2024-10-31 08:16:9 Author: isc.sans.edu(查看原文) 阅读量:2 收藏
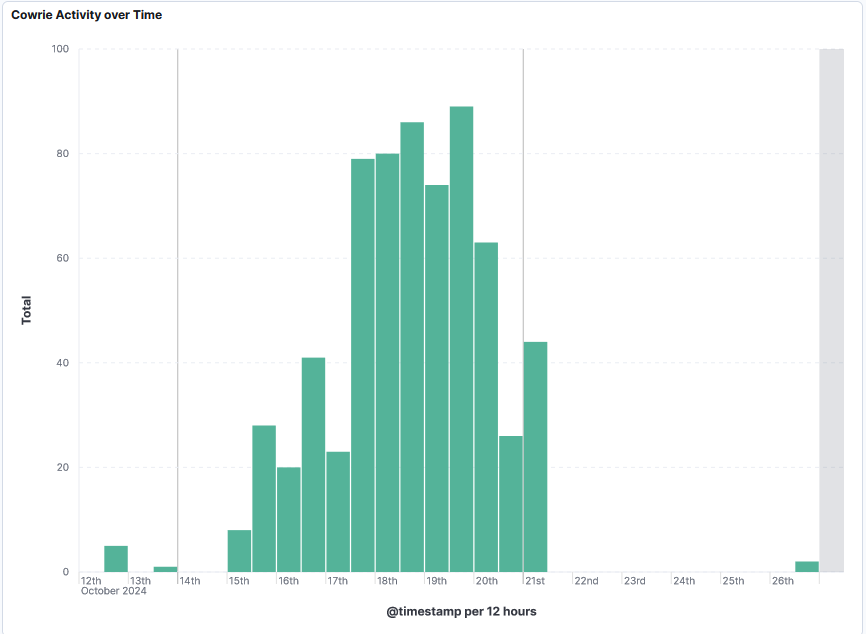
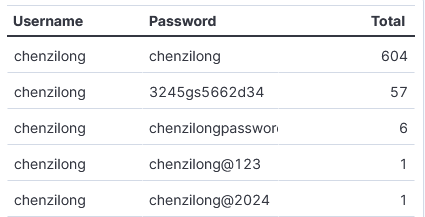
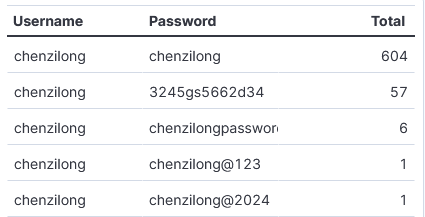
After reviewing the Top 10 Not So Common SSH Usernames and Passwords [1] published by Johannes 2 weeks ago, I noticed activity by one in his list that we don't really know what it is. Beginning 12 October 2024, my DShield sensor started storing one of the usernames mentioned in his diary that I had never seen before (I have over a year of data). The username chenzilong has been used with 5 different passwords including, some combination with the same username. So far, this account activity has been used with 302 different IPs.
Some of the activity appears to have succeeded to login the DShield sensor but it appears to just login and leave, no other activity noted. It only appears to be testing.
Reviewing each of the 25 IPs with successfully login, the bot (I'm assuming it is), didn't execute any commands after each successful login. This was no data transferred.
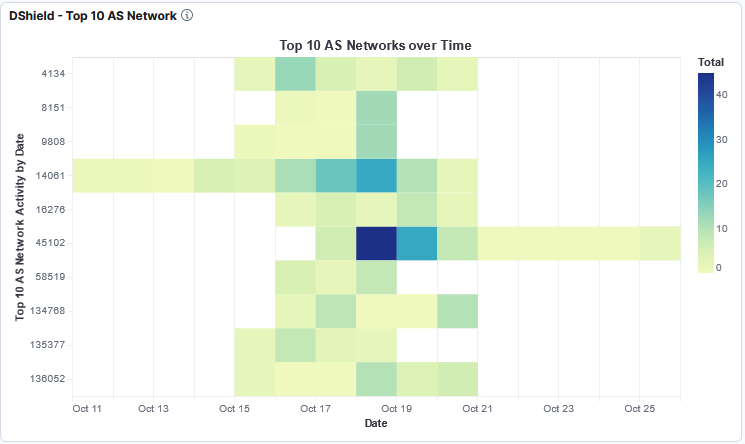
This picture shows the ASN traffic distribution with ASN 45102 (Alibaba US Technology) being the most active during that period.
[1] https://isc.sans.edu/diary/The+Top+10+Not+So+Common+SSH+Usernames+and+Passwords/31360
[2] https://github.com/bruneaug/DShield-SIEM/tree/main
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
如有侵权请联系:admin#unsafe.sh