2024-10-1 14:18:6 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
User interaction with online platforms, applications, and websites has become a fundamental aspect of daily life. Whether you’re shopping, managing finances, or engaging with social media, your interaction with a user interface (UI) shapes your experience. However, not all UI designs have your best interests in mind. Hackers sometimes use clickjacking and dark patterns to trick users into performing unintended actions. These deceptive tactics can lead to compromised security, unwanted purchases, or data breaches. In this blog, we will explore how clickjacking works, its impact on users, and strategies to defend against these deceptive practices.
What are Dark Patterns?
Dark patterns are deceptive design techniques used in digital platforms to manipulate users into making choices they may not intend, such as purchasing items, subscribing to services, or sharing personal information. Unlike effective user interface (UI) design that prioritizes user experience, these misleading tactics serve the interests of the business at the user’s expense. They can manifest in various ways, including misleading language, hidden fees, and confusing layouts.
Some of the most prevalent dark patterns aim to:
- Frustrate users when trying to cancel an account, close pop-up windows, or unsubscribe from services.
- Create a sense of urgency to compel users to purchase products or services quickly.
- Mislead users into actions they did not intend, such as automatically adding insurance to a flight ticket.
- Coerce users into consenting to share more information than they intended, for instance, by presenting location tracking as an opt-out choice rather than requiring consent or by making the “Accept Cookies” button far more prominent than the “Decline” option.
Why is it Important to Avoid Dark Patterns?
Avoiding dark patterns is crucial for fostering trust and transparency in digital interactions. These manipulative design strategies can mislead users into making choices they wouldn’t typically make, ultimately eroding their autonomy and leading to negative experiences. Here are some key reasons why it’s important to avoid dark patterns:
Compromise in Customer’s Trust
The existence of dark patterns in websites and applications can quickly undermine an organization’s credibility and consumer trust, ultimately harming the businesses that employ them. A 2021 study in the UK revealed that nearly 25% of respondents held negative views about organizations using UI manipulation, and 16% reported they had ceased using a website or app (either temporarily or permanently) because of these practices.
Violate Privacy Laws
The use of dark patterns is not only unethical but also illegal in certain jurisdictions. Patterns in UI and UX have become so prevalent that lawmakers in both the U.S. and the European Union have recently taken steps to address them.
For instance, the California Consumer Privacy Act (CCPA) specifically targets companies that use UI to manipulate users into consenting to the sale and sharing of their personal data. The law explicitly states that consent obtained through UI manipulation is not valid under the CCPA.
Similarly, European data protection authorities are cracking down on dark patterns. In March 2021, a coalition of EU and EEA data protection authorities released guidelines detailing how these deceptive practices violate the core principles of the GDPR. The upcoming EU Digital Services Act will also ban online platforms from using UI manipulation.
Impact on User Experience
UX has a direct impact on user retention and conversion rates. However, there is a clear distinction between good UX and dark patterns. While both aim to encourage users to complete a desired action, the difference lies in intent: good UX focuses on meeting the user’s needs and providing a positive experience, whereas UI manipulation prioritizes business objectives at the expense of the user.
Good UX designers create a seamless, intuitive interface that enhances user satisfaction and engagement. On the other hand, UI manipulation is inherently manipulative, steering users into actions they didn’t intend to take.
Clickjacking: A Classic Example of Dark Patterns
It is a technique where an attacker overlays invisible or misleading elements on a webpage to trick users into clicking on something they did not intend to. This method takes advantage of the user’s trust in the website they are interacting with by disguising the malicious actions underneath what appears to be a legitimate interface.
For instance, imagine you are clicking a “Play” button to watch a video, but instead, you unknowingly authorize a transfer of funds or share private information. In a clickjacking attack, the legitimate button is hidden beneath a transparent layer that performs a different action, catching the user completely unaware.
