

It takes time to understand the pros and cons of each API security tool, but don't worry—we’ve done the work for you!
Salt Security has made a massive investment in its PR, heavily relying on AI buzzwords and partnerships with well-established organizations like AWS. They have been a well-known market player for years. However, as with Noname, frustration among security professionals has been mounting—whether due to the months it takes to run a POC or because the tool's findings are not actionable.
How can Escape create a better API security solution? We’ll let you decide if we’re better by comparing time-to-value. In this article, we’ll explain why and what makes us different from Salt Security.
When it comes to API discovery and security, choosing the right tool can significantly impact your organization's ability to protect its sensitive data and ensure compliance.
Dive right in!
Below you’ll find an in-depth comparison between Escape and Salt Security across the entire API security workflow – from API discovery to remediation. We focused on key differences between those two tools. If you want to get a quick recap and an infographic that you can download and share with others, jump to the last section.
As Salt Security doesn't have publically accessible documentation, we've built this comparison based on the following sources:
- Salt Security's official website & product datasheets
- Salt Security's publically accessible demos on YouTube
- Feedback from security professionals
- Feedback from an independent industry analyst
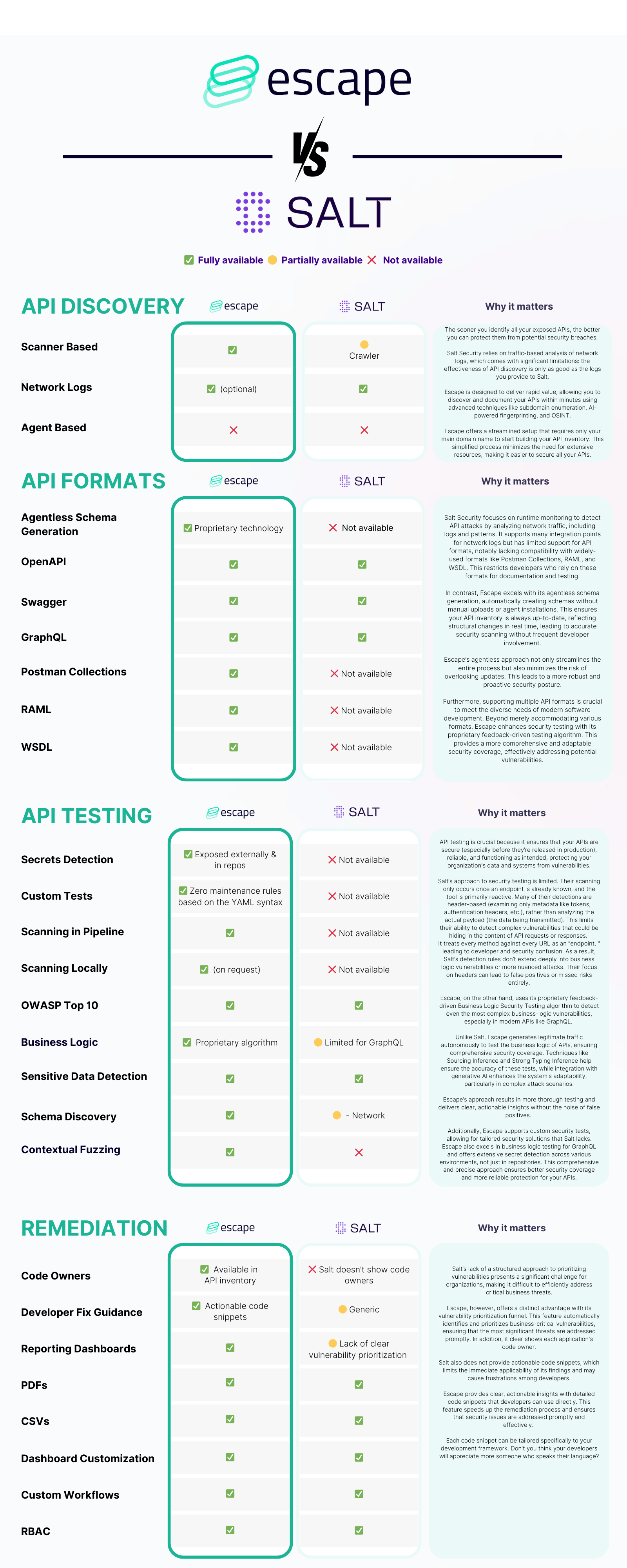
API Discovery
You can't secure what you can't see, so the faster you get to see what are the APIs exposed on the internet, the more you reduce the risk of API security breaches.
Salt Security relies heavily on traffic-based analysis for API discovery. This method examines network logs to identify APIs, which means it can only detect APIs that are already part of your network traffic. This approach can miss dormant APIs or those not frequently accessed, for example, located outside of API gateways, WAFs or proxies, leading to incomplete visibility.
However, Salt Security's clear benefit is its many integration points for network logs. They take logs from wherever you can give it to them, tag those logs with metadata about the traffic they’re seeing, and then discard the real payloads while relying on “AI” for detection. Due to not wanting to send them all your data, they can never really test payloads.
This presents them with some difficult limitations: the discovery is only as good as the logs you provide to Salt.
Unfortunately, Salt Security doesn't provide a step-by-step process of their API discovery setup (contrary to other traffic-based solutions, which are more transparent about different integration steps), so we can't provide a detailed overview here.
However, for AWS deployments, Salt Security states on its website tha they get a copy of your API traffic through AWS and 3rd party service integrations, then send API metadata into the Salt Platform. Salt mentions that its "fully automated process makes it quick to set up VPC Traffic Mirroring and enables advanced protection for your APIs", but we can't access docs to provide you an overview of the required steps.

Keep in mind that traffic mirroring is expensive, basically doubling your logging costs. According to the AWS website (Network Analysis tab), it’s $0.015 per ENI per hour, so if you had 1,000 instances with one ENI it would be $360/day.
On the other side, Escape is built to help you get the value out of it in the shortest time possible and without increasing costs. It allows you to discover your APIs within a matter of minutes. Escape uses a sophisticated combination of subdomain enumeration, AI-powered fingerprinting, and OSINT techniques to identify and inventory APIs. This ensures that all APIs, including those not actively in use, are discovered and documented.
“Our top priority was to achieve complete visibility and conduct detailed, valuable analysis. That’s exactly what the product delivers.” – Claude-Alain Sabatier, Director of IT Governance and Security, French Footbal Federation
With Escape, to get started all you need is to put in your main domain name, so you can build inventory without any intervention from the development team, which is not necessarily the case when you need to deploy traffic-based API discovery tool. Simplified deployment processes minimize the need for specialized knowledge and extensive internal resources.
