2024-10-15 16:13:2 Author: perception-point.io(查看原文) 阅读量:3 收藏
The NIS 2 Directive, set to take effect on October 17th, 2024, represents a significant shift in EU cybersecurity regulations. Designed to improve resilience across key sectors, NIS 2 introduces new obligations for all types of businesses.
Here’s what you need to know about its goals, its broad impact, and the key steps your organization should take to ensure compliance.
For example, small and medium-sized businesses (SMBs) that may not have extensive cybersecurity resources will need to adjust to the directive’s stricter reporting requirements. A cyber incident that goes unreported within the required 24-hour window could result in fines of up to €10 million or 2% of global turnover, alongside potential reputational damage. This creates a need for robust incident response capabilities across all sectors.
With the deadline approaching, organizations of all sizes should review and enhance their cybersecurity frameworks, incident response capabilities, and supply chain security to ensure compliance with NIS2’s requirements.
The Aims of NIS 2: Strengthening Cyber Resilience and Standardizing Cybersecurity Across the EU
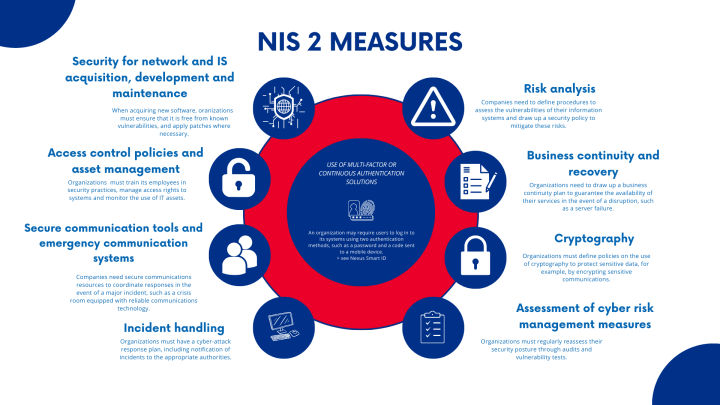
The directive’s primary objective is to strengthen cybersecurity across the EU by ensuring that organizations can effectively protect themselves against the growing number and sophistication of cyber threats.
NIS 2 aims to:
- Enhance cyber resilience across critical sectors.
- Reduce inconsistencies in cybersecurity standards between EU member states.
- Improve incident reporting and ensure rapid responses to cyber incidents
Who Must Comply with NIS2? Understanding the Impact Across Industries
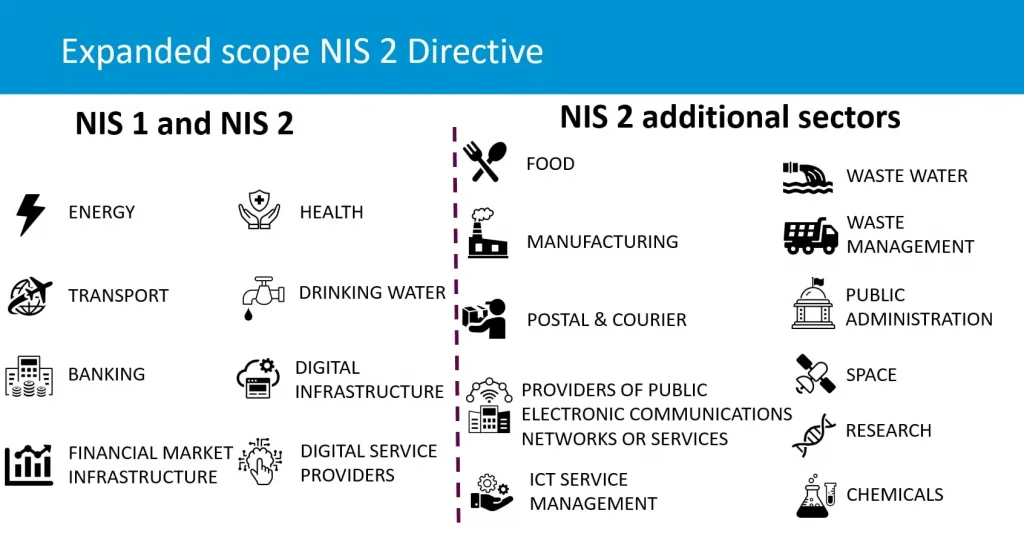
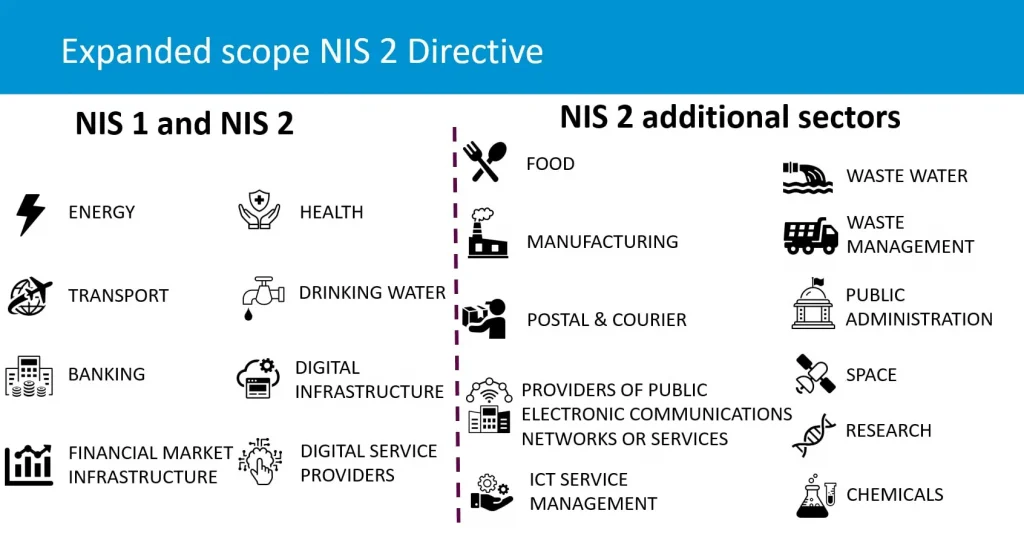
NIS 2 significantly expands its scope to cover more sectors than the original NIS Directive, including:
- Public administration
- Healthcare
- Energy
- Digital infrastructure
- Food production
