
2024-10-15 13:32:44 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
DDoS botnet gained attention a few years ago due to its record-breaking attacks, but the emergence of new threats in 2024 illustrates the evolving tactics of cyber attackers. The cyber threat landscape is in constant flux, with vulnerabilities like Zyxel’s CVE-2023-28771 being exploited and MySQL servers coming under fire from variants like Ddostf and Mirai’s IZ1H9.
Complicating matters further, researchers identified new DDoS botnets linked to the Mirai source code in September 2023. Among these, hailBot, kiraiBot, and catDDoS have gained prominence, showing increased activity and spreading rapidly.
What is DDoS Botnet?
A botnet is a collection of computers infected by malware and controlled by a malicious actor. The term “botnet” combines the words “robot” and “network,” with each infected device referred to as a “bot.” Botnets can be used for various illegal or malicious activities, such as sending spam, stealing data, conducting ransomware attacks, fraudulently clicking on ads, or executing distributed denial-of-service (DDoS) attacks.
While certain types of malware, like ransomware, directly impact the device owner, DDoS botnet malware can vary in visibility. Some malware takes full control of a device, whereas others operate silently in the background, awaiting instructions from the attacker or “bot herder.”
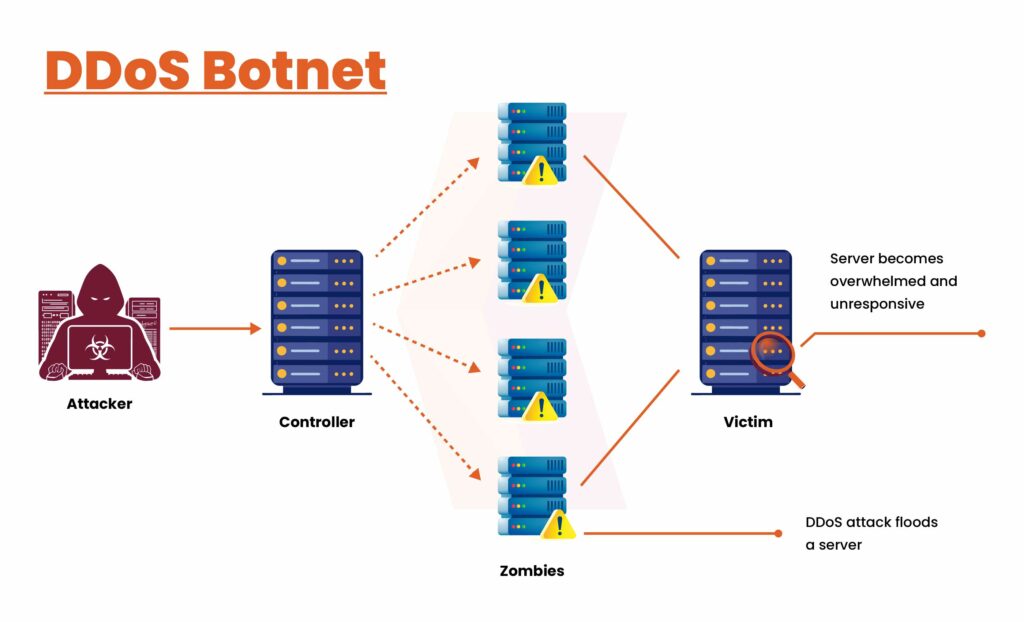
Self-propagating botnets expand their reach by recruiting additional bots through various channels. Infection pathways include exploiting website vulnerabilities, deploying Trojan horse malware, and cracking weak authentication to gain remote access. Once access is achieved, these methods lead to the installation of malware on the target device, allowing the botnet operator to gain remote control. After infection, the device may attempt to spread the botnet malware by recruiting other devices within its network.
Bot Attacks: An Ongoing Evolving Threat
As attacks on APIs increase, bot attacks have emerged as a widespread and costly threat, leading to annual losses of up to $116 billion. Bots—automated software programs designed for specific tasks—are often weaponized for malicious purposes, including credential stuffing, web scraping, online fraud, and distributed denial-of-service (DDoS) attacks.
