Whether you manage a gaming blog, an e-commerce platform, or an enterprise-level website you probably want to be able to detect infections when they occur. A hacked website can lead to financial loss, disruption of business operations, and the exposure of confidential information. The key is acting fast once you discover possible compromise.
But how can you tell if your website has been hacked?
In this post, we’ll explore the most common causes of infection, how to monitor your site to avoid bad actors from accessing your website, and how to restore its security and functionality after a hack.
Key Indicators That Your Website Is Hacked
There are several signs that your website may be compromised, some of which might seem minor at first. However, these signs can become serious issues if left unchecked. Let’s break down the most common indicators:
1. Unexplained Traffic Drops
One sign of a compromised website is a sudden drop in organic traffic. This can happen when search engines detect security issues on your website and either deindex or blacklist your website. SEO spam infections are the most common cause of this, targeting explicit keywords that ultimately poison your ranking.
Here are three of the most common and damaging types of malicious injections that hackers use to compromise a website’s traffic:
- SQL Injection: SQL injections (SQLi) can cause severe issues such as hackers obtaining full access control and leaking sensitive information from site users. These can occur through the web page or application input. If a web application isn’t validating its values received from a web form, cookie, input parameter, etc., before passing them via SQL queries, it’s executed on a database server. Without proper input validation, a hacker can manipulate the input so data is interpreted as code, rather than as data.
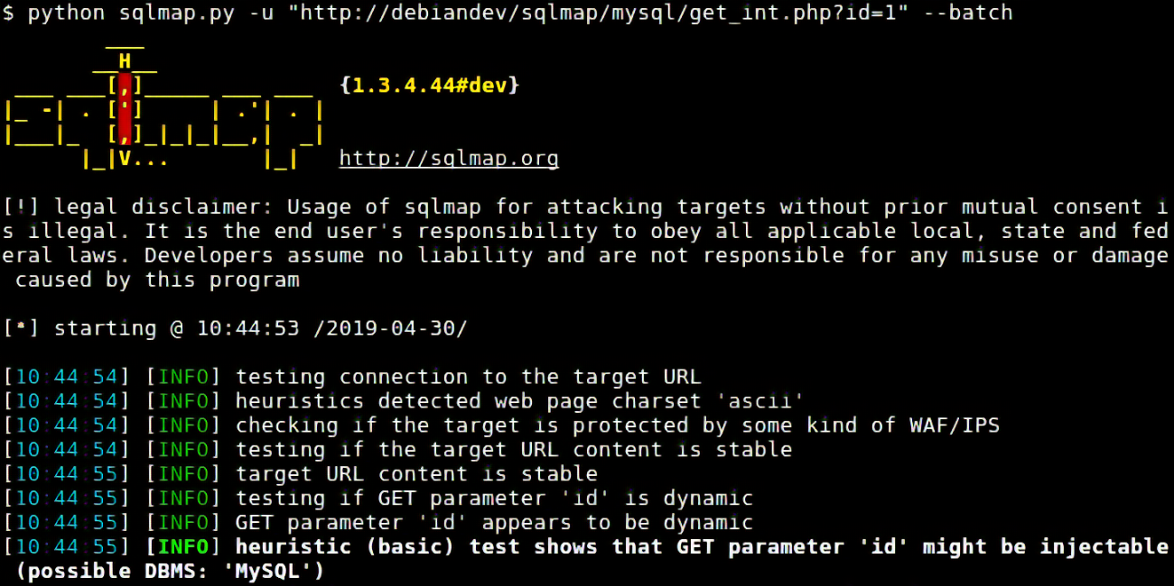
These injections can be detected with tools such as SiteCheck, SQLmap, Havij, or jSQL. Tools such as SQLmap are also handy in being able to detect possible intrusion points, helping prevent an injection before it occurs. Hackers exploit vulnerabilities in your website’s SQL database to inject malicious code.
- Backdoor Installation: Once hackers gain access, they plant backdoors in your website’s code, providing continuous access to inject malicious scripts and opening the door to further attacks.
