
In April, we reported that a “substantial proportion” of Americans may have had their health and personal data stolen in the Change Healthcare breach. That was based on a report provided by the UnitedHealth Group after the February cyberattack on its subsidiary Change Healthcare.
The attack on Change Healthcare, which processes about 50% of US medical claims, was one of the worst ransomware attacks against American healthcare and caused widespread disruption in payments to doctors and health facilities.
UnitedHealth CEO Andrew Witty estimated the attack compromised the data of a third of US individuals when he testified before the Senate Finance Committee on Capitol Hill on May 1, 2024 in Washington, DC.
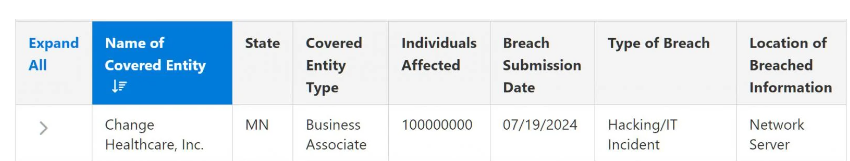
He wasn’t exaggerating. Yesterday, Change Healthcare reported a number of 100,000,000 affected individuals on the breach portal of the US Department of Health and Human Services (HHS).
The Office for Civil Rights (OCR) at the HHS confirmed that it prioritized and opened investigations of Change Healthcare and UnitedHealth Group, focused on whether a breach of protected health information (PHI) occurred and on the entities’ compliance with the Health Insurance Portability and Accountability Act of 1996 (HIPAA) Rules. OCR did this because of the cyberattack’s unprecedented impact on patient care and privacy.
On July 19, 2024, Change Healthcare filed a breach report with OCR that identified 500 individuals as the “approximate number of individuals affected.” This is the minimum number of individuals affected that results in a posting of a breach on the HHS Breach Portal, and it was perhaps cited because Change Healthcare still needed to determine the actual number of impacted users.
Acting Director of the Office for Civil Rights at the US Department of Health & Human Services Melanie Fontes Rainer said about 140 million people were affected by large breaches in 2023, up from 51 million in 2022. And 2024 looks even worse, she added:
“And this year, with both the Change breach and Ascension breach, we expect that number to potentially double or go higher.”
Affected people can visit a dedicated website at changecybersupport.com to get more information or call 1-866-262-5342 to set up free credit monitoring and identity theft protection.
Protecting yourself after a data breach
There are some actions you can take if you are, or suspect you may have been, the victim of a data breach.
- Check the vendor’s advice. Every breach is different, so check with the vendor to find out what’s happened, and follow any specific advice they offer.
- Change your password. You can make a stolen password useless to thieves by changing it. Choose a strong password that you don’t use for anything else. Better yet, let a password manager choose one for you.
- Enable two-factor authentication (2FA). If you can, use a FIDO2-compliant hardware key, laptop or phone as your second factor. Some forms of two-factor authentication (2FA) can be phished just as easily as a password. 2FA that relies on a FIDO2 device can’t be phished.
- Watch out for fake vendors. The thieves may contact you posing as the vendor. Check the vendor website to see if they are contacting victims, and verify the identity of anyone who contacts you using a different communication channel.
- Take your time. Phishing attacks often impersonate people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
- Consider not storing your card details. It’s definitely more convenient to get sites to remember your card details for you, but we highly recommend not storing that information on websites.
- Set up identity monitoring. Identity monitoring alerts you if your personal information is found being traded illegally online, and helps you recover after.
Malwarebytes has a new free tool for you to check how much of your personal data has been exposed online. Submit your email address (it’s best to give the one you most frequently use) to our free Digital Footprint scan and we’ll give you a report and recommendations.
