To stay safe from cyber attacks, organizations need effective ways to gather information about threats before they cause irreparable damage. Let’s look at several methods for gathering threat intelligence (TI) to see how they can help you gain a better view of the current threat landscape.
Why is Threat Intelligence Important?
Threat intelligence is important for several reasons:
- Proactive Awareness: Knowing about potential threats helps organizations take steps to deal with them before they escalate.
- Quick Response: When an attack happens, having threat intelligence allows teams to respond faster and more effectively.
- Better Risk Management: Understanding vulnerabilities helps organizations prioritize where to focus their security efforts.
How to Collect Cyber Threat Intelligence
Gathering threat intelligence isn’t just about knowing where to look; it’s about understanding how to use those sources effectively. Let’s explore key methods for collecting threat intelligence, diving into the techniques and tools that can help cybersecurity professionals.
Integrating Threat Intelligence Feeds
Threat intelligence feeds provide real-time streams of data on malware, vulnerabilities, and emerging risks. By using these feeds, organizations can stay up-to-date with the latest threats and trends. To effectively gather intelligence:
- Automate Data Collection: Integrate feeds with your cybersecurity tools (like SIEM) for continuous monitoring.
- Correlate Information: Use multiple feeds to cross-reference threats and identify patterns.
- Customize for Relevance: Focus on feeds that provide the most pertinent information for your industry or organization’s needs.
Using Threat Intelligence Portals
Threat intelligence portals centralize data and allow for comprehensive threat analysis. ANY.RUN‘s TI Lookup is an example of a tool that helps with such analysis. Using TI Lookup, users can:
- Investigate Indicators: Enter suspicious IP addresses, domains, or file hashes to gain insights into potential threats.
- Search for Known Threats: Use the portal to research malware, attack methods, or Indicators of Compromise (IOCs).
- Analyze Attack Techniques: The tool can also be used to link threats to known tactics and vice versa, such as those in the MITRE ATT&CK framework, helping users understand the nature of the threats they face.

Try Threat Intelligence
from ANY.RUN
Explore TI Feeds and TI Lookup
to see how they can help you achieve better threat visibility.
Request trial
Monitoring Dark Web Forums
The Dark Web is often a hub for cybercriminal activities. Monitoring these forums can yield valuable information about planned attacks, new exploit techniques, and stolen data. Key steps include:
- Forum Monitoring Tools: Use automated tools to track conversations on Dark Web forums, collecting insights into new attack vectors.
- Analyze Discussions: Gather intelligence on specific threat actors, potential targets, and trends emerging in cybercrime.
By keeping an eye on dark web forums, organizations can stay aware of evolving threats before they escalate.
Reviewing Publicly Available Reports
Cybersecurity organizations regularly release reports and threat research that provide detailed analyses of recent attacks and vulnerabilities. These reports are invaluable for keeping up with emerging threats. To use them effectively:
- Review Reports for Trends: Look for trends in the attacks, methods, and vulnerabilities discussed.
- Implement Recommendations: Use insights from these reports to adjust security practices and defense strategies.
Data Mining for Threat Intelligence
Data mining is a powerful method for extracting useful intelligence from large datasets. It allows security teams to identify patterns and anomalies that indicate potential threats:
- Anomaly Detection: By analyzing network traffic and system logs, data mining techniques can reveal suspicious behavior that may indicate an attack in progress.
- Predictive Analytics: Historical data can be analyzed to predict future attack trends, helping organizations take preventative measures.
Deploying Honeypots
Honeypots are decoy systems set up to attract cybercriminals. These fake targets are used to observe attackers and gather intelligence on their tactics and methods. To use honeypots effectively:
- Simulate Real Systems: Honeypots should mimic genuine vulnerabilities to lure attackers.
- Gather Attack Data: Record all interactions with the honeypot to study the attackers’ methods, tools, and behaviors in a controlled environment.
Honeypots provide invaluable insights into how attackers operate, enabling organizations to improve their defensive strategies based on real-world data.
Crowdsourcing Threat Intelligence
Collaboration is another valuable tool for collecting threat intelligence. Crowdsourcing allows organizations to benefit from the collective knowledge of the broader cybersecurity community:
- Threat Intelligence Sharing: Platforms like ISACs (Information Sharing and Analysis Centers) enable the exchange of threat data across industries.
- Collaborative Investigations: Participating in shared investigations can help identify complex threats and provide faster, more accurate responses.
