2024-10-25 21:0:13 Author: www.sentinelone.com(查看原文) 阅读量:1 收藏
The Good | CISA Safety Proposal Set to Protect U.S. Data & Recovery Tool for Mallox Ransomware Published
Following President Biden’s Executive Order 14117, signed earlier in the year, CISA has proposed new security measures to prevent adversary nations from accessing sensitive personal and government-related data across the U.S.
The proposal is aimed at organizations handling bulk data exposed to “countries of concern” or “covered persons” that are liable to extending or amplifying security risks at a national level. Adversarial countries are those that have a known background in cyber espionage, state-backed campaigns, and data breaches. Affected industries include AI developers, cloud service providers (CSPs), as well as firms within the telecom, financial, biotech, and defense sectors.
At a glance, the measures cover areas such as maintaining asset inventories, remediating exploited flaws within specific timeframes, enforcing multi-factor authentication (MFA), restricting unauthorized hardware, detailed log collection, and using encryption to protect data. CISA is encouraging public input to move the proposal forward and suggestions can be made by visiting https://www.regulations.gov/ (ID: CISA-2024-0029).
In other good news, security researchers this week published a free file recovery tool for early victims of Mallox ransomware. Mallox is focused on multi-extortion tactics and is known to encrypt victims’ data before threatening to post it on public TOR-based sites.
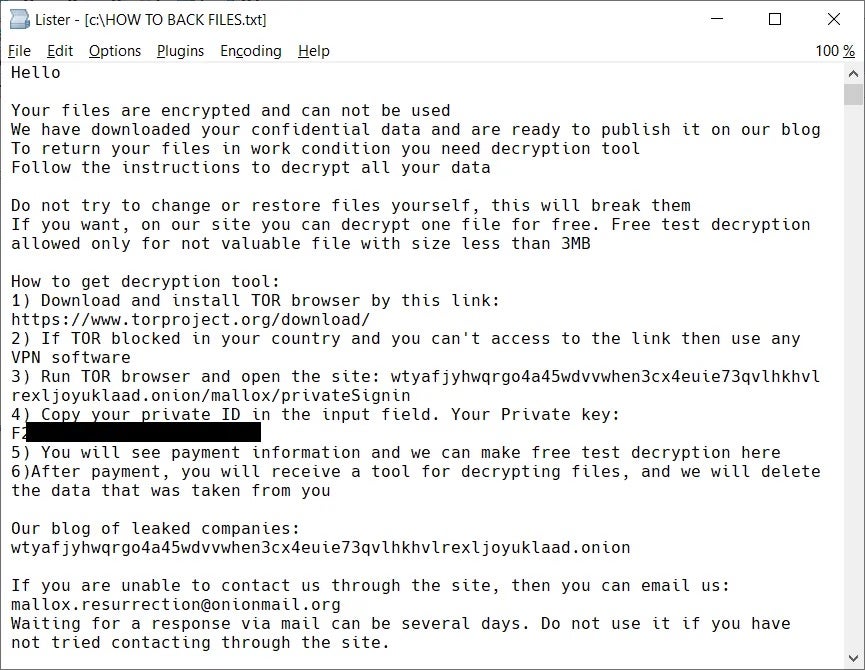
Prior to the development of the tool, researchers had identified a flaw in the cryptographic schema of a Mallox variant, active from January 2023 to February 2024. The malware authors writing this variant made mistakes in the code, allowing data decryption without having the private ECDH key. Decryptable files of this variant can be recognized by their .bitenc, .ma1x0, .mallab, .malox, .mallox, .malloxx, or .xollam extensions. Full instructions on how to download and use the tool can be found here.
The Bad | AWS S3 Abused By Novel macOS.NotLockBit Ransomware
Though LockBit operations were severely disrupted in February, its notoriety has remained – so much so that threat actors have been disguising their own Golang-based ransomware under the LockBit brand, attempting to leverage the group’s reputation to further pressure victims.
The masquerade was first reported by Trend Micro, detailing the actors abusing Amazon S3’s Transfer Acceleration feature in ransomware attacks to exfiltrate victim data to S3 buckets they controlled. The attacker-controlled AWS accounts have since been suspended by AWS.