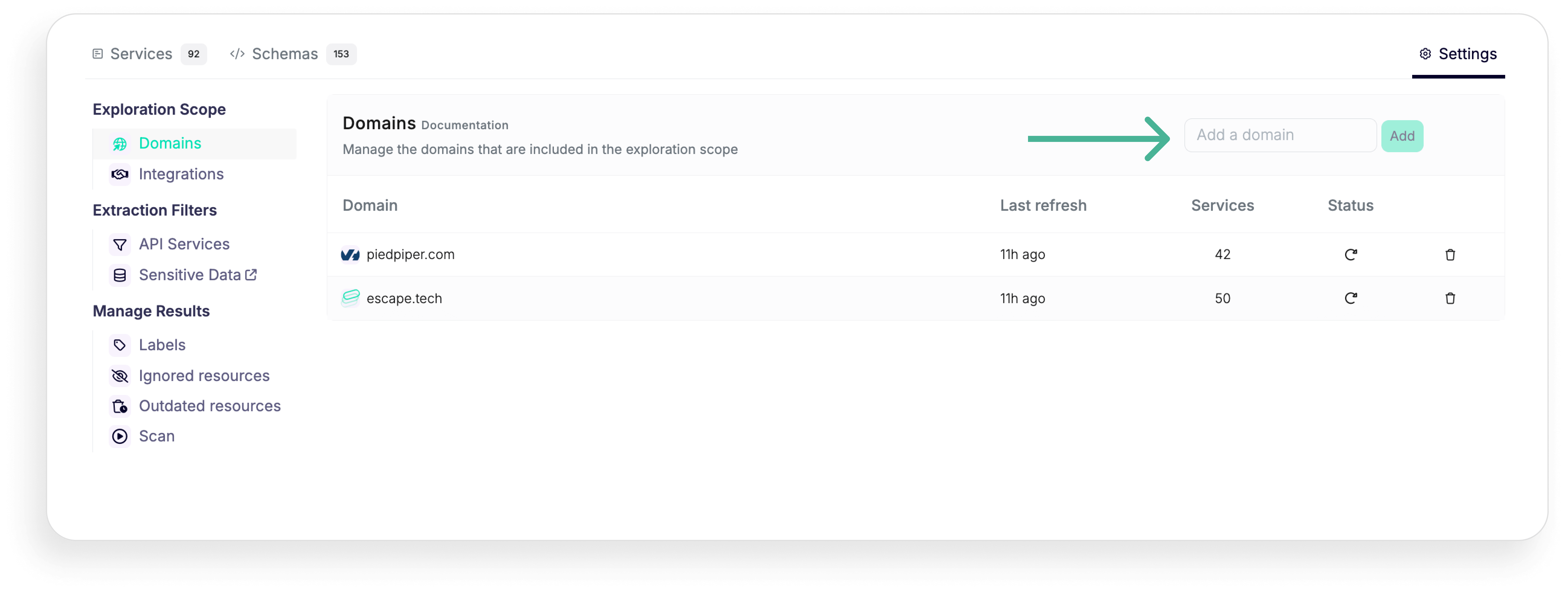
Once you've discovered all your exposed APIs, you can enrich the data discovered and classified in API inventory by connecting with your developer tools like Postman, GitHub, and GitLab, cloud platforms like AWS and Azure and gateways like Apigee, Axway, Kong Gateway and Kong Connect and Mulesoft. To scan internal APIs behind your organization's firewall or VPN, you can connect Escape's repeater proxy.
