On October 23, we hosted a webinar “How to Improve Threat Investigations with TI Lookup”. The session was led by Dmitry Marinov, CTO at ANY.RUN, who showed the audience effective methods for collecting the latest threat intelligence.
Here is a quick rundown of the main topics and examples of investigations covered during the event.
What is Threat Intelligence Lookup
Threat Intelligence (TI) Lookup is a centralized service for threat data exploration, collection, and analysis. It contains fresh threat data extracted from public malware and phishing samples uploaded to ANY.RUN’s Interactive Sandbox over the past 180 days. Each search request you make returns results that provide expanded context related to the threat data in your query.
Key features of TI Lookup include:
- Search results take just 5 seconds for events spanning the last six months. You can quickly get in-depth information about how events work, whether they are linked to a threat, and how they are related to that threat.
- With over 40 search parameters, TI Lookup provides examples and context from other investigations to help with decision-making. Unlike other solutions where you can work only with IOCs, Lookup can search among events and YARA rules, which is extremely helpful.
- TI Lookup has a large amount of data from the ANY.RUN sandbox, where cybersecurity analysts from around the world analyze threats. New samples are uploaded and analyzed daily, providing data that you cannot find in any other open sources.
How TI Lookup Sources Data
A core component of the suite is the Public submissions database. It is a vast repository that houses millions of unique malware and phishing samples submitted daily by a global community of over 500,000 security professionals from different spheres and industries using ANY.RUN.
Every time a user runs a public analysis in the sandbox, the systems capture the key data from that analysis. This data is then immediately sent to Threat Intelligence Lookup. As a result, Threat Intelligence Lookup becomes a centralized hub where you can search through threat data extracted from millions of malware and phishing analysis sessions launched in the ANY.RUN sandbox.
How TI Lookup Works
Let’s say we want to collect the latest domains used by threat actors that utilize Lumma, a notorious malware infostealer.
To do this, we can submit the following search request:
- The first part of the query, threatName:”lumma”, instructs the search engine to find sandbox sessions where Lumma was detected.
- The second part of the query, domainName:””, tells the system to retrieve all domain names identified in those sandbox sessions. The empty field essentially acts as a wildcard, indicating that you are interested in all domain names associated with the threat.
The service returns numerous domains that match our request. At the top, you can see domains with the malconf tag, which tells you that these domains were extracted directly from the configs of Lumma samples, the most reliable source of indicators of compromise. We can easily copy each indicator or download all of them in JSON format.
As you can see, apart from domains, the service also provides a large number of other types of indicators, including events, files, URLs, and others. That’s one of TI Lookup’s unique advantages – the diversity of data it provides.
Use Cases of TI Lookup
To demonstrate how TI Lookup can be used in real-world investigations, Dmitry outlined several use cases where the service can be particularly useful.
Checking a Suspicious IP Address
One of the most straightforward use cases is identifying threats using a suspicious IP address. For example, if you receive an alert about a connection to a suspicious IP address (e.g., 162[.]254[.]34[.]31) coming from one of the machines on your network, TI Lookup can quickly check if this IP address has been used in other malware attacks.
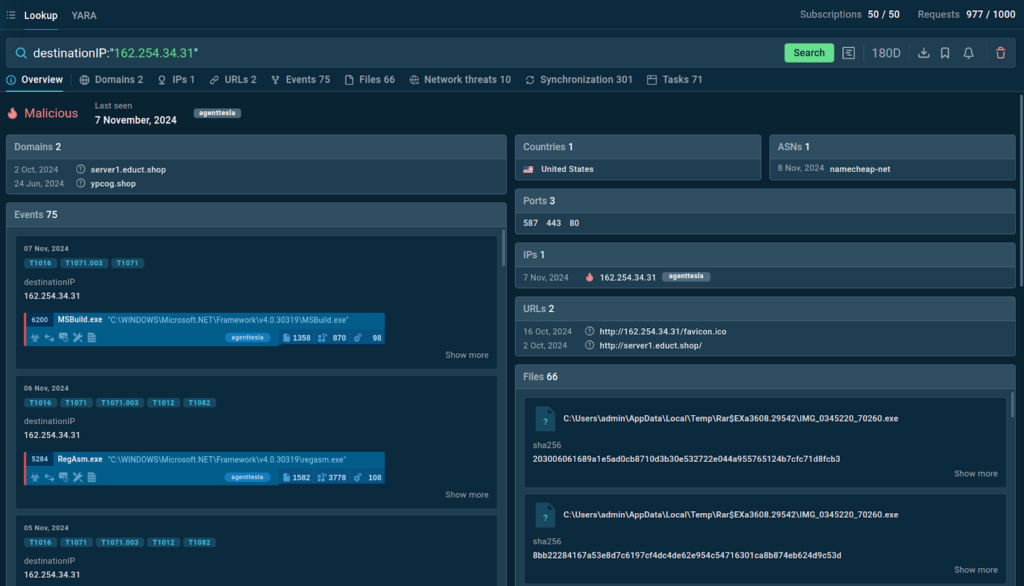
By entering the query destinationIP:”162.254.34.31″, the service identifies the IP address as malicious and links it to AgentTesla.
