Detecting Secrets with Noir - The PassiveScan Advantage
Hello, security enthusiasts! Today, we’re diving into the exciting new features of OWASP Noir v0.18, particularly focusing on the PassiveScan functionality. This update enhances Noir’s capabilities; while it used to only detect endpoints, now it can also identify secrets and other security issues based on rule files concurrently. Here’s how you can leverage this feature:
What is Noir?
OWASP Noir is an open-source project dedicated to identifying vulnerabilities in software systems. It specializes in enhancing whitebox security testing and security pipelines by providing the ability to discover API endpoints, web endpoints, and other potential entry points within source code.
Want to learn more? Check out our Documents and OWASP Project Documents.
Noir’s PassiveScan
With version v0.18.x, Noir introduces the PassiveScan feature, which can be activated using the -P or --passive-scan flag. This functionality enables the tool to scan for passive rules in predefined paths or custom locations:
| OS | Path |
|---|---|
| MacOS: | ~/.config/noir/passive_rules/ |
| Linux: | ~/.config/noir/passive_rules/ |
| Windows: | %APPDATA%\noir\passive_rules\ |
Each rule follows the YAML format, and you can explore various rules at OWASP Noir Passive Rules. For example, a rule for detecting a PRIVATE KEY would look something like this:
id: private-key
info:
name: "Detect PRIVATE_KEY"
author:
- "hahwul"
severity: critical
description: "Detects the presence of PRIVATE_KEY in the code"
reference:
- ""
matchers-condition: or
matchers:
- type: word
patterns:
- "PRIVATE_KEY"
- "-----BEGIN PRIVATE KEY-----"
condition: or
- type: regex
patterns:
- "PRIVATE_KEY\\s*=\\s*['\"]?[^'\"]+['\"]?"
- "-----BEGIN PRIVATE KEY-----[\\s\\S]*?-----END PRIVATE KEY-----"
condition: or
category: secret
techs:
- '*'
Preparing the Rules
To make use of these rules efficiently, you might want to clone the noir-passive-rules repository into the default path:
git clone https://github.com/owasp-noir/noir-passive-rules ~/.config/noir/passive_rules/
Alternatively, you can clone it to another directory and update Noir’s configuration to point to this new location:
# cat ~/.config/noir/config.yaml
passive_scan: true
passive_scan_path: ["~/repositories/noir-passive-rules"]
Running the Scan
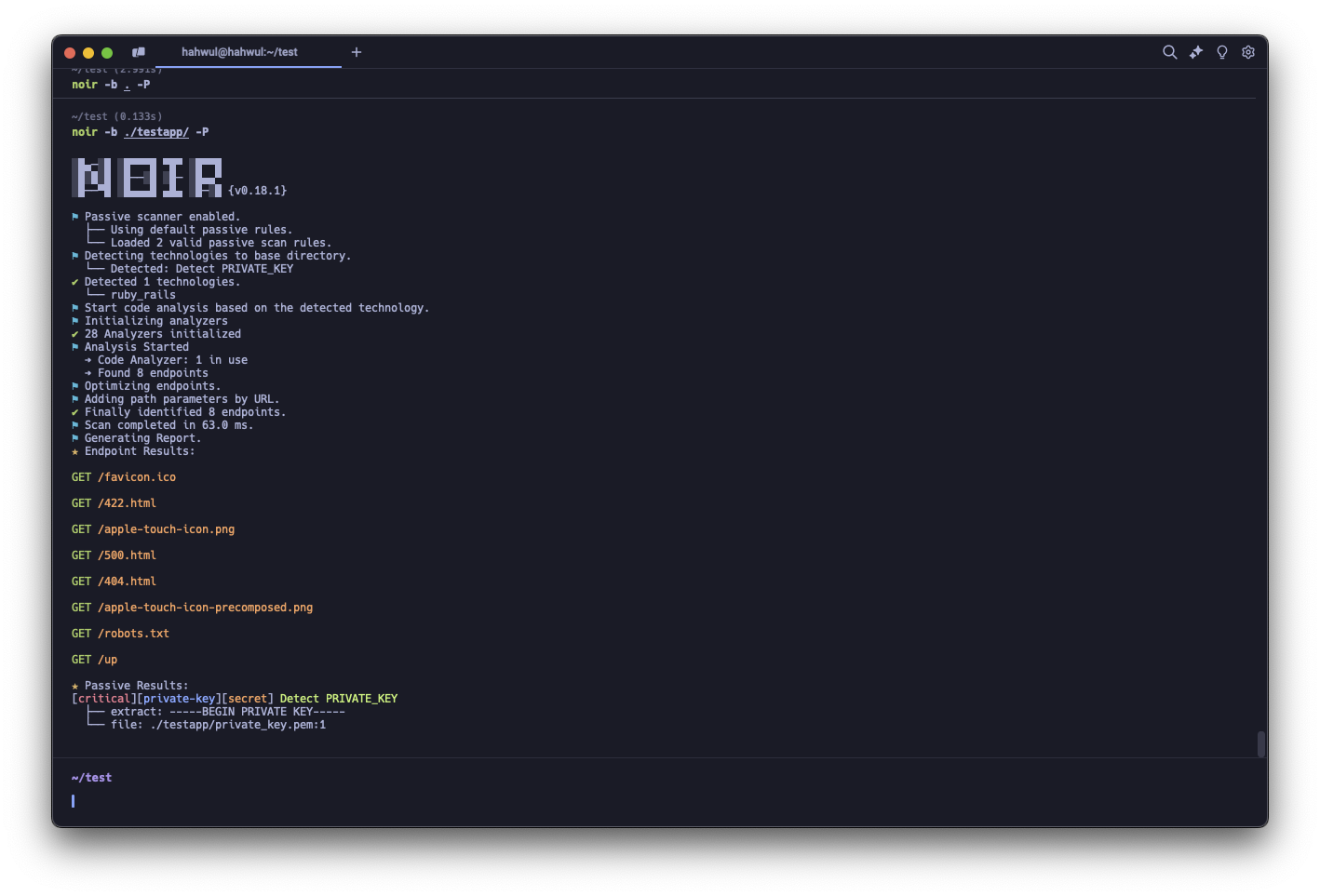
Once configured, you can initiate a scan with the -P flag:
Let’s set up a simple test environment with a Rails app and a private key to see this in action:
rails new testapp
openssl genrsa -out ./testapp/private_key.pem 1024
Now, run Noir:
You’ll see that Noir not only detects the endpoints but also identifies the PRIVATE_KEY file through PassiveScan.
If integration with other tools is needed, you can adjust the output format, for instance, to JSON:
noir -b ./testapp/ -P -f json --no-log
This will provide results including both endpoint information and passive scan findings, like this:
{
"endpoints": [
{
"url": "/favicon.ico",
"method": "GET",
"params": [],
"details": {
"code_paths": [
{
"path": "./testapp/public/favicon.ico"
}
]
},
"protocol": "http",
"tags": []
},
{
"url": "/422.html",
"method": "GET",
"params": [],
"details": {
"code_paths": [
{
"path": "./testapp/public/422.html"
}
]
},
"protocol": "http",
"tags": []
},
{
"url": "/apple-touch-icon.png",
"method": "GET",
"params": [],
"details": {
"code_paths": [
{
"path": "./testapp/public/apple-touch-icon.png"
}
]
},
"protocol": "http",
"tags": []
},
{
"url": "/500.html",
"method": "GET",
"params": [],
"details": {
"code_paths": [
{
"path": "./testapp/public/500.html"
}
]
},
"protocol": "http",
"tags": []
},
{
"url": "/404.html",
"method": "GET",
"params": [],
"details": {
"code_paths": [
{
"path": "./testapp/public/404.html"
}
]
},
"protocol": "http",
"tags": []
},
{
"url": "/apple-touch-icon-precomposed.png",
"method": "GET",
"params": [],
"details": {
"code_paths": [
{
"path": "./testapp/public/apple-touch-icon-precomposed.png"
}
]
},
"protocol": "http",
"tags": []
},
{
"url": "/robots.txt",
"method": "GET",
"params": [],
"details": {
"code_paths": [
{
"path": "./testapp/public/robots.txt"
}
]
},
"protocol": "http",
"tags": []
},
{
"url": "/up",
"method": "GET",
"params": [],
"details": {
"code_paths": [
{
"path": "./testapp//config/routes.rb"
}
]
},
"protocol": "http",
"tags": []
}
],
"passive_results": [
{
"id": "private-key",
"info": {
"name": "Detect PRIVATE_KEY",
"author": [
"hahwul"
],
"severity": "critical",
"description": "Detects the presence of PRIVATE_KEY in the code",
"reference": [
""
]
},
"category": "secret",
"techs": [
"*"
],
"file_path": "./testapp/private_key.pem",
"line_number": 1,
"extract": "-----BEGIN PRIVATE KEY-----"
}
]
}
By integrating PassiveScan into your security checks, you not only enhance endpoint detection but also significantly improve your ability to uncover hidden security vulnerabilities.
Stay secure, and happy scanning!
如有侵权请联系:admin#unsafe.sh