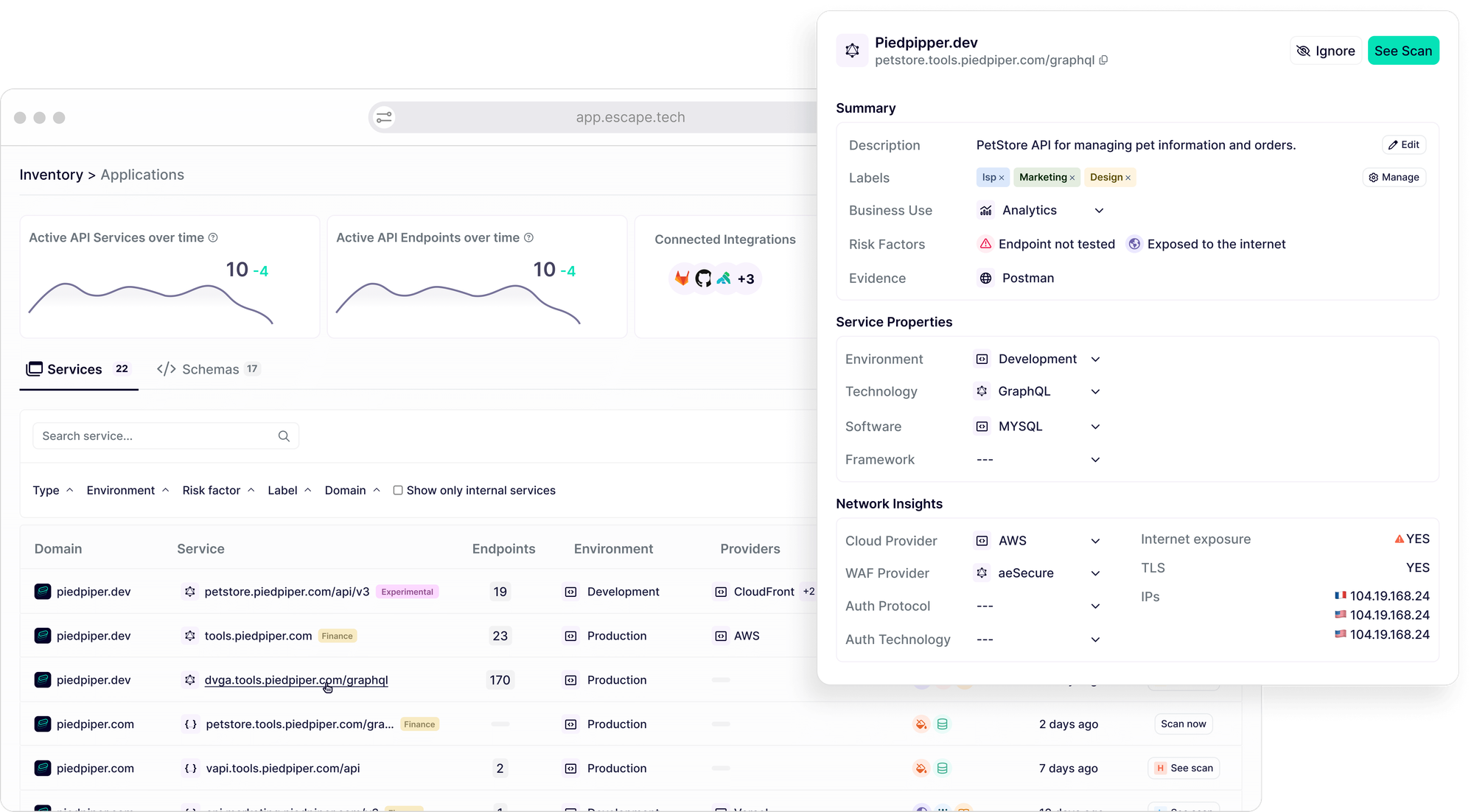
Despite making it easy to discover all APIs, Escape doesn't fall short in the depth of the information it uncovers. You can see it for yourself 👇
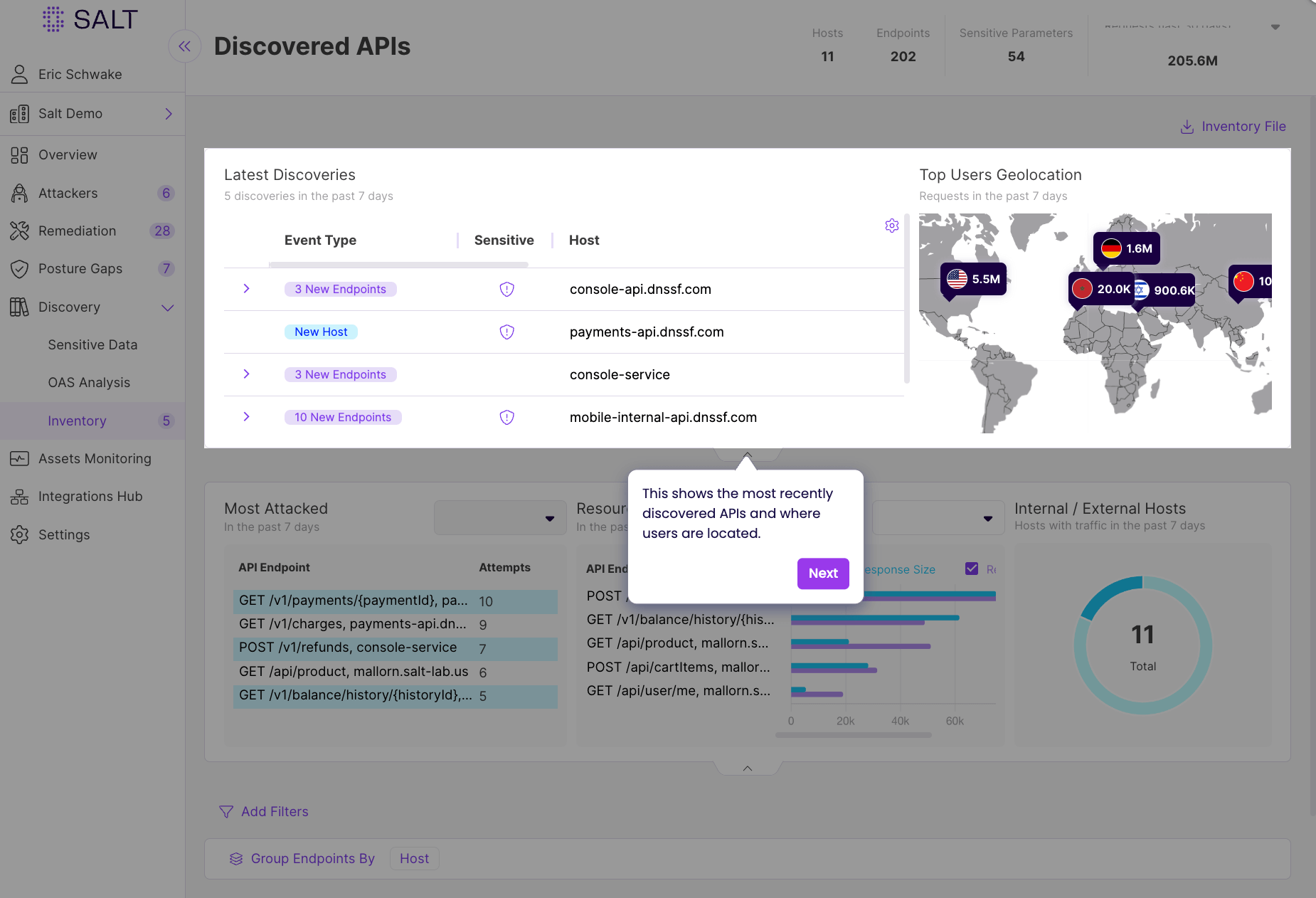
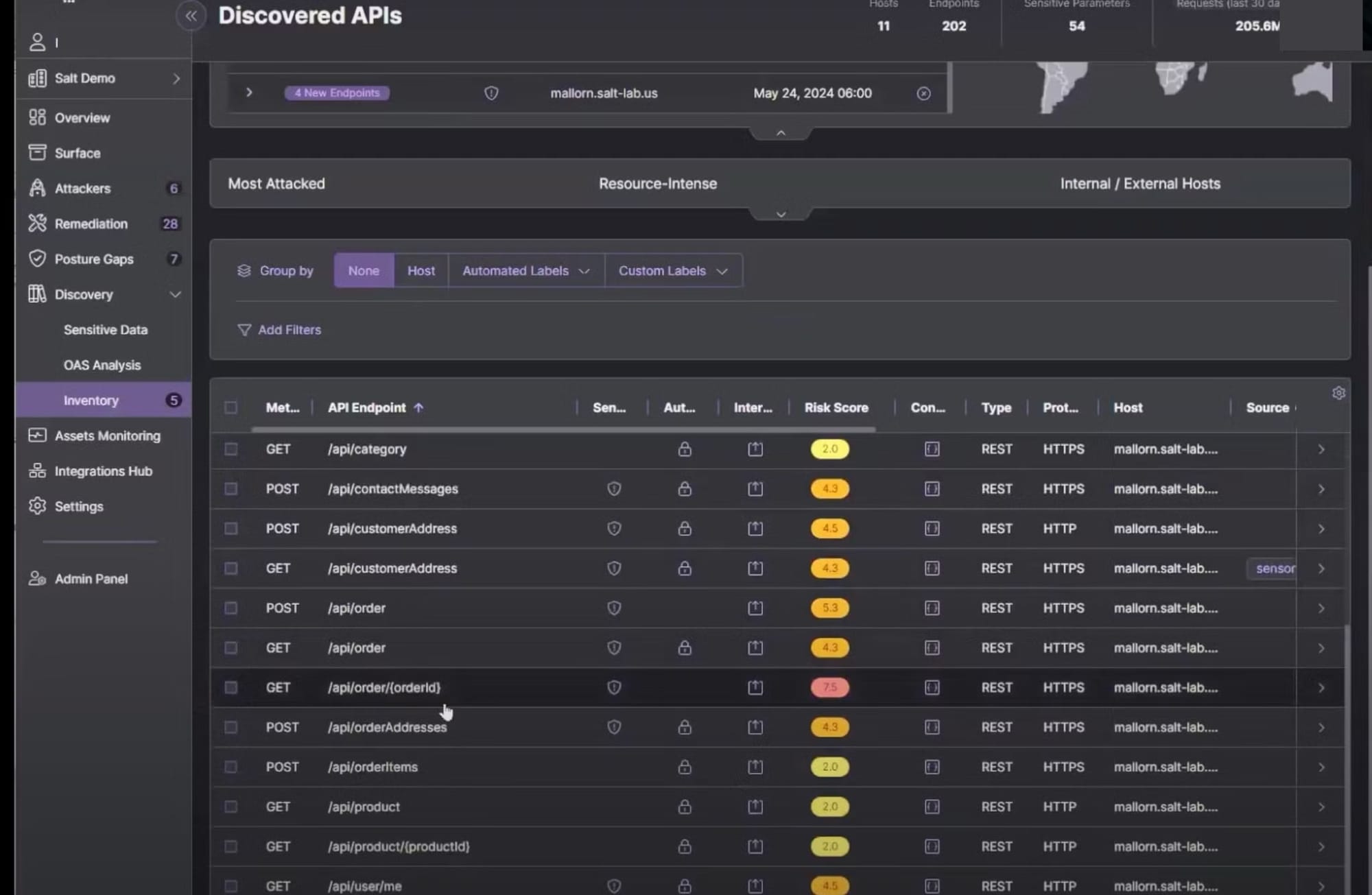
Salt Security API Discovery
API Security
Once discovery is done, it comes down to API security testing.