With over 160,000 organizations expected to fall under its scope, the directive affects both essential entities and important entities, meaning compliance will be required not just for internal security but across supply chains as well.
For example, in healthcare, the directive mandates rapid incident reporting for attacks such as ransomware, which frequently disrupts hospital operations and patient data management. The benefit of NIS 2’s stricter reporting requirements is that they encourage faster containment and response, potentially minimizing the spread of malware and limiting the exposure of sensitive patient data. However, the downside is that organizations under pressure to meet the 24-hour reporting window may provide incomplete or inaccurate reports, increasing the risk of non-compliance fines if details are found to be insufficient or inconsistent during follow-up audits.
In the energy sector, supply chain attacks pose a significant threat, where vulnerabilities in third-party systems can compromise power plants or grid operations. NIS 2’s requirement for rapid reporting ensures swift action can be taken to prevent widespread outages, enhancing overall system resilience. The challenge, however, is that energy companies may face penalties if incidents are reported prematurely without full investigation, leading to miscommunication or confusion across different regulatory bodies, particularly when coordination with international partners is required.
For public administration bodies, credential theft is a critical concern, especially due to the sensitive data these organizations handle. NIS 2’s requirement for rapid reporting helps contain unauthorized access and prevent large-scale breaches of citizen data. But, similar to other sectors, the need to report incidents quickly could lead to over-reporting or the submission of partial information, which could trigger penalties if the organization fails to follow up with detailed and accurate reports in the required timeframe.
