
2024-10-24 04:37:56 Author: www.tenable.com(查看原文) 阅读量:20 收藏

Frequently asked questions about a zero-day vulnerability in Fortinet’s FortiManager that has reportedly been exploited in the wild.
Background
The Tenable Security Response Team (SRT) has compiled this blog to answer Frequently Asked Questions (FAQ) regarding a zero-day vulnerability in Fortinet’s FortiManager.
Update October 23: The blog has been updated with new information about in-the-wild exploitation and threat actor activity associated with this vulnerability.
FAQ
What is FortiJump?
FortiJump is a name given to a zero-day vulnerability in the FortiGate-FortiManager (FGFM) protocol in Fortinet’s FortiManager and FortiManager Cloud. It was named by security researcher Kevin Beaumont in a blog post on October 22. Beaumont also created a logo for FortiJump.
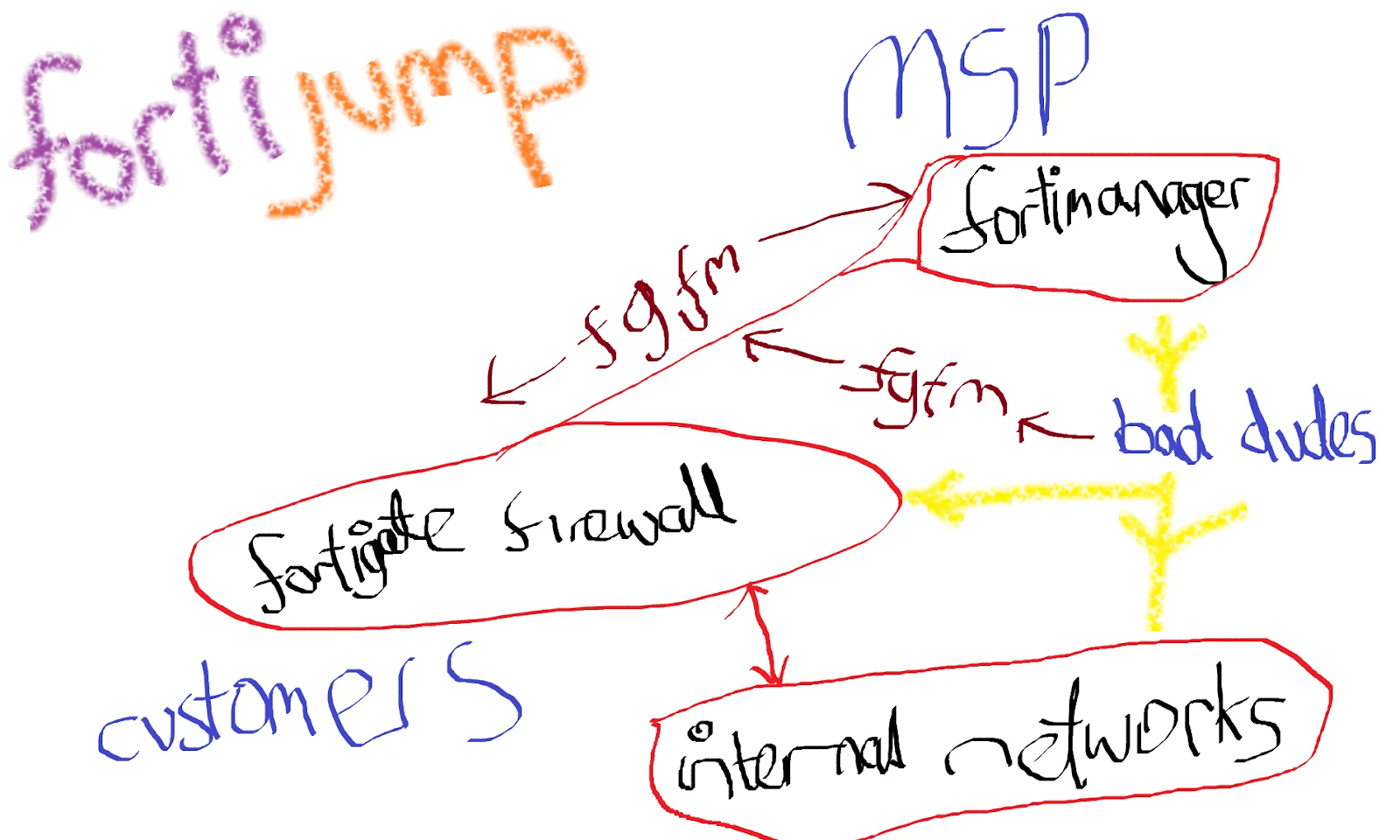
What are the vulnerabilities associated with FortiJump?
