As more organizations shift their workloads to the cloud, securing these environments becomes critical. Cloud misconfigurations, such as exposed storage buckets or improper access controls, have become a significant source of vulnerabilities, increasing the risk of data breaches. Key to controlling these digital threats is a proper CSPM (Cloud Security Posture Management). What is CSPM? Keep reading. In this blog, we'll explore what CSPM is, its key capabilities, and its role in protecting cloud infrastructures from common misconfigurations. Whether you're looking to understand CSPM's meaning, its role in cloud security, or how it compares to other tools like CNAPP, this blog will equip you with the knowledge to enhance your cloud security posture and prevent common pitfalls. As organizations increasingly adopt cloud infrastructure, Gartner highlights the need for Cloud Security Posture Management (CSPM) to address configuration vulnerabilities. CSPM tools are designed to automatically detect misconfigurations, compliance violations, and other security risks across IaaS, PaaS, and SaaS environments. By providing continuous visibility and monitoring, CSPM ensures that cloud resources align with best practices and regulatory standards, significantly reducing the risk of breaches. As Gartner rightly say, this proactive approach helps organizations maintain a secure and compliant cloud environment as it scales and evolves. CSPMs are so critical right now because of the rising threat of ransomware, and related malicious phenomena. The global cost of ransomware is projected to reach $10.5 trillion annually by 2025, an increase from $6 trillion in 2021. These costs are due to lost data, downtime, and ransom payments. The level of sophistication and lucrative operation of ransomware cybercrime is compounding at a rate that’s never been seen before - and even more exponentially amidst the chaos of the COVID-19 pandemic and its disorienting effect on the healthcare industry. As of 2023, ransomware continues to be a major threat in the healthcare sector. Over 141 hospitals were directly impacted by ransomware attacks this year, underscoring how cybercriminals increasingly target critical healthcare systems. These attacks not only disrupt essential services but can also compromise sensitive patient data. Additionally, the FBI reported that cybercrime losses, driven in part by ransomware, reached a staggering $12.5 billion. “Pharmaceuticals, hospitals, healthcare, public companies, organizations that don’t have the talent and skills to defend themselves - they’re getting sucker- punched.” - Kevin Mandia As organizations continue to transition into the cloud to scale operations and enable remote work, improper cloud configurations have emerged as one of the biggest global threats to business security. These misconfigurations create vulnerabilities that cybercriminals, including ransomware operators, are quick to exploit. Addressing these weaknesses through proper configuration is critical to avoiding data breaches and other major security incidents. Cloud Security Posture Management targets failures at their root, focalizing an organization's cloud configuration. Previously known as Cloud Infrastructure Security Posture Assessment, CSPM was defined in response to the growing