
2024-11-13 05:7:3 Author: www.vmray.com(查看原文) 阅读量:11 收藏
While threats against cybersecurity increase in complexity, it calls for proactive intelligence to stay ahead rather than mere defensive capabilities. Threat intelligence feeds provide security teams with live insight into finding, understanding, and mitigating potential threats before they affect the system. The following post will give the details about what the Threat Intelligence Feeds are, their types, and how they can be integrated into an already existing cybersecurity strategy; the feature below looks at how VMRay adds value with advanced technology.
What Is a Threat Intelligence Feed?
A threat intelligence feed is a stream of aggregated data from contributions on cyber threats that allow an organization to monitor and, when possible, predict an attack. These feeds take in indicators of compromise, IoCs, suspicious IP addresses, known malware signatures, and behavior insights into actionable intelligence deliverables that can be immediately integrated into security operations.
Unlike simple threat feeds, which just give information, threat intelligence feeds add to raw data such critical context that security teams can zero in on the relevant and urgent threats. For example, VMRay’s Threat Intelligence solution extends beyond traditional feeds through additional context layers used to enhance the accuracy and usability of threat insights.
Types of Threat Intelligence Feeds
- Open-source feeds are usually free, which includes data coming out of open security communities, malware analysis platforms, and government sources. Most open-source feeds lack much in depth and reliability, so their best use is part of a greater intelligence strategy.
- Commercial Feeds are brought and gather data on threats from proprietary sources. They assure high accuracy, timeliness, and context. The VMRay intelligence feed represents such a category. It provides contextually enriched insight through its advanced malware analysis and detection technology that makes for comprehensive coverage.
- Community-Based Feeds rely on collective intelligence shared among security professionals who know and trust each other. When these threats are very niche or sector-specific, added context may be required for these feeds to become useful operationally.
- Government & NGO Feeds Agencies like the FBI and DHS provide feeds like InfraGard and AIS, respectively, which are targeted toward critical infrastructure protection. Though very useful, they usually have limited scopes; therefore, in a wider strategy, their role will be supplementary.
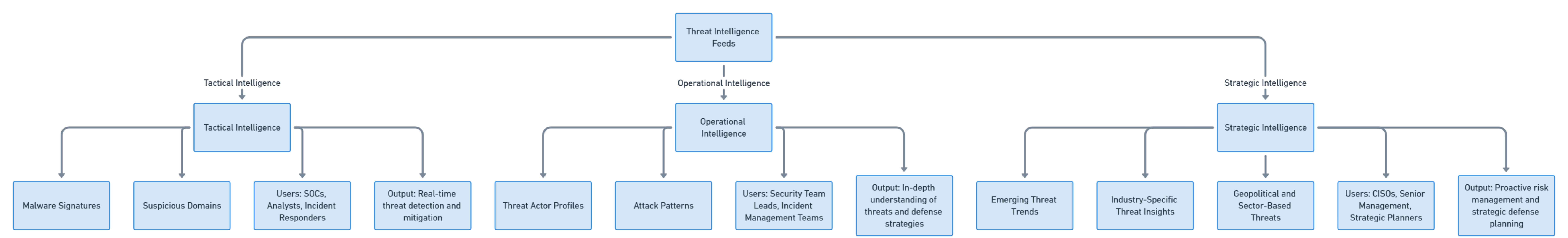
How Do Threat Intelligence Feeds Work?
Setting up and using threat intelligence feeds follows an organized method of data gathering and analysis:
- Define Data Requirements: Security teams define explicit threats and intelligence types that are relevant to their organization.
- Automate Data Collection: Feeds pull data from various sources, including open-source platforms and specialized tools like VMRay’s malware analysis solution
- Convert and Analyze Data: The data gets normalized and analyzed for patterns; threat intelligence reports are created to drive both strategic and tactical responses.
- Disseminate Insights: The findings are shared in several formats with teams and decision-makers-be it at the executive level for strategic decisions, or at the level of security managers who will make operational and tactical decisions.
- Feedback Loop: Threat feeds are constantly updated and validated to ensure relevance and accuracy.
What sets the VMRay feed apart is that these steps are automated with minimum human intervention. Its various deep analysis capabilities, like malware detection through sandboxing, transform raw data into actionable intelligence with high fidelity and fast decision-making.