On October 23, Fortinet published an advisory (FG-IR-24-423) for FortiJump, assigning a CVE identifier for the flaw.
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2024-47575 | FortiManager Missing authentication in fgfmsd Vulnerability | 9.8 |
What is CVE-2024-47575?
CVE-2024-47575 is a missing authentication vulnerability in the FortiGate to FortiManager (FGFM) daemon (fgfmsd) in FortiManager and FortiManager Cloud.
How severe is CVE-2024-47575?
Exploitation of FortiJump could allow an unauthenticated, remote attacker using a valid FortiGate certificate to register unauthorized devices in FortiManager. Successful exploitation would grant the attacker the ability to view and modify files, such as configuration files, to obtain sensitive information, as well as the ability to manage other devices.
Obtaining a certificate from a FortiGate device is relatively easy:
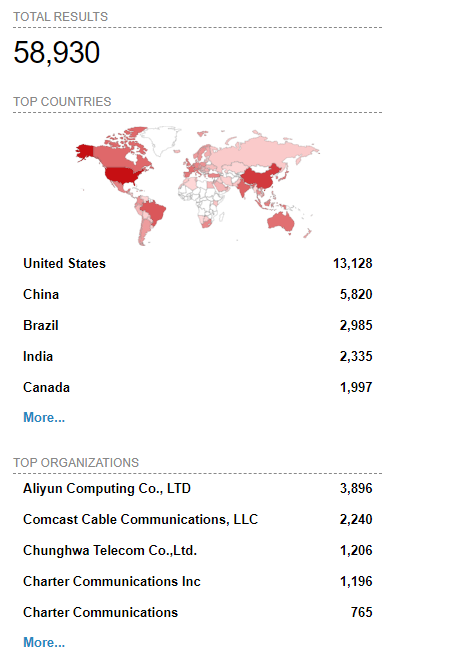
According to results from Shodan, there are nearly 60,000 FortiManager devices that are internet-facing, including over 13,000 in the United States, over 5,800 in China, nearly 3,000 in Brazil and 2,300 in India:
When was FortiJump first disclosed?
There were reports on Reddit that Fortinet proactively notified customers using FortiManager about the flaw ahead of the release of patches, though some customers say they never received any notifications. Beaumont posted a warning to Mastodon on October 13:
Was this exploited as a zero-day?
Yes, according to both Beaumont and Fortinet, FortiJump has been exploited in the wild as a zero-day. Additionally, Google Mandiant published a blog post on October 23 highlighting its collaborative investigation with Fortinet into the “mass exploitation” of this zero-day vulnerability. According to Google Mandiant, they’ve discovered over 50 plus “potentially compromised FortiManager devices in various industries.”
Which threat actors are exploiting FortiJump?
Google Mandiant attributed exploitation activity to a new threat cluster called UNC5820, adding that the cluster has been observed exploiting the flaw since “as early as June 27, 2024.”
Is there a proof-of-concept (PoC) available for this vulnerability/these vulnerabilities?
As of October 23, there are no public proof-of-concept exploits available for FortiJump.
Are patches or mitigations available for FortiJump?
