2024-10-4 15:2:7 Author: www.mobile-hacker.com(查看原文) 阅读量:7 收藏
![]()
Running Kali Linux on a Raspberry Pi Zero is a fantastic way to create a portable, powerful testing device. This guide will walk you through setting up Kali Linux Pi-Tail on a headless Raspberry Pi Zero 2 W that is powered and controlled from a smartphone via SSH or VNC that provides a graphical interface to your Pi-Tail. I find it as of-the-shelf, cheap, portable and the smallest hacking lab that is fully controlled from any smartphone. Since controlling it doesn’t require you to have a keyboard, mouse or screen, it makes it a very convenient setup for Wi-Fi pentesting such as AP and clients scanning, deauthentication, WPS pin cracking, evil twin attack, capturing handshake and also network scanning and vulnerability assessment using nmap, brute-forcing, Bluetooth attacks, social engineering, running Metasploit framework, wardriving, web proxy using Burp Suite, using proxmark3, communicate with another Android using ADB commands, or even dynamically analyze iOS and Android apps using Frida.
If Kali Pi-Tail is connected to energy supply, it will automatically connect to predefined Wi-Fi networks that is broadcasted by a smartphone as a hotspot, allowing you to control it via SSH or VNC.
- Raspberry Pi Zero 2 W,
- microSD card (at least 16GB),
- OTG adapter,
- USB power cable or USB-A board add-on,
- Smartphone with SSH (Termux) and VNC (VNC Viewer for Android) apps installed. For some reason RealVNC app wasn’t able to connect to Pi-Tail,
- Kali Linux Pi-Tail image.
1. Download and Prepare the Kali Linux Pi-Tail Image
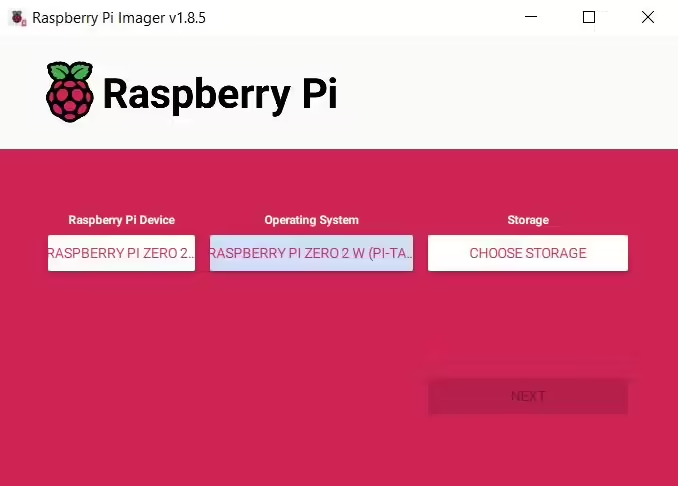
- Download the Pi-Tail image from the official Kali Linux website.
- Use Raspberry Pi Imager to write the image to your microSD card.
- From Operating System select
Other specific-purpose OS->Kali Linux->Raspberry Pi Zero 2 W (Pi-Tail)
- From Operating System select
2. Insert the MicroSD Card and Power Up
- Insert the microSD card into your Raspberry Pi Zero 2 W.
- Connect the OTG adapter to your smartphone and the USB power cable to the Pi-Tail to power it up.
3. Configure Your Smartphone
- Enable the hotspot on your smartphone with the SSID
sepulturaand passwordR4t4m4h4tt4. - Install the Termux (for SSH) and alternatively VNC Viewer for Android app on your smartphone.