- Threat Sample Databases: There sources like ANY.RUN’s Public submissions database, containing millions of public sandbox analyses of the latest malware and phishing samples.
Crowdsourcing creates a network of shared defense, helping organizations quickly identify emerging threats and stay updated on the latest attack vectors.
How to Gather Cyber Threat Intelligence with TI Lookup
Gathering cyber threat intelligence involves utilizing various tools and techniques.
ANY.RUN’s TI Lookup simplifies this process by offering a centralized repository of millions of IOCs, extracted from ANY.RUN’s extensive database of interactive malware analysis sessions.
You can use over 40 search parameters to investigate search this database, turning isolated data points into a comprehensive understanding of persistent and emerging threats.
Key Benefits of TI Lookup for researchers:
- Comprehensive Threat Data: Access detailed threat intelligence by analyzing processes, files, network traffic, and more. TI Lookup links related IOCs, helping you fully understand the scope and impact of an attack.
- Fast and Accurate Searches: With 2-second response time and 1,000 new entries daily, TI Lookup provides swift access to the latest threat intelligence.
- Seamless Integration: Whether using the web interface or API, TI Lookup integrates easily with your existing security tools like Splunk.
By using ANY.RUN TI Lookup, your security team can efficiently investigate threats, reduce risks, and enhance your overall cybersecurity posture.
Here are a few examples using ANY.RUN TI Lookup:
Analyzing Destination IPs
You can enter a suspicious IP address into TI Lookup to see if it is linked to any threat.
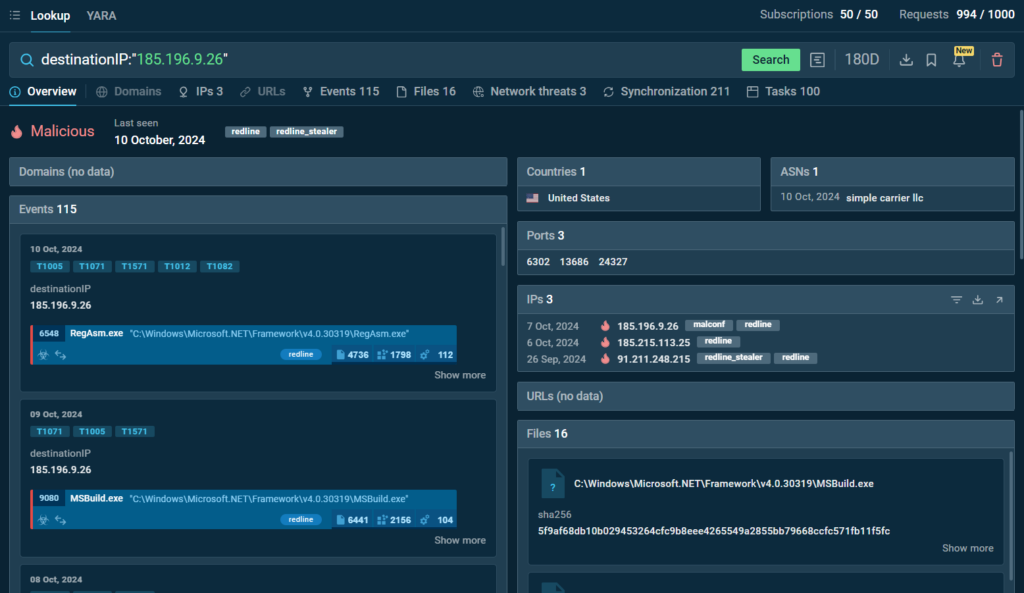
The tool will display details such as the IP’s location and any associated indicators, samples, and sandbox sessions, giving you crucial insights into potential risks.
Threat Name Investigation
You can also identify the latest samples of a known threat using its name.