Salt Security focuses on runtime monitoring for API attacks. It relies on network traffic analysis, inspecting logs and traffic to detect threats. However, Salt’s approach to security testing is limited. Their scanning only occurs once an endpoint is already known, and the tool is primarily reactive.
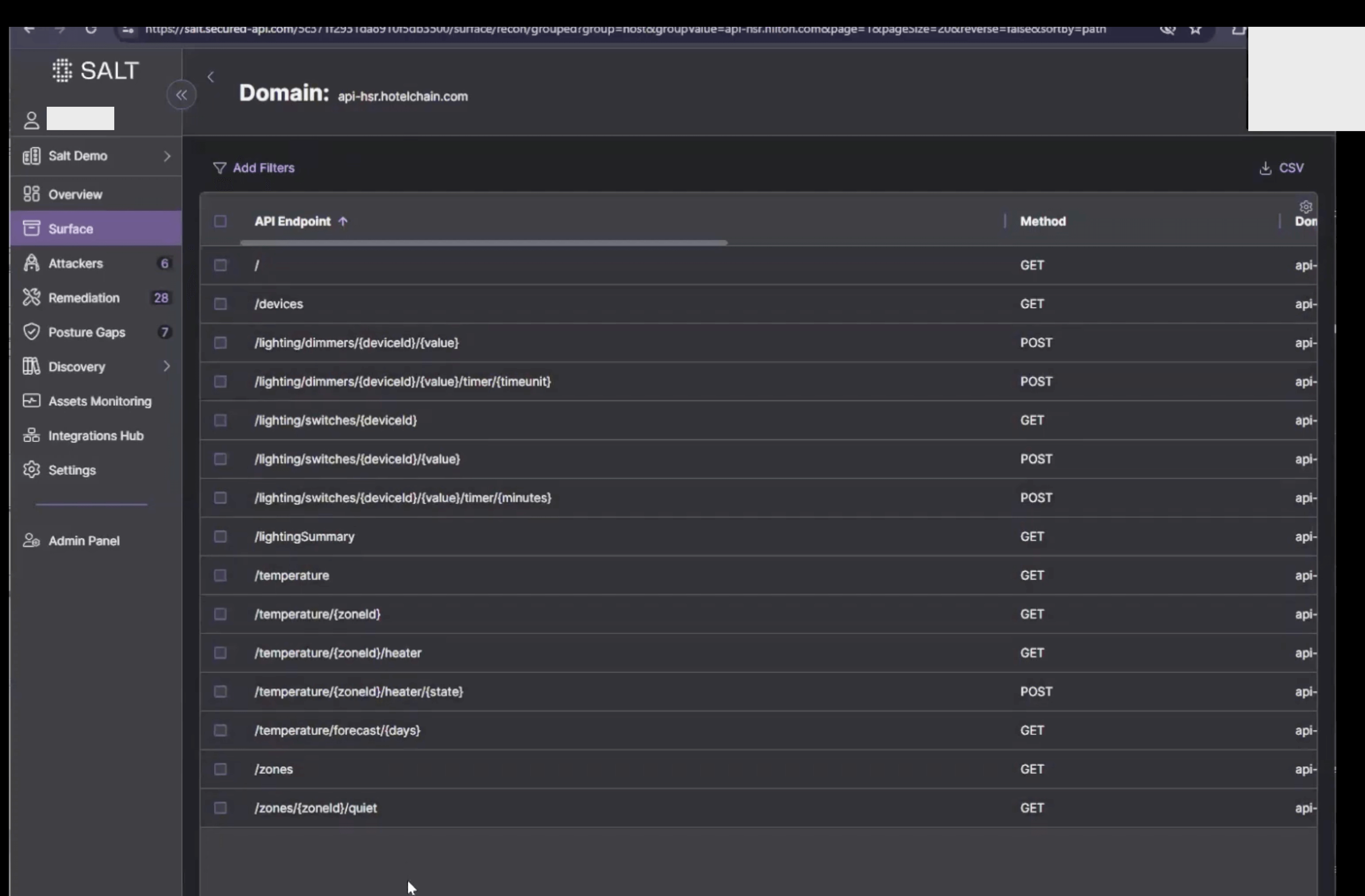
By default Salt comes with a wide array of out of the box risks are created equal. Security engineers need to understand which you can use (designated by the Salt Logo):

The exact quantity of pre-defined posture rules is unclear and many of their detections are header-based (examining only metadata like tokens, authentication headers, etc.), rather than analyzing the actual payload (the data being transmitted). This limits their ability to detect complex vulnerabilities that could be hiding in the content of API requests or responses.
It treats every method against every URL as an “endpoint, " leading to developer and security confusion.
As a result, Salt’s detection rules don’t extend deeply into business logic vulnerabilities or more nuanced attacks. Their focus on headers can lead to false positives or missed risks entirely.
