TOPqw Webportal is a web application developed by bit baltic information technologies GmbH for social service providers such as local authorities. It can be used to publicly view information about various facilities. For providers and their facilities, there is a login-protected area in which services can be adjusted, statistics viewed and various documents exchanged.
The software is used by over 12 federal states all over Germany and the application stores sensitive personal information about citizens as well as confidential documents such as applications for social matters.
As part of two penetration tests G DATA ADAN conducted, we identified some partly critical vulnerabilities and for five of the found vulnerabilities we applied for and received CVEs.
bit baltic information technologies GmbH reacted quickly when notified of the vulnerabilities and fixed them immediately. GD ADAN followed the principles of Responsible Disclosure when releasing the CVEs.
Overview of the CVEs
| CVE Number | Name | Severity |
|---|---|---|
| CVE-2024-45876 | Unauthenticated SQL Injection | Critical |
| CVE-2024-45875 | Authenticated SQL Injection | High |
| CVE-2024-45877 | Broken Access Control | High |
| CVE-2024-45879 | Stored Cross-Site Scripting (XSS) in “QWKalkulation” | Medium |
| CVE-2024-45878 | Stored Cross-Site Scripting (XSS) in “Stammdaten” | Medium |
CVEs in Detail
Unauthenticated SQL Injection (CVE-2024-45876)
The login form of baltic-it TOPqw Webportal v1.35.283.2 in /Apps/TOPqw/Login.aspx is vulnerable to SQL injection. The vulnerability exists in the POST parameter txtUsername, which allows the manipulation of SQL queries. By exploiting this, it was possible to gain complete access over the database.
Finding the SQL injection was actually quite simple. If a single quote (‘) was used in the username during the login, an SQL error message was returned. Figure 01 shows such a request using Test as the username. The response contains a StackTrace with the SQL error message.
Thefore, this can be considered an error-based SQL injection. sqlmap was used to easily prove exploitability. Figure 02 shows a portion of the sqlmap enumerations. In addition to names, addresses, email addresses, and hashed passwords, files stored in the database could be accessed. However, it was not possible to achieve remote code execution (xp_cmdshell was deactivated 😔) or write files to the server.
Authenticated SQL Injection (CVE-2024-45875)
The SaveNewUser function in TOPqw Webportal v1.35.287.1 in /Apps/TOPqw/BenutzerManagement.aspx/SaveNewUser, is vulnerable to an authenticated SQL injection. The JSON object Username allows the manipulation of SQL queries. By exploiting this, it was possible to gain complete access over the database.
If an administrative user creates a new user in the TOPqw Webportal and enters a single quote (‘) into the value of the JSON object Username, a 500 HTTP Error is returned. To illustrate this, the payload 'foobar123456 was used in the JSON object, as can be seen in Figure 03:
The single quote breaks out of the syntax of the current SQL query and this generates a server-side error. The existence of the vulnerability can be verified by the fact that if the same value with two single quotes (“) is inserted at the beginning of the username, the application responds with a 200 HTTP and successfully creates the new user. For demonstration purposes, the payload ''foobar123456 was used for this, as shown in Figure 04:
This is due to the fact that two single quotes preserve the syntax of the SQL query and no error occurs. This demonstrates typical behavior of a SQL injection vulnerability.
After detailed investigation, a time-based blind SQL injection vulnerability was identified in this function. For easy exploitation of the vulnerability, the tool sqlmap was used. Figure 05 shows the output of sqlmap with the malicious payload that was used to detect the vulnerability:
As can be seen in the output, sqlmap used the following payload to verify the vulnerability:
"Username":"123' AND 2867=(SELECT COUNT(*) FROM sysusers AS sys1,sysusers AS sys2,sysusers AS sys3,sysusers AS sys4,sysusers AS sys5,sysusers AS sys6,sysusers AS sys7) AND 'Zfbu'='Zfbu"
Let’s take a deep dive into understanding this payload. This time-based blind SQL injection payload consists of the following components:
Explanation of the Components:
-
123':- The single quote (
') is intended to close a previous SQL string or value, allowing us to inject our own SQL code.
- The single quote (
-
AND 2867=(SELECT COUNT(*) FROM sysusers AS sys1, sysusers AS sys2, sysusers AS sys3, sysusers AS sys4, sysusers AS sys5, sysusers AS sys6, sysusers AS sys7):-
This condition checks whether the value
2867matches the result of the followingSELECT COUNT(*)expression. -
The query counts the combinations of all rows in the system table
sysusersby using multiple aliases (sys1throughsys7). -
By using
COUNT(*)with multiple joins across the aliases of thesysuserstable, the query calculates a large number of combinations. If the database configuration and the number of users insysusersproduce this value, the condition2867 = ...will evaluate toTRUE.
-
-
AND 'Zfbu'='Zfbu:-
This condition is always true since
'Zfbu'is equal to'Zfbu'. -
It primarily serves to close the SQL syntax correctly and ensure that the payload is syntactically valid.
-
As indicated by Figure 05, sqlmap enumerated six different databases and at this point, we were able to extract all data from these databases. In addition to names, addresses, email addresses, and hashed passwords, files stored in the database could be accessed. However, it was not possible to achieve remote code execution (xp_cmdshell was deactivated 😔) or write files to the server.
