
2024-10-4 19:39:49 Author: www.vmray.com(查看原文) 阅读量:13 收藏
The Labs team at VMRay actively gathers publicly available data to identify any noteworthy malware developments that demand immediate attention. We complement this effort with our internal tracking and monitor events the security community reports to stay up-to-date with the latest changes in the cybersecurity landscape.
In September 2024, the VMRay Labs team has been focused on the following areas:
1) New VMRay Threat Identifiers addressing:
- Detect disabling Windows Defender notifications
- Detect disabling Windows A notifications
- Detect rundll32.exe loading remote DLLs from network drives
- Detect querying for Thunderbird profile information
2) Configuration Extraction capabilities for:
- Latrodectus
3) New YARA rules for:
-
3 new PhishKits
- Known anti-debugging and evasion techniques
Now, let’s delve into each topic for a more comprehensive understanding.
, we introduced you to the concept of the VMRay Threat Identifiers (VTIs). In short, VTIs identify threatening or unusual behavior of the analyzed sample and rate the maliciousness on a scale of 1 to 5, with 5 being the most malicious. The VTI score plays a key role in determining the ultimate Verdict of the sample, which is displayed in the VMRay Platform after the analysis is complete. Here’s a summary of the new VTIs we’ve added or enhanced over the past month.
Detect disabling Windows Defender notifications
Category: Hide Tracks
MITRE ATT&CK® Technique: T1112
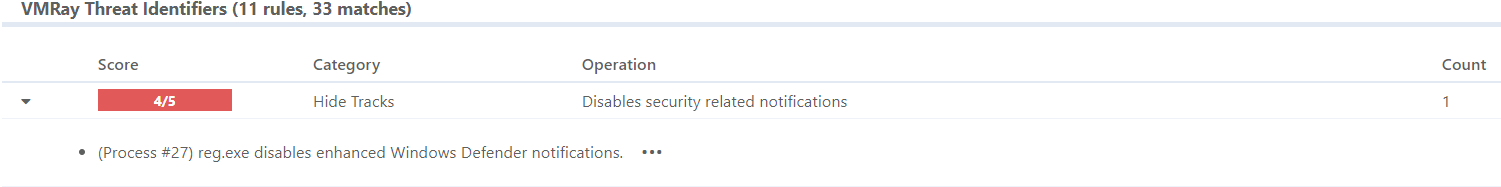
In recent months, we’ve focused on detecting modifications to Windows Defender settings. Now, we’re expanding to address a related tactic: disabling Windows Defender notifications. Our new VTI identifies when malware attempts to silence crucial security alerts, ensuring that users remain informed of potential threats.
Cybercriminals often employ various methods to conceal malicious activities from users and administrators. One effective tactic involves suppressing Windows Defender notifications to prevent security warnings from being displayed. By muting these alerts, malware can operate undetected, giving attackers more time to steal data or cause damage.
Malware can modify the Windows Defender setting known as the Notification_Suppress value, preventing Windows Defender from displaying alerts. As a result, even if a threat is detected, users remain unaware, allowing the malware to continue its operations undisturbed. This increases the likelihood of the infection going unnoticed until significant harm is done.
Disabling enhanced notifications
Beyond basic alerts, Windows Defender also provides enhanced notifications, offering detailed information on non-critical threats or quarantined files. By tampering with the DisableEnhancedNotifications registry key, malware can disable these more comprehensive warnings, further reducing the user’s ability to detect early signs of a security breach.
This is where our new VTI comes into play. If malware successfully disables these notifications after gaining administrative control, it can remain hidden for an extended period. Our VTI helps detect such changes, allowing security teams to respond quickly and prevent potential damage—even when alerts are suppressed.
Detect disabling Windows A notifications
Category: Hide Tracks
MITRE ATT&CK® Technique: T1112
In September, we released a new VTI designed to tackle a specific malware technique targeting Windows systems. The malware operates by disabling Windows Security Center notifications, leaving users vulnerable to security threats without their knowledge.
In this technique, the malware exploits a registry key to disable the Windows Action Center, cutting off crucial security notifications from reaching the user. This change effectively disables Action Center notifications, allowing the malware to carry out malicious activities undetected. The disabling of the Action Center also affects the visibility of important security alerts like antivirus notifications, making it harder for users and security teams to react in a timely manner.
To combat this, we’ve introduced a new VMRay Threat Identifier that detects this behavior. The VTI triggers upon identifying any malware samples attempting to modify this registry value, providing an early warning system against attacks using this technique.
Detect rundll32.exe loading remote DLLs from network drives
Category: Defense Evasion
MITRE ATT&CK® Technique: T1218.011
We’re happy to announce a new VTI that detects when the rundll32.exe tool is used to load and run files (DLLs) from remote network drives.
Rundll32.exe is a legitimate Windows utility that allows users to execute functions stored in dynamic-link libraries (DLLs). DLLs contain code and data that can be used by multiple applications simultaneously, and rundll32.exe provides a way to call functions within these DLLs directly from the command line. In normal cases, this tool helps run important system functions. However, it can also be exploited by attackers to run harmful code while appearing as a legitimate Windows process.