4. Connect to the Pi-Tail
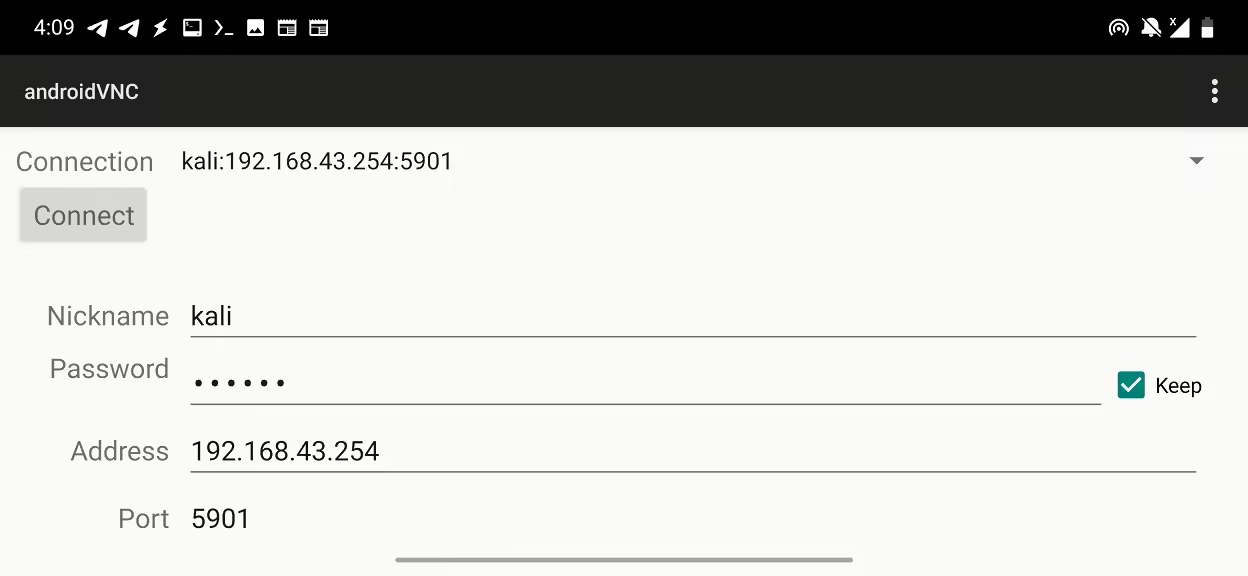
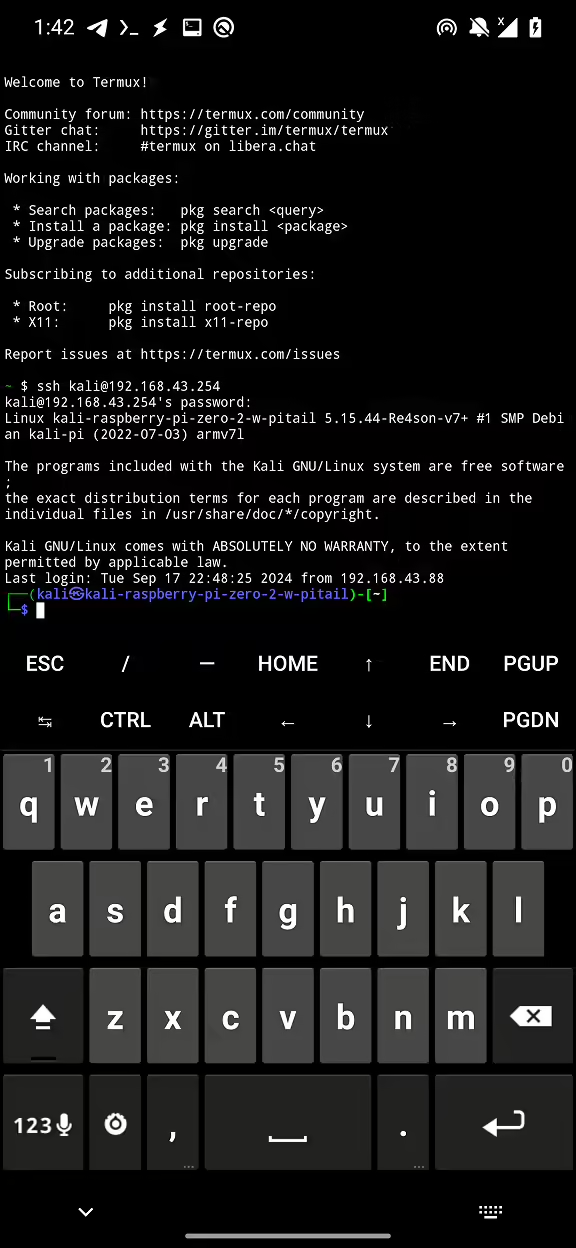
- Open Termux app and connect to the Pi-Tail using the IP address 192.168.43.254 with the username
kaliand passwordkali.