In 2022, incidents related to bot attacks rose by 88%, followed by an additional 28% increase in 2023. This alarming trend is driven by various factors, including the growth of digital transactions, the proliferation of APIs, and geopolitical tensions like the Russia-Ukraine conflict. The widespread availability of attack tools and generative AI models has also significantly improved bot evasion techniques, enabling even less-skilled attackers to execute sophisticated bot attacks.
According to Imperva, bots now pose one of the most significant threats to API security. Last year, 30% of all API attacks were attributed to automated threats, with 17% specifically linked to bots exploiting business logic vulnerabilities. The increasing dependence on APIs—and their direct access to sensitive information—has made them prime targets for bot operators. Automated abuse of APIs alone is costing businesses as much as $17.9 billion annually. As bots grow more sophisticated, attackers increasingly use them to exploit API business logic, circumvent security measures, and exfiltrate sensitive data, making detection and mitigation increasingly difficult for organizations.
How Does DDoS Botnet Attack Happen?
This process consists of several stages. When utilized to their full capacity, botnets can execute large-scale attacks. Hackers often need to support a botnet with additional machinery or devices to enhance its capabilities. To gain a deeper understanding of how botnets operate, it’s essential to familiarize oneself with key terminologies.
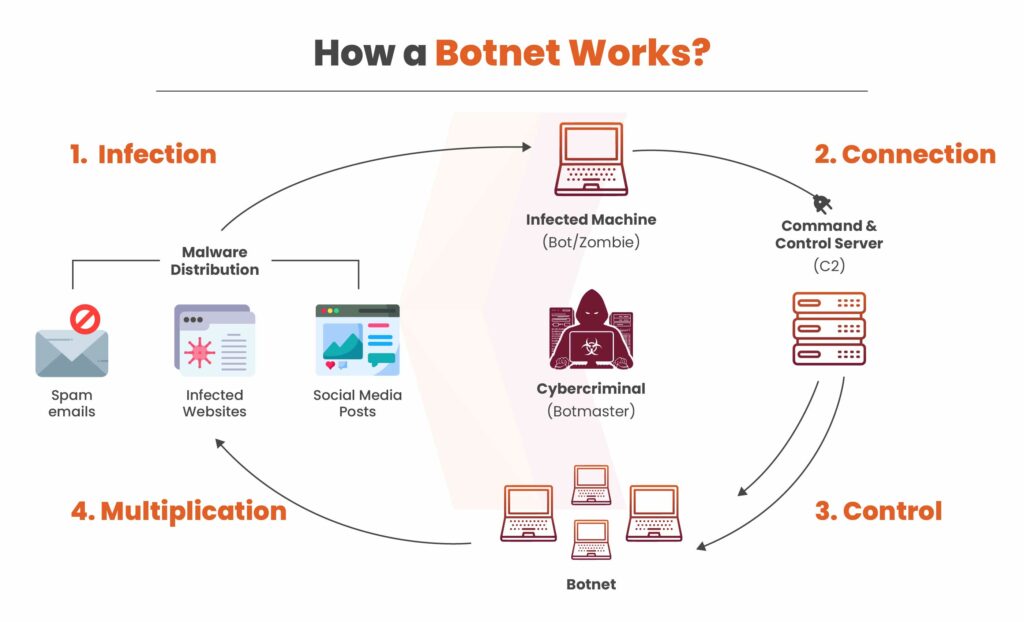
A DDOS bot herder is necessary to manage the network of connected infected devices. It operates through remote commands, directing the devices to perform specific actions.
The term bot or zombie computer refers to the infected system or device that contributes to the formation of a botnet. These bots operate without independent thought, following the commands given by the bot herder.
What Purposes DDoS Botnet Servers?
Depending on the attackers’ intent, botnets can be extensively used to achieve goals related to money or data theft. The most common application of DDoS botnets is described as follows:
Fraudulent Activities Or Financial Theft
Botnets can be used to steal money both directly and indirectly. Common methods include sending phishing emails or creating fake banking websites to deceive users. Attackers can intercept payment or transaction details and use them to commit financial theft.
Data Theft
User data holds significant value in the market, and hackers use DDoS botnets to steal personal information or breach enterprise databases. They then sell this stolen data to third parties for profit. These botnets often remain dormant, silently collecting sensitive information.
Perform Spamming and Phishing Frauds
Bad actors can leverage botnets to launch large-scale email spamming and phishing campaigns, distributing infected emails to millions of targets at once. Specialized spam DDoS botnets are designed specifically for this task.
