2024-10-11 21:0:0 Author: www.tenable.com(查看原文) 阅读量:7 收藏
More security teams are incorporating AI to uplevel their defense strategies and boost productivity. With so much AI buzz, it may be overwhelming to decipher which tools to acquire and how they fit in a modern security strategy. Read on to explore how AI-enabled tools can help enhance your security program in this special edition of the Tenable Cybersecurity Snapshot!
It’s clear that artificial intelligence (AI) has the potential to transform security operations by helping organizations move from traditional defense mechanisms to proactive and real-time threat detection. In essence, the role of AI in modern cybersecurity involves integrating advanced technologies to more quickly and precisely predict, identify and mitigate threats before they cause harm.
Today, with the rise of cloud environments, the convergence of IT and operational technology (OT), generative AI-enhanced exploits and phishing lure content, the attack surface has ballooned. As a result, cybersecurity teams are looking beyond traditional methods and embracing AI security solutions to protect sensitive data.
In fact, the recent “State of AI and Security Survey Report” from the Cloud Security Alliance (CSA) reveals a majority of security professionals (63%) believe in AI’s potential to enhance security measures.
How strongly do you agree or disagree with the following statement: AI will improve security within our organization.

(Source: “State of AI and Security Survey Report” from the Cloud Security Alliance, April 2024)
The study, based on a survey of 2,500 IT and security pros, also found that 67% of respondents say they have tested AI specifically for security purposes, and 48% say they are either “very” or “reasonably” confident in their organizations’ ability to use AI for security successfully.
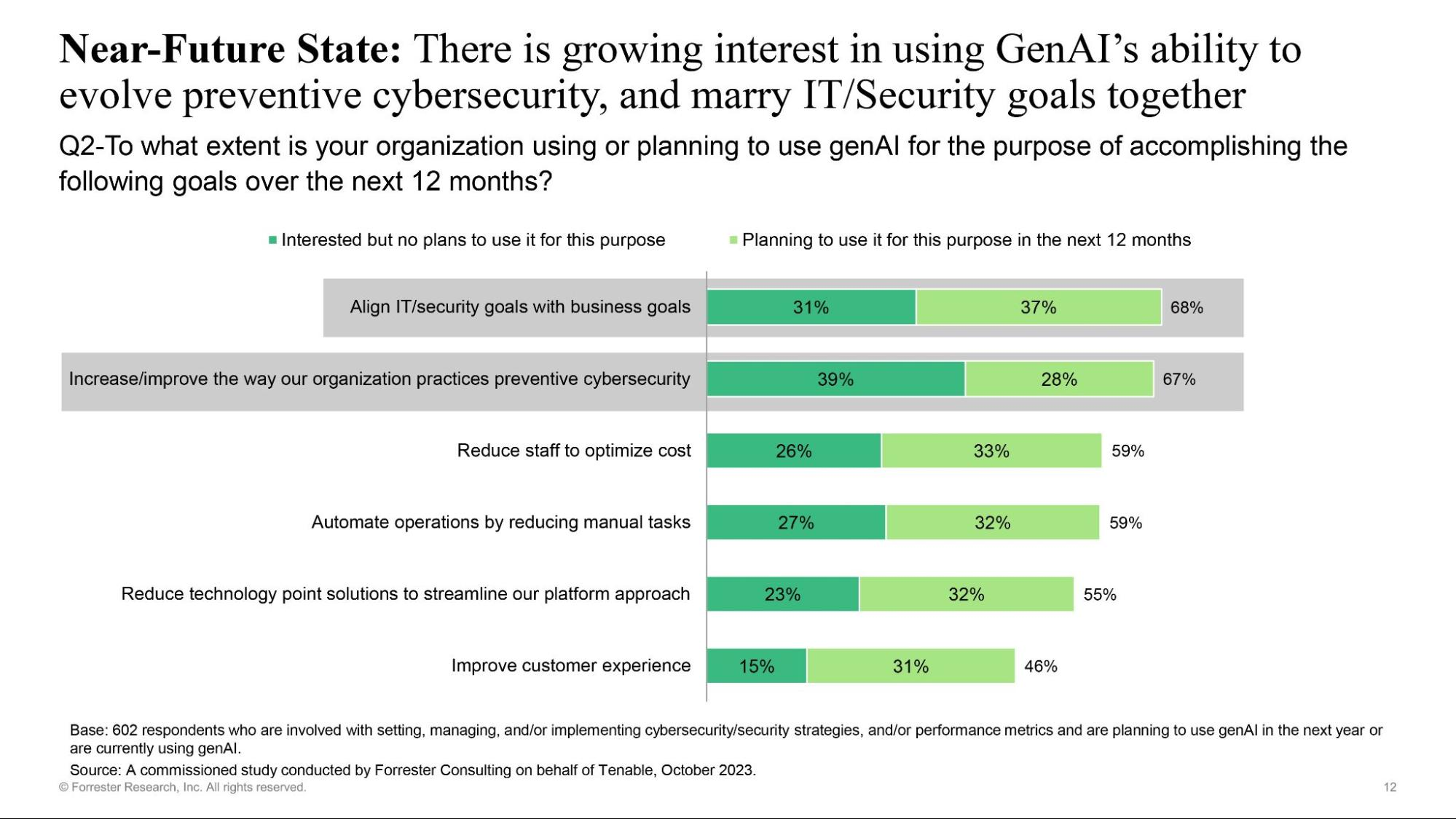
Meanwhile, in a commissioned study conducted by Forrester Consulting on behalf of Tenable in October 2023, 44% of IT and security leaders polled said they were either “extremely confident” or “very confident” about their ability to use generative AI to enhance their organization’s cybersecurity strategy.