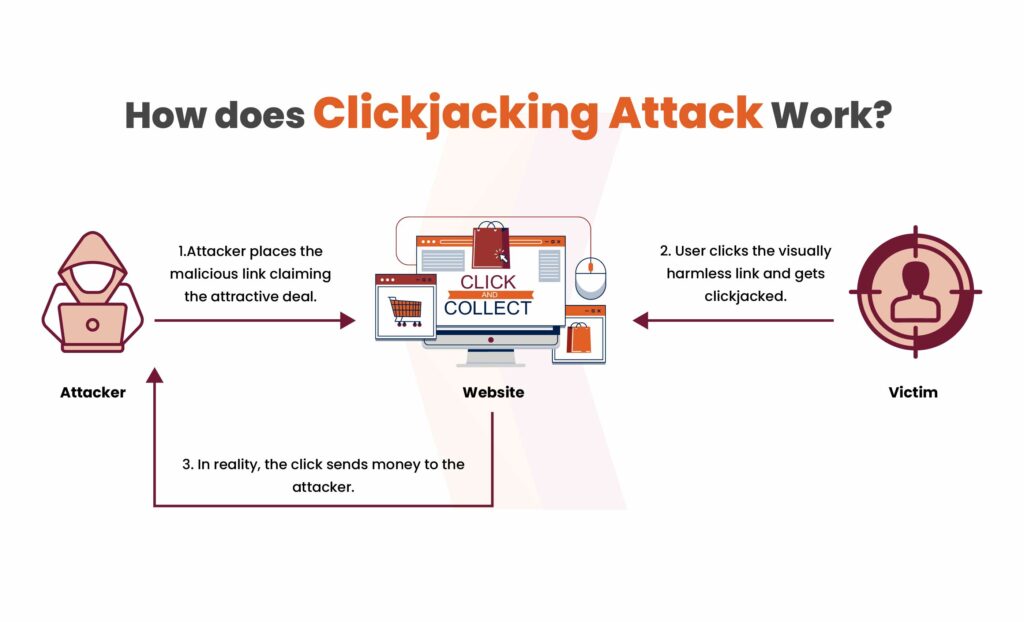
How Clickjacking Attack Works?
When a user unsuspectingly clicks on an appealing link, the attack initiates its deceptive process. Here’s a simplified explanation of how it usually occurs:
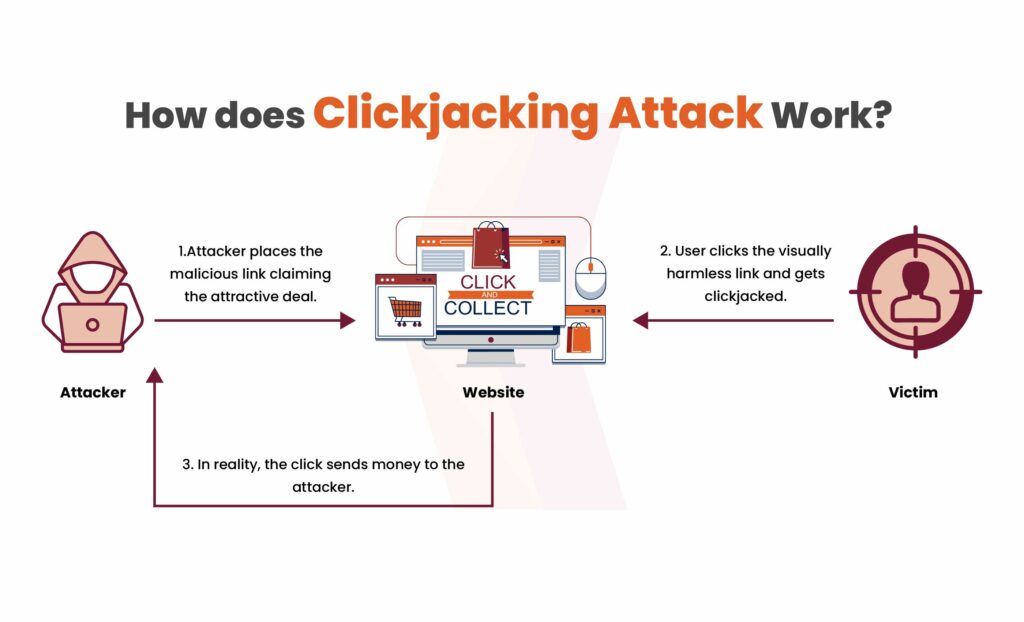
- The attacker first checks if the user is logged into critical accounts, such as banking or online shopping platforms.
- They then manipulate the user interface (UI) by overlaying fake buttons or links on top of real, legitimate ones, making it appear like harmless content.
- When the user interacts with what looks like a legitimate offer or action, they unintentionally click on the concealed buttons beneath the surface.
- These hidden clicks trigger unauthorized transactions or actions, such as transferring money or sharing personal data, without the user’s awareness or consent.
- The attacker executes their hidden goal, such as fraudulent transfers or data theft, while distracting the user with a fake offer or content.
- Since the user initiated the actions while logged in, it becomes challenging to trace the attack back to the attacker, as the activity appears to be coming from the legitimate account holder.
Impact of Clickjacking Attack
The attack can have serious consequences for both users and organizations. The effects of a successful attack depend upon the attacker’s goals and the actions users unknowingly perform. Below are some of the key impacts of clickjacking attack:
Unauthorized Actions
Clickjacking enables attackers to deceive users into unintentionally performing actions they never intended. This can involve unauthorized purchases, sharing confidential information, granting access to malicious applications, or interacting with hidden elements that jeopardize security.
Data Theft
Clickjacking attacks can result in the theft of sensitive user data. Attackers may trick users into clicking hidden elements that initiate malware downloads or prompt them to enter confidential information, leading to data compromise.
