2024-11-1 19:30:45 Author: cyble.com(查看原文) 阅读量:5 收藏
Overview
Cyble Research and Intelligence Labs (CRIL) researchers investigated 17 vulnerabilities and nine dark web exploits during the period of Oct. 23-29, and highlighted seven vulnerabilities that merit high-priority attention from security teams.
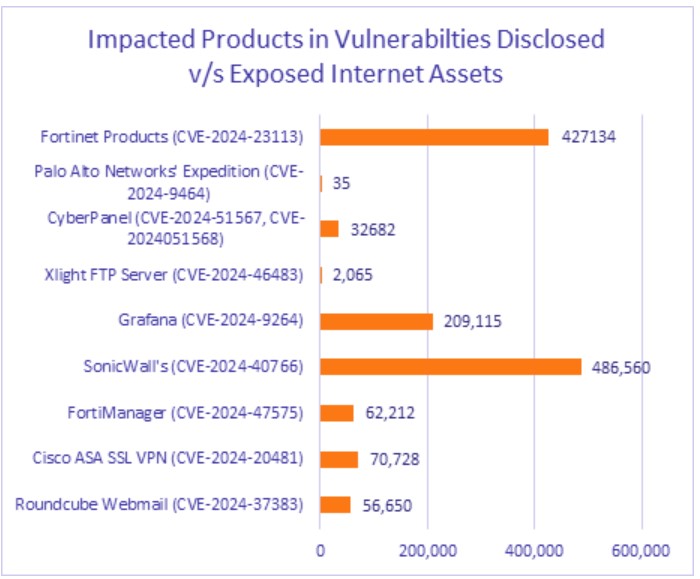
This week’s IT vulnerability report affects an unusually high number of exposed devices and instances: Vulnerabilities in Fortinet, SonicWall, and Grafana Labs can be found in more than 1 million web-facing assets, and a pair of 10.0-severity vulnerabilities in CyberPanel have already been mass-exploited in ransomware attacks.
Security teams should assess which of these vulnerabilities are present in their environments and the risks they pose and apply patches and mitigations promptly.
The Week’s Top IT Vulnerabilities
Here are the top IT vulnerabilities identified by Cyble threat intelligence researchers this week.
CVE-2024-40766: SonicWall SonicOS
CVE-2024-40766 is a 9.8-severity improper access control vulnerability in the administrative interface and controls in the SonicOS operating system used for managing SonicWall’s network security appliances and firewalls. Managed security firm Arctic Wolf has reported that Fog and Akira ransomware operators are increasingly exploiting this vulnerability in SSL VPN environments to gain an initial foothold to compromise networks.
Cyble has detected more than 486,000 internet-exposed devices with this vulnerability, making it a critically important priority for security teams.
CVE-2024-47575 and CVE-2024-23113: Fortinet FortiOS and FortiManager
Fortinet environments are under attack from threat actors exploiting a pair of recent 9.8-severity vulnerabilities: CVE-2024-47575, also known as “FortiJump,” is a vulnerability in Fortinet FortiManager that allows an attacker to execute arbitrary code or commands via specially crafted requests. Recently, researchers disclosed that the threat actor tracked as UNC5820 has been exploiting the flaw since at least June 27, 2024.
For more than a week before the October 23 disclosure of CVE-2024-47575, security researchers were concerned that Fortinet was slow in disclosing a FortiManager zero-day known to be under exploitation. However, it appears that a week before the CVE was released, Fortinet notified customers of a FortiManager vulnerability and provided some recommended mitigations. Some FortiManager customers reported that they didn’t get that communication, suggesting a need for a clearer advisory process. Fortinet update its guidance on the vulnerability yesterday.
Cyble researchers also observed threat actors on a cybercrime forum discussing exploits of CVE-2024-23113, a critical vulnerability in multiple versions of FortiOS, FortiProxy, FortiPAM, and FortiSwitchManager that allows remote, unauthenticated attackers to execute arbitrary code through specially crafted requests.
Cyble has identified 62,000 exposed instances of the FortiManager vulnerability, and 427,000 internet-facing Fortinet devices exposed to CVE-2024-23113 (see graphic below).

CVE-2024-9264: Grafana Labs
CVE-2024-9264 is a 9.4-severity vulnerability in the SQL Expressions experimental feature of Grafana, an open-source analytics and monitoring platform developed by Grafana Labs. It is designed to visualize and analyze data from various sources through customizable dashboards. This feature allows for the evaluation of ‘duckdb’ queries containing user input. These queries are insufficiently sanitized before being passed to ‘duckdb,’ leading to a command injection and local file inclusion vulnerability.
Cyble reported 209,000 internet-facing Grafana instances exposed to the vulnerability.