Furthermore, 68% of respondents showed some level of interest in using GenAI to align IT/security goals with business goals; and a similar number – 67% – showed interest in using it to increase or improve the way their organization practices preventive cybersecurity.

So how is AI being put to use in security programs? How has generative AI affected security? In this special edition of Cybersecurity Snapshot, we examine a few of the ways AI can enhance your cybersecurity strategy.
1 - Better real-time threat detection
AI has greatly impacted real-time threat detection by analyzing large datasets at unmatched speeds and identifying subtle, often-overlooked, changes in network traffic or user behavior. For example, AI can detect when an employee’s account displays unusual activity or when a system accesses sensitive data that it typically wouldn't. Traditional tools may miss these nuanced anomalies, but AI systems are adept at spotting them.
“For security, GenAI can revolutionize the field if applied correctly, especially when it comes to threat detection and response. It enhances efficiency and productivity by swiftly processing and delivering critical information when it matters most,” Nicholas Weeks, a Tenable senior product marketing manager, wrote in a recent blog post.
One of AI's significant advantages in threat detection is its ability to be proactive. AI-powered systems continuously refine their algorithms as new malware strains and attack techniques emerge, learning from each event and integrating new insights into their threat detection mechanisms. This allows them to respond to both known and unknown threats more effectively than traditional, static, signature-based tools.

"There has been automation in threat detection for a number of years, but we're also seeing more AI in general. We're seeing the large models and machine learning being applied at scale," Josh Schmidt, partner in charge of the cybersecurity assessment services team at BPM, a professional services firm, told TechTarget.
In addition to monitoring internal network behavior, AI systems can more comprehensively analyze external sources of intelligence like RSS feeds, cybersecurity forums and global threat data. This wide-reaching capability helps AI gather actionable insights and recommend defense strategies that are tailored to current attack trends. For example, AI can flag a spike in phishing attacks targeting specific industries and suggest measures to counter these emerging threats.
Additionally, as AI-generated phishing lures become nearly impossible for humans to detect, researchers and operators are turning to AI-based systems to assess if an email was AI-generated by looking for subtle telltales or differences when compared to a legitimate human-sourced email.
2 - Improved automated response and mitigation
AI's capability to automate responses to detected threats drastically reduces the time between identifying an anomaly and taking action. Once a threat is detected, AI-driven systems can autonomously recommend or execute mitigation steps. This may include isolating compromised systems or blocking malicious traffic — actions that minimize human intervention and reduce the risk of manual errors.
“As AI-driven incident response automation capabilities grow more sophisticated, tools will likely get better at recognizing and responding to atypical behavior without immediate human intervention — even for zero-day threats,” reads TechTarget’s article “Incident response automation: What it is and how it works.”
In SANS Institute’s “SANS 2024 AI Survey: AI and Its Growing Role in Cybersecurity: Lessons Learned and Path Forward,” automated incident response ranked third among the top cybersecurity areas in which organizations are using AI, cited by 49% of respondents.
Key Areas of AI Usage