Why this is suspicious?
We recently observed a doubtful activity where rundll32.exe was used to load a DLL file from a network drive instead of the usual local system location (like C:\Windows\System32). This is unusual for several reasons:
- Normal behavior – Typically,
rundll32.exeloads DLLs from trusted, local directories. Loading a file from an external or network drive is not standard and could mean that an unauthorized source is trying to run code on your system. - Bypassing security – Running code from a remote drive might allow attackers to avoid traditional security tools, like antivirus software, because the malicious files aren’t directly stored on the victim’s machine.
- Risk of untrusted files – Remote drives, such as network shares, may not be as secure as local storage. If compromised, they could host untrusted or harmful code, increasing the risk of a malware attack.
To address this threat, we’ve introduced a new VTI that automatically detects when rundll32.exe is used to load DLLs from network drives.
Detect querying for Thunderbird profile information
Category: Credential Access
MITRE ATT&CK® Technique: T1555
In our arsenal, we already had a VTI capable of detecting attempts to read or search for sensitive email data. Now, we have expanded this capability to include attempts to access sensitive information stored in Mozilla Thunderbird, a popular and free email client. Thunderbird is widely used for managing emails, contacts, and calendars, and it supports multiple email accounts. Because of its widespread use, attackers may target Thunderbird to exploit sensitive data stored in user profiles.
Recently, we identified a suspicious sample trying to access Thunderbird profile information. These profiles contain data like email account settings, messages, and contacts, which could be valuable to attackers. Our new VTI triggers when malware attempts to search for or access Thunderbird profiles. For example, it will detect when suspicious code tries to locate files in the following directory:
C:\Users\<username>\AppData\Roaming\Thunderbird\Profiles\.
By detecting these attempts early, we can stop attackers from gaining access to your private email data. This detection aligns with MITRE ATT&CK® technique T1555, which refers to malicious actors trying to gather email-related data for their attacks.
YARA rules
, also known as phishing kits, are pre-packaged sets of tools used by cybercriminals to facilitate phishing attacks. These kits typically contain HTML pages, scripts, and resources needed to create a fake version of a legitimate website, like a banking portal or a social media login page. The goal of these phishing sites is to deceive users into entering sensitive information, such as usernames, passwords, or financial data.
are designed to make phishing attacks easy to execute, even for individuals with minimal technical skills. They usually include:
- Website templates – These mimic the look and feel of real, legitimate websites, making it difficult for victims to distinguish between fake and real sites.
- Form submission scripts – When a victim enters their credentials,
- Email templates – Some kits come with pre-written emails to lure victims, mimicking official communications from trusted organizations.
- Hosting instructions – Some kits provide instructions on how to host the phishing site, whether on compromised websites, free hosting services, or rented infrastructure.
In September, we’ve added new YARA rules to detect three types of PhishKits:
- PhishKit.MSDoc, is a specific type of phishing kit that uses webpages disguised as Microsoft Office files to deliver phishing attacks. These kits exploit users’ trust and familiarity with Office formats like Word, Excel, and PowerPoint documents. Attackers employ PhishKit.MSDoc to create phishing campaigns that lure users into interacting with maliciously crafted webpages, potentially leading to credential theft or other malicious activities.
- PhishKit.JSSlice, another type of phishing kit that primarily uses JavaScript to carry out its malicious activities. This kit leverages JavaScript slicing techniques to evade detection, create deceptive web pages, and steal sensitive information, such as login credentials or payment data, from unsuspecting users.
- PhishKit.EDG is a phishing kit designed to replicate email provider login pages. It pre-fills the login form with the victim’s email address and enhances the page’s authenticity by dynamically loading the favicon (e.g., Gmail) of the victim’s email provider. This tactic deceives users into thinking they are on a genuine email login page. The kit is named for the frequent appearance of “EDG” in its URLs.
New YARA rules for known anti-debugging and evasion techniques
In September, we introduced two new YARA rules to enhance our detection capabilities against emerging malware evasion techniques. These new rules focus on identifying behaviors that malware increasingly uses to probe the environment it is executing in, allowing it to evade detection and analysis—particularly in sandboxed environments or security tools.
1) Detecting Al-Khaser’s anti-debugging techniques
Most programs use these functions for legitimate purposes, such as ensuring they have sufficient memory for their operations. However, malware can abuse these functions to check if a security product is observing their behavior.
How malware abuses VirtualAlloc
A common tactic used by malware is to provide VirtualAlloc with invalid parameters. This technique allows malicious code to detect whether it is being debugged or analyzed. For example, by feeding VirtualAlloc unrealistic size values or conflicting flags, malware can provoke unusual responses that would not occur in a typical environment. This helps the malware determine if it is being observed, and, if so, it can choose to remain inactive, thereby avoiding detection.
One advanced technique involves using the MEM_WRITE_WATCH flag with VirtualAlloc. This flag allows malware to monitor changes to specific memory regions. If the malware detects unexpected modifications—such as a sandbox overwriting or observing its memory—it can alter its behavior or terminate itself, effectively evading analysis.
