2024-11-13 03:9:10 Author: lab.wallarm.com(查看原文) 阅读量:5 收藏
There’s no doubt that API security is a hot topic these days. The continued growth in API-related breaches and increase in publicized API vulnerabilities has pushed API security to the top of CISO’s lists. The tools in the market for API security still have room for improvement, of course. One of the challenges security practitioners face with APIs is understanding the context in which an attack took place. In order to help, Wallarm has released API Sessions, a powerful new feature designed to help security teams detect and respond to threats more efficiently.
In this post, we’ll explore how the new API Sessions feature provides deeper insights into API usage patterns, potential security risks, and improves your ability to monitor, investigate, and respond to suspicious activity in real-time.
Why Sessions Matter in an API-Driven World
While a single API may be stateless, there are few, if any, API-based applications that operate on a single request/response pair as a complete interaction. API-based applications build business logic into their workflows. And even though some attacks can be detected in a single request, they still occur in the context of a larger session. As APIs support more sophisticated business logic, so do attackers. An attack will often span multiple endpoints and blend malicious behavior with legitimate user traffic, making it difficult for security tools and teams to pinpoint threats. A tool that only evaluates each API request individually simply doesn’t have the context to identify sophisticated attacks, and can’t provide users with the context for relatively simple attacks.
With the launch of API Sessions, Wallarm addresses these critical gaps by giving security teams a powerful tool to:
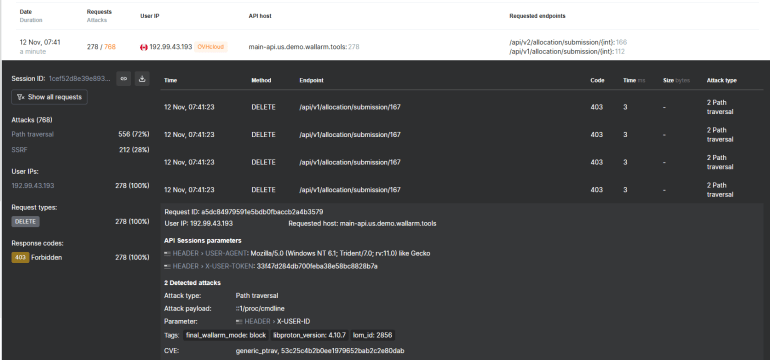
- Aggregate, correlate, and view API activity by user session.
- Identify patterns of malicious behavior that would otherwise go unnoticed.
- Respond faster to threats by providing the full context of user actions.

Key Features of Wallarm’s API Sessions
1. Session-Based Visibility for Enhanced Monitoring
Rather than tracking individual API requests in isolation, API Sessions groups activity by user-configurable sessions, allowing security teams to see the entire sequence of interactions—from legitimate actions to attacks. This comprehensive view helps security teams:
- Identify anomalies that span multiple endpoints and mutiple IP’s
- Discover hidden attack patterns and gain better visibility into API abuse.
2. Support for Legacy and Modern API Architectures
Whether your applications use traditional cookie-based WebApps or modern JWT/OAuth sessions, Wallarm’s API Sessions feature is fully compatible, giving you the flexibility to monitor both older and newer systems. This means your team can unify security monitoring across your entire API architecture without missing any critical insights.
3. Configurable Tracking of Business Flow Parameters
One of the most powerful aspects of API Sessions is its ability to track custom business flow parameters, such as usernames, transaction volumes, and order amounts, in either plaintext or hashed form. This helps organizations comply with OWASP API-6 recommendations for secure API design, while giving security teams more granular control over what data to monitor.
For example, you can now:
- Detect unusual spikes in transaction volumes during a user session.
- Monitor high-value orders that could indicate fraudulent activity.
- Investigate discrepancies in username usage across different sessions.
4. Correlation of Malicious and Non-Malicious Actions
API Sessions enables security teams to correlate malicious behaviors with normal user activity, reducing the number of false positives and improving the accuracy of threat detection. This not only saves time during investigations but also ensures that security resources are focused on real threats.
The Benefits of API Sessions: Why It’s a Game-Changer
1. Faster Incident Response One of the most significant benefits of API Sessions is the acceleration of incident response times. By allowing security teams to filter and investigate session data by critical criteria—such as IP addresses, specific endpoints, or user behavior—API Sessions ensures that potential threats are identified and dealt with quickly, often within minutes instead of hours or days.
2. Visibility into Shadow and Zombie APIs As enterprises scale their API infrastructures, undocumented Shadow APIs and outdated Zombie APIs can create serious security risks. Wallarm has discovered these “rogue APIs” for a long time, but API Sessions now allows users to monitor requests to these APIs, providing valuable context about their use.
3. Improved Collaboration and Investigation Security incidents are rarely solved in isolation. API Sessions simplifies the sharing of critical insights with your team, making it easier to collaborate on investigations and resolve threats faster. The detailed session-based view offers all stakeholders the clarity needed to take informed actions quickly.
Real-World Use Case: How API Sessions Can Help Your Business
Let’s look at a practical example. Imagine you run an e-commerce platform, and you notice an unusual spike in orders from a particular region. API Sessions allows your team to track all interactions related to those orders, including the sequence of API calls, the IP addresses used, and the volume of transactions. With this level of insight, your security team can determine whether this spike is due to legitimate behavior or something more suspicious, such as API abuse or fraudulent activity.
Without API Sessions, piecing together this information would require time-consuming cross-referencing of logs from multiple systems. With Wallarm’s new feature, you can investigate in real-time, ensuring a faster response to potential threats.
Start Leveraging API Sessions Today
In an environment where APIs are constantly under attack, having the right tools to detect, monitor, and respond to threats is critical. Wallarm’s API Sessions gives your security team the visibility and context they need to stay one step ahead of attackers, prevent API abuse, and ensure compliance with the latest security standards.
Start leveraging API Sessions today and see how Wallarm can help you transform your security strategy. For more information about API Sessions and how it can benefit your business, request a demo!
如有侵权请联系:admin#unsafe.sh