- Admin Panel Compromise: These are one of the most common attacks everyday WordPress admins face. By default, there are inherent risks like a lack of 2FA, the login page being widely accessible, and having no limit on failed login attempts. Consider incorporating these security measures, along with setting a strong password.
2. Unexpected Redirects or Pop-ups
If users report being redirected to unfamiliar websites or encountering unexpected pop-ups, this is a clear sign of a compromised site. This usually occurs when malicious code is injected into your website, leading users to harmful sites or displaying unwanted ads. These redirects are often used in phishing attacks to steal sensitive information from your users.
Here are three common methods hackers use to execute redirects or pop-up attacks:
- Malicious iFrame Injections: Hackers embed malicious iFrames into your website’s code, which secretly load harmful websites or phishing pages without the user’s knowledge.
- Malvertising: Attackers inject malicious ads that appear legitimate but are designed to redirect users to harmful sites or trigger unwanted pop-ups. These ads can be especially dangerous on high-traffic websites.
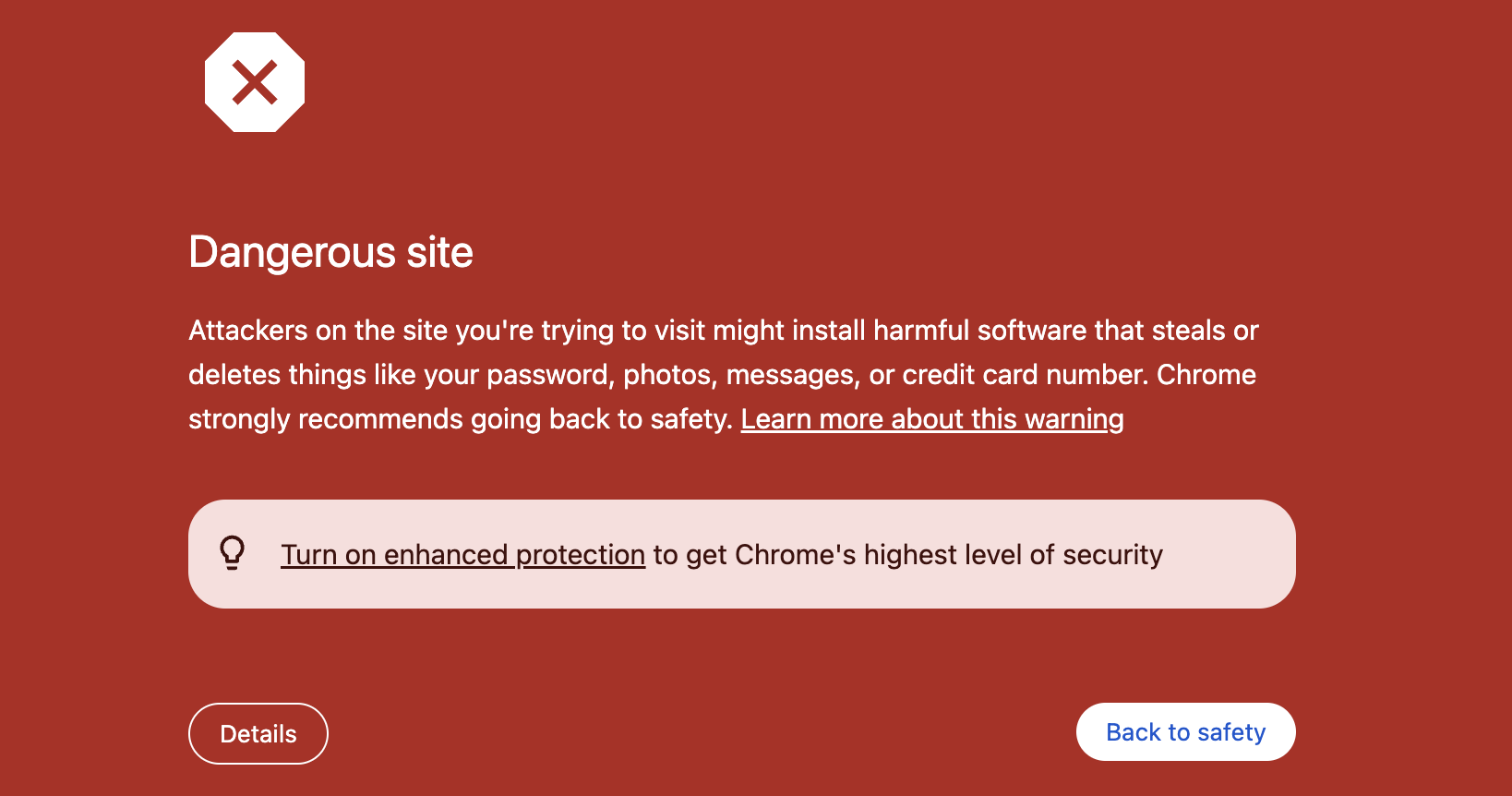
3. Browser and Antivirus Warnings
One of the clearest signs that your site is under attack is when browsers like Chrome or antivirus programs display security warnings. These warnings indicate that your site has been flagged as harmful or compromised. Ignoring these warnings can lead to significant traffic and revenue losses, as users will avoid visiting your site.