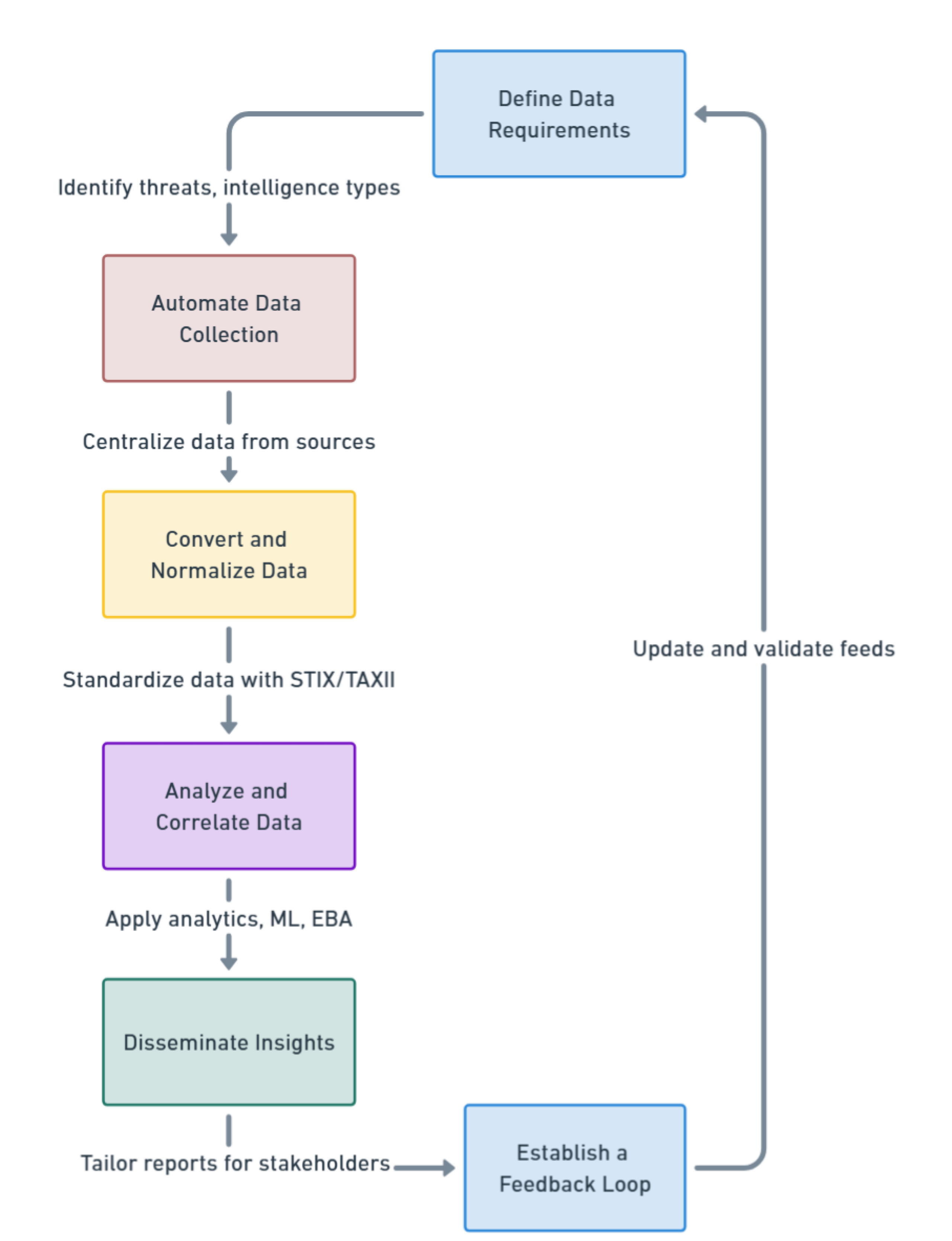
Key Components of Effective Threat Intelligence Feeds
Threat intelligence feeds should be more than a supply of data; it should empower security teams with insights into effective detection, prioritization, and response. The following is a rundown of the must-have components that make threat intelligence actionable, including ways to maximize their impact in daily operations:
Real-Time Updates:
Cyber threats emerge at an incredible speed; tactics and malware are found almost daily. Real-time updating ensures that your team has access to the latest information to enable timely mitigation against threats. Real-time feeds keep you updated with new IoCs and threat patterns for quicker identification and addressing of emerging risks.