Financial Loss
If clickjacking results in unauthorized actions, users could face financial losses from fraudulent purchases or transactions carried out without their knowledge or consent.
Reputational Damage
Organizations with vulnerable websites risk reputational damage if their users fall victim to clickjacking attacks. This can result in a loss of trust from both customers and stakeholders.
Privacy Violations
Clickjacking can lead to privacy violations if users unknowingly share personal or confidential information on social media or other platforms.
Malware Distribution
Attackers can use clickjacking to distribute malware to users’ devices, leading to further security breaches or system compromises.
Clickjacking Test: Is your Site at Risk?
A simple method to check if your site is vulnerable to clickjacking is to create an HTML page that tries to load a sensitive page from your website within an iframe. Be sure to run the test code on a separate web server, as this mimics the typical behavior of a clickjacking attack. You can use code similar to the example provided in the OWASP Testing Guide.
Open the HTML page in a browser and assess it as follows:
- If you see the message “Website is vulnerable to clickjacking” along with the content of your sensitive page below it, your page is vulnerable to clickjacking.
- If only the message “Website is vulnerable to clickjacking” appears without displaying your sensitive page, the page is not susceptible to the simplest form of clickjacking.
We need to conduct additional testing to determine which anti-clickjacking measures are in place on the page and whether attackers can bypass them.
How to Defend Against Clickjacking Attacks?
While clickjacking might initially seem trivial, it represents a serious risk. It’s not merely a harmless trick; its objectives can be quite harmful. To protect your finances, customers, and brand reputation, it is vital to take proactive measures against these attacks.
Enhance your web applications to close vulnerabilities and prevent unauthorized access. Investing in a managed Web Application Firewall (WAF) can provide constant protection, swift vulnerability fixes, and continuous threat surveillance, ensuring that false positives are minimized. Other effective measures to prevent clickjacking attacks include:
X-Frame-Options Header
Configure the web server to include the X-Frame-Options HTTP header in its response to control whether a web page can be rendered in an iframe.
The “DENY” option completely disallows the page from being shown in any iframe, whereas “SAMEORIGIN” allows it to be displayed only within the same origin (same domain).
Content Security Policy
Enforce a strict Content Security Policy (CSP) by utilizing the “frame-ancestors” directive to designate which domains are permitted to embed the website’s content within an iframe. This measure helps to prevent unauthorized framing of the site.
Frame Busting Scripts
Add frame-busting JavaScript code to your web pages. This code detects if the page is loaded within an iframe and redirects the user to the top-level window, escaping the iframe and preventing clickjacking attacks.
Use X-Content-Type-Options
Configure the X-Content-Type-Options HTTP header to have the value “nosniff” to stop browsers from interpreting files as an alternative MIME type. This measure helps protect against specific clickjacking attacks that exploit the browser’s ability to misinterpret content.
Book a Free Consultation with our Cyber Security Experts

Conclusion
Dark patterns and clickjacking pose significant risks to both users and organizations. As online interactions continue to grow, it is critical for businesses to prioritize ethical design practices, ensuring transparency and user autonomy. At the same time, individuals must stay vigilant and aware of these manipulative tactics. By implementing protective measures like the X-Frame-Options header, Content Security Policies, and frame-busting scripts, organizations can safeguard their platforms from clickjacking attacks, minimizing vulnerabilities and ensuring a secure, trustworthy user experience.
As a CERT-In empanelled organization, Kratikal is equipped to enhance your understanding of potential risks. Our manual and automated Vulnerability Assessment and Penetration Testing (VAPT) services proficiently discover, detect, and assess vulnerabilities within your IT infrastructure. Additionally, Kratikal provides comprehensive security auditing services to ensure compliance with various regulations, including ISO/IEC 27001, GDPR, PCI DSS, and more, assisting your business in adhering to legal requirements set forth by diverse governments.
FAQs
- Why are dark patterns used?
A dark pattern, also known as a “deceptive design pattern,” is a user interface deliberately crafted to mislead users. It tricks them into actions like buying unnecessary insurance or signing up for recurring charges.
- Is clickjacking a serious vulnerability?
Clickjacking poses a significant risk to internet users, potentially resulting in unauthorized actions and exposure of sensitive data.
- Are dark patterns unethical?
Yes, dark patterns are unethical because they manipulate users into doing things they wouldn’t otherwise do. They can lead to financial losses and data sharing and can make users more vulnerable to exploitation.
- What is the root cause of clickjacking?
This type of attack usually involves concealing the user interface of the target website while manipulating the visible interface so that the user is unaware they are clicking on the target site. Because of this arrangement of the UI, it is commonly referred to as UI redressing or a UI redress attack.
The post How Dark Patterns Trick Users into Unintended Actions? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/how-dark-patterns-trick-users-into-unintended-actions/
如有侵权请联系:admin#unsafe.sh