Shorter Reporting Windows: Less Time, More Pressure
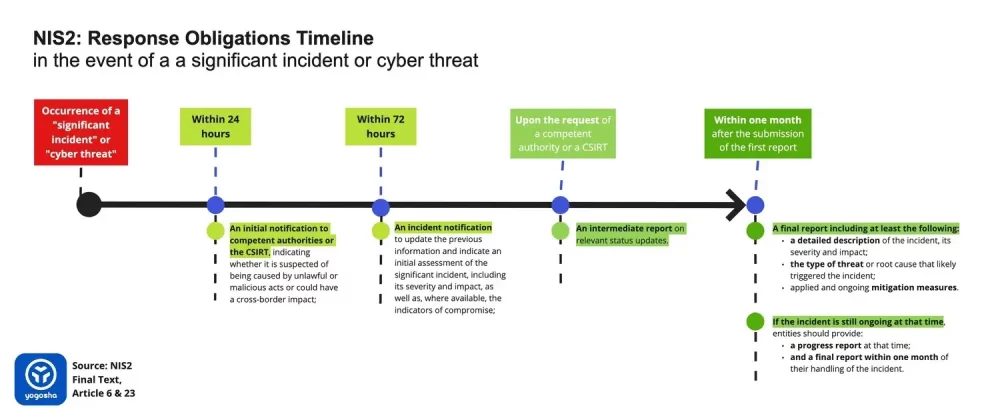
Under NIS 2, the reporting windows for cyber incidents have been significantly reduced. Essential entities are now required to report incidents within 24 hours, while important entities have up to 72 hours. This shorter timeframe places pressure on organizations to have rapid detection and response systems in place to meet these deadlines and avoid potential penalties.
Failing to Comply Could Cost You Millions – Here’s What You Need to Know
Non-compliance with NIS 2 can lead to significant financial penalties. Essential entities could face fines of up to 2% of global annual turnover or €10 million, while important entities might incur penalties of 1.4% of turnover or €7 million. Beyond the fines, failing to meet the directive’s requirements could result in operational disruptions, further compounding the financial impact. Staying compliant not only helps avoid these costly outcomes but also ensures that your organization is better protected against potential cyber threats in the long run.
Preparing for NIS 2: What Organizations Can Do Now
With the October 17th, 2024 deadline fast approaching, organizations must prioritize compliance.
Here are some critical steps to prepare:
- Strengthen incident response capabilities to meet the shortened reporting deadlines.
- Bolster risk management systems to ensure alignment with NIS 2’s requirements.
- Enhance supply chain security, ensuring third-party vendors and partners also comply with the directive’s standards.
How Perception Point Helps with NIS 2 Compliance
At Perception Point, we understand the increasing demands placed on organizations by regulations such as NIS 2. Long before these directives were introduced, we’ve been working with businesses to secure the modern workspace, where the need for seamless protection spans across email, web browsers, and SaaS applications. By combining AI-powered threat prevention, anti-evasion technology, and real-time detection, along with 24/7 managed incident response, Perception Point empowers organizations to meet even the strictest compliance requirements, without compromising on security or operational efficiency.
Perception Point’s unified platform offers key capabilities to help businesses stay ahead of NIS 2’s demands:
- AI-Driven Threat Detection: Real-time detection and reporting systems ensure that businesses can respond swiftly to advanced threats, helping meet NIS 2’s strict timelines.
- Cross-Channel Protection: Comprehensive security coverage across email, SaaS applications, and web browsers ensures robust protection and compliance with NIS 2’s risk management guidelines.
- Rapid Managed Incident Response: Autonomous threat response together with 24/7 IR & support teams ensure quick, effective management of incidents, which is crucial for minimizing damage in line with NIS 2’s requirements.
- Continuous Monitoring: Perception Point’s X-Ray offers advanced reporting and forensic capabilities, enabling ongoing continuous monitoring and risk assessments ensuring compliance with NIS 2 proactive risk management guidelines without adding operational overhead.
Are you ready for NIS2 compliance?
Perception Point’s advanced threat prevention platform can help your organization meet NIS2 requirements. Ensure your organization is both compliant and protected—schedule a call with an expert.
如有侵权请联系:admin#unsafe.sh