In contrast, Escape uses a proprietary machine learning algorithm to automatically reconstruct API schemas, enabling context-aware scanning that can be initiated right away without requiring API traffic.
Escape relies on its proprietary feedback-driven Business Logic Security Testing algorithm. It excels in detecting even complex business-logic vulnerabilities, especially in modern API types like GraphQL. Escape's algortihm addresses this complexity by autonomously generating legitimate traffic to test API's business logic.
Through techniques like Sourcing Inference and Strong Typing Inference, Escape ensures the accuracy of generated requests, while integration with generative AI enhances adaptability, particularly in complex attack scenarios.
Escape’s testing is more thorough, happens before API is released into production and provides clear, actionable insights without the noise of false positives:

“Escape is an innovative tool, and its results and algorithms are truly impressive. It was able to find GraphQL vulnerabilities that their competitors haven't seen. It also provides me with extensive testing capabilities." – Pierre Charbel, Product Security Engineer, Lightspeed
Escape also offers custom security tests that users can implement on their own. They are based don't the YAML operators (detectors/transformations). Escape rules adapt to the evolution of your existing APIs and to your new APIs without the need to maintain them. This includes adapting to database fixtures in the development environment.

Risk-scoring
Not all risks are created equal. Security engineers need to understand which vulnerabilities represent the highest risk to assign the most critical fixes first to their developers.
When we asked one of the security practitioners about Salt Security's risk scoring, who viewed Salt's demo recently, he mentioned that Salt's risk scoring is "very basic and noisy, using empty requests and payloads in their demo which will never actually return things in a real-world example."
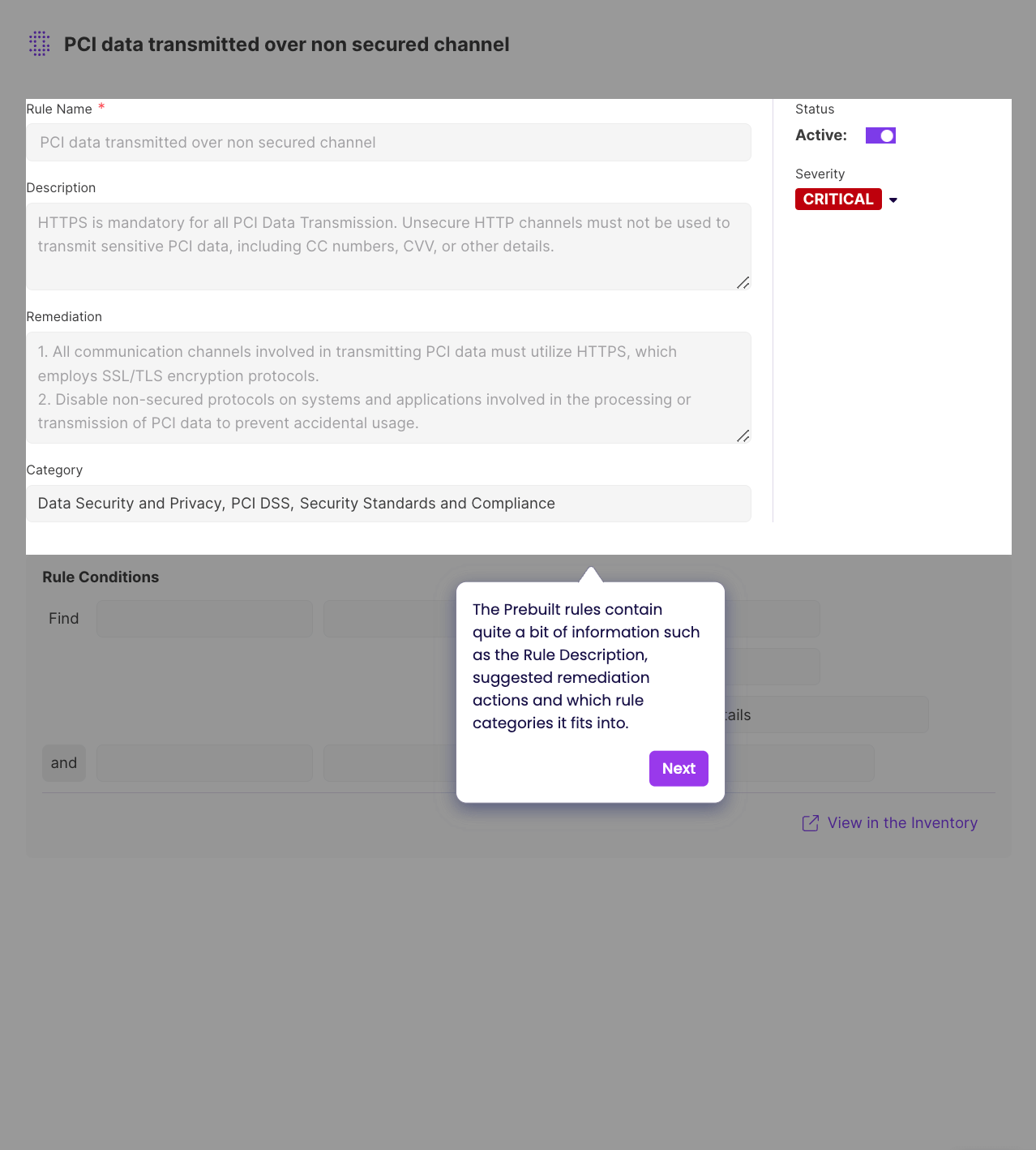
According to Salt's website, their scoring is based on the type of data in the API (sensitive, PII, PCI, etc) , the type of attack and the severity of associated posture gap rules.