(Source: SANS Institute’s “SANS 2024 AI Survey: AI and Its Growing Role in Cybersecurity: Lessons Learned and Path Forward,” September 2024)
The benefit of AI in automated response is evident in its speed. AI can isolate a compromised system in seconds, preventing the lateral movement of an attacker within the network — a tactic cybercriminals frequently use to escalate breaches. Acting as an automated first responder, AI can handle incident responses far quicker than any human team, ensuring the organization’s operations continue with minimal disruption.
“AI systems are … capable of automatically responding to detected threats 24/7, implementing countermeasures around the clock and reducing the window of opportunity for attackers,” reads AI Business’ article “AI in Cybersecurity: Understanding the Digital Security Landscape.”
Predefined playbooks for handling various types of incidents, like ransomware or phishing attacks, can also be integrated into AI-driven response systems. These playbooks ensure that the correct steps are taken in a consistent manner, reducing the possibility of human errors during a crisis. In large-scale environments, where multiple incidents may occur simultaneously, AI’s ability to handle multiple threats concurrently ensures quicker resolutions and more robust defenses.
AI-driven automation is still nascent. However, it has the potential to have a major impact on incident response.
“AI-driven automation is a game-changer for security incident response. It swiftly isolates compromised systems, blocks malicious traffic, and initiates remediation steps. This automation reduces manual intervention, ensuring a rapid, effective security event-driven response,” reads Techopedia’s “AI and Cybersecurity: Accelerate Your Defenses in 2024” article.
3 - Predictive analytics transformation
One of AI’s most powerful features is its ability to predict future threats, transforming how security teams allocate resources and prioritize their actions. In the aforementioned “SANS 2024 AI Survey,” 42% of respondents said their organizations are applying AI to predictive threat intelligence.
Predictive models, such as Tenable's Vulnerability Priority Rating (VPR), use machine learning to anticipate which vulnerabilities are most likely to be exploited within a specific timeframe, such as the next 28 days.
This foresight empowers security teams to focus their patching and mitigation efforts on the most critical vulnerabilities, ensuring that resources are used efficiently. By analyzing vast amounts of historical and real-time data, including cybersecurity news, forums, and threat intelligence, AI can provide summarizations and insights into emerging vulnerabilities. This allows for a proactive approach to threat management, enabling organizations to address vulnerabilities before they are actively exploited.

