2024-10-18 23:25:16 Author: www.trustwave.com(查看原文) 阅读量:2 收藏
3 Minute Read
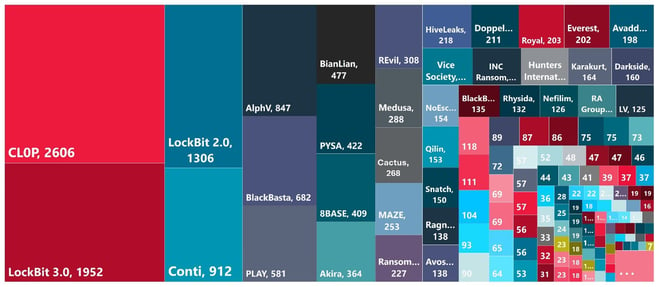
At the end of every year, the Trustwave content team asks its in-house experts what cybersecurity topics they predict will be top of mind in the coming 12 months, and inevitably the top answer is more ransomware. Instead of waiting an extra couple of months, we thought why not get ahead of the curve, pretend that ransomware will again be an issue, because it will, and proceed to the part of the story where we go through the problem and mitigation methods. Recent research compiled by Trustwave SpiderLabs from several sources was the basis for the chart below that graphically displays which ransomware threat groups are most active. The team’s work revealed Clop, Lockbits 2.0 and 3.0, Conti, and ALPHV are the most active when it comes to spreading ransomware. Microsoft, which partners with Trustwave on a variety of solutions designed to help organizations unlock the full potential of Microsoft Security under its Microsoft 365 enterprise plans, noted in its latest report a 2.75X increase year over year in human-operated ransomware attacks on its customer base. Trustwave and Microsoft have noted that social engineered email, SMS and voice-based phishing attacks, along with identity compromise, exploiting known vulnerabilities and running unpatched operating systems were the primary methods threat actors used to gain an initial foothold. The reason behind this activity is obvious. Big bucks. According to several sources, the attackers have made about $3.75 billion over the last five years, with this number ramping up with $1.1 billion being illegally garnered in just 2023. These billions of stolen dollars equate to each attack costing the victim about $5 million, with a mean time to identify an issue of 211 days and mean time to contain of 73 days. US-based targets received 48% of all ransomware attacks, followed by the EU, 19%, UK, 12%, and Australia 2%. These numbers are intimidating, but the silver lining is every organization has the ability to take the steps necessary to harden itself against a ransomware attack. Step 10 needs to be fleshed out a bit. All conversations on ransomware prevention and preparedness must include information on what to do if the unthinkable happens and your organization is successfully attacked. It is all about the speed of detection and speed of response. As noted above, the average MTTI and MTTC can be quite long, which means the faster an organization can mitigate an incident, the better. Organizations that partner with managed security service providers can ensure there are always eyes on the environment. Adversaries can attack any system at any time of day. It's also important that organizations have an incident response retainer. We've seen organizations who recognize that they have been attacked but never switch to partner organizations that can help respond to the attack. Meanwhile, the attacker gains more and more information and sensitive data from the network. Trustwave offers comprehensive support for dealing with ransomware attacks through several key services: These services collectively ensure that organizations are not only prepared to handle ransomware attacks but also equipped to recover swiftly and strengthen their security posture for the future. By implementing these strategies, organizations can build a strong cybersecurity foundation and significantly reduce their risk of falling victim to ransomware attacks.
Raw data taken from ransomlook.io and ecrime.ch. Analysis done by Trustwave SpiderLabs.Be Fundamentally Sound
Testing and Evaluation
Collaboration and Preparedness
The Role Trustwave Plays to Keep Organization’s Safe
Sign up to receive the latest security news and trends straight to your inbox from Trustwave.Stay Informed
如有侵权请联系:admin#unsafe.sh