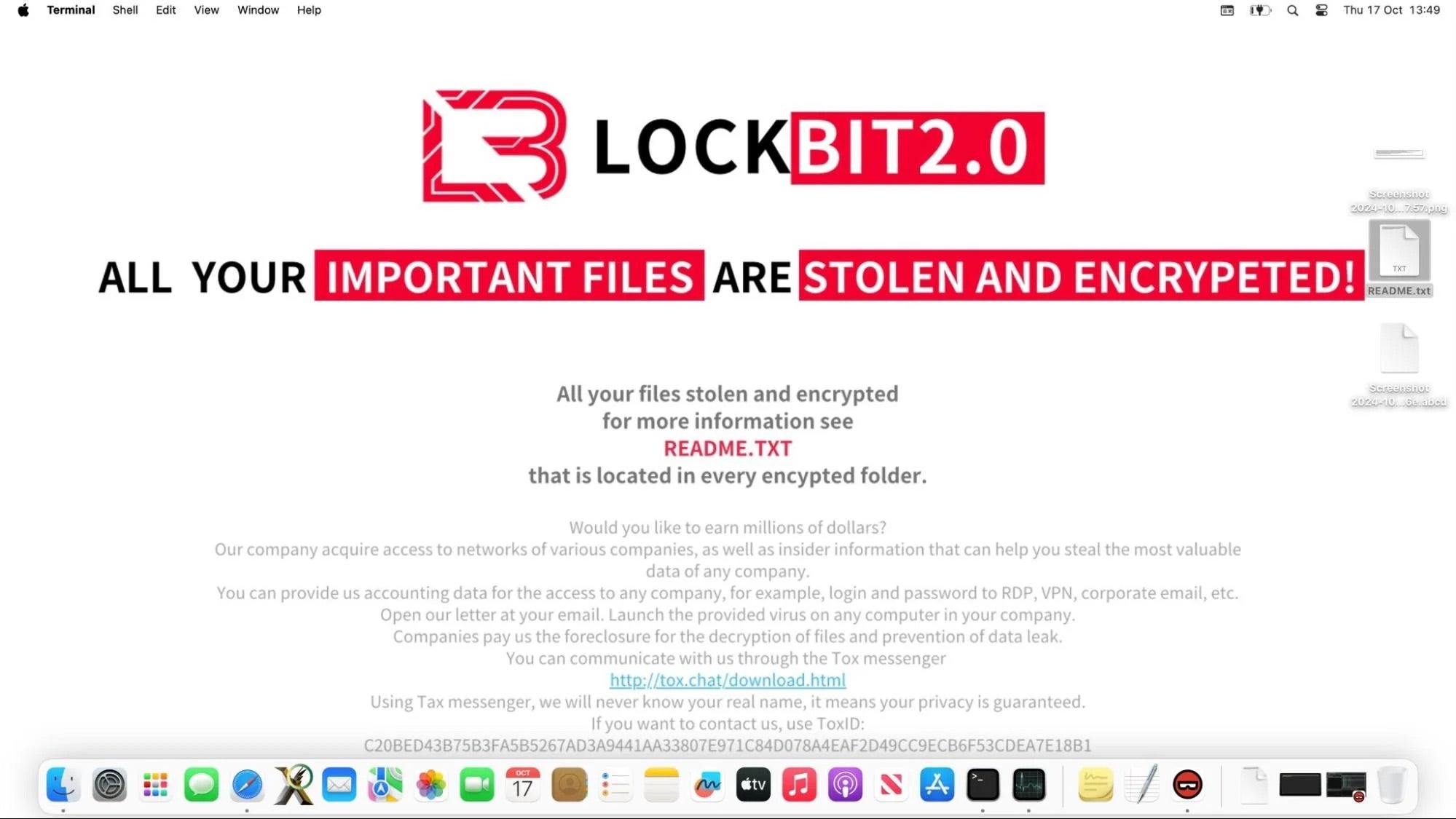
Trend Micro’s analysis identified a macOS malware sample with data exfiltration and file encryption capabilities, all using the LockBit brand. Adding to this, SentinelLabs’ latest findings note a separate set of related Mach-O samples found on VirusTotal. SentinelLabs has since dubbed the masquerading malware ‘macOS.NotLockBit’.
While the delivery method is unclear, once executed, macOS.NotLockBit gathers the acquired host machine’s UUID and generates a master key for file encryption. It then encrypts files based on their extensions and exfiltrates them to AWS using S3 Transfer Acceleration for faster uploads. Encrypted files are renamed with the file extension .abcd. After encryption, the ransomware changes the device’s wallpaper to display a LockBit 2.0 image, likely to coerce its victims into paying.