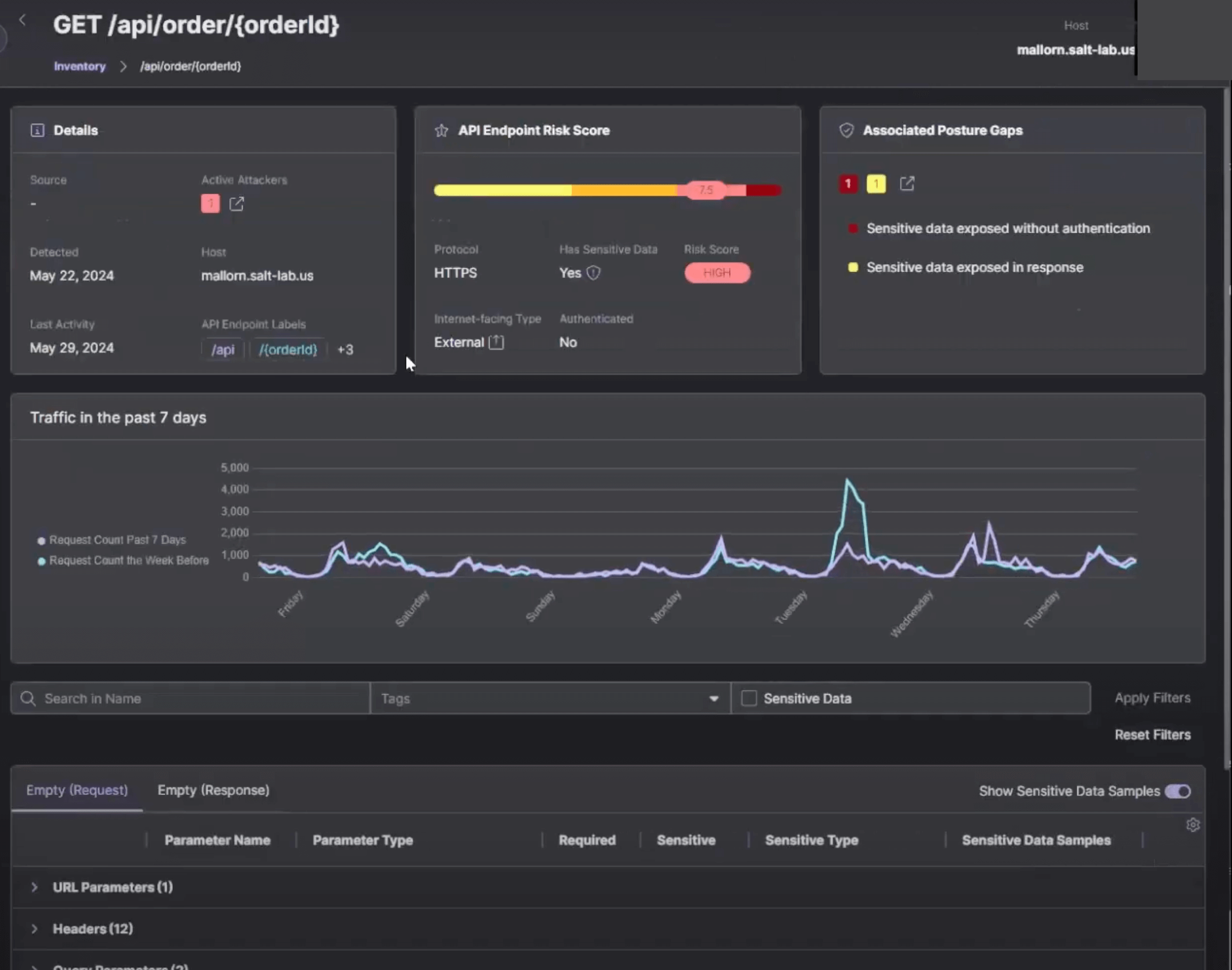
Going further, the posture alerts look super noisy and not context-aware. The alerts are primarily based on network traffic analysis, which means they can detect exploits in real-time but might miss more nuanced security issues:
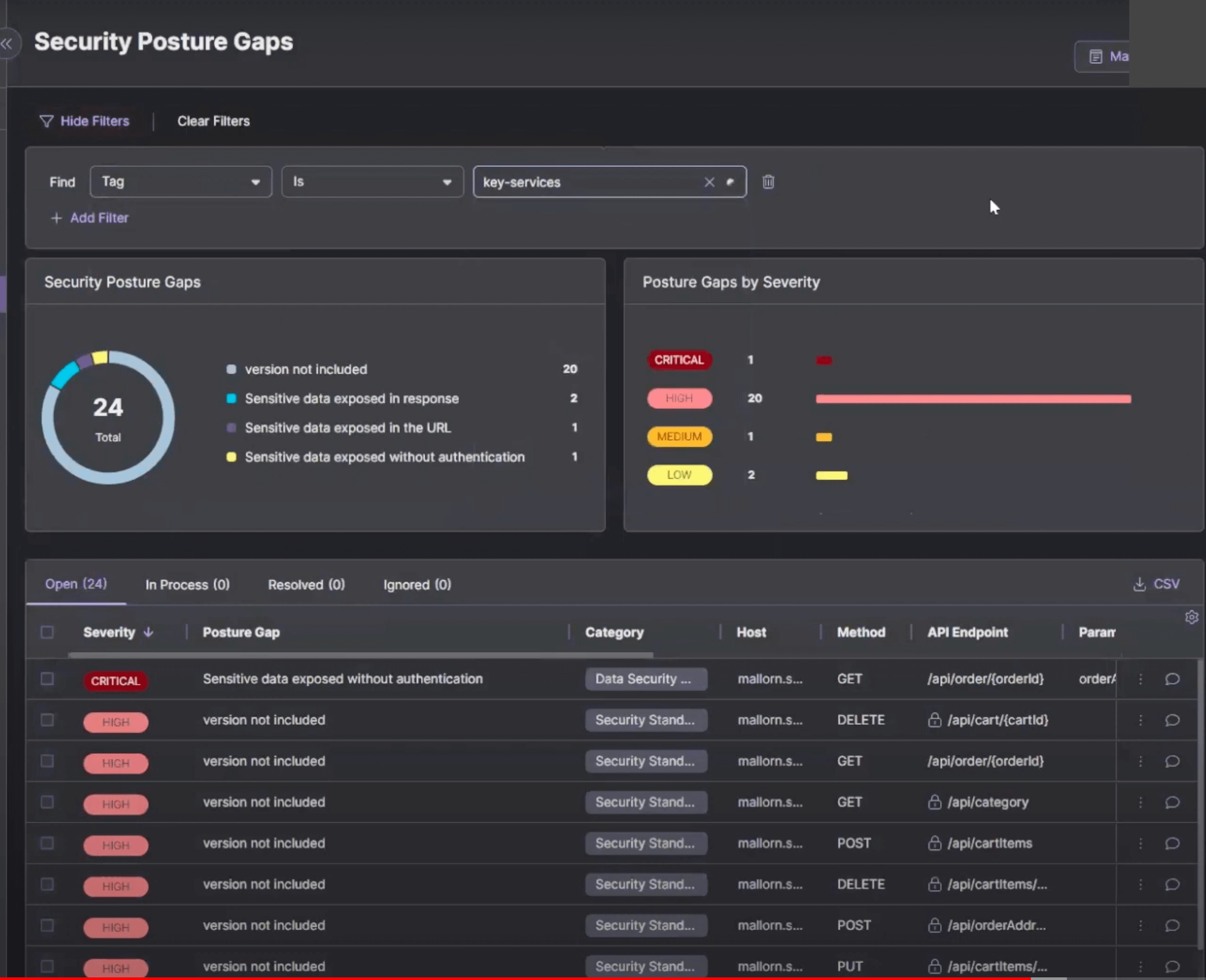
Escape, however, offers a distinct advantage with its vulnerability prioritization funnel. This feature automatically identifies and prioritizes business-critical vulnerabilities, ensuring that the most significant threats are addressed promptly. In addition, it clear shows each application's code owner .