For example, the following warning is what an Avast AV user would see in the event that they attempt to visit a site that is injected with malware from a blocked domain:
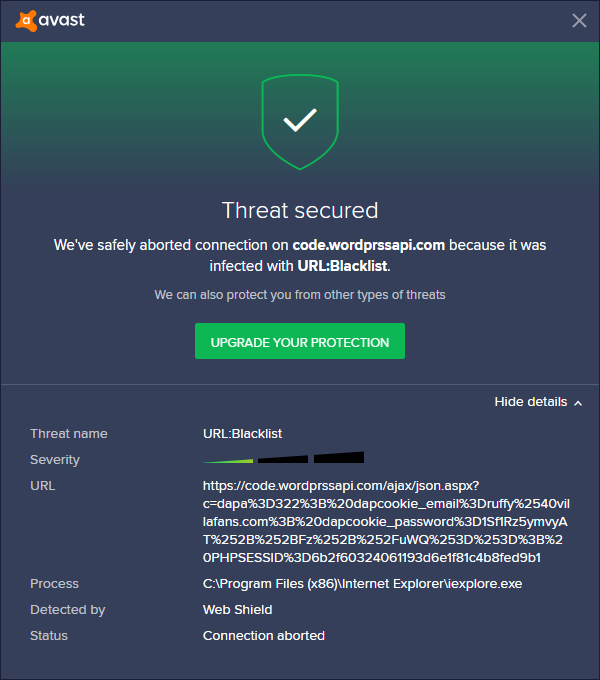
Here are the most common reasons your site may trigger Google Safe Browsing warnings:
- Phishing Content: If your site has been compromised by phishing attacks, it may host fake login pages or forms designed to steal user credentials, leading browsers to flag your site as unsafe.

- Malware Distribution: If your site is spreading malware—whether through downloads or malicious code injection—it will be blacklisted by search engines and trigger security warnings.

- SSL Certificate Issues: Expired or improperly configured SSL certificates can also result in browser warnings, as they indicate a lack of secure data transmission, increasing the risk of hacking.

If you’d like to see a preview of each warning, go to chrome://interstitials/ in your Chrome browser to see a full list of warning interstitials for your specific version.
4. Unapproved Changes to Your Website
Bad actors can alter your site’s content, inject malicious code, or create new admin users. If you notice blog posts, products, or pages that you or your team did not create, your website has likely been breached. Regularly reviewing your site’s CMS for unauthorized changes can help you catch these signs early.
Here are three common ways hackers make unapproved changes to compromised websites:
- Admin Account Creation: Hackers can create new admin accounts to gain full access to your site. This allows them to make changes to content, add malware, or even lock you out of your own site.
- Content Injection: Malicious actors may inject spammy content, such as fake product listings, blog posts, or external links, to promote phishing schemes or generate ad revenue.
- Defacement Attacks: In defacement attacks, hackers modify the visual appearance of your site, replacing it with propaganda or offensive content. This is often done to damage a brand’s reputation.
5. Account Suspensions or Web Host Notifications
If your web host sends warnings or suspends your account, this is a serious red flag. Hosting providers monitor their networks for abnormal activity, so it’s important to act on these notifications quickly to prevent further damage.