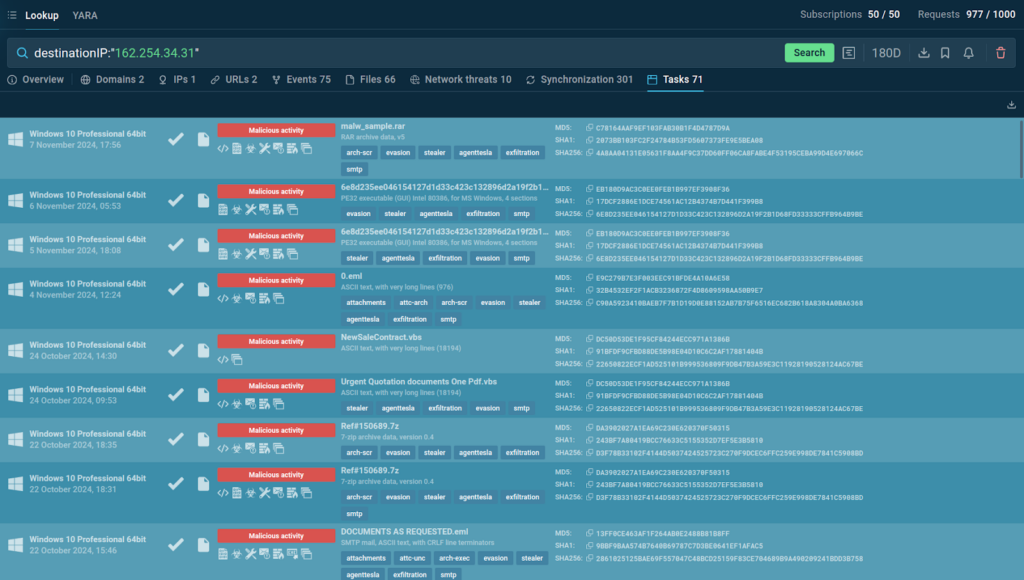
It also provides related indicators, including processes, files, and most importantly, sandbox sessions where you can see the analysis of actual attacks and collect more data.
Identifying a Malware Family Using a Mutex
Another way to use TI Lookup is to identify a threat by using unique indicators such as mutexes. For instance, you can use mutexes to identify the Remcos malware.