Regardless of the technique used, the objectives are usually the same—stealing money or data. However, some attackers deploy botnets simply to showcase their skills. In many instances, we’ve seen security breaches where hackers steal enterprise data and expose it on the dark web for free to demonstrate their capabilities.
Strategies for Detecting and Mitigating Botnet Attacks
To effectively combat botnet attacks, organizations should implement the following key strategies:
Get Insight Into Botnet Infiltration
Understanding how botnets infiltrate systems and gain control for malicious purposes is essential. Your device can become infected by visiting a malicious website that automatically downloads malware without your consent.
Additionally, downloading files from seemingly reliable sources, such as email attachments, can inadvertently introduce malware, functioning as trojans. Botnets also target unprotected devices, including everything from baby monitors to computers, by exploiting weak passwords. Even seemingly harmless devices like internet-connected toasters can be quickly compromised by botnets, resulting in significant cyberattacks.
Resetting of Devices
Resetting your device to eliminate a botnet can be a simple process, despite the potential damage it may cause.
Here’s how to go about it:
- Backup Your Data: Protect your important files by backing them up to the cloud before taking any steps.
- Reset to Factory Settings: Restore your device to its factory settings to remove any traces of the botnet. This action can effectively eliminate botnets like Mirai.
- Reset Routers and Equipment: Ensure your routers and other wireless devices are also free of any botnet infections by resetting them as well.
- Change Default Passwords: Enhance your security by changing default passwords to strong and unique ones.
- Monitor for Unusual Activity: Stay alert for any strange behavior on your devices, which could suggest that a botnet is attempting to reinstall itself.
Installation of Patches
Your devices, applications, and operating systems consistently remind you to update for a good reason. These new patches aren’t just optional but crucial for your digital security.
Hackers frequently take advantage of known vulnerabilities to develop a breach in systems. Device manufacturers issue patch updates to defend against known hacks or botnets targeting their products. Make it a habit to regularly update your devices, software, and apps. Stay aware of the latest app vulnerabilities that may affect your systems and business. It’s also important to perform vulnerability testing to pinpoint potential entry points for hackers.
Book a Free Consultation with our Cyber Security Experts

Conclusion
The threat posed by DDoS botnets remains significant and complex. As these malicious networks grow more sophisticated, understanding their mechanisms and potential impacts is crucial for organizations. DDoS botnets not only facilitate financial theft and data breaches but also enable large-scale spam and phishing campaigns that can undermine trust and security.
To effectively defend against these threats, organizations must prioritize proactive measures, including regular updates, robust security protocols, and vigilant monitoring of network activity. By implementing strategies to identify and mitigate botnet attacks, businesses can safeguard their systems and data from potential harm. Ultimately, a comprehensive understanding of how DDoS botnets operate—and the strategies to combat them—will empower organizations to navigate the challenges of cybersecurity and maintain a secure digital environment.
As a CERT-In empanelled organization, Kratikal is equipped to enhance your understanding of potential risks. Our manual and automated Vulnerability Assessment and Penetration Testing (VAPT) services proficiently discover, detect, and assess vulnerabilities within your IT infrastructure. Additionally, Kratikal provides comprehensive security auditing services to ensure compliance with various regulations, including ISO/IEC 27001, GDPR, PCI DSS, and more, assisting your business in adhering to legal requirements set forth by diverse governments.
FAQs
- What is DDoS Botnet network?
A bot network, commonly known as a botnet, consists of thousands or even millions of machines, computers, and Internet of Things (IoT) devices. These devices are coordinated to carry out various types of attacks, such as large-scale distributed denial-of-service (DDoS) campaigns and credential stuffing attacks.
- Can botnet steal data?
Botnets are used for a variety of malicious activities, including sending spam, data theft, and ransomware attacks. They can also be deployed for fraudulent ad clicks or to launch distributed denial-of-service (DDoS) attacks.
- How big is Botnet?
Attackers leverage the combined power of these networks to carry out disruptive activities. These activities include sending massive volumes of spam, spreading malware, and launching Denial-of-Service (DoS) attacks.
The post How DDoS Botent is used to Infect your Network? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/how-ddos-botent-is-used-to-infect-your-network/
如有侵权请联系:admin#unsafe.sh

