2024-10-23 18:57:30 Author: securityaffairs.com(查看原文) 阅读量:3 收藏
Crooks are targeting Docker API servers to deploy SRBMiner

Threat actors are targeting Docker remote API servers to deploy SRBMiner crypto miners on compromised instances, Trend Micro warns.
Trend Micro researchers observed attackers targeting Docker remote API servers to deploy SRBMiner crypto miners on compromised instances.
The threat actors used the gRPC protocol over h2c to bypass security and execute crypto mining on Docker hosts, manipulating Docker functionalities via gRPC methods.
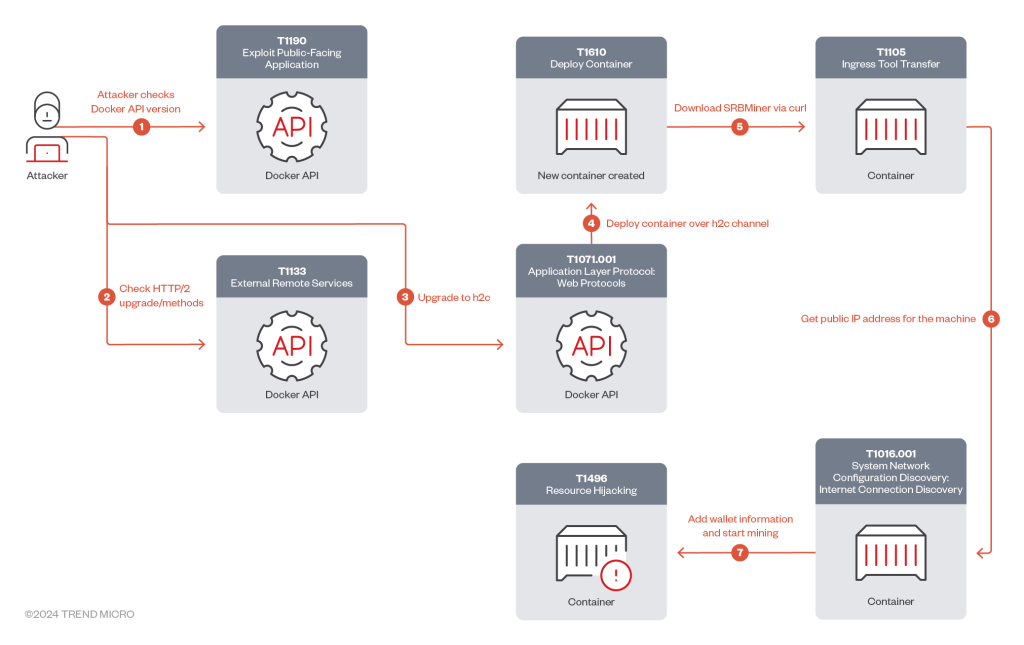
“The attacker first checked the availability and version of the Docker API, then proceeds with requests for gRPC/h2c upgrades and gRPC methods to manipulate Docker functionalities.” reads the analysis published by Trend Micro. “Afterwards, the attacker downloaded and deployed the SRBMiner cryptominer from GitHub, and started mining to their cryptocurrency wallet and public IP address.”
The attack begins by scanning for public-facing Docker API hosts and checking for HTTP/2 upgrades, followed by a connection upgrade request to the unencrypted h2c protocol.
Then attackers check for gRPC methods to perform operations on Docker environments, including those that can be used to perform health checks, file synchronization, authentication, secrets management, and SSH forwarding.
The attacker then requests an upgrade through the h2c protocol.
“Once the connection upgrade request has been processed by the server with all the required parameters using gRPC requests, the attacker sends the /moby.buildkit.v1.Control/Solve gRPC request to build the Docker image-based Dockerfile.srb (Figure 6), which contains Docker container building details based on the legitimate Docker image, debian:bookworm-slim. continues the analysis.

The attacker downloads SRBMiner from GitHub, unzips it into a temporary directory, and deploys it in the /usr/sbin directory. Then attackers start the mining process using a Ripple wallet and mask their public IP address by replacing periods with underscores.
“cybercriminals can exploit features like remote management APIs to their advantage: The malicious actor in this case leveraged the gRPC protocol over H2C, effectively bypassing several security layers to deploy the SRBMiner cryptominer on the Docker host and mine XRP cryptocurrency illicitly.” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Docker API)
如有侵权请联系:admin#unsafe.sh