Pro Tip: Set up automated alerting through your SIEM or TIP to immediately mark high-priority threats the moment they are picked up from real-time feeds. This automation offers quicker response times and a more proactive stance toward ever-changing threat tactics.
Accuracy & Relevance:
A good feed focuses on high-fidelity data to minimize false positives. Noise reduction is so important to avoid alert fatigue, which enables analysts to focus on real threats. An accurate feed will be one that has verified intelligence, so a cut through the irrelevant data enables teams to confidently act and make data-driven decisions.
Pro Tip: Continuously tune your feed filters to reflect your organization’s threat profile. Is ransomware a major risk for your industry? Update alert filtering to focus on IoCs and behaviors which will relate to ransomware. And again, with some periodicity, revisit the thresholding to ensure the only threats elevated to your team are pertinent.
Contextual Analysis:
Adding context to raw threat data turns it into actionable intelligence: how and why a threat might impact your organization. It will often contain contextual information on who the possible target might be, what the possible attack vectors are, and what IoCs apply-so analysts will be prepared for priority and planning accordingly.
Pro Tip: Create incident-specific playbooks for the common threat scenarios that you have contextualized in your feed. Playbooks will have specific response actions for threats such as phishing, ransomware, or malware. What this means is that if such threats happen again, teams will be able to take immediate consistent action with much more speed.
STIX/TAXII Standards:
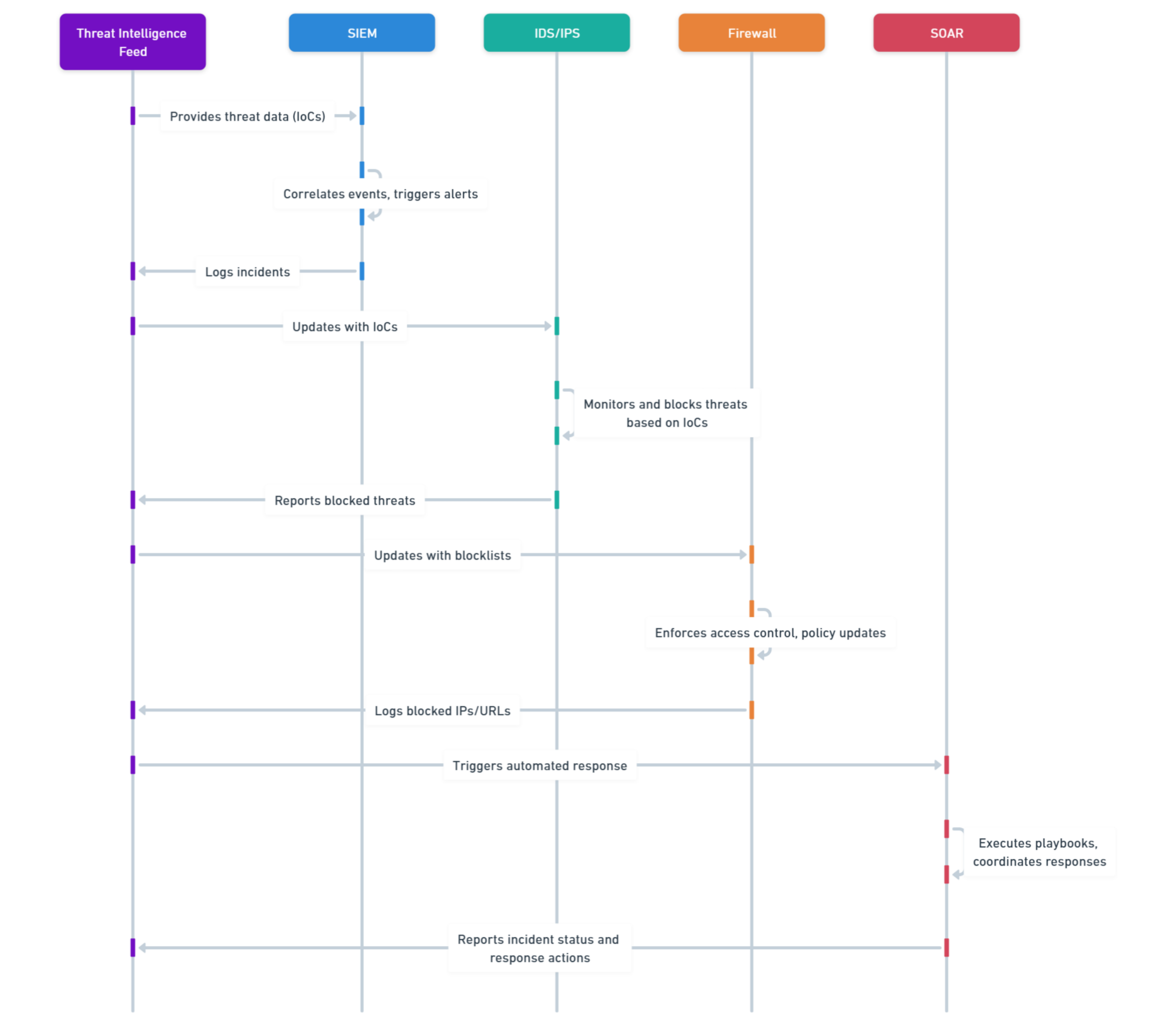
Threat intelligence should be in standards for easy integration among various security tools. In STIX, languages describing threat data are consistent, while TAXII allows for the secure transfer of this information. Such standards support seamless sharing of intelligence across SIEMs, IDS, firewalls, and other tools inside your security ecosystem.
Pro Tip: Utilize a TIP or SIEM platform that natively supports STIX/TAXII for the automation of threat intelligence ingestion, and distributes it across your security stack. This not only amplifies team coordination but also cuts down on a significant amount of manual re-formatting, thereby helping to deliver a far more comprehensive security posture.
Diverse Sources:
The most effective feed would be able to incorporate intelligence from various sources, such as proprietary research, open-source data, and user telemetry, into one feed in order to provide a complete view of the threat landscape. Multiple data points give teams a broad view that ranges from known to emerging threats.