The following table contains a list of affected products, versions and fixed versions.
| Affected Product | Affected Versions | Fixed Version |
|---|---|---|
| FortiManager 6.2 | 6.2.0 through 6.2.12 | Upgrade to 6.2.13 or above |
| FortiManager 6.4 | 6.4.0 through 6.4.14 | Upgrade to 6.4.15 or above |
| FortiManager 7.0 | 7.0.0 through 7.0.12 | Upgrade to 7.0.13 or above |
| FortiManager 7.2 | 7.2.0 through 7.2.7 | Upgrade to 7.2.8 or above |
| FortiManager 7.4 | 7.4.0 through 7.4.4 | Upgrade to 7.4.5 or above |
| FortiManager 7.6 | 7.6.0 | Upgrade to 7.6.1 or above |
| FortiManager Cloud 6.4 | 6.4 all versions | Migrate to a fixed release |
| FortiManager Cloud 7.0 | 7.0.1 through 7.0.12 | Upgrade to 7.0.13 or above |
| FortiManager Cloud 7.2 | 7.2.1 through 7.2.7 | Upgrade to 7.2.8 or above |
| FortiManager Cloud 7.4 | 7.4.1 through 7.4.4 | Upgrade to 7.4.5 or above |
| FortiManager Cloud 7.6 | Not affected | Not Applicable |
Fortinet’s advisory provides workarounds for specific impacted versions if patching is not feasible. These include blocking unknown devices from attempting to register to FortiManager, creating IP allow lists of approved FortiGate devices that can connect to FortiManager and the creation of custom certificates. Generally speaking, it is advised to ensure FGFM is not internet-facing.
Has Tenable released any product coverage for these vulnerabilities?
A list of Tenable plugins for this vulnerability can be found on the individual CVE page for CVE-2024-47575 as they’re released. This link will display all available plugins for this vulnerability, including upcoming plugins in our Plugins Pipeline.
Get more information
- Burning Zero Days: FortiJump FortiManager vulnerability used by nation state in espionage via MSPs
- FortiGuard Labs PSIRT FG-IR-24-423 Advisory
Change Log
Update October 23: The blog has been updated with new information about in-the-wild exploitation and threat actor activity associated with this vulnerability.
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

Satnam Narang
Satnam joined Tenable in 2018. He has over 15 years experience in the industry (M86 Security and Symantec). He contributed to the Anti-Phishing Working Group, helped develop a Social Networking Guide for the National Cyber Security Alliance, uncovered a huge spam botnet on Twitter and was the first to report on spam bots on Tinder. He's appeared on NBC Nightly News, Entertainment Tonight, Bloomberg West, and the Why Oh Why podcast.
Interests outside of work: Satnam writes poetry and makes hip-hop music. He enjoys live music, spending time with his three nieces, football and basketball, Bollywood movies and music and Grogu (Baby Yoda).

Rody Quinlan
Rody Quinlan previously worked at Tenable and in mid 2024 returned as a member of the Security Response Team (SRT). Prior to this he led the Security Operations team at Fenergo, a fintech unicorn, for a number of years delivering a number of functions including incident response, threat intelligence and vulnerability management. He has also worked previously as a Senior Threat & Vulnerability Management Analyst for one of Ireland's pillar banking institutions as well as a security supervisory role in a leading cloud providers data centers for a number of years. He holds and maintains a number of certifications too long to list here but can be found on his LinkedIn and Credly profiles, is an avid learner and usually has at least one course on the go at any given time.
Interests outside of work: Whether he’s holding a recurve or compound bow, Rody enjoys some downtime from screens on the archery range. He also enjoys building props from his favorite films and TV series and is an avid fan of Sir Terry Pratchett's works.

