
2024-10-22 13:40:47 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
75% of Mobile Apps Fail Basic Security Tests. Hackers are increasingly focusing on the mobile channel, making mobile apps a prime target for fraud and security breaches. With this growing threat, it’s essential for organizations and app developers to adopt a proactive approach to mobile application security. The OWASP Top 10 Mobile Risks outlines the most critical security flaws and vulnerabilities that developers must address to protect their applications.
To help you secure your apps, we have compiled the updated checklist of 2024 based on these top 10 threats, detailing how app shielding can safeguard against common vulnerabilities.
What is OWASP Mobile Security Guide?
The Mobile Security Testing Guide (MSTG) serves as a detailed resource for security testing and reverse engineering of mobile applications for both iOS and Android platforms. The MSTG includes the following content:
- Insights into mobile platform internals
- Security testing throughout the mobile app development lifecycle
- Fundamental static and dynamic security testing methodologies
- Techniques for reverse engineering and tampering of mobile apps
- Evaluation of software protections
- Comprehensive test cases aligned with the requirements of the Mobile Application Security Verification Standard (MASVS).
Top 10 OWASP Mobile Updated 2024
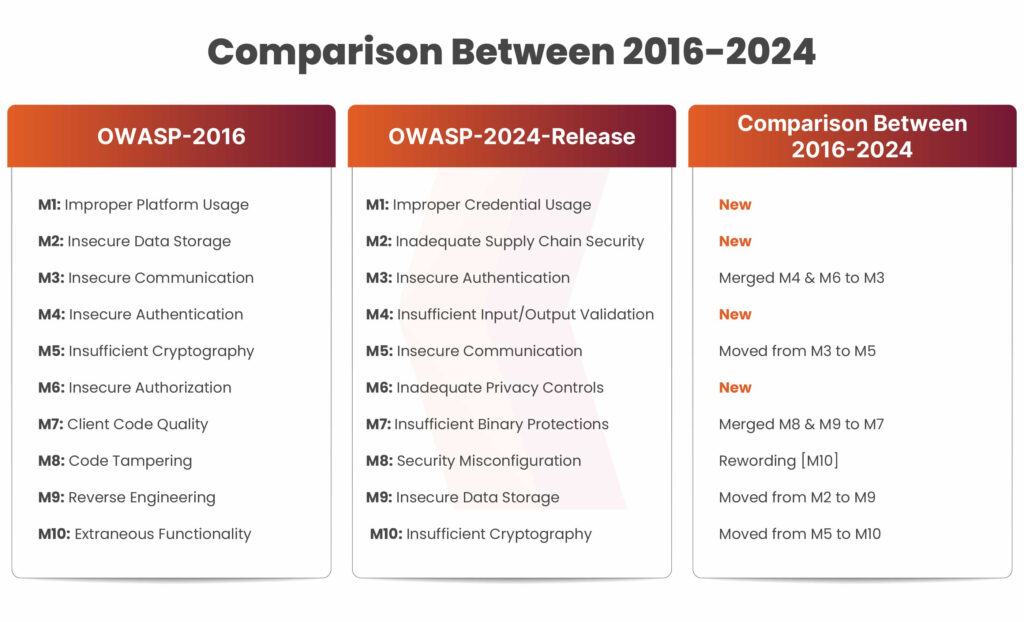
M1: Improper Credential Usage
The inclusion of Improper Credential Usage in the OWASP Mobile Top 10 for 2024 highlights growing concerns over the mishandling of user credentials. This new focus underscores the critical importance of secure authentication methods and emphasizes the need for stronger protection of user identities. It reflects the evolving landscape of mobile application security, where proper handling of credentials, such as passwords, tokens, and API keys, is essential to prevent unauthorized access and safeguard sensitive information. Addressing this risk is vital for enhancing overall mobile application security and protecting user trust.
Prevention Of Improper Credential Usage
Avoiding insecure credential management requires eliminating hardcoded credentials and securely managing user credentials.
Avoid Hardcoding Credentials
Hardcoded credentials in your mobile app’s code or configuration files are easily exploitable by attackers, providing a straightforward entry point for unauthorized access. To enhance security, always avoid embedding credentials in your app.
Secure User Credential Management
Ensure user credentials are securely stored, transmitted, and authenticated by following these practices:
- Encrypt credentials during transmission.
- Avoid storing credentials directly on the device; opt for secure, revocable access tokens instead.
- Use strong authentication protocols.
- Regularly update and rotate API keys or tokens in use.
Inadequate Supply Chain Security
The addition of Inadequate Supply Chain Security to the OWASP Mobile Top 10 for 2024 signals an increased emphasis on the validation of input and output across mobile application processes. This expanded focus highlights the need for a more comprehensive evaluation of data integrity, ensuring that external components and dependencies within the supply chain are secure. By addressing this, mobile applications can better protect against vulnerabilities introduced through third-party services or insecure libraries, ultimately enhancing the overall security of the app and its ecosystem.
Prevention of Supply Security
- Incorporate secure coding practices, thorough code reviews, and regular testing throughout the mobile app development lifecycle to identify and address potential vulnerabilities.
- Ensure secure app signing and distribution processes to prevent attackers from distributing malicious versions of the app.
- Utilize only trusted and validated third-party libraries or components to minimize the risk of vulnerabilities.
- Implement robust security controls for app updates, patches, and releases to protect against exploitation of any vulnerabilities.
- Regularly monitor and detect supply chain security incidents through testing, scanning, or other techniques to quickly identify and respond to threats.
