
Many pieces of malware found over the years have been complex and difficult to find. Attackers often obfuscate their code to make it harder to track. Some pieces of malware require extensive reviews to uncover. But in other instances, that is not always the case. Threat actors find new ways to inject malware to avoid detection, and in some situations, they hide their malicious code in plain sight. Recently, I discovered a cleverly disguised malicious redirect, where attackers leveraged a popular redirect plugin in a WordPress site. By routing through an intermediary domain, they initiated the redirect process in a way that evaded detection.
Let’s review this injection more in depth.
Redirect Symptoms
A client recently came to us concerned that their site was redirecting to an Indonesian gambling website, as seen below:
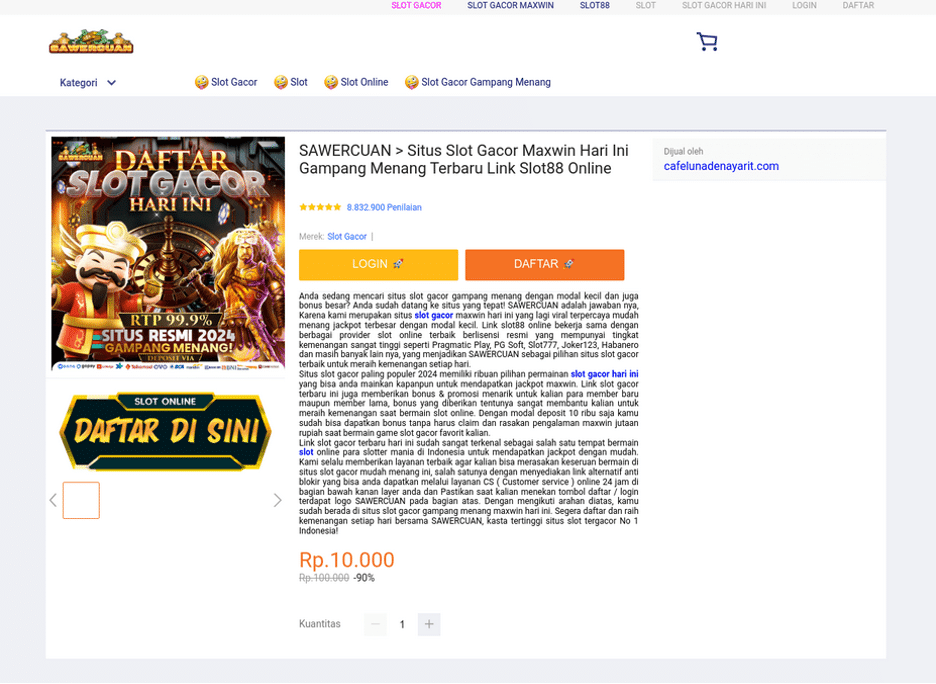
Upon reviewing the symptoms, the infected website took a handful of seconds to load before the redirect occurred. Additionally, it occurred even with all javascript disabled, indicating it was not a script injection. The gambling domain the victim’s website redirected to was surfatech-tis[.]com. However, I came up empty handed when searching for this domain in the files and database. How could this be? In other samples found in the past, redirects like this that cannot be found by searching the domain via plain text are usually obfuscated in some fashion. More extensive reviews were performed and yet, I still came up short. Another tactic I decided to employ was to look at the recently modified files. That is when I stumbled upon a plugin called 301 redirects, which was added 2 days prior to my search. I decided to look at the redirects added in that plugin which revealed the malicious redirect chain.
Uncovering the redirect via a popular redirect plugin
The 301 redirect plugin is a popular, verified tool that’s legitimately used in most cases. However, I decided to take a closer look inside to be sure. Inside the 301 redirect plugin was the domain uad.uinfasbengkulu[.]ac[.]id. Initially, I didn’t think this was the cause of the malicious redirect, until I remembered that the domain extension, .id, is an Indonesian based extension. Not only was the client’s site not based in Indonesia, redirects to Indonesian gambling sites are a common tactic attackers use when exploiting vulnerable sites.
Sure enough, after loading the domain uad.uinfasbengkulu[.]ac[.]id through https://urlscan.io, a sandbox testing site, it landed on surfatech-tis[.]com, which was the domain our client’s website was redirecting to. The attackers likely accessed the victim’s site through a vulnerability or compromised WordPress admin account, then proceeded to insert the intermediary domain in the redirect plugin after installing it.
Moral of the story
To wrap up this case, we can conclude that not all malware relies on heavy obfuscation. Threat actors are constantly evolving, and developing new waves of infections. Some of these tactics include hiding malicious content in plain sight, through a popular verified plugin as seen above. This means that even seemingly harmless elements on a site can carry hidden risks. It is crucial that WordPress site owners take every possible step to protect their sites and stay vigilant against potential threats. Mitigation steps to better protect a WordPress site can be found below.
Mitigation steps
To mitigate risk, there are a number of steps you can take to protect your website from serving malware to your clients:
- Keep your plugins, themes, and website software up-to-date: Always patch to the latest version to help mitigate risk known software vulnerabilities. Website visitors should be sure to keep their browser and operating system up to date as well.
- Enforce unique passwords for all of your accounts: That includes credentials for sFTP, database, cPanel, and WordPress admin users.
- Remove WordPress admin users no longer in use: That includes credentials for sFTP, database, cPanel, and admin users.
- Periodically check WordPress admin users in your dashboard: Ensure that you recognize all WordPress admin users in your dashboard and remove any that are unrecognizable.
- Review installed plugins: Check that all plugins are ones that have been installed by you or your developer.
- Regularly scan for backdoors and malware: That means scanning at the server and client level to identify any malicious injections, SEO spam, or backdoors that may be lurking on your site.
- Monitor your logs for indicators of compromise: Regularly check for unusual or suspicious behavior and consider using a file integrity monitoring system on your website.
- Get a web application firewall (WAF): Firewalls can help mitigate bad bots, prevent brute force attacks, and detect attacks in your environment, which are features the Sucuri firewall provides.
And if you believe your site has been compromised or injected with malicious scripts, we can help! Reach out to our support team for assistance and we can get the malware cleaned up for you.
Kayleigh Martin is a Security Analyst at Sucuri who joined the company in 2020. Kayleigh's job is to clean infected websites and hunt for undetected malware. She has a versatile technical background working with infected websites, investigating server issues, and troubleshooting broken sites. When Kayleigh isn't hunting for undetected malware, she might be spending time with her family, exploring beaches, or cooking new cuisines.