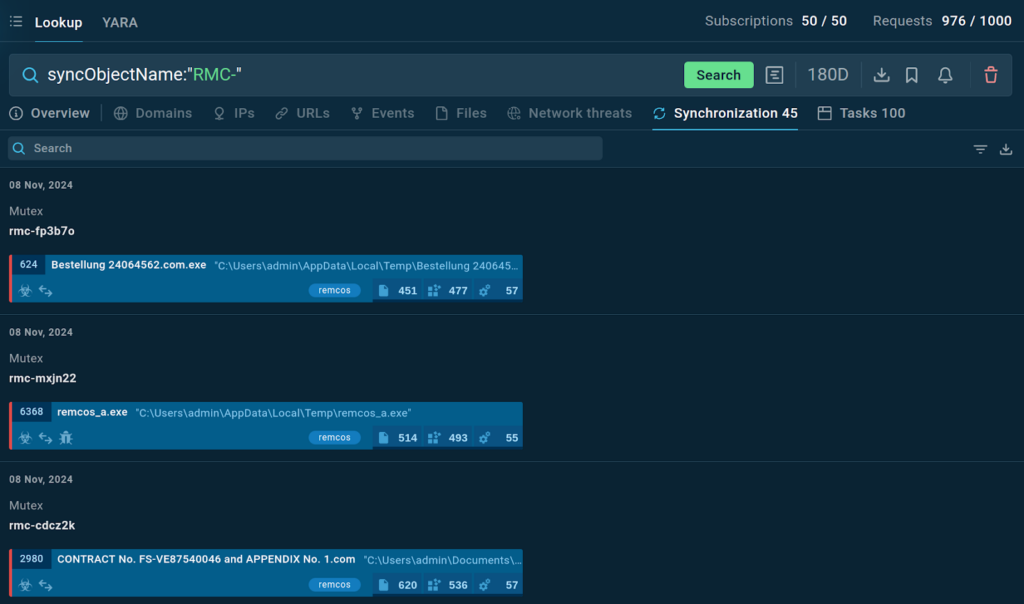
By entering the query syncObjectName:”RMC-“, the service shows specific mutexes and provides a list of sandbox sessions to explore the threat further.

Learn to Track Emerging Cyber Threats
Check out expert guide to collecting intelligence on emerging threats with TI Lookup
Read full guide
Uncovering a Threat Using a File Path
You can also find threats using a file path.
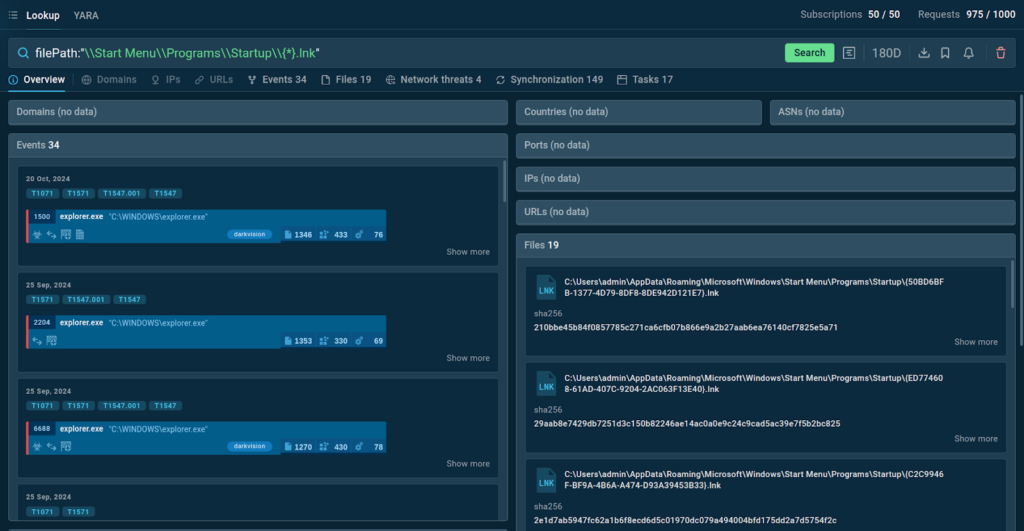
For example, a search for filePath:”\\Start Menu\\Programs\\Startup\\{*}.lnk” reveals that this file path has been observed in sessions featuring the DarkVision RAT.