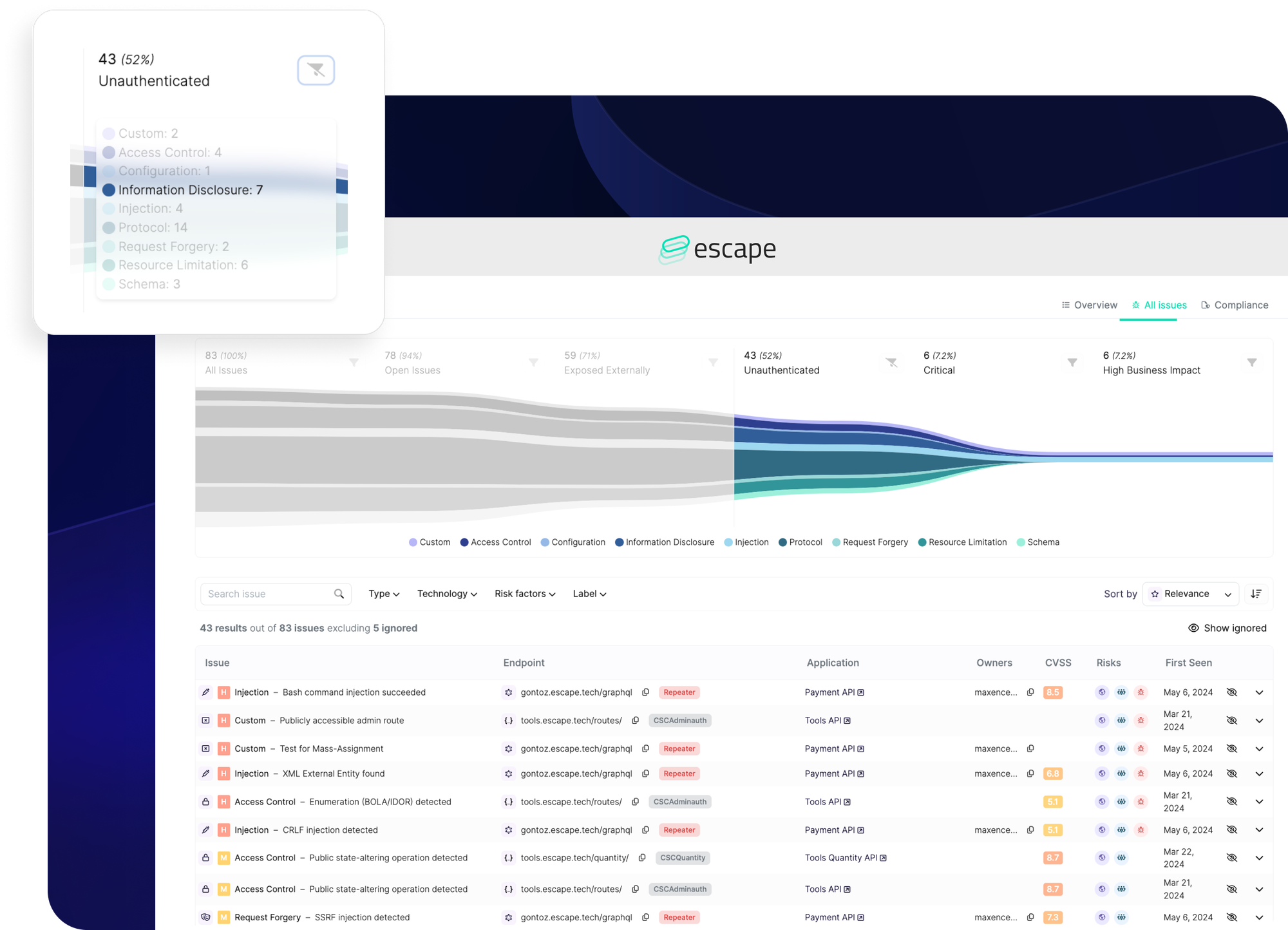
Since August 2024, Escape has been moving away from the traditional CVSS score-based system and adopting a new approach that highlights Escape Severity, including context related to API services. While CVSS scores provide a numerical risk measure, they don’t always capture the full picture. Escape Severity considers various factors such as the type of vulnerability, its exploitability, CVSS score, and other risk factors.
This comprehensive approach helps us better align issue prioritization with real-world risks and ensures you tackle the most critical issues more effectively.
By streamlining the prioritization process, Escape enables security teams to focus their efforts where they matter most, enhancing overall security and providing peace of mind that critical vulnerabilities are being effectively managed.
One of Salt Security's key drawbacks is that its findings aren’t easily actionable. While Salt can detect issues, its platform provides little direct support for developers to fix the identified vulnerabilities. The absence of code snippets or step-by-step remediation instructions means that security engineers need to manually translate alerts into fixes, which can be slow and error-prone.
Escape provides clear, actionable insights with detailed code snippets that developers can use directly. This feature speeds up the remediation process and ensures that security issues are addressed promptly and effectively.
Each code snippet can be tailored specifically to your development framework. Don't you think your developers will appreciate more someone who speaks their language?


Salt Security remediation advice vs Escape's remediation actionable code snippet
For each vulnerability, security teams can automatically share these code snippets with pre-filled remediation steps in Jira, saving time and ensuring faster resolution. Your developers can hit the ground running with the fix already in hand.

Compliance
Compliance with industry standards is a major factor for API security, especially in highly regulated industries like finance or healthcare.
It looks like Salt ensures compliance through pre-defined posture rules and gives the ability to export detailed reports to help auditors document the current environment and sensitive data your APIs may be sharing:

However, it does not provide a straightforward view of which API services are the least compliant, to what extent, or whether an API is compliant before it goes into production and traffic begins to flow through it.
As a result, it’s hard to judge whether Salt’s product can effectively help identify compliance gaps across all applications at a glance, limiting faster decision-making and prioritization of security efforts.