Common reasons hosting providers may suspend your account due to hacking:
- Excessive Resource Usage: A compromised site may use excessive server resources due to bot traffic or malware activity, prompting your host to suspend your account.
- Hosting Policy Violations: If your site is found hosting malicious content, such as malware or phishing pages, your hosting provider may suspend your account to protect their other customers.
How Sucuri Helps Protect Your Website
To further protect your website from security risks, Sucuri offers a comprehensive suite of tools designed to keep your site secure. Here’s how Sucuri can safeguard your website from the most common threats:
Website Scanning
Incorporating the use of website scanners to monitor both the front and back end is a security precaution every site owner should take. Front-end scanners are like a surveillance system monitoring the perimeter of your home. Server-side scanners, on the other hand, have perspective of the entire house and its contents, allowing them to identify what’s being moved around more efficiently.
For front-end scans, Sucuri offers a free remote scanner, as well as a plugin for WordPress sites. These scans will be able to determine if any known malicious content is displaying on the website. Paid plans have the option of enabling a back end scanner. Check out our configuration guide to learn how to set up our server-side scanning. This should remain actively scanning every 24 hours on the back-end with low resource usage, monitoring for changes to your site files.
Here’s an example of what the SiteCheck external scanner results will look like when injected malware is detected:
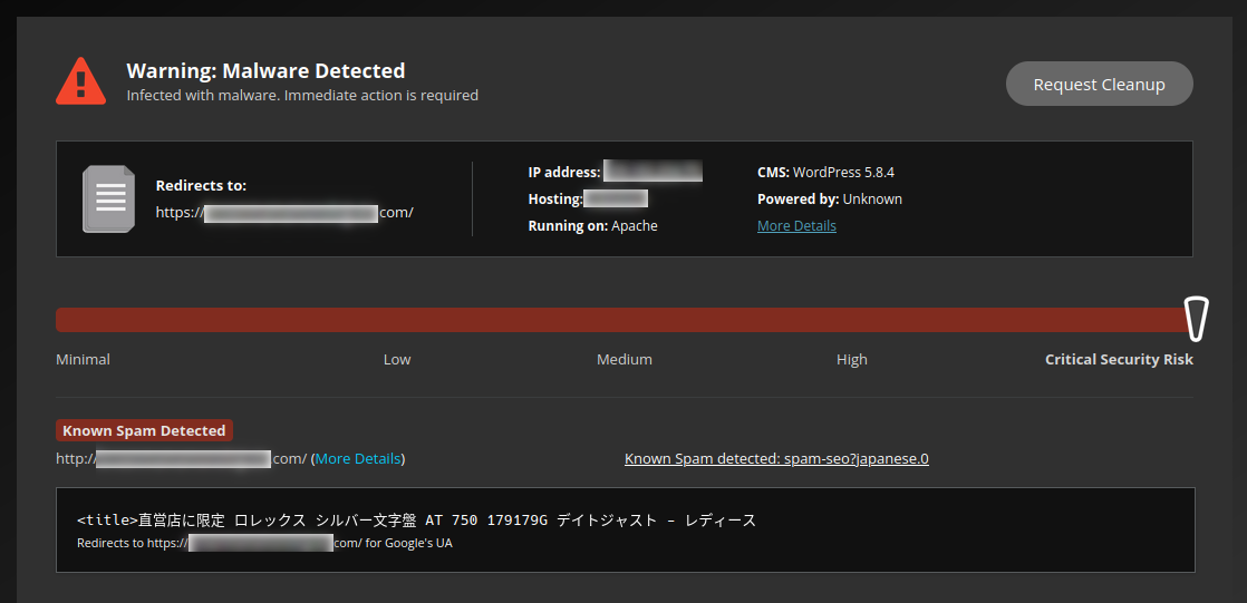
And via server-side scanning:
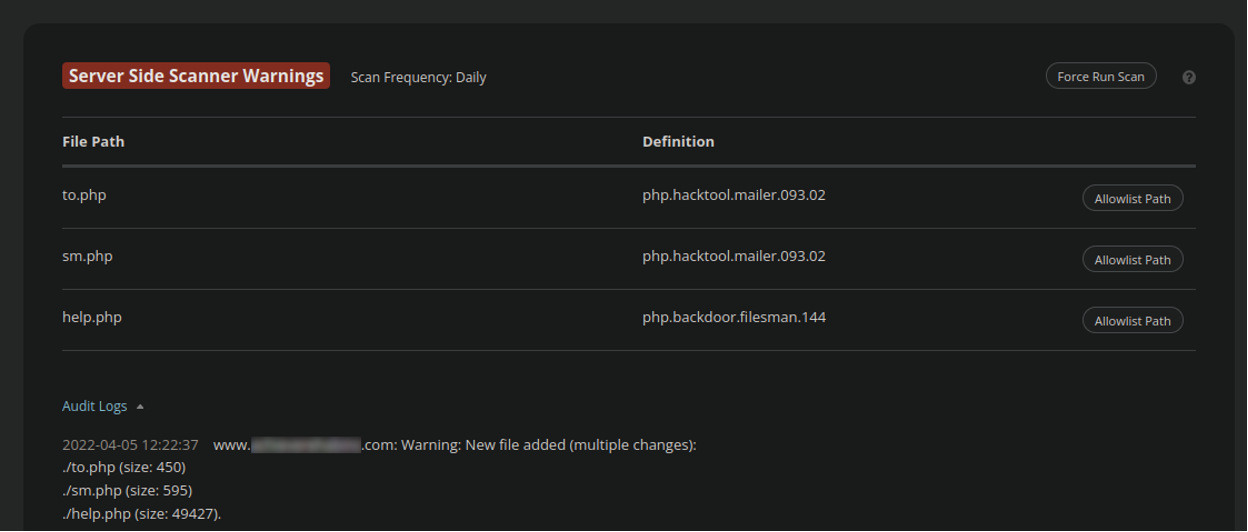
Malware Detection and Removal
Sucuri provides malware detection and removal as a core component of our website antivirus product line. Our remediation and research teams work tirelessly to identify new malware threats, samples, and campaigns to stay on top of the latest threats. Beyond that, we’re constantly monitoring to identify and virtually patch vulnerabilities with our website firewall as soon as possible, minimizing the risk of downtime and further damage to your site.
