2024-10-15 22:0:0 Author: blogs.microsoft.com(查看原文) 阅读量:4 收藏
Microsoft customers face more than 600 million cybercriminal and nation-state attacks every day, ranging from ransomware to phishing to identity attacks. Once again, nation-state affiliated threat actors demonstrated that cyber operations—whether for espionage, destruction, or influence—play a persistent supporting role in broader geopolitical conflicts. Also fueling the escalation in cyberattacks, we are seeing increasing evidence of the collusion of cybercrime gangs with nation-state groups sharing tools and techniques.
We must find a way to stem the tide of this malicious cyber activity. That includes continuing to harden our digital domains to protect our networks, data, and people at all levels. However, this challenge will not be accomplished solely by executing a checklist of cyber hygiene measures but only through a focus on and commitment to the foundations of cyber defense from the individual user to the corporate executive and to government leaders.
These are some of the insights from the fifth annual Microsoft Digital Defense Report, which covers trends between July 2023 and June 2024.
State-affiliated actors increasingly are using cybercriminals and their tools.
Over the last year, Microsoft observed nation-state actors conduct operations for financial gain, enlist cybercriminals to collect intelligence, particularly on the Ukrainian military, and make use of the same infostealers, command and control frameworks, and other tools favored by the cybercriminal community. Specifically:
- Russian threat actors appear to have outsourced some of their cyberespionage operations to criminal groups, especially operations targeting Ukraine. In June 2024, a suspected cybercrime group used commodity malware to compromise at least 50 Ukrainian military devices.
- Iranian nation-state actors used ransomware in a cyber-enabled influence operation, marketing stolen Israeli dating website data. They offered to remove specific individual profiles from their data repository for a fee.
- North Korea is getting into the ransomware game. A newly-identified North Korean actor developed a custom ransomware variant called FakePenny, which it deployed at organizations in aerospace and defense after exfiltrating data from the impacted networks—demonstrating both intelligence gathering and monetization motivations.
Nation-state activity was heavily concentrated around sites of active military conflict or regional tension
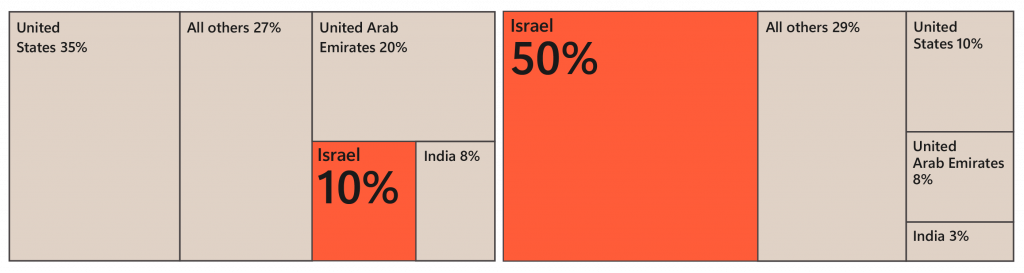
Aside from the United States and the United Kingdom, most of the nation-state-affiliated cyber threat activity we observed was concentrated around Israel, Ukraine, the United Arab Emirates, and Taiwan. In addition, Iran and Russia have used both the Russia-Ukraine war and the Israel-Hamas conflict to spread divisive and misleading messages through propaganda campaigns that extend their influence beyond the geographical boundaries of the conflict zones, demonstrating the globalized nature of hybrid warfare.
- Approximately 75% of Russian targets were in Ukraine or a NATO member state, as Moscow seeks to collect intelligence on the West’s policies on the war.
- Chinese threat actors’ targeting efforts remain similar to the last few years in terms of geographies targeted—Taiwan being a focus, as well as countries within Southeast Asia—and intensity of targeting per location.
- Iran placed significant focus on Israel, especially after the outbreak of the Israel-Hamas war. Iranian actors continued to target the US and Gulf countries, including the UAE and Bahrain, in part because of their normalization of ties with Israel and Tehran’s perception that they are both enabling Israel’s war efforts.