“AI and ML algorithms can predict potential threats, allowing organizations to take proactive measures to prevent attacks. Predictive analytics enable organizations to identify vulnerabilities, prioritize patching and remediation efforts, and optimize security resources,” reads the article “The Impact of Artificial Intelligence and Machine Learning on Cyber Security” from the Association for Advancing Automation.
AI automates the prediction and identification of vulnerabilities, shifting the security posture from reactive to proactive, helping organizations to stay ahead of attackers and reduce the time and cost associated with mitigating lower-priority vulnerabilities.
“AI can analyze historical data and identify patterns to predict future threats, enabling proactive defense and more effective resource allocation,” reads the article “5 Ways AI Enhances Cybersecurity” from Acceleration Economy.
4 - Clearer, more insightful attack path analysis
AI has also transformed attack path analysis by enhancing the process and providing key insights and support that help security teams act more effectively and efficiently.
AI plays a critical role in summarizing attack paths, offering high-level overviews that simplify how an attacker could potentially exploit vulnerabilities within a network. These summaries are designed to make the information accessible, highlighting how assets, exposures, and tactics, techniques, and procedures (TTPs) might be leveraged by attackers. This is particularly helpful for decision-makers who may not have deep technical expertise but need a clear understanding of risks.
AI also provides mitigation guidance once the top attack paths have been identified through traditional analysis. By suggesting specific steps to mitigate these risks, AI helps security teams close gaps more quickly, ensuring a proactive approach to threat defense.
AI also acts as an interactive assistant, offering a virtual "mini security analyst" that can answer questions about the attack path or provide further details on individual steps. This AI assistant helps bridge the gap between complex attack path models and the actionable insights security teams need to improve their defenses.
AI complements attack path analysis by offering easy-to-understand summaries, actionable mitigation guidance, and real-time support, empowering security teams to stay one step ahead of potential threats.
To get more information, check out these two videos from Tenable:
Summarizations with AI in Tenable Attack Path Analysis
Mitigation Guidance with AI in Tenable Attack Path Analysis
5 - Stronger exposure management
AI in exposure management involves continuously monitoring an organization’s attack surface in real-time to identify vulnerabilities as they emerge. Unlike predictive analytics, which forecasts future threats, exposure management focuses on real-time detection and dynamic defense adjustments. AI can monitor system configurations, network activity, and threat intelligence feeds, providing immediate feedback on potential weaknesses.
“AI can process massive amounts of data in real time, detecting threats early and reducing potential damage. AI can identify new and evolving threats more effectively than manual methods,” wrote Kenny Mullican, CIO of Paragon Films, in the article “From Malware Detection to Predictive Analytics, 5 Ways AI Enhances Cybersecurity.”
“As a CIO with a small staff, I need the cybersecurity software we use to constantly adapt to the threat landscape automatically, without my team having to constantly configure it,” he wrote.

Incorporating AI into exposure management allows for adaptive security measures that change based on new threats. For example, if AI detects a suspicious event, it can automatically tighten access controls or adjust firewall settings, ensuring that defenses are continually optimized to meet evolving risks. By allocating resources efficiently, AI ensures that critical vulnerabilities are addressed quickly, helping to maintain a strong and resilient security posture.
“AI-driven systems excel in identifying anomalies and detecting unseen attack patterns, mitigating potential risks before they escalate. For instance, real-time intelligence can be used by AI algorithms to monitor networks in real-time and accurately defend against threats as they emerge, reducing the occurrence of false positives,” reads the World Economic Forum article “The double-edged sword of artificial intelligence in cybersecurity.”
“We believe the future of preventive security is Exposure Management, powered by AI,” wrote Nate Dyer, Senior Director of Product Marketing at Tenable, in a blog.
VIDEO
Making Decisions Easier with AI
6 - Streamlined incident response planning
Incident response planning, often a time-consuming process, is being streamlined by AI tools capable of analyzing historical incident data and suggesting optimized playbooks for future incidents. AI-generated playbooks offer a solid foundation for building effective response strategies, and the ability to process vast amounts of data ensures that the responses are timely and accurate.
For example, AI can triage alerts, isolate compromised systems, and block malicious traffic in real time, while also initiating forensic investigations to understand the scope of the breach. Human oversight remains essential, but AI drastically reduces the time between detecting an incident and taking action, minimizing potential damage. AI also automates communication during incidents, providing real-time updates to stakeholders and ensuring a coordinated response.
To learn more about AI security, check out these Tenable resources:
- “Introducing ExposureAI in Tenable One: Meet the Future of Preventive Cybersecurity” (blog)
- “How Generative AI Is Changing Security Research” (research report)
- “AI Is About To Take Cybersecurity By Storm: Here's What You Can Expect” (blog)
- “Predicting Risk and Exposure: Harnessing AI and Machine Learning in Tenable Security Center” (on-demand webinar)
VIDEOS
Tenable CEO Amit Yoran discusses AI and preventive security on CNBC
How Generative AI is Changing Security Research: The Development of the G-3PO Tool
如有侵权请联系:admin#unsafe.sh