CVE-2024-51567 and CVE-2024-51568: CyberPanel
CVE-2024-51567 and CVE-2024-51568 are critical vulnerabilities in CyberPanel, an open-source web hosting control panel designed to simplify server management, particularly for those using the LiteSpeed web server. NVD has yet to rate the vulnerabilities, but MITRE has assigned them each a 10.0. CVE-2024-51567 is a flaw in upgrademysqlstatus in databases/views.py, which allows remote attackers to bypass authentication and execute arbitrary commands via /dataBases/upgrademysqlstatus by bypassing secMiddleware (which is only for a POST request) and using shell metacharacters in the statusfile property, and was exploited in the wild in October in a massive PSAUX ransomware attack.
CVE-2024-51568 is a command Injection flaw via completePath in the ProcessUtilities.outputExecutioner() sink.
Nearly 33,000 CyberPanel instances are exposed to these vulnerabilities, more than half of which have been targeted in mass ransomware and cryptominer attacks.
CVE-2024-46483: Xlight FTP Server
CVE-2024-46483 is a critical integer overflow vulnerability still undergoing analysis that affects Xlight FTP Server, a high-performance file transfer server for Windows designed to facilitate secure and efficient FTP and SFTP (SSH2) file transfers. The flaw lies in the packet parsing logic of the SFTP server, which can lead to a heap overflow with attacker-controlled content. Multiple organizations across various sectors use this server because of its Active Directory and LDAP integration functionalities. Cyble assesses that attackers could leverage this vulnerability in campaigns due to the availability of public Proof of Concepts (PoC).
Vulnerabilities and Exploits on Underground Forums
CRIL researchers observed multiple Telegram channels and cybercrime forums where channel administrators shared or discussed exploits weaponizing a number of vulnerabilities, some of which were discussed above. Others include:
CVE-2024-9464: A critical OS command injection vulnerability found in Palo Alto Networks’ Expedition tool, which allows an attacker to execute arbitrary OS commands as root, potentially leading to the disclosure of sensitive information.
CVE-2024-42640: A critical vulnerability affecting the angular-base64-upload library, specifically in versions prior to v0.1.21. This vulnerability allows remote code execution (RCE) through the demo/server.php endpoint, enabling attackers to upload arbitrary files to the server.
CVE-2024-3656: A high-risk vulnerability affecting Keycloak versions prior to 24.0.5. The vulnerability allows low-privilege users to access certain endpoints in Keycloak’s admin REST API, enabling them to perform actions reserved for administrators.
CVE-2024-9570: A critical buffer overflow vulnerability in the D-Link DIR-619L B1 router, specifically in firmware version 2.06, occurs in the ‘formEasySetTimezone’ function. The issue arises when the ‘curTime’ argument is manipulated, leading to a situation where an attacker can execute arbitrary code remotely.
CVE-2024-46538: A critical cross-site scripting (XSS) vulnerability in pfSense version 2.5.2 allows attackers to execute arbitrary web scripts or HTML by injecting a ‘crafted payload’ into the $pconfig variable, specifically through the ‘interfaces_groups_edit.php’ file.
CVE-2024-21305: A vulnerability identified as a Hypervisor-Protected Code Integrity (HVCI) Security Feature Bypass allows attackers to circumvent HVCI protections, enabling the execution of unauthorized code on affected systems running versions of Windows and Windows Server OS.
CVE-2024-23692: A critical vulnerability affecting the Rejetto HTTP File Server (HFS) that allows unauthenticated remote code execution (RCE) through a command injection flaw.
Cyble Recommendations
To protect against these vulnerabilities and exploits, organizations should implement the following best practices:
- To mitigate vulnerabilities and protect against exploits, regularly update all software and hardware systems with the latest patches from official vendors.
- Develop a comprehensive patch management strategy that includes inventory management, patch assessment, testing, deployment, and verification. Automate the process where possible to ensure consistency and efficiency.
- Divide your network into distinct segments to isolate critical assets from less secure areas. Use firewalls, VLANs, and access controls to limit access and reduce the attack surface exposed to potential threats.
- Create and maintain an incident response plan that outlines procedures for detecting, responding to, and recovering from security incidents. Regularly test and update the plan to ensure its effectiveness and alignment with current threats.
- Implement comprehensive monitoring and logging solutions to detect and analyze suspicious activities. Use SIEM (Security Information and Event Management) systems to aggregate and correlate logs for real-time threat detection and response.
- Subscribe to security advisories and alerts from official vendors, CERTs, and other authoritative sources. Regularly review and assess the impact of these alerts on your systems and take appropriate actions.
- Conduct regular vulnerability assessment and penetration testing (VAPT) exercises to identify and remediate vulnerabilities in your systems. Complement these exercises with periodic security audits to ensure compliance with security policies and standards.
Conclusion
These vulnerabilities highlight the urgent need for security teams to prioritize patching critical vulnerabilities in major products and those that could be weaponized as entry points for wider attacks. With increasing discussions of these exploits on dark web forums, organizations must stay vigilant and proactive. Implementing strong security practices is essential to protect sensitive data and maintain system integrity.
Related
如有侵权请联系:admin#unsafe.sh