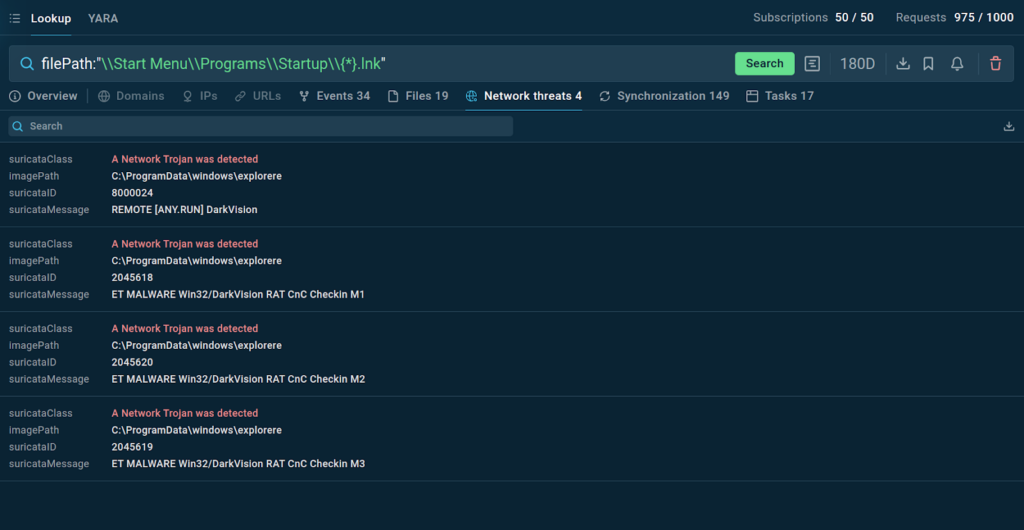
This allows you to see the context and related sandbox sessions for further investigation.
Connecting Unrelated Data Points
One of the most powerful features of TI Lookup is its ability to connect pieces of data that may seem unrelated. Consider a scenario where you have a command line artifact and a network artifact.
The command line artifact might be commandLine:”timeout \/t 5 & del”, which indicates a command that delays execution for 5 seconds and then deletes a file. The network artifact might be destinationIP:”185.215.113.37″, which represents an IP address that the system is communicating with.
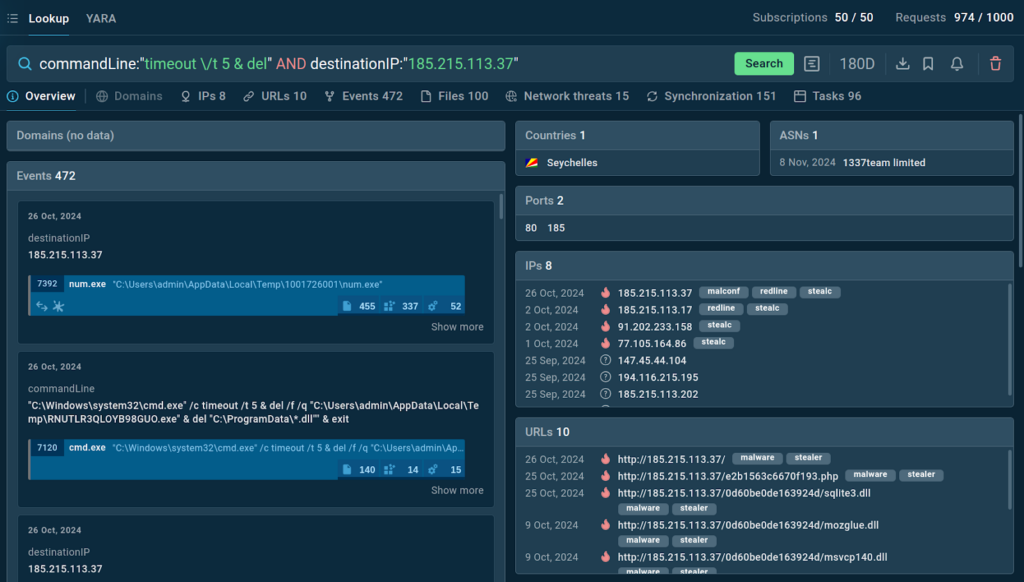
By combining these indicators into a single query, commandLine:”timeout \/t 5 & del” AND destinationIP:”185.215.113.37″, you can zoom in on the threat you’re dealing with.