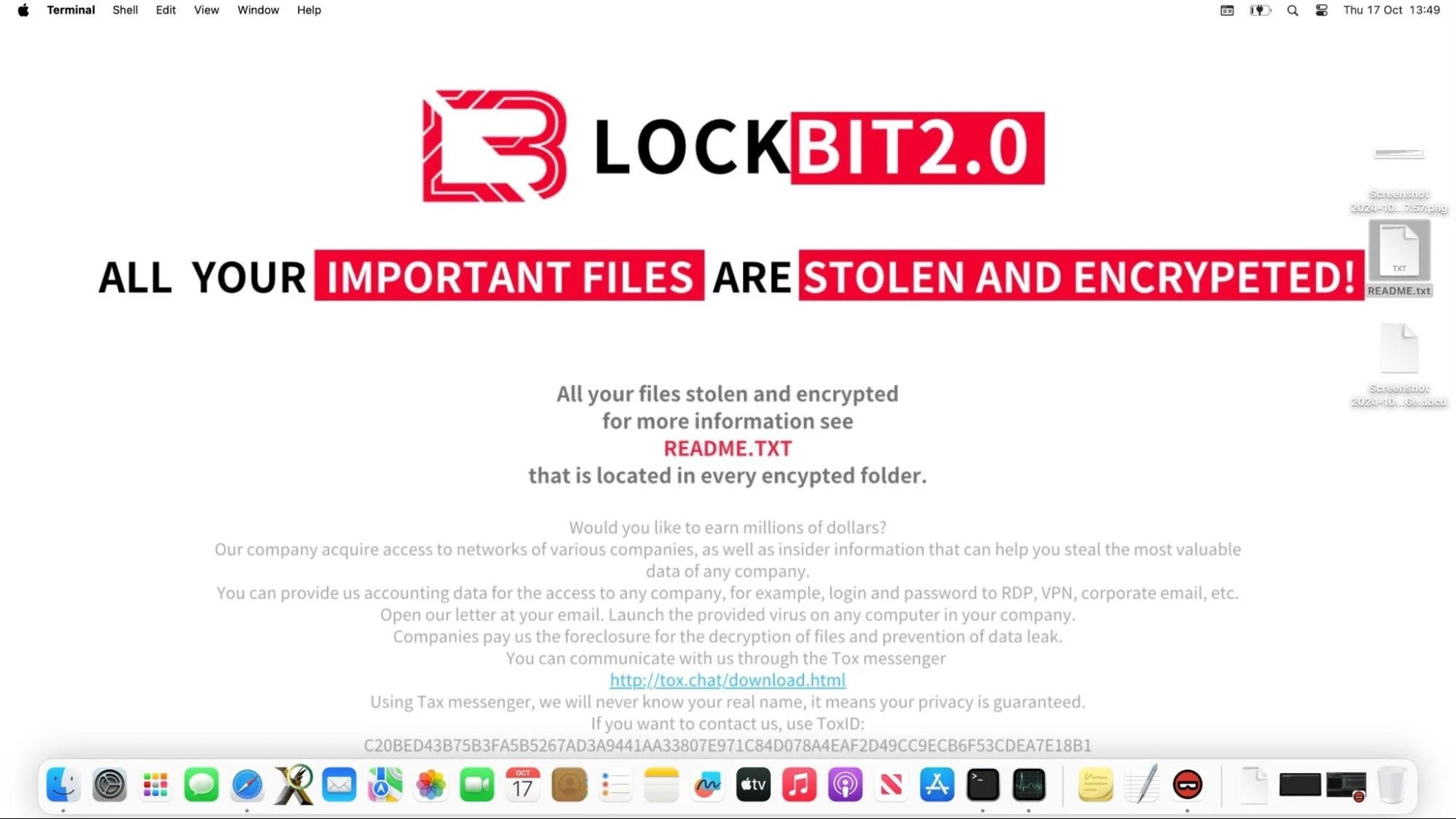
So far, ransomware for macOS remains a relatively small threat, but threat actors are ramping up the use of double extortion tactics, combining data theft and file encryption in the same attack. Though there were no known victims from macOS.NotLockBit’s emergence, the malware’s ongoing development points to a potential for future attacks. SentinelOne customers are protected from all variants of this malware both pre- and on-execution.
The Ugly | Critical Fortinet Zero-Day Vulnerability Exploited In-the-Wild Since June
Following the critical-level “FortiJump” vulnerability disclosed earlier this week, security researchers now confirm its exploitation since June, potentially affecting over 50 servers in zero-day attacks. Fortinet has stated that the vulnerability (CVE-2024-47575) is a missing authentication flaw in the FortiGate to FortiManager Protocol (FGFM) API.
The attack flow starts with the actors registering attacker-controlled FortiManager and FortiGate devices using valid certificates on exposed FortiManager servers. This allows the actors to execute unauthorized API commands and steal configuration data such as sensitive information about managed FortiGate devices, hashed passwords, and configuration settings.
🛡️We added #Fortinet FortiManager missing authentication vulnerability CVE-2024-47575 to our Known Exploited Vulnerabilities Catalog. Visit https://t.co/myxOwap1Tf & apply mitigations to protect your org from cyberattacks. #Cybersecurity #InfoSec pic.twitter.com/vz6PDfZVDb
— CISA Cyber (@CISACyber) October 23, 2024
Researchers have attributed the attacks to a threat group tracked as UNC5820. Their report notes that the stolen data could be used to further compromise the FortiManager via lateral movement, ultimately targeting the enterprise environment. At this time, the researchers have not found evidence of malicious payloads or tampering. Also, while the actors did create multiple files to store device details and exfiltrated information, they have not appeared to use the data to compromise FortiGate devices or move laterally within networks. The investigation to identify the actor’s motivations and location are ongoing as of this writing.
Fortinet has notified affected customers and released a patch for CVE-2024-47575. For those who cannot patch immediately, the company urges users to use the set fgfm-deny-unknown enable command to prevent devices with unknown serial numbers from registering to the FortiManager, create custom certificates when creating the SSL tunnel, and create allow lists of IP addresses cleared to connect with FortiGate devices. Fortinet’s advisory lists all additional indicators of compromise (IOCs) as well as recovery methods to assist organizations in mitigating risk.
如有侵权请联系:admin#unsafe.sh