2024-10-11 03:16:47 Author: stalkphish.com(查看原文) 阅读量:10 收藏
Since last summer, StalkPhish.io, our advanced platform dedicated to combating bank fraud, phishing, and scams, has been upgraded with a system for classifying phishing kits. This enhancement allows us to effectively categorize phishing kits collected through our infrastructure, bringing a new level of insight and prevention for businesses facing phishing threats.
PhishingKit-Yara-Rules: An Open Source Initiative
At the heart of this system is the PhishingKit-Yara-Rules project, an open-source initiative developed by StalkPhish. We’ve made this project freely accessible to the public under an open-source license, enabling companies and security professionals to integrate these tools into their own systems.
By leveraging Yara rules, a popular tool for identifying and classifying malware, the platform classifies phishing kits automatically as they are downloaded. These Yara rules allow for quick identification of phishing kits, helping users stay ahead of malicious actors.
What are Phishing Kits
The StalkPhish.io platform – in addition to its various detection functions – is designed to harvest the sources of phishing kits when they are available and left accessible (hidden or not) by the threat actor.

These phishing kits reveal a great deal of information about the threat, whether it’s the threat itself: the usurped brand, the harvested data, the exfiltration vectors for stolen data, etc.
Or the different ways of detecting the kits and paths used by this kit, which is very useful for detecting deployed URLs using the same phishing kit. At StalkPhish, we regularly analyze the kits we’ve collected in order to share our expertise in this field.
Insightful Analysis via PhishingKit-Yara-Rules
The PhishingKit-Yara-Rules project is a powerful public resource aimed at companies and cybersecurity experts. It offers a comprehensive set of Yara rules designed to identify phishing kit sources, with over a hundred new phishing kits analyzed daily by StalkPhish.io.
One of the key benefits of these rules is that they operate solely on the headers of ZIP files containing phishing kits, such as file paths, names, and directories within the archive. This approach enables quick analysis without the need to decompress or open the files, saving time and resources.

For example, when a Yara rule detects a phishing kit designed to impersonate a major financial institution, our system flags this activity, allowing rapid classification and response.
For more details, see the video presentation of StalkPhish projects at the Pass The Salt 2024 conference: https://passthesalt.ubicast.tv/videos/2024-hunt-for-phishing-urls-scammers-and-their-materials/ where Thomas Damonneville presents several free and open-source tools dedicated to detection and investigation on phishing.
Integration into StalkPhish.io
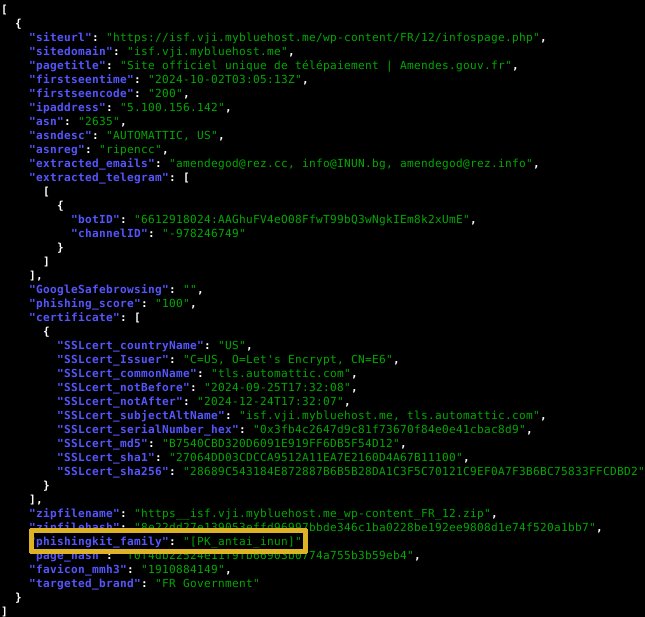
The data is available via the StalkPhish.io REST API: the API generates a JSON stream where you can find all the information collected, enriched and analyzed by the StalkPhish.io backend. We’ve recently added the “phishingkit_family” JSON key:

This JSON key contains the name(s) of the Yara rule(s) triggered when analyzing the sources of the harvested phishing kit. The advantage of such information is that it enables our customers to quickly assess the threat detected and the brand impersonated.
Knowing the phishing kit involved not only allow you to learn more about the threat, as seen above, but also to pivot on the campaign. For example, now that you know the Yara rule, you could use it to find out if other campaigns have been detected, where and when, as some internal portals or applications allow this kind of retro-hunting.
About Stalkphish
We propose free, open source and downloadable tools, mainly focused on anti-phishing and brand identity theft (StalkPhish OSS, PhishingKit-Yara-Rules, PhishingKitHunter), check our dedicated page.
We provide enriched data related to these massive phishing campaigns, through our StalkPhish.io REST API, dedicated to digital detection and investigation of actors and their infrastructures.
Also, we regularly share knowledge and analysis of phishing kits on our StalkPhish.com (this) blog.
You can contact us for more information via our contact page.
如有侵权请联系:admin#unsafe.sh