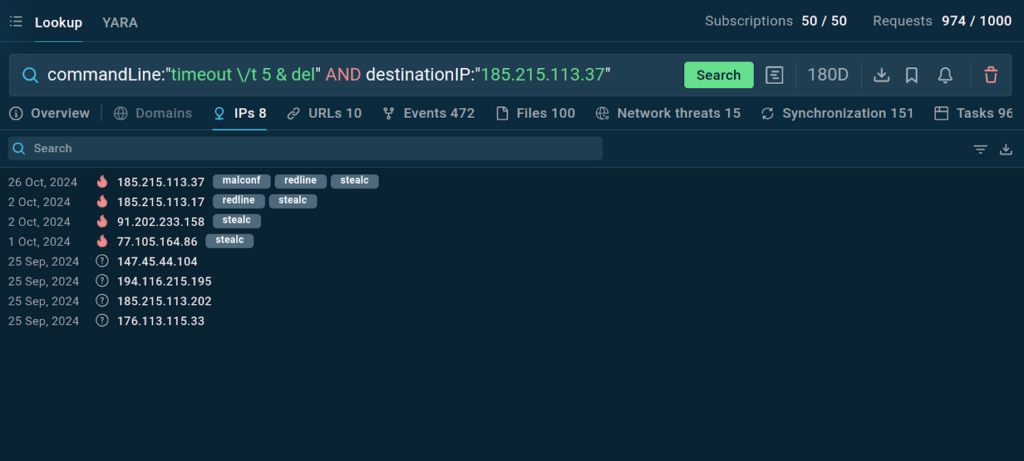
The service provides plenty of context and shows that the malware in question is StealC. Some of the additional indicators provided include malicious IPs and URLs, which were used in StealC attacks.
You can always go back to the source by navigating to a sandbox session of your interest to observe the threat’s behavior, and even rerun the analysis using your own VM settings.
Collecting Fresh Samples with YARA Rules
Another handy feature of TI Lookup is YARA Search. Thanks to the built-in editor, you can create, edit, store, and use YARA rules to find samples that match them.
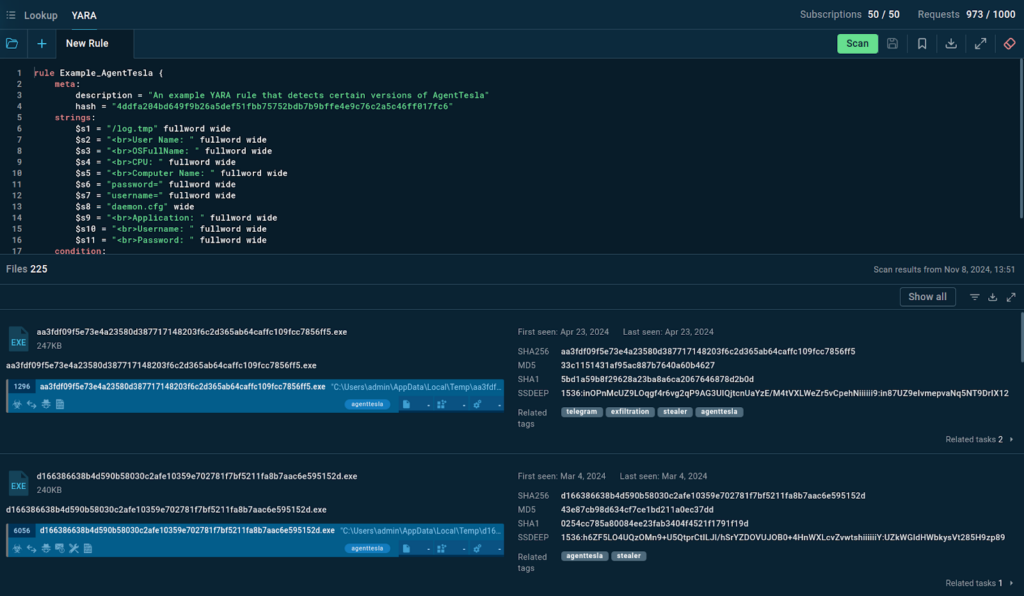
For example, using a YARA rule for AgentTesla, which is available by default in TI Lookup, the search returns numerous files that can be filtered by date. You can explore each result in detail by clicking on them and navigating to the sandbox session where it was detected.
You can also download a JSON file containing file hashes along with links to corresponding sandbox sessions.
Conclusion
The webinar gave a detailed look at TI Lookup, showing how it can help improve threat investigations. The tool’s ability to provide fast results, offer a wide range of search options, and give access to real samples and the latest data makes it very useful for cybersecurity professionals.
Stay tuned for more webinars from ANY.RUN by following us on social media like X, Facebook, and Discord. Subscribe to ANY.RUN’s YouTube channel for the upcoming release of a video recording of the webinar.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