M4: Insufficient Input/Output Validation
The recognition of Insufficient Input/Output Validation in the OWASP Mobile Top 10 for 2024 underscores a heightened focus on the critical need for thorough validation of data throughout mobile application security processes. This emphasis on comprehensive checks ensures data integrity and helps prevent vulnerabilities like data tampering and injection attacks. Addressing this issue strengthens the overall security and reliability of mobile applications, providing better protection for both the system and its users.
Prevention of Input/Output Validation
To prevent Insufficient Input/Output Validation vulnerabilities, follow these practices:
Input Validation:
- Use strict validation techniques to validate and sanitize user input.
- Enforce input length restrictions and reject unexpected or malicious data.
Output Sanitization:
- Sanitize output data properly to prevent cross-site scripting (XSS) attacks.
- Apply output encoding techniques when displaying or transmitting data.
Context-Specific Validation:
- Perform validation tailored to the data context (e.g., file uploads, database queries) to block attacks like path traversal or injection.
Data Integrity Checks:
- Implement checks to ensure data integrity, detecting and preventing corruption or unauthorized modifications.
Secure Coding Practices:
- Follow secure coding principles, such as using parameterized queries and prepared statements to avoid SQL injection.
Regular Security Testing:
- Conduct frequent security assessments, including penetration testing and code reviews, to uncover and mitigate vulnerabilities.
Book a Free Consultation with our Cyber Security Experts

M6: Inadequate Privacy Controls
Inadequate privacy controls in mobile apps present significant risks to user data, potentially exposing sensitive information and undermining user trust. These risks emerge when developers fail to implement strong privacy protections, leading to various violations.
Common issues include over-collection of data, sharing information without user consent, and mishandling Personally Identifiable Information (PII). Such practices leave users vulnerable to privacy breaches, identity theft, and possible legal repercussions.
Prevention of Inadequate Privacy Controls
To prevent privacy violations, the safest strategy is to minimize the collection and processing of Personally Identifiable Information (PII). If PII doesn’t exist, it cannot be compromised. This requires full awareness of all PII assets within an app. Once identified, consider the following:
- Is all the PII truly necessary (e.g., name, address, gender, age)?
- Can some PII be replaced by less sensitive data (e.g., fine-grained location swapped for coarse-grained location)?
- Can the amount of PII be reduced (e.g., location updates every hour instead of every minute)?
- Can some PII be anonymized or blurred (e.g., using hashing, bucketing, or adding noise)?
- Can PII be deleted after a certain period (e.g., retaining health data for only the past week)?
- Can users opt-in to provide optional PII for better services while being informed of the additional risk?
The remaining PII should only be stored or transferred when absolutely necessary, and access should be protected through proper authentication, and possibly authorization. Critical data should have additional layers of defense; for example, health data could be encrypted using a key sealed within the device’s TPM. This ensures that even if an attacker bypasses sandbox protections, the data remains inaccessible.
Additionally, threat modeling can identify potential privacy violation risks specific to an app, allowing security efforts to focus on these areas. Tools for static and dynamic security analysis can help detect common issues, such as logging sensitive data or leaks to clipboard or URL query parameters.
Conclusion
OWASP Mobile Top 10 2024 highlights the pressing security risks that mobile applications face in today’s threat landscape, emphasizing the importance of proactive measures to safeguard user data and maintain application integrity. By understanding and addressing these vulnerabilities, ranging from improper credential usage to inadequate privacy controls, developers and security teams can significantly enhance the security posture of their mobile applications. Implementing best practices, such as secure coding, regular security assessments, and effective data management strategies, will only help mitigate potential risks but also foster user trust and confidence in mobile app ecosystems. As the mobile security landscape continues to evolve, staying informed about these top risks and adapting security measures accordingly is crucial for protecting sensitive information and ensuring robust application security.
As a CERT-In empanelled organization, Kratikal is equipped to enhance your understanding of potential risks. Our manual and automated Vulnerability Assessment and Penetration Testing (VAPT) services proficiently discover, detect, and assess vulnerabilities within your IT infrastructure. Additionally, Kratikal provides comprehensive security auditing services to ensure compliance with various regulations, including ISO/IEC 27001, GDPR, PCI DSS, and more, assisting your business in adhering to legal requirements set forth by diverse governments.
FAQs
- What is OWASP Top 10?
The OWASP Top 10 is a widely recognized standard for raising awareness among developers and enhancing web application security. It reflects a global consensus on the most critical security threats facing web applications and serves as an essential starting point for developers aiming to improve secure coding practices.
- Does OWASP apply to mobile apps?
The OWASP Mobile Application Security Verification Standard (MASVS) is the industry benchmark for mobile app security. It provides guidance for mobile software architects and developers aiming to create secure applications, while also offering a framework for security testers to ensure comprehensive and consistent testing results.
- Why is OWASP important?
OWASP assists in identifying and mitigating the most common and severe security risks, but achieving 100% security online is impossible. Staying up to date, performing regular security assessments, and responding to emerging threats is crucial. OWASP is a dynamic and evolving project.
- When was OWASP top 10 last updated?
The OWASP Top Ten is a list highlighting the 10 most common application vulnerabilities, along with their associated risks, impacts, and recommended countermeasures. Updated every three to four years, the latest version was released on September 24, 2021.
The post OWASP Mobile Top 10 2024: Update Overview appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Shikha Dhingra. Read the original post at: https://kratikal.com/blog/owasp-mobile-top-10-2024-update-overview/
如有侵权请联系:admin#unsafe.sh