Pro Tip: Schedule periodic reviews of the quality and relevance of your feed sources against the needs of your organization. For further reinforcement, add to general feeds with sources that are more specialized on certain risks or regions relevant to your organization’s operation.
This will enable Threat Intelligence Feed to concentrate on those components and maximize the value of your feeds: driving more detections, with higher accuracy, reduced alert fatigue, and informing incident response wherever possible. The integration of this whitepaper into your threat intelligence workflows can strengthen your organization’s overall defensive posture against today’s sophisticated cyber adversaries.
Benefits of Threat Intelligence Feeds
If applied correctly, threat intelligence feeds provide actionable insights for the threat analysts in proactive defense and smooth security operations. Following are some of the key benefits that the well-curated feeds offer to the threat intelligence teams:
Enhanced Proactive Defense:
Real-time data coming from reliable threat intelligence feeds enables the team to identify and project threats before they can strike. Analysts can identify all potential IOCs with updated information about threats and ready defenses against beginning-stage attacks.
Best Practice: Combine malware sandboxing with real-time Threat Feeds for dynamic analysis. Sandboxes confirm and profile unknown threats, which provides added assurance proactive defenses are based on confirmed intelligence and not untested data.
Better Resource Utilization:
Sourced intelligence empowers a team to understand how best to implement a struggle against the most threatening affairs, making sure the time and resources are channeled into where they are much needed. Other than spending a lot of time sifting through volumes of data with their irrelevant pieces, the analysts will spend more time paying attention to high-risk alerts that call for immediate attention.
Best Practice: Set up your threat feeds to filter and apply prioritization options so that your team only sees high-priority alerts. This reduces noise from the information overload and conserves resources for focusing on genuinely impactful threats.
Amplified Threat Detection:
Automation of feeds and integrations to detection tools limits manual handling of data, hence giving the security teams the capability for speed and accuracy. The automated feeds can pick up in anomalies and flag those as possible threats without much human intervention.
Best Practice: Integrate threat feeds with automated analysis tools such as sandboxes and SIEMs to simplify the process of threat detection and accelerate the process of alerting. Automation frees the analysts to investigate and mitigate validated threats.