Russia, Iran, and China focus in on the U.S. election
Russia, Iran, and China have all used ongoing geopolitical matters to drive discord on sensitive domestic issues leading up to the U.S. election, seeking to sway audiences in the U.S. to one party or candidate over another, or to degrade confidence in elections as a foundation of democracy. As we’ve reported, Iran and Russia have been the most active, and we expect this activity to continue to accelerate over the next two weeks ahead of the U.S. election.
In addition, Microsoft has observed a surge in election-related homoglyph domains—or spoofed links—delivering phishing and malware payloads. We believe these domains are examples both of cybercriminal activity driven by profit and of reconnaissance by nation-state threat actors in pursuit of political goals. At present, we are monitoring over 10,000 homoglyphs to detect possible impersonations. Our objective is to ensure Microsoft is not hosting malicious infrastructure and inform customers who might be victims of such impersonation threats.
Financially motivated cybercrime and fraud remain a persistent threat
While nation-state attacks continue to be a concern, so are financially motivated cyberattacks. In the past year Microsoft observed:
- A 2.75x increase year over year in ransomware attacks. Importantly, however, there was a threefold decrease in ransom attacks reaching the encryption stage. The most prevalent initial access techniques continue to be social engineering—specifically email phishing, SMS phishing, and voice phishing—but also identity compromise and exploiting vulnerabilities in public facing applications or unpatched operating systems.
- Tech scams skyrocketed 400% since 2022. In the past year, Microsoft observed a significant uptick in tech scam traffic with daily frequency surging from 7,000 in 2023 to 100,000 in 2024. Over 70% of malicious infrastructure was active for less than two hours, meaning they may be gone before they’re even detected. This rapid turnover rate underscores the need for more agile and effective cybersecurity measures.
Threat actors are experimenting with generative AI
Last year, we started to see threat actors—both cybercriminals and nation-states—experimenting with AI. Just as AI is increasingly used to help people be more efficient, threat actors are learning how they can use AI efficiencies to target victims. With influence operations, China-affiliated actors favor AI-generated imagery, while Russia-affiliated actors use audio-focused AI across mediums. So far, we have not observed this content being effective in swaying audiences.

But the story of AI and cybersecurity is also a potentially optimistic one. While still in its early days, AI has shown its benefits to cybersecurity professionals by acting as a tool to help respond in a fraction of the time it would take a person to manually process a multitude of alerts, malicious code files, and corresponding impact analysis. We continue to innovate our technology to find new ways that AI can benefit and strengthen cybersecurity.
Collaboration remains crucial to strengthening cybersecurity.
With more than 600 million attacks per day targeting Microsoft customers alone, there must be countervailing pressure to reduce the overall number of attacks online. Effective deterrence can be achieved in two ways: by denial of intrusions or by imposing consequences for malicious behavior. Microsoft continues to do our part to reduce intrusions and has committed to taking steps to protect ourselves and our customers through our Secure Future Initiative.
While the industry must do more to deny the efforts of attackers via better cybersecurity, this needs to be paired with government action to impose consequences that further discourage the most harmful cyberattacks. Success can only be achieved by combining defense with deterrence. In recent years, a great deal of attention has been given to the development of international norms of conduct in cyberspace. However, those norms so far lack meaningful consequence for their violation, and nation-state attacks have been undeterred, increasing in volume and aggression. To shift the playing field, it will take conscientiousness and commitment by both the public and private sectors so that attackers no longer have the advantage.
Microsoft continues to share important threat intelligence with the community, including our recent Cyber Signals research looking at cyber risks in the education sector.
Tags: AI, artificial intelligence, China, cyberattacks, cybercrime, cybersecurity, election, elections, generative ai, Hamas, homoglyphs, Iran, Israel, malware, Microsoft Digital Defense Report, NATO, North Korea, phishing, Russia, Secure Future Initiative, Tech scams, Ukraine, United Kingdom, United States
如有侵权请联系:admin#unsafe.sh