In contrast, Escape provides a comprehensive compliance matrix, allowing you to easily verify if your applications meet key standards such as OWASP Top 10, PCI-DSS, GDPR, SOC 2, PSD2, ISO 27001, NIST, and FedRamp. This unified view simplifies compliance management across multiple frameworks:
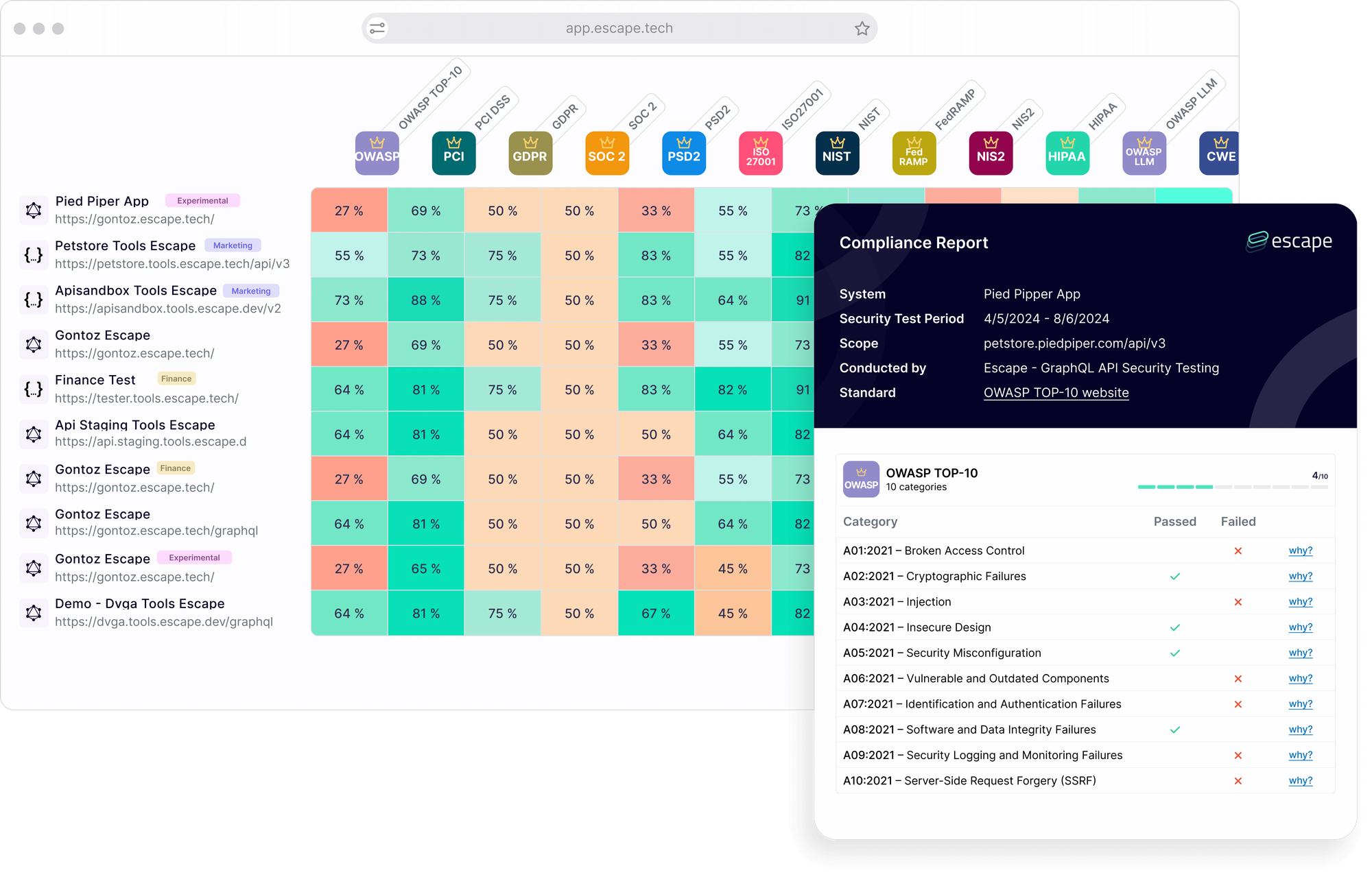
Recap: Pros and Cons
Side-by-side comparison table
Salt Security
Pros:
- Real-Time Detection: The platform can detect certain security threats in real-time based on network traffic.
- Integration Options: Salt Security offers numerous integration points for network logs and can detect sensitive data using these logs.
- Posture Management: Users can save searches as posture rules, enhancing ongoing security assessments.
Cons:
- Limited Testing: The system lacks comprehensive testing capabilities, as it primarily analyzes network logs without testing actual payloads, leading to potential blind spots in detection.
- Header-Based Alerts: Most alerts are based on HTTP headers rather than payloads, which may cause confusion and diminish the effectiveness of threat detection.
- Basic Scanning: Scanning capabilities are considered basic, primarily crawling known API endpoints without proactively discovering dormant or unmonitored APIs outside of API gateways, proxies, or WAFs.
- Noisy Risk Scoring: Risk scoring is very basic and can generate a lot of noise, complicating prioritization.
- High Costs: Utilizing traffic mirroring for detection can significantly increase logging costs, making it a potentially expensive option for organizations.
- Lack of Actionable Remediation: The absence of actionable remediation code snippets slows down the fixing process.
Escape
Pros:
- Exceptional ability to discover even Shadow APIs in minutes by scanning exposed source code, reducing the time to value and risk of overlooked vulnerabilities
- Automated schema generation that helps you to launch scans right away and reduces the need for maintenance
- In-depth GraphQL testing capabilities and lowest false-positive rate
- Ability to prioritize the most critical API by business context, data sensitivity, and exposure.
- Actionable remediation code snippets for developers that help you build better relationships with them
Cons:
- Advanced feature sets like Custom Security Tests that may require specialized knowledge
- Number of integrations with some of the operational tools
Conclusion
Salt Security offers features like traffic-based API discovery and real-time attack monitoring, but it struggles with the quality of security testing and remediation guidance. Users note a lack of effective tools for quickly addressing vulnerabilities. The quality of API discovery relies heavily on the provided logs; incomplete or poorly formatted logs can lead to undetected Shadow APIs and vulnerabilities. Additionally, while Salt provides risk scoring, many users find it inadequate to prioritize security efforts effectively.
Escape provides a more holistic and automated approach to API discovery and security. Its focus is on agentless API discovery, automated schema generation, advanced API security testing, and actionable insights for developers.
If you still have doubts, take a moment with our team and see directly during a demo what APIs your organization left exposed.
💡Want to learn more? Discover the following articles:
- Reinventing API security: Why Escape is better than traditional traffic-based tools
- Escape vs Noname
- Escape vs Cequence
- Escape vs Rapid7
*** This is a Security Bloggers Network syndicated blog from Escape - The API Security Blog authored by Alexandra Charikova. Read the original post at: https://escape.tech/blog/escape-vs-salt-security/
如有侵权请联系:admin#unsafe.sh
