2024-10-15 15:30:19 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
With the rapid growth of the internet, especially in areas like cloud computing, 5G, and IoT technologies, the scale of botnets continues to expand, intensifying the battle between attack and defense. In response, DDoS attacks have evolved, taking on a more intelligent form to evade security defenses.
Traditional DDoS attacks typically target specific services—either a single IP address or a small group of IP addresses—resulting in a sudden increase in traffic or connection attempts. The attack characteristics are often quite obvious. However, as the internet continues to evolve, the DDoS threat landscape has escalated. Attackers now increasingly target internet data centers (IDCs), ISPs, or enterprises with a large number of IP addresses using carpet-bombing attacks.
In a carpet-bombing attack, instead of launching a DDoS flood attack against a single IP or a few IPs, attackers simultaneously or sequentially target many IP addresses. In simultaneous attacks, the traffic directed at each IP is relatively small but, when combined, it exceeds the overall bandwidth. During sequential attacks, each IP suffers a large attack but only for a very short duration.
Most current DDoS detection methods focus on traffic changes for individual IPs or detect high-traffic IPs when overall traffic exceeds limits. However, carpet-bombing attacks can evade these traditional detection and defense methods, presenting new challenges to DDoS defense.
How Carpet-Bombing Attacks Work
From the Attacker’s Perspective
Attackers often acquire the target’s network address range through various methods. When analyzing the Mirai botnet code, it’s clear that when the attack target is specified as a network segment, the target IP for each attack is randomly selected from that range.
This shows that the target is no longer a fixed IP address, but a group of addresses receiving attack traffic.
From the Victim’s Perspective
The victim experiences a noticeable increase in overall network traffic (or a specific type of traffic), but no single IP address shows abnormal traffic. The increased traffic is distributed across multiple IP addresses, leading to link congestion or anomalies in session tables of back-end firewalls or security devices, affecting network quality.
From the Defender’s Perspective
Compared to traditional single-IP attacks, carpet-bombing attacks distribute traffic across multiple IP addresses.
Defenders typically focus on attacks targeting single IPs, leading to missed detections or inadequate defenses for carpet-bombing attacks.
Real-World Carpet-Bombing Attack Cases
SYN Flood Carpet-Bombing Attack
An organization experienced a carpet-bombing attack from a fixed source IP through SYN packets, causing the back-end firewall’s concurrent session limit to be exceeded, resulting in service disruption.
ISP NTP Amplification Carpet-Bombing Attack
An Internet Service Provider (ISP) faced an NTP reflection amplification carpet-bombing attack, which led to link congestion and reduced network quality.
Defending Against Carpet-Bombing Attacks
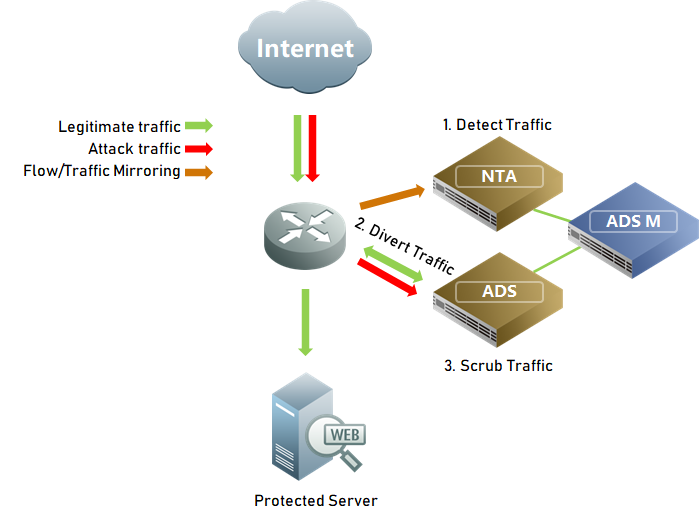
A typical out-of-the-path DDoS deployment involves traffic detection, diversion, and scrubbing.
Traffic Detection:
Traditional detection methods focus on anomalies in individual IPs or overall traffic volumes. However, targeted low-speed carpet-bombing attacks may go undetected. For example, a low-speed SYN Flood carpet-bombing could cause firewall anomalies, so detection mechanisms must support more granular, network segment-based attack type detection.
Additionally, since single IP attacks may also trigger subnet alerts, a more comprehensive detection model is needed to improve the accuracy of carpet-bombing attack detection. For example, when triggering a subnet alert, it is necessary to detect the traffic proportion of the Top IP addresses or to detect in conjunction whether there is any single IP attack alert triggered, etc.
Traffic Diversion:
Most DDoS defenses use BGP diversion. During a carpet-bombing attack, the traditional single-IP diversion method is slow and increases the number of routing entries. Using network segment diversion helps, but large segments can sometimes cause routing issues due to the longest prefix match rule. For effective traffic diversion, routing splits should be supported. For example, a /24 network should be split into multiple routes with /26 masks.
Traffic Scrubbing:
In addition to traditional scrubbing thresholds for individual IPs, network segment-based scrubbing strategies should be implemented. Two key scenarios must be addressed:
- False Source Scenario: A SYN Flood carpet-bombing attack using forged source IPs requires individualized scrubbing strategies for each target IP, as different services have varying traffic models. This minimizes false positives during scrubbing.
- Real Source Scenario: A UDP Flood carpet-bombing attack with real sources is more challenging to defend against due to the difficulty of identifying patterns based on rate or behavior. In this case, defenders should focus on the core of the attack—using behavior analysis (such as the number of target IP addresses visited within a specified period) to identify the attack source.
As businesses expand their internet services and IP address ranges, carpet-bombing attacks are no longer limited to ISPs. Enterprises often have smaller local bandwidth and rely on two-layer scrubbing:
- ISP scrubbing plus local scrubbing, or
- High-capacity traffic scrubbing plus local scrubbing
In such cases, when attack traffic exceeds local bandwidth, rapid cooperation with ISPs for scrubbing is essential. Currently, most setups involve API calls or manual IP traffic scheduling, but a fast, network-segment-based traffic scheduling mechanism is needed.
In recent years, carpet-bombing attacks have gained momentum, combining multiple attack vectors in network and application layers, and tactics like burst flooding. This makes them harder to defend against. To effectively protect against these attacks, defenders need to continuously iterate their detection and defense models, integrating threat intelligence and machine learning to establish a smart defense system.
NSFOCUS is at the forefront of the industry in combating carpet-bombing attacks, leveraging its cutting-edge technology and extensive experience to continuously refine protection algorithm. To learn more about protection solution for carpet-bombing or other types of DDoS attacks, contact us now!
The post A Deep Dive into DDoS Carpet-Bombing Attacks appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks..
*** This is a Security Bloggers Network syndicated blog from NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks. authored by NSFOCUS. Read the original post at: https://nsfocusglobal.com/a-deep-dive-into-ddos-carpet-bombing-attacks/
如有侵权请联系:admin#unsafe.sh








