2024-10-1 23:4:51 Author: lab.wallarm.com(查看原文) 阅读量:6 收藏
Modern businesses are increasingly reliant on APIs. They are the building blocks facilitating data exchange and communication between disparate systems. Because of their prevalence and importance, they are also under attack by actors exploiting vulnerabilities and misconfigurations.
Unauthorized access, data exposure, injection attacks, broken authentication, DoS attacks, shadow or unmanaged APIs, insecure API dependencies, and more present a real risk to APIs and the organizations that use them. As more APIs enter production, the attack surface grows ever larger.
Most organizations are aware of these threats and know they must protect against them. OWASP is doing a great job pinpointing these issues. The problem, however, is that many organizations are confused about which tools to use to solve which problems, leaving them at risk of attack. Much of this confusion surrounds API gateways and API protection. This confusion is understandable. Both tools provide security capabilities for APIs. However, they are not interchangeable: organizations must use API gateways and API protection, not one or the other.
What are API Gateways?
As the name suggests, API gateways are a single, centralized entry point for managing, routing, and optimizing API traffic between clients and backend services. They primarily provide operational and performance-related functions while providing basic security features.
What is API Protection?
API protection – or API security – refers to a comprehensive set of security capabilities designed to protect APIs from a wide range of security risks, including data breaches, unauthorized access, injection attacks, and abuse.
How Do They Complement Each Other?
As noted, although API gateways and API security are distinct tools, they work best when used in tandem. They each perform critical functions for different aspects of good API governance. By using them together, organizations can implement a complete strategy for managing and protecting APIs.
API Gateways and API Protection at the Business Level
At the business level, API security tools and gateways contribute distinct, but essential functions to an overall API governance program. They ensure optimal API performance and security, meaning businesses can manage their API infrastructure and safeguard against risks.
API gateways centralize API traffic management. They act as a single point of entry for all API calls, offering organizations greater visibility and control over how APIs are consumed across the enterprise so they can ensure these processes align with API governance policies. By using API gateways, organizations ensure that requests are routed between clients and backend services, and handle operational tasks such as load balancing, rate limiting, authentication, and monitoring.
API protection complements these functions by securing APIs across their entire lifecycle, helping to discover unmanaged or shadow APIs that the gateway may not yet manage. These tools also ensure the enforcement of API specifications, setting rules for how APIs are built, secured, and maintained. These capabilities help API governance teams conduct proper versioning, documentation, and security enforcement.
API Gateways and API Protection: Better Together for Enhanced Security
At the security level, API security tools and gateways provide different controls to protect APIs from various threats. API gateways provide basic, traffic-related security, while API security tools address more complex vulnerabilities and attack vectors. Let’s take a deeper look at their respective security capabilities.
API Gateways
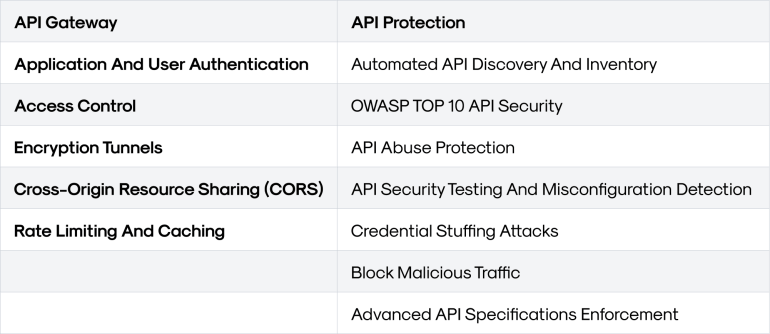
As mentioned earlier, API gateways primarily manage the flow of API traffic, but they also include some basic security controls. They include:
- Application and User Authentication: API Gateways implement various authentication methods, such as Basic Auth, API Key, OAuth/OIDC, and LDAP, to verify the identity of users and applications accessing APIs. This ensures that only authorized entities can interact with API endpoints.
- Access Controls: API Gateways enforce granular permissions through mechanisms like Access Control Lists (ACLs) and JWT scopes, ensuring that authenticated users have access only to authorized resources and actions.
- Encryption Tunnels: API Gateways secure data in transit using TLS and support mutual TLS (mTLS) for certificate-based authentication between servers and clients. This encryption protects sensitive data from being intercepted during transmission.
- Cross-Origin Resource Sharing (CORS): CORS policies managed by API Gateways control how different domains can access API resources, protecting against unauthorized resource sharing.
- Rate Limiting and Caching: Gateways use rate limiting to control API request traffic and prevent Denial-of-Service (DoS) attacks. Caching improves performance while reducing the load on backend services, mitigating risks associated with high traffic volumes.
API Protection
API Protection tools, however, build on these functions by focusing on securing the API itself, identifying vulnerabilities, and preventing sophisticated threats. Key security contributions include:
- Automated API Discovery and Inventory: These tools automatically detect new or changed API endpoints and monitor sensitive data exposure, such as Personally Identifiable Information (PII), ensuring that no API remains unprotected or undocumented.
- OWASP API Security: API Protection tools defend against the OWASP Top 10 API Security risks, such as broken object-level authorization, injection attacks, and misconfigurations, ensuring adherence to best security practices.
- API Abuse Protection: API security tools monitor for and block malicious or abusive behavior, such as excessive API calls, credential stuffing, or unauthorized data access, protecting the API from exploitation.
- API Security Testing: These tools perform automated security tests, identifying misconfigurations and vulnerabilities that could go unnoticed during API development, thus proactively strengthening API defenses.
- Credential Stuffing Protection: API security tools guard against credential stuffing attacks, where attackers use stolen credentials to take over accounts, protecting users and data.
- Blocking Malicious Traffic Sources: API protection tools prevent harmful traffic from reaching APIs by identifying and blocking requests from known malicious actors, such as Tor networks or certain geographic regions.
- Advanced API Specifications Enforcement: These tools ensure that APIs conform to predefined specifications, such as OpenAPI, reducing misconfigurations and ensuring all endpoints are secure and properly documented.
These two tools complement each other because they perform entirely different functions. Using only an API gateway, for example, would leave your organization vulnerable to API abuse and credential stuffing. Using only an API protection tool, however, would leave data unsecured in transit. The same goes for all of the other functions listed above.
The image below shows a comparison of API gateways and API protection.

How Wallarm Can Help
Proper API management and security require both API gateways and API protection. As we like to say, these solutions are Better Together. Wallarm’s API Attack Surface Management (AASM) greatly integrates with market-leading API gateways to discover all external hosts with their APIs, identify missing WAF/WAAP solutions, and mitigate API leaks. To discover what Wallarm can do for your organization, request a demo or log into our Playground.
如有侵权请联系:admin#unsafe.sh