Faster Response Times:
Enabled with refreshed and contextual intelligence, shrinking incident response times help security teams take urgent, timely actions to mitigate potential breaches. Timely intelligence means analysts know the nature and urgency of the threat in no time; hence, they can triage cases efficiently for quicker resolution or remediation.
Best Practice: Ensure your team is fully knowledgeable in using threat intelligence feeds with playbooks for swift action. By knowing exactly how to interpret feed data and initiate response activities, your team reduces latency and prevents threats before they affect critical assets.
By embedding these advantages in operations, the work a threat intelligence analyst undertakes will be resoundingly more effective, efficient, and impactful in enabling the organization to stay resilient against changing cyber threats.
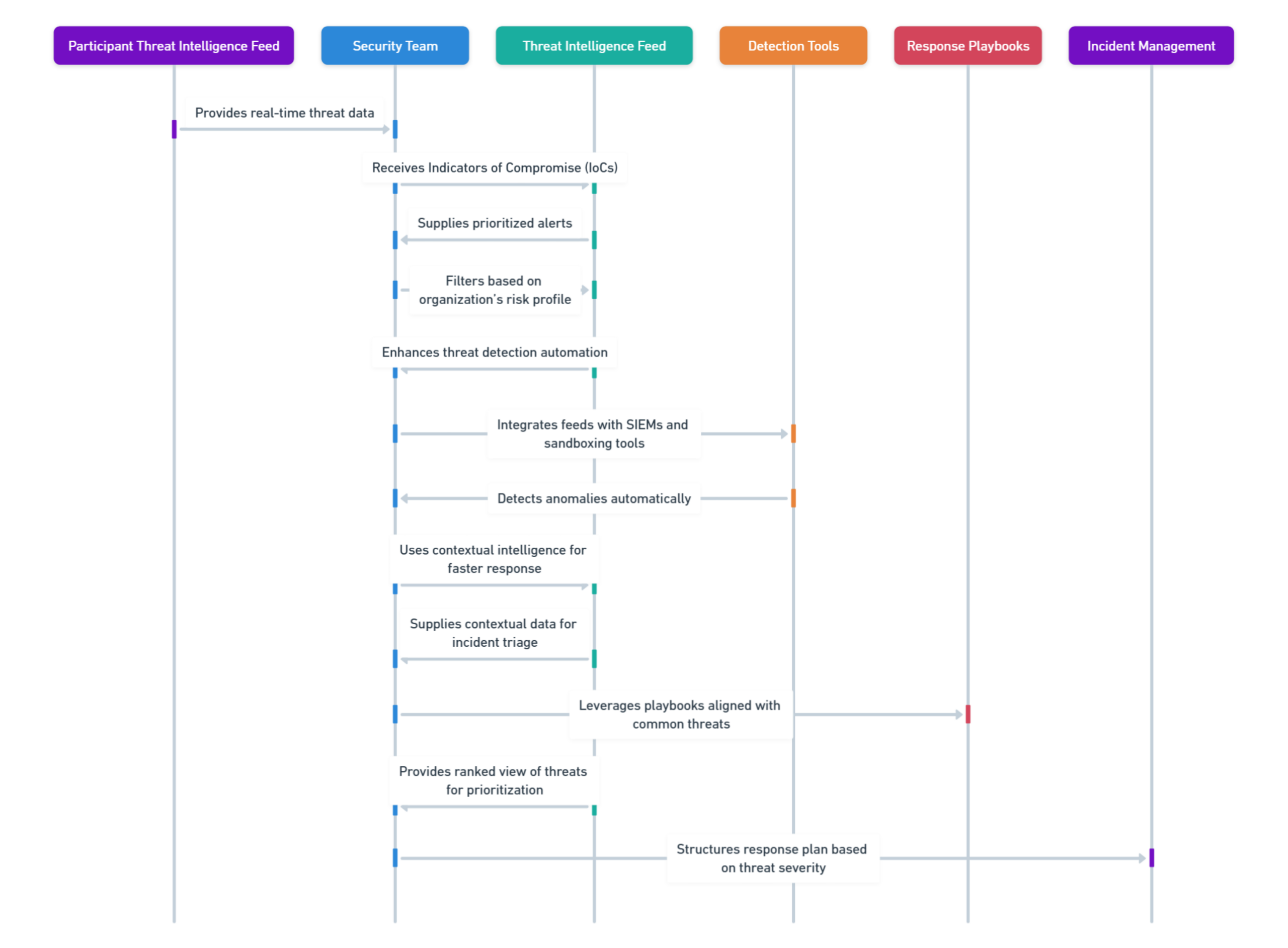
Integrating Threat Intelligence Feeds with Security Tools:
For maximum effectiveness, intelligence feeds should seamlessly integrate with existing tools:
Integration with SIEMs, IDS and Firewalls: VMRay’s threat intelligence integrates with a wide swath of security systems for the extension of capabilities in detection.