While VirtualAlloc is a tool designed for legitimate memory management, malware misuse of this function for evading sandbox and debugging checks is a sophisticated tactic. Our YARA rule is designed to detect these anomalies, helping security teams identify suspicious behavior early in the execution process.
2) Detecting evasion via Windows Defender AV emulator’s goat files
The second YARA rule is designed to detect attempts by malware to evade Windows Defender’s AV emulator, particularly by tracking its “goat files.” Recent research presented at the Black Hat conference shown that Windows Defender includes a built-in emulator for analyzing potential threats in a controlled environment. This emulator comes with a predefined file system, which includes numerous files known as “goat files.” These files are harmless and pre-created to simulate a typical Windows environment.
Some sophisticated malware families have begun to check for the presence of these goat files to determine if they are running inside the Windows Defender AV emulator. If these files are detected, the malware halts execution, thus avoiding analysis. Our YARA rule specifically monitors this behavior to catch instances where malware tries to evade Windows Defender’s built-in protections. By doing so, we can offer customers critical insights into evasive malware behavior.
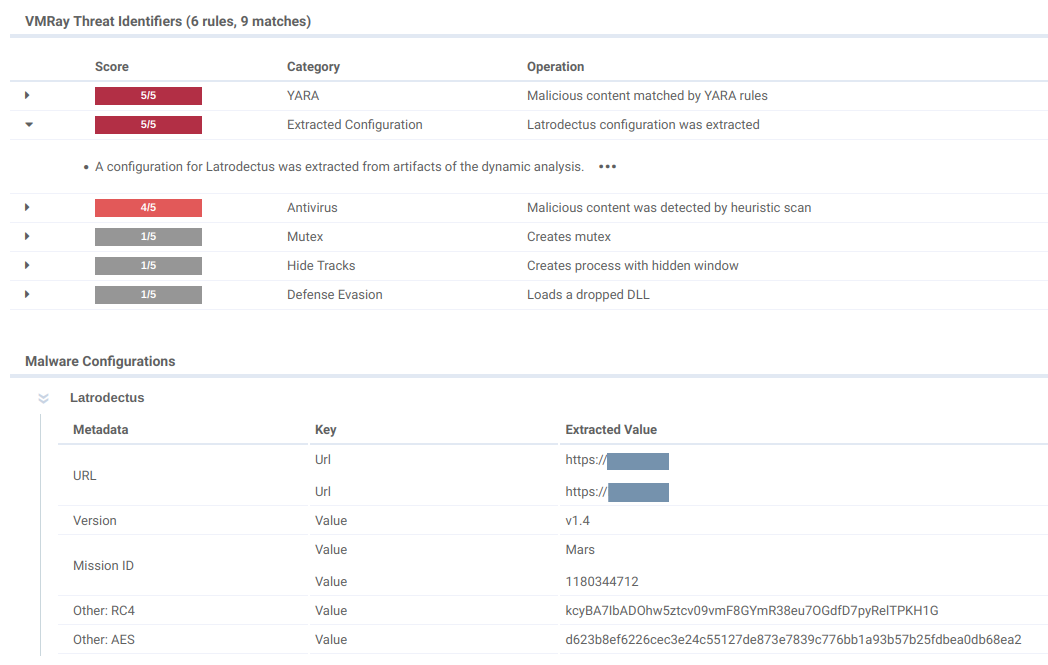
In our last blog post, we took a deep dive into what configuration extraction is and how it works. If you’ve been following along, you know we recently rolled out a config extractor for Socks5Systemz—but we’re not stopping there. This month, we’re excited to announce that Latrodectus is now on board for configuration extraction.
Latrodectus is a highly active downloader, often seen as the next evolution of the infamous IcedID loader. It’s been making waves for a while, and with the release of Latrodectus version v.1.4, we’ve seen some major updates. One standout change? The switch to (CTR mode) encryption to secure its internal strings. This is a big deal, and we’re happy to offer configuration extraction for this evolving threat.
What is AES-256 encryption? AES-256 (Advanced Encryption Standard) is a highly secure method of encrypting dataThis encryption standard is widely trusted and used by governments and industries globally to protect sensitive data because of its strength and reliability. In the case of Latrodectus, the malware uses AES-256 to hide critical data, making it more difficult for security tools to detect and analyze the threat.
With the addition of Configuration Extraction for Latrodectus v.1.4, our Platform can now automatically decode and extract the hidden configurations—even those protected by AES-256 encryption. This new capability enhances our coverage of the malware, combining both YARA-based detection and detailed configuration extraction to provide a more complete threat profile.
We hope our ongoing research into emerging malware trends and the new features we’re adding to our products help you tackle the world of cybersecurity with confidence. With the latest updates—like new Windows VTIs to disable notifications, YARA rules that spot phishing kits, and the advanced config extractor for the Latrodectus malware family—you’ve got some serious tools at your disposal.
We’re always on the lookout for the latest threats, and we’ll be bringing you more updates and insights in the weeks ahead. Until then, wishing you a safe and enjoyable fall season!
如有侵权请联系:admin#unsafe.sh