Scott Caveza
Scott joined Tenable in 2012 as a Research Engineer on the Nessus Plugins team. Over the years, he has written hundreds of plugins for Nessus, and reviewed code for even more from his time being a team lead and manager of the Plugins team. Previously leading the Security Response team and the Zero Day Research team, Scott is currently a member of the Security Response team, helping the research organization respond to the latest threats. He has over a decade of experience in the industry with previous work in the Security Operations Center (SOC) for a major domain registrar and web hosting provider. Scott is a current CISSP and actively maintains his GIAC GWAPT Web Application Penetration Tester certification.
Interests outside of work: Scott enjoys spending time with his family, camping, fishing and being outdoors. He also enjoys finding ways to break web applications and home renovation projects.
Related Articles
- Exposure Management
- Vulnerability Management
Cybersecurity News You Can Use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose your subscription option:
Thank You
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose your subscription option:
Thank you
Thank you for your interest in Tenable.io. A representative will be in touch soon.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy.
Your Tenable Vulnerability Management trial also includes Tenable Lumin and Tenable Web App Scanning.
Tenable Vulnerability Management
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
100 assets
Choose your subscription option:
Thank you
Thank you for your interest in Tenable Vulnerability Management. A representative will be in touch soon.
Try Tenable Web App Scanning
Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.
Your Tenable Web App Scanning trial also includes Tenable Vulnerability Management and Tenable Lumin.
Buy Tenable Web App Scanning
Enjoy full access to a modern, cloud-based vulnerability management platform that enables you to see and track all of your assets with unmatched accuracy. Purchase your annual subscription today.
Try Tenable Lumin
Visualize and explore your exposure management, track risk reduction over time and benchmark against your peers with Tenable Lumin.
Your Tenable Lumin trial also includes Tenable Vulnerability Management and Tenable Web App Scanning.
Buy Tenable Lumin
Contact a sales representative to see how Tenable Lumin can help you gain insight across your entire organization and manage cyber risk.
Thank you
Thank you for your interest in Tenable Lumin. A representative will be in touch soon.
Request a demo of Tenable Security Center
Please fill out this form with your contact information.
A sales representative will contact you shortly to schedule a demo.
* Field is required
Request a demo of Tenable OT Security
Get the Operational Technology security you need.
Reduce the risk you don’t.
Request a demo of Tenable Identity Exposure
Continuously detect and respond to Active Directory attacks. No agents. No privileges.
On-prem and in the cloud.
Request a demo of Tenable Cloud Security
Exceptional unified cloud security awaits you!
We’ll show you exactly how Tenable Cloud Security helps you deliver multi-cloud asset discovery, prioritized risk assessments and automated compliance/audit reports.
See
Tenable One
in action
Exposure management for the modern attack surface.
See Tenable Attack Surface Management in action
Know the exposure of every asset on any platform.
Get a demo of Tenable Enclave Security
Please fill out the form with your contact information and a sales representative will contact you shortly to schedule a demo.
Thank You
Thank you for your interest in Tenable Enclave Security. A representative will be in touch soon.
Try Tenable Nessus Professional free
Free for 7 days
Tenable Nessus is the most comprehensive vulnerability scanner on the market today.
NEW - Tenable Nessus Expert
now available
Nessus Expert adds even more features, including external attack surface scanning, and the ability to add domains and scan cloud infrastructure. Click here to Try Nessus Expert.
Fill out the form below to continue with a Nessus Pro trial.
Buy Tenable Nessus Professional
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team.
Buy a multi-year license and save. Add Advanced Support for access to phone, community and chat support 24 hours a day, 365 days a year.
Try Tenable Nessus Expert free
Free for 7 days.
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Already have Tenable Nessus Professional?
Upgrade to Nessus Expert free for 7 days.
Buy Tenable Nessus Expert
Built for the modern attack surface, Nessus Expert enables you to see more and protect your organization from vulnerabilities from IT to the cloud.
Learn How Tenable Helps Achieve SLCGP Cybersecurity Plan Requirements
Tenable solutions help fulfill all SLCGP requirements. Connect with a Tenable representative to learn more.
如有侵权请联系:admin#unsafe.sh