Automation of Routine Tasks: Feeds will automatically act on their own based on the detection of a threat, thus improving efficiency and reducing time-to-response.
Ongoing Training of Teams: Teams need to be trained to interpret and make use of intelligence information so that insights will prove well and actionable in the SOC.
Best Practices for Using Threat Intelligence Feeds
Threat intelligence feeds are the lifeblood that helps organizations stay ahead of the threats. It is, in most cases, very difficult to manage feeds and apply their full value. Following are some common challenges coupled with the best practices for Threat Intelligence Analysts that help them make the most out of their feeds.
Data Overload Management:
The volume of information from the different feeds could overwhelm teams and cause alert fatigue. Focus resources on high-priority threats that are relevant to your organization’s risk profile.
Best Practice: Feeds are filtered and prioritized according to the organization’s risk level and threat profiles. Because the criteria for a critical alert will have already been defined, the group is not sifting through tonnes of low-priority information but can instead narrow the focus onto highly relevant and consequential threats.
Minimize False Positives:
Poor feeds, or feeds with unverified data in them, can lead to wastes of time and lowering of response efficiency by flagging lots of false positives. The high-fidelity feeds help the teams spend their resources on genuine threats instead of chasing non-relevant alerts.
Best Practice: Give preference to threat feeds that offer consistent and verified data. In situations where automated analysis can be possible, the use of sandbox technology for sample validation reduces the chances of false positives as the flagged alert will definitely show malicious behavior.
Stay Relevant and Current:
Threat intelligence that is not current about the existing landscape is reasonably ineffective. Data that is outdated or irrelevant has the potential to mislead analysts and slow down response times.
Best Practice: Periodically review the feeding sources to ensure they are current about emerging threat tactics, techniques, and strategies. Look to sources that refresh their data frequently and assess the relevance of new feeds for rapid adaptation to shifting threat landscapes.
Contextualizing Actionable Intelligence:
That is, the raw data alone does not avail enough context with which informed decisions can be made. Intelligence feeds are far more useful when they contain indicators such as TTPs, motivations of threat actors, and known target sectors.
Best Practice: Feed data should support enriched data in context on threat insights for the “who, why, and how” of threats. Where feasible, integrate feeds that can contextualize threat data, as well as provide feeds that outline typical behavior from similar threats, to drive a more holistic view toward identifying and informing strategies for defense.
Threat Intelligence Integration Across the Security Stack:
For the complete utilization of threat intelligence, it needs to seamlessly integrate into the different security tools that an organization may have, such as SIEMs, EDRs, and firewalls. The feeds have to be in a format that can enable seamless threat detection, correlation, and response across those tools.
Best Practice: Make sure your threat feeds support widely adopted standards like STIX and TAXII to allow for seamless integration. That way, the data will be shared and acted on easily within your security ecosystem for better operational efficiency, making it easier on the team in terms of collaboration regarding threat intelligence and incident response.
By focusing on these best practices, analysts can better enhance the effectiveness of threat intelligence feeds to provide relevant, timely, and actionable insights that improve overall security operations.
Conclusion: Why Choose VMRay for Threat Intelligence
Threat intelligence feeds are instrumental in proactive cybersecurity teams, turning this raw data into actionable insights that make proactive defense real. With its leading threat detection and real-time intelligence, VMRay’s intelligence feed is cut out for today’s complex threat landscape. From high-fidelity IoCs to frictionless integrations, VMRay empowers your security teams to outpace threats while offering unmatched accuracy that optimizes their defense strategies.
如有侵权请联系:admin#unsafe.sh