It is important to emphasize that this vulnerability can only be exploited by authenticated users. Authorized users are known contractual partners of the social authority who had to be explicitly created as users by the social authority.
Broken Access Control (CVE-2024-45877)
The TOPqw Webportal v1.35.283.2 is vulnerable to Broken Access Control in the User Management function in /Apps/TOPqw/BenutzerManagement.aspx. This allows a low privileged user to access all modules in the web portal, view and manipulate information and permissions of other users, lock other users or unlock the own account, change the password of other users, create new users or delete existing users and view, manipulate and delete reference data.
The navigation bar displays only those functions for which a user is authorized. However, all functions can be used by identifying the URL, as there are no server-side authorization checks. This means that any authenticated user can use
/Apps/TOPqw/BenutzerManagement.aspxto view, edit, delete and create users./Apps/TOPqw/qwStammdaten.aspxto change social service data, for example to exploit CVE-2024-45878./Apps/TOPqw/QWKalkulation/QWKalkulation.aspxto manipulate application information and files, such as replacing files with malicious files, or to exploit CVE-2024-45879.
Similar to CVE-2024-45875, this can only be exploited by authenticated users.
Stored Cross-Site Scripting (XSS) in “QWKalkulation” (CVE-2024-45879)
The file upload function in the QWKalkulation tool of TOPqw Webportal v1.35.287.1 in /Apps/TOPqw/QWKalkulation/QWKalkulation.aspx, is vulnerable to stored Cross-Site Scripting (XSS).
The file names of uploaded files were not validated properly and were inserted in an onclick event handler. This made it possible to add any JavaScript to the event handler. The XSS payload we used for this specific case is the following:
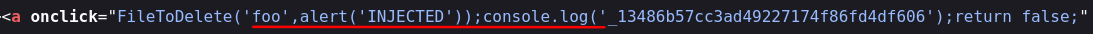
foo',alert('INJECTED'));console.log('
This payload is embedded in the HTML document in the following way as shown in Figure 07:
The foo' terminates the string early, effectively ending the first part of the JavaScript statement in the FiletoDelete function and starting its own. After that follows alert('INJECTED'), which simply triggers an alert dialog box displaying the text INJECTED. The rest of the payload );console.log(' preserves the syntax of the original FiletoDelete function.
This created an alert box for illustration purposes as can be seen in Figure 08:
However, the event handler is only executed if the file containing the XSS payload in its name is deleted. Therefore, it requires some social engineering for a successful exploit. Due to this reason, the risk level was downgraded from High to Medium.
Stored Cross-Site Scripting (XSS) in “Stammdaten” (CVE-2024-45878)
The Stammdaten function of baltic-it TOPqw Webportal v1.35.283.2, in /Apps/TOPqw/qwStammdaten.aspx, is vulnerable to stored Cross-Site Scripting (XSS).
As a countermeasure against XSS, the use of < followed by anything other than a space is prohibited in any modifyable data in the Stammdaten function. In addition, user input is HTML encoded and not included in HTML tags or other potentially vulnerable locations, with one exception. Authenticated users who are authorized to edit data (OR exploit CVE-2024-45877 😉) can specify a URL to a service provider’s website. This URL is inserted into the href attribute of an anchor tag. It is not possible to break out of this attribute because special characters, including quotation marks, are encoded in HTML. However, it has not been considered that JavaScript can be used as a protocol.
Figure 07 shows a simple proof of concept using the payload javascript:alert(document.domain). Unfortunately, as it was not possible to break out of the href attribute, the payload is only executed when a user clicks on the anchor tag. In our experience, the Javascript protocol trick actually works quite often, as it is little known to developers, and although modern web frameworks are good at ensuring that user input is always rendered in HTML-encoded form, this does not prevent the Javascript protocol from being used for XSS payloads.
bit baltic information technologies GmbH were cooperating actively with G DATA ADAN and baltic reacted quickly when notified of the vulnerabilities and fixed them immediately.
All of the described vulnerabilities have been fixed in version 1.35.291, released on July 25, 2024, and updated in the production systems of all customers.
Timeline
| 2024-01-08 | Start of first penetration test |
| 2024-01-09 | Reported unauthenticated SQL Injection |
| 2024-01-12 | Confirmed that unauthenticated SQL Injection is fixed |
| 2024-01-12 | End of first penetration test |
| 2024-01-15 | Sent the detailed report of the first penetration test |
| 2024-04-03 | Start of second penetration test (retests and test of functions that were broken during first penetration test) |
| 2024-04-05 | Reported authenticated SQL Injection |
| 2024-04-05 | End of second penetration test |
| 2024-04-09 | Sent the detailed report of the second penetration test |
| 2024-04-25 | Issued first CVE request to MITRE (rejected) |
| 2024-06-21 | Issued second CVE request to MITRE (rejected) |
| 2024-07-22 | Issued CVE request to other CNA (rejected) |
| 2024-07-25 | bit baltic information technologies GmbH remediated all vulnerabilities in version 1.35.291 |
| 2024-10-01 | Issued third CVE request to MITRE (accepted) |