Cloud-Based Web Application Firewall (WAF)
Sucuri’s WAF is a crucial layer of defense against attacks like SQL injections, cross-site scripting, and DDoS. Since it operates in the cloud, the WAF doesn’t impact your site’s performance while providing real-time protection.
It includes virtual patching and hardening to safeguard your site even when security patches cannot be immediately applied. The WAF helps block DDoS attacks through a global Anycast network and an intrusion prevention system, ensuring minimal downtime and optimal performance. Sensitive pages can be further protected with features such as CAPTCHA, two-factor authentication (2FA), or IP allowlisting, which restrict access to authorized users. Application profiling and signature detection are employed to analyze traffic and block malicious requests that do not align with your web application’s profile.
24/7 Security Monitoring and Support
Sucuri provides expert support available to chat 24/7, ensuring that any issues are resolved quickly to minimize downtime and protect your business.
Best Practices for Maintaining Website Security
While Sucuri offers robust protection, website owners should still follow these best practices to enhance their security and practice defence-in-depth:
- Keep Your Software Updated: Always keep your CMS, plugins, and other software up to date. Outdated software can have vulnerabilities that hackers can exploit.
- Use Strong Passwords and Enable Two-Factor Authentication (2FA): Weak passwords are an easy target for hackers. Using strong passwords and enabling 2FA adds an extra layer of protection.
- Regularly Backup Your Website: Ensure you have frequent backups of your website. In the event of a breach, restoring from a recent backup can minimize data loss and downtime.
For more information and steps to secure a site that has already been compromised, refer to our definitive guide on how to secure your website.
With Sucuri’s comprehensive platform and team of experts, you can further protect your website from malware, DDoS attacks, and other threats, ensuring your online presence remains secure.
如有侵权请联系:admin#unsafe.sh