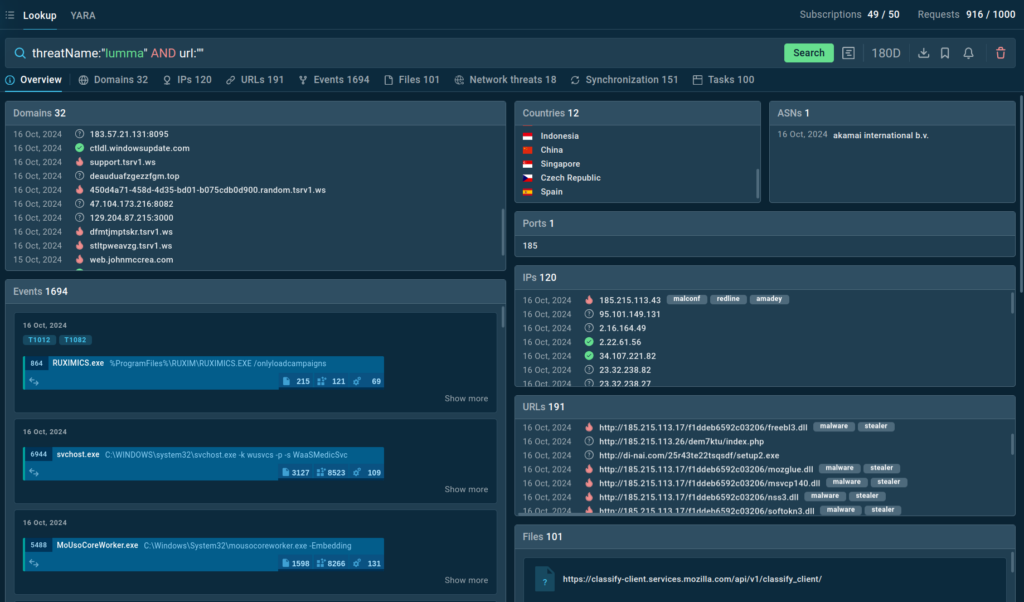
You will receive detailed information about the threat, including its behavior and Indicators of Compromise. This helps in understanding how the threat operates.
Identifying Threats via MITRE ATT&CK TTPs
ANY.RUN’s TI Lookup lets you search using specific tactics or techniques of the MITRE ATT&CK framework.
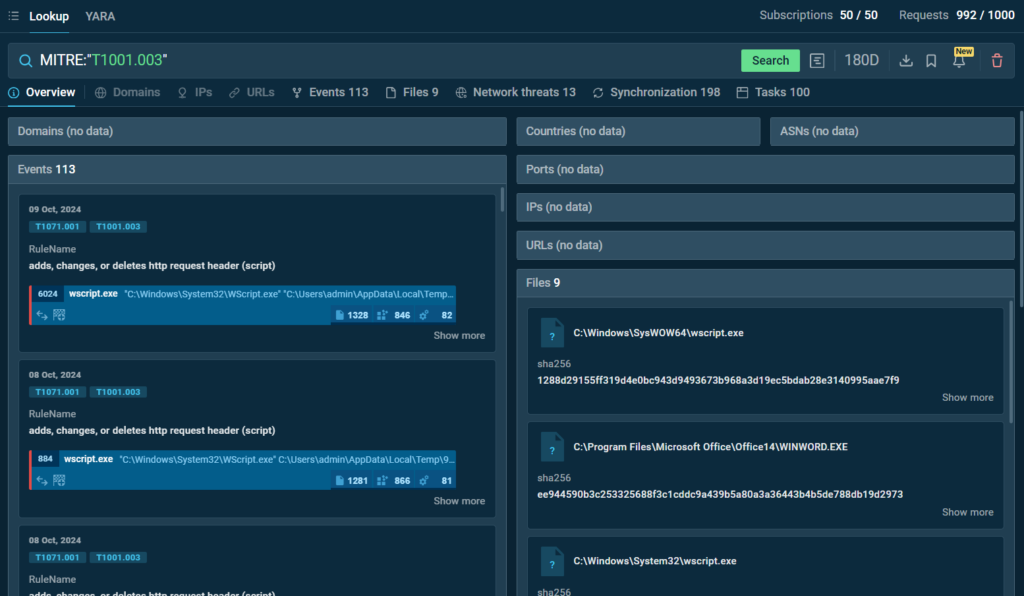
The tool will show relevant examples of how these techniques are used in attacks, helping you understand their application in real-world scenarios.
Using ANY.RUN TI Lookup, cybersecurity teams can efficiently gather threat intelligence, investigate malware behavior, and equip themselves with the knowledge needed to combat emerging threats.

Learn to investigate threats
Discover a practical guide
to gathering Threat Intelligence with TI Lookup from a seasoned researcher.
See real-world use cases
Learn to collect intel
Wrapping up
Gathering cyber threat intelligence is essential for understanding and combating cyber threats. By using various sources like threat intelligence feeds, dark web forums, publicly available reports, and tools like ANY.RUN TI Lookup, organizations can improve their awareness of potential risks. Being informed about these threats is a key part of a strong cybersecurity strategy.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