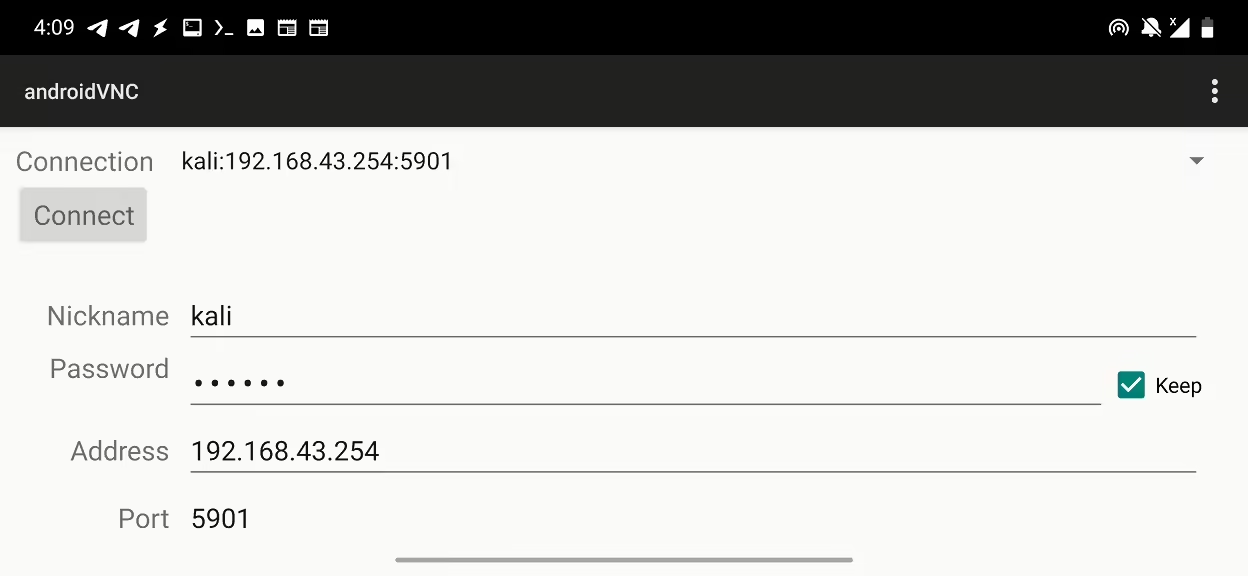
- For VNC, start the VNC server on the Pi-Tail by running
sudo vncserver -localhost no. When requested, create a password that you will need for VNC connection. Now to connect to it, use VNC Viewer for Android app with 192.168.43.254:5901 IP address andkaliusername with the password you created.
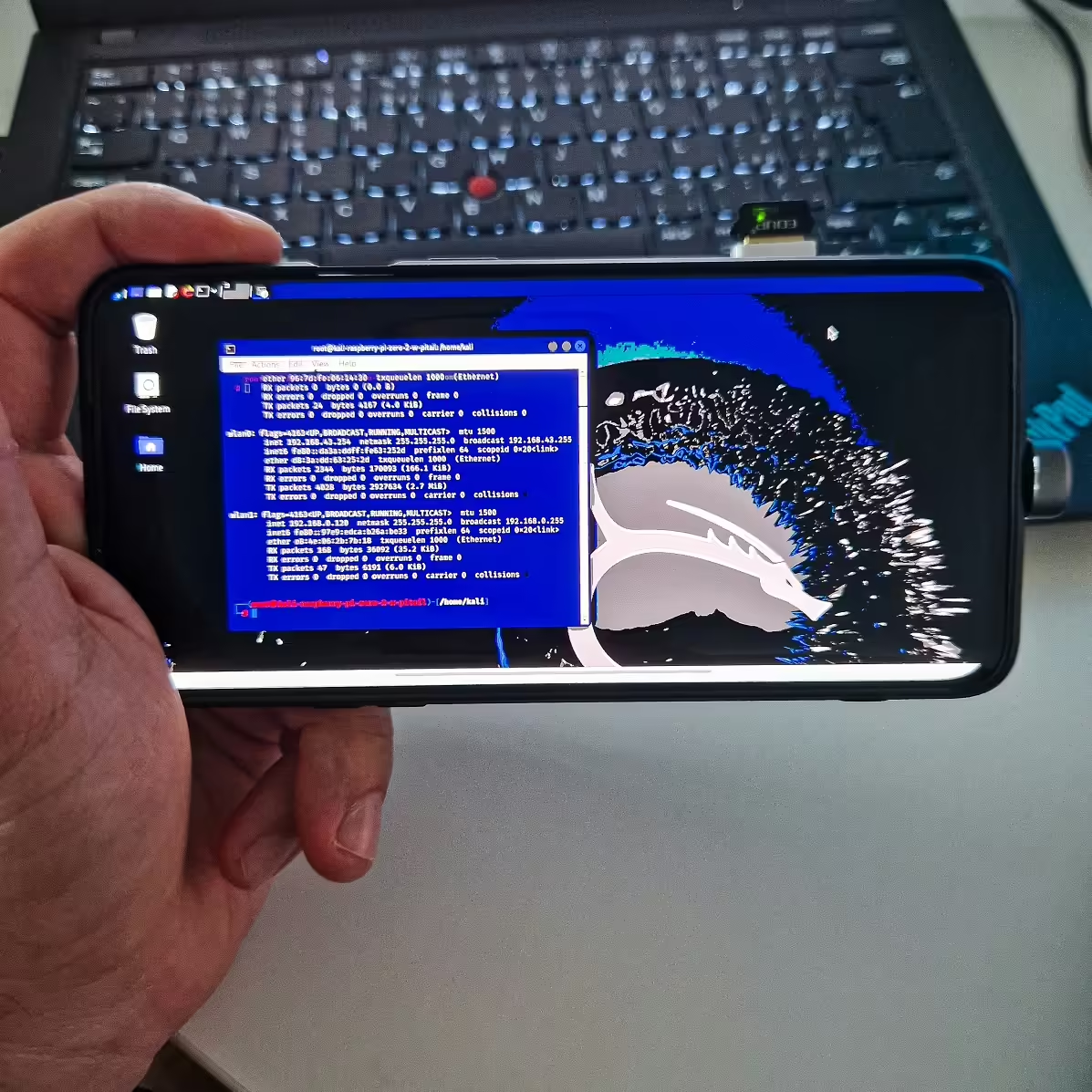

5. Update and Upgrade Kali Linux
Once connected via SSH, update and upgrade the system:
sudo apt-get update&&sudo apt-get upgrade- Since most likely your
sepulturahotspot doesn’t have an internet connection, you can plug in an external Wi-Fi adapter into Pi-Tail and use it to connect to access point with internet access. - Alternatively, you can pull out the microSD card and plug it into another device such as Raspberry Pi and update or install additional software.
The Pi-Tail setup is highly portable. Your smartphone acts as the power supply, screen, keyboard, and mouse, making it an excellent field companion for penetration testing.
Connecting to an additional Wi-Fi network requires an extra Wi-Fi adapter. This is particularly useful when you need either an internet connection or want to run network scanning tools like Nmap on different network simultaneously. For convenience, you can use a script below that connects to a network based on its name and password.
#!/bin/bash
# Check if two arguments are provided
if [ "$#" -ne 2 ]; then
echo "Usage: $0 <wifi_network> <password>"
exit 1
fi
wifi=$1
pass=$2
sudo service NetworkManager start &
sudo ifconfig wlan1 up
sudo nmcli dev wifi connect $wifi password $pass ifname wlan1A good case makes it easier to carry around and use, keeping everything safe and stylish wherever you go. You can print a 3D case designed and published by 4x0nn available for download at Odysee.
When I added a USB-A board, I had to adjust it a bit to made it little thicker and add an opening for USB.

I experimented with testing iOS using a Kali Pi-Tail and faced some interesting challenges. I created a sepultura hotspot on my iPhone, but the Pi-Tail didn’t get enough power when connected via an OTG adapter. Using an external battery allowed it to connect to the hotspot, but I couldn’t establish an SSH connection. In conclusion, the setup didn’t work as intended. It likely needs some tweaks, but as I’m not an iPhone user, so I didn’t spend more time troubleshooting.