need of organizations to correctly configure public cloud Iaas, PaaS services and remediate cloud risk. CSPM uses automation to identify and remediate vulnerabilities within cloud infrastructures, and is known for its risk visualization and assessment, incident response, compliance monitoring, and DevOps integration enablement. Notably, CSPM is able to uniformly apply best practices for cloud security against hybrid, multi-cloud, and container environments. With the dynamic nature of cloud environments, number of connected resources, and API driven approaches to integration, misconfigurations can easily be made. Cloud-based services include many moving parts, and when compounded with the lack of active observability lessen an organization's ability to discover and address configuration gaps. Accidentally granting public access to storage buckets or containers within the cloud that are otherwise assigned individually to storage classes is a common misconfiguration with considerable risk. Like an unlocked house, storage buckets that are left open are susceptible to attack by anyone who discovers them. Automated detection and remediation: CSPM tools quickly identify misconfigurations and remediate security issues in real time. Best practices inventory: CSPM maintains an inventory of best practices tailored to different cloud configurations, ensuring uniform security. Configuration status mapping: This links cloud configurations to a security control framework or regulatory standard, streamlining compliance efforts. Storage bucket monitoring: CSPM monitors cloud storage, ensuring encryption and access permissions are properly configured to reduce compliance risks. With the scope of an organization's due diligence advancing and complexifying with every new cybercrime event, having a strong offensive stance that can detect and respond at the tempo necessary is a task that only Cloud Security Posture Management has proven to deliver. When it comes to Cloud Security Posture Management (CSPM), Uptycs offers a unified platform that simplifies cloud security for hybrid, multi-cloud, and container environments. Our CSPM provides enhanced visibility across all cloud resources—whether they are in IaaS, PaaS, or SaaS environments—allowing organizations to detect and automatically remediate misconfigurations and vulnerabilities. By aligning cloud configurations with industry standards and regulatory requirements, we help reduce the risk of data breaches, ensuring that your cloud environment remains secure and compliant. By combining workload protection, security posture management, and threat detection into one unified platform, we deliver a holistic approach to cloud security, empowering your team to respond quickly and confidently to emerging threats. Read more about best practices and fundamentals with our FREE Cloud Strategy Guide below:Gartner’s CSPM Meaning
Cloud Misconfigurations: The Weak Link, and an Invitation to Ransomware
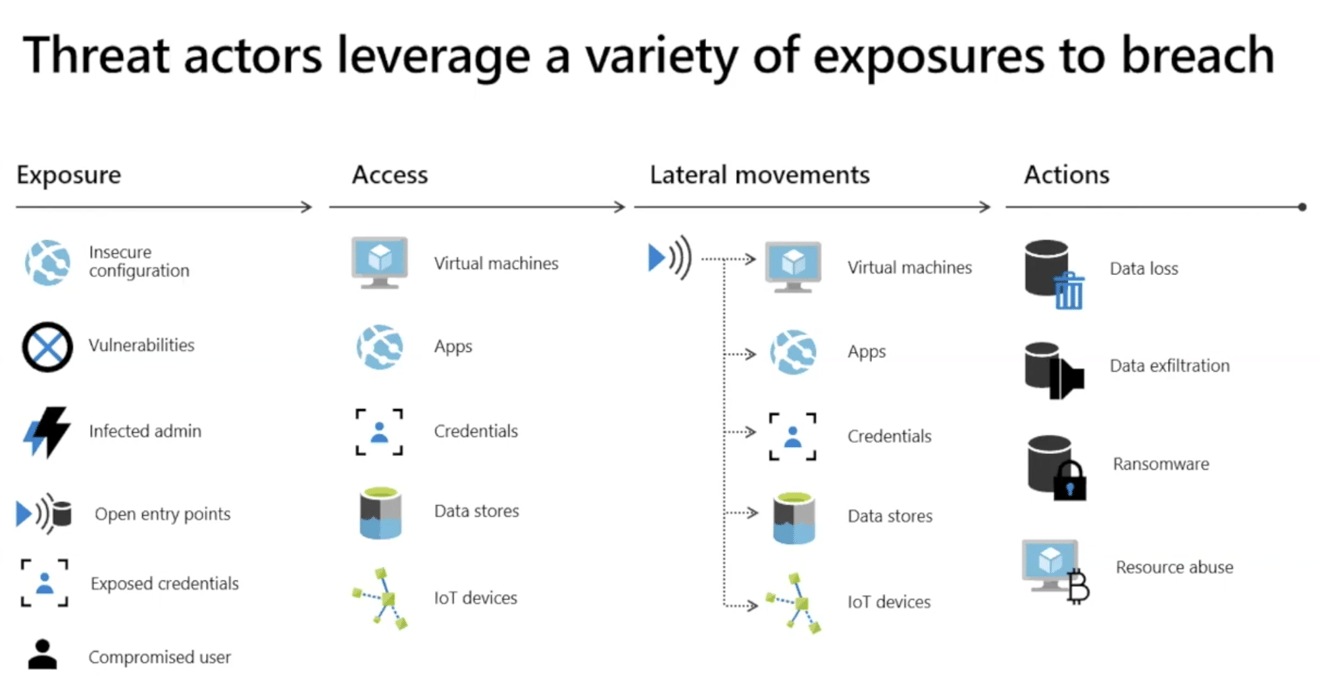 Image provided by Sans
Image provided by SansHow Cloud Security Posture Management Can Help
The Key CSPM Capabilities
Strengthening Your Cloud Security Posture with Uptycs

文章来源: https://www.uptycs.com/blog/what-is-cspm-cloud-security-posture-management
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh
