2024-11-4 18:45:0 Author: lab.wallarm.com(查看原文) 阅读量:11 收藏
In a concerning trend, cybercriminals are leveraging DocuSign's APIs to send fake invoices that appear strikingly authentic. Unlike traditional phishing scams that rely on deceptively crafted emails and malicious links, these incidents use genuine DocuSign accounts and templates to impersonate reputable companies, catching users and security tools off guard.

The Unusual Suspects: Beyond Traditional Phishing
Typical phishing attacks often involve spoofed emails that mimic trusted brands, luring victims into clicking malicious links or providing sensitive information, such as the login and password to your bank account. Email and anti-spam filters are constantly getting better at flagging these tactics for users.
When malicious emails actually come from trusted services, it makes them much harder to identify. Attackers have used different online services before, such as sharing documents from Google docs. These latest incidents use the e-signing service Docusign to deliver malicious content.
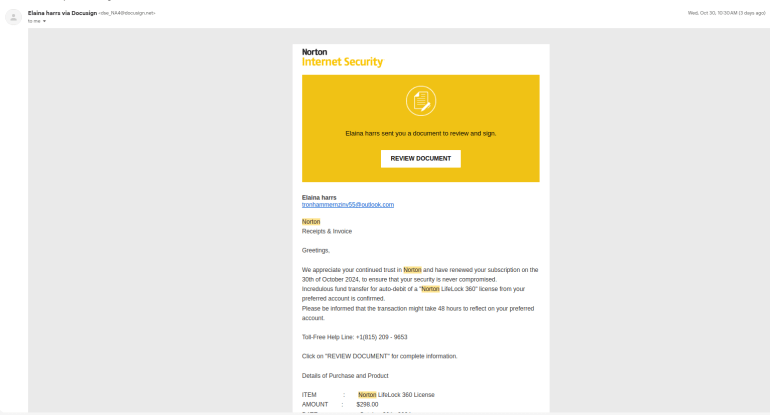
Here’s how it works. An attacker creates a legitimate, paid DocuSign account that allows them to change templates and use the API directly. The attacker employs a specially crafted template mimicking requests to e-sign documents from well known brands, mostly software companies; for example, Norton Antivirus.

These fake invoices may contain accurate pricing for the products to make them appear authentic, along with additional charges, like a $50 activation fee. Other scenarios include direct wire instructions or purchase orders.
If users e-sign this document, the attacker can use the signed document to request payment from the organization outside of DocuSign or send the signed document through DocuSign to the finance department for payment.
Other attempts have included different invoices with different items, usually following the same pattern of getting signatures for invoices that then authorize payment into the attackers bank accounts.
Because the invoices are sent directly through DocuSign's platform, they look legitimate to the email services and spam/phishing filters. There are no malicious links or attachments; the danger lies in the authenticity of the request itself.
Over the past five months, user reports of such malicious campaigns have noticeably increased and DocuSign's community forums have seen a surge in discussions about fraudulent activities. This thread is one example: Phishing Emails from docusign.net Domain
These user reports highlight a worrying pattern: attackers are not just impersonating companies, but are embedding themselves within legitimate communication channels to execute their attacks.
Abusing DocuSign's APIs: Automation at Scale
The longevity and breadth of the incidents reported in DocuSign’s community forums clearly demonstrate that these are not one-off, manual attacks. In order to carry out these attacks, the perpetrators must automate the process. DocuSign offers APIs for legitimate automation, which can be abused for these malicious activities. Wallarm security researchers were alerted to this activity because we received just such an email.
By utilizing endpoints like the Envelopes: create API, an attacker can send out large volumes of fraudulent invoices with minimal manual intervention.
DocuSign's API-friendly environment, while beneficial for businesses, inadvertently provides a way for malicious actors to scale their operations. With paid accounts and access to official templates, attackers can customize invoices to match the branding of target companies, including unauthorized use of trademarks like Norton's.

Protecting Your Organization
Wallarm security researchers emphasize that this threat is not limited to DocuSign. Other e-signature and document services could be equally vulnerable to similar exploitation tactics. To safeguard your organization, they recommend:
For organizations:
- Verifying Sender Credentials: Always double-check the sender's email address and any associated accounts for legitimacy (not an email sender, but Reply-To email field, private emails like @outlook or Gmail should raise your concerns).
- Requiring Internal Approvals: Implement strict internal procedures for approving purchases and financial transactions, involving multiple team members where possible.
- Conducting Awareness Training: Educate employees about this new type of threat, highlighting the importance of skepticism even when communications appear legitimate.
- Monitoring for Anomalies: Keep an eye on unexpected invoices or requests, especially those that include unusual charges or fees. Even last names starting with the lowercase should raise attention.
- Follow DocuSign’s Advice: DocuSign provides guidance on how to avoid phishing.
For Service Providers:
- Conducting Threat Modeling: Understanding where your APIs might be abused is key to implementing effective security controls. Conduct regular threat modeling exercises to identify potential points of abuse.
- Implementing API Rate: Rate limiting isn’t a new control, but applying rate limiting to specific API endpoints is a more sophisticated application of the capability. If you understand how your APIs are used, you can implement smarter rate limits to prevent attackers from scaling.
- Detecting API Abuse: API abuse is hard to detect, but there are tools that can profile the behavior of your APIs and identify anomalous activities.
Conclusion
The exploitation of trusted platforms like DocuSign through their APIs marks a concerning evolution in cybercriminal strategies. By embedding fraudulent activities within legitimate services, attackers increase their chances of success while making detection more challenging. Organizations must adapt by enhancing their security protocols, prioritizing API security, and fostering a culture of vigilance.
Book a demo of our cutting-edge solutions to see how Wallarm can help your organization.
如有侵权请联系:admin#unsafe.sh