sepultura hotspot created by iPhone- Connection Issues: From my experience, using my Samsung smartphone, Pi-Tail has for some reason a problem to connect to a hotspot. I couldn’t find a solution or workaround.
- Performance: The Raspberry Pi Zero 2 W is a low-power device. For intensive tasks, consider using a more powerful Raspberry Pi model. Sometimes, Pi-Tail has a problem to initialize an external Wi-Fi adapter. Because of that, I had to unplug and plug until it was recognized by device.
- Change Access Points: For some reason, changes in
wpa_suplicantfile are not reflected nor stored after restart. Because of that, it is difficult to connect to another Wi-Fi network thensepulturausing internal Wi-Fi chipset. - SSH connection refused: I experienced that suddenly Pi-Talis doesn’t allow me to connect to it over SSH with Connection refused error. This happened to me when I was switching from
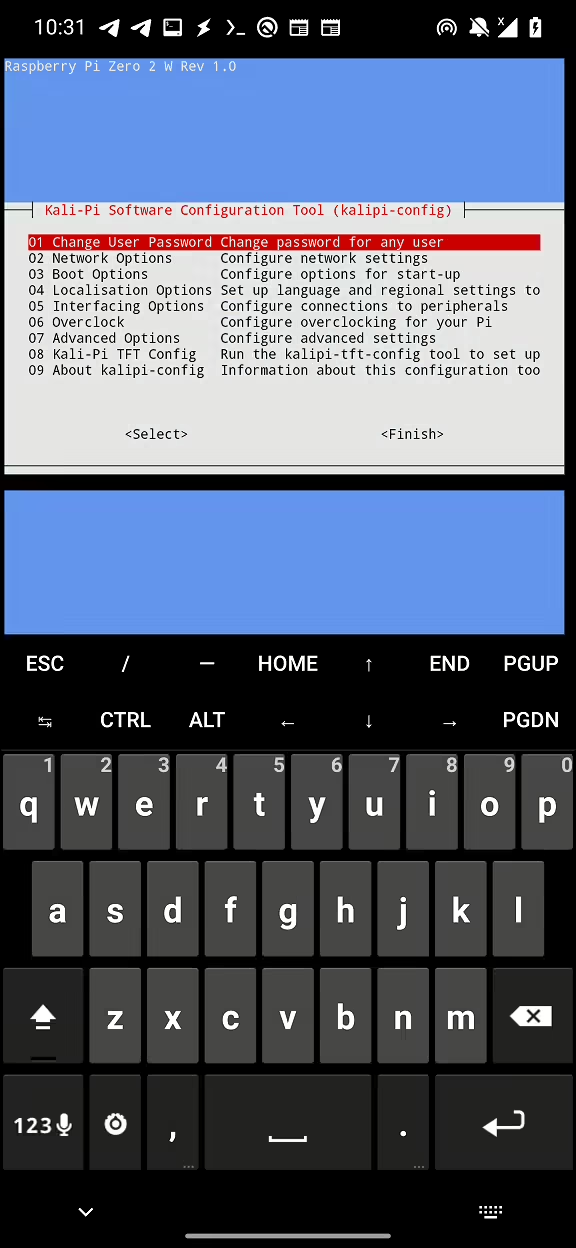
sepulturahotspot to my home LAN and vice versa. To fix it, you need to enable SSH service fromkalipi-configmenu. This can be done by connecting Pi-Tail over HDMI to monitor and plug-in a keyboard. Executesudo kalipi-config->Interfacing Options->SSH-> Yes
By following these steps, you can set up and use Kali Linux Pi-Tail on a headless Raspberry Pi Zero 2 W, controlled entirely from your smartphone. This setup provides a compact and efficient solution for on-the-go penetration testing and other cybersecurity tasks. Using an OTG adapter, you can connect your Raspberry Pi to both Android and iOS devices, allowing for seamless control and power directly from your smartphone. You can easily connect additional devices like WiFi adapters, Bluetooth adapters, and SDRs to enhance your testing capabilities, making your setup even more versatile.
如有侵权请联系:admin#unsafe.sh