operation Endgame, a multinational cyber operation dismantling financial enablers of organized crime syndicates. As Russia continues to act as a safe harbor for such criminals and show ongoing support for high-profile actors like Cyber Army of Russia Reborn and LockBit group, efforts like Operation Endgame will prove critical in cutting off threat actor funding at the source.
The Bad | Mallox Ransomware Affiliate Rebrands Kryptina to Target Linux
An adapted version of Kryptina ransomware has been spotted in use by an affiliate of Mallox ransomware operation, TargetCompany. Based on new research from SentinelLabs, this development calls to attention ever-evolving tactics from players within the ransomware ecosystem.
Launched in late 2023 as a low-cost ransomware-as-a-service (RaaS) platform for Linux, Kryptina initially failed to gain traction on dark markets. However, in February 2024, the platform’s alleged administrator, ‘Corlys’, leaked its source code for free on hacking forums, leading to various ransomware actors, including Mallox affiliates, to repurpose Kryptina’s code. Just three months after this, another Mallox affiliate leaked staging server data, revealing that their Linux ransomware was based on a modified version of Kryptina.
This new version, dubbed ‘Mallox Linux 1.0’ retains Kryptina’s core source code, encryption mechanisms (AES-256-CBC), and command line functions. The affiliate only changed the appearance, removed Kryptina’s branding, and simplified documentation. In addition to the Mallox Linux 1.0 variant, SentinelLabs discovered various tools on the threat actor’s server, including a legitimate Kaspersky password reset tool, an exploit for Windows privilege escalation (CVE-2024-21338), PowerShell scripts for privilege escalation, Java-based payload droppers, disk images containing Mallox payloads, and data folders linked to 14 potential victims.
Described as having a rags-to-riches story, Mallox went from being a free giveaway in public forums to being featured in active attacks on SMBs and enterprises within just a few months. While Kryptina is still considered an outlier platform, experts warn that stories like these are an indication that ransomware actors will continue to cross-pollinate toolsets and codebases in order to commoditize and level up.
The Ugly | North Korean Adversary Kimsuky Deploys Two New Malware Strains in Targeted Attacks
North Korean-tied threat group Kimsuky (aka Sparkling Pisces, APT43, or ARCHIPELAGO) has debuted two new malware strains dubbed ‘KLogEXE’ and ‘FPSpy’ in their latest campaigns. While Kimsuky threat actors have been around since 2012, cyber researchers have uncovered their recent evolution, including new capabilities along with the novel malware.
Given how notorious Kimsuky is for social engineering and spoofed emails, KLogEXE and FPSpy are portable executables delivered through highly targeted spear-phishing emails designed to look like legitimate communications. The victims are tricked into downloading and extracting malicious ZIP files, which then initiate the infection chain that deploys KLogEXE and FPSpy.
KLogEXE, written in C++, is a variant of a previously documented PowerShell-based keylogger called ‘InfoKey’. It can monitor running applications, record keystrokes, and capture mouse clicks. Alternatively, FPSpy is a variant of malware disclosed in 2022, and has more extensive capabilities, including system reconnaissance, command execution, and further payload delivery. It can enumerate files, drives, and folders on compromised devices. Researchers noted similarities in the source code of both strains, leading to the idea of a common author.
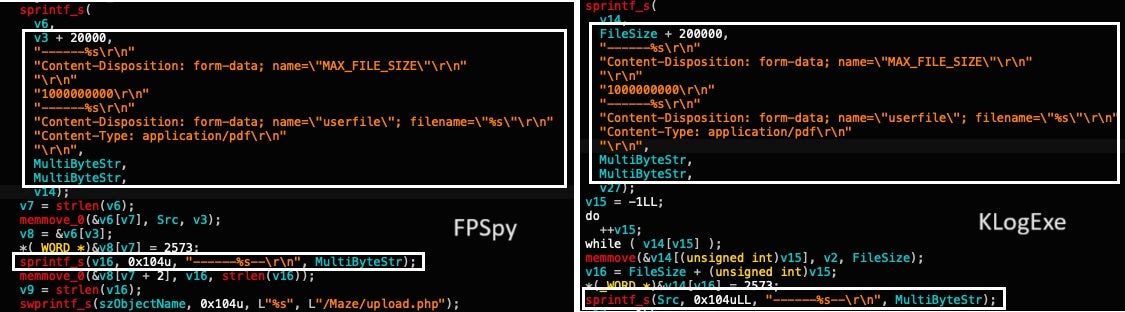
Though Kimsuky’s primary targets in these recent campaigns are mostly contained within Japanese and South Korean organizations, its attacks remain extremely targeted rather than widespread, zeroing in on specific industries and regions. Use of both KLogEXE and FPSpy only highlight the group’s continuous evolution and demonstrates an ongoing effort to enhance its malware arsenal and expand its operational reach, posing a persistent threat to select targets in Asia.
如有侵权请联系:admin#unsafe.sh