2024-11-13 22:15:43 Author: cyble.com(查看原文) 阅读量:20 收藏
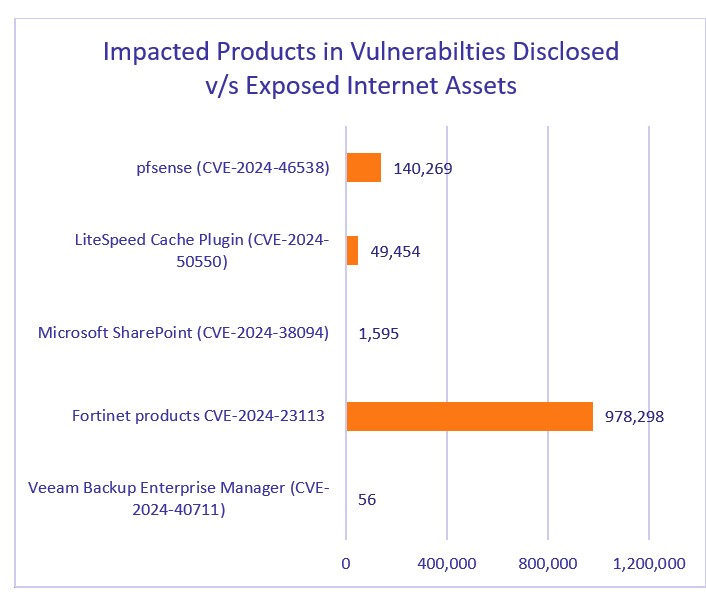
Cyble Research and Intelligence Labs (CRIL) researchers investigated 18 vulnerabilities and 10 dark web exploits in the last week – including an actively exploited Fortinet vulnerability with nearly 1 million exposed assets on the internet.
Other vulnerabilities analyzed by Cyble affect third-party Windows drivers, SharePoint, Qualcomm, Android, QNAP and more.
Here are the vulnerabilities highlighted by Cyble as meriting high-priority attention by security teams.
CVE-2024-23113: FortiOS Format String Vulnerability
CVE-2024-23113 is a critical format string vulnerability affecting Fortinet’s FortiOS, specifically within the FGFM (FortiGate to FortiManager) service. The vulnerability could allow unauthenticated remote code execution (RCE) by malicious actors.
While the vulnerability dates from February, CISA added it to its Known Exploited Vulnerabilities (KEV) catalog last month, and Cyble researchers have seen multiple exploits and proofs of concept (PoC) targeting the vulnerability discussed on the dark web and in cybercrime forums.
Cyble’s ODIN vulnerability search tool has detected 978,000 vulnerable Fortinet instances:

CVE-2024-50550: LiteSpeed Cache plugin for WordPress
Another vulnerability with wide exposure is CVE-2024-50550, a critical privilege escalation vulnerability in LiteSpeed Cache plugin for WordPress, which is installed on over 6 million websites. Cyble honeypot sensors recently detected attacks on a different LiteSpeed vulnerability (CVE-2024-44000) and another WordPress plugin.
Cyble researchers said the new LiteSpeed vulnerability “could be leveraged to access backend databases as well to install arbitrary plugins or sniffers, leading attackers to exfiltrate payment card data and sensitive information of users,” as well as altering web pages.
CVE-2021-41285 and CVE-2020-14979: Windows Drivers
CVE-2021-41285 and CVE-2020-14979 are high-severity vulnerabilities in drivers that could allow attackers to achieve local privilege escalation to NT AUTHORITY\SYSTEM in Windows Systems. A newly identified malware called “SteelFox” has been observed mining for cryptocurrency and stealing credit card data by using the “bring your own vulnerable driver” (BYOVD) technique to create a service that runs WinRing0.sys inside vulnerable drivers, leading to privilege escalation.
CVE-2024-38094: Microsoft SharePoint
CVE-2024-38094 is a high-severity remote code execution vulnerability affecting Microsoft SharePoint. Microsoft recently disclosed that the vulnerability is being exploited to gain initial access to corporate networks by attackers. Researchers also observed that attackers are targeting vulnerable SharePoint servers using publicly disclosed SharePoint proof-of-concept exploit code to plant a web shell that they later leverage to gain privileges and pivot into the compromised network.
CVE-2024-43047 and CVE-2024-43093: Android Kernel Components
CVE-2024-43047 is a high-severity use-after-free issue in closed-source Qualcomm components within the Android kernel that can lead to elevated privileges. CVE-2024-43093 is also a high-severity elevation of privilege flaw, impacting the Android Framework component and Google Play system updates, specifically in the Documents UI. Recently Google fixed both of the actively exploited zero-day flaws as part of its November security updates.
CVE-2024-8956 and CVE-2024-8957: PTZ Cameras
CVE-2024-8956 and CVE-2024-8957 impact PTZ cameras, which are extensively used in organizations around the world for applications such as live streaming, security surveillance, and conference automation. The critical vulnerabilities can also be chained by attackers to execute arbitrary OS commands on these devices, as well as access sensitive data such as usernames, password hashes, and device configuration details.
CVE-2024-10443: Synology NAS Devices
CVE-2024-10443 is a critical vulnerability in Synology’s BeeStation and DiskStation NAS devices, specifically within the BeePhotos and SynologyPhotos applications, which are designed to provide user-friendly personal cloud storage solutions. The vulnerability can allow remote attackers to execute arbitrary code. As NAS devices are commonly used to store sensitive data by both home and enterprise customers, Cyble researchers have assessed that attackers could attempt to leverage the vulnerability to breach the systems and steal data.
CVE-2024-50387: QNAP
CVE-2024-50387: This as of yet unclassified vulnerability detailed in a QNAP advisory was revealed at Pwn2Own 2024. It is a critical SQL injection (SQLi) vulnerability impacting QNAP’s SMB Service, which is the vendor’s implementation of the Server Message Block (SMB) protocol within QNAP NAS devices, enabling file sharing and network services across Windows and other operating systems.
Dark Web and Cybercrime Forum Exploits
Here are 7 vulnerabilities and exploits that Cyble researchers observed under active discussion on underground forums and Telegram channels, plus claims of zero-day vulnerabilities for sale in Palo Alto Networks and Microsoft products.
CVE-2024-6778: A high-severity vulnerability affecting the Chromium web browser prior to version 126.0.6478.182. The vulnerability arises from a race condition in the DevTools component. An attacker can convince a user to install such an extension, allowing them to inject arbitrary scripts or HTML into privileged pages, thereby facilitating a sandbox escape.
CVE-2024-46538: A critical cross-site scripting (XSS) vulnerability identified in pfSense version 2.5.2. This vulnerability allows attackers to execute arbitrary web scripts or HTML by injecting a ‘crafted payload’ into the $pconfig variable, specifically through the ‘interfaces_groups_edit.php’ file.
CVE-2024-44193: A vulnerability affecting Apple iTunes for Windows, specifically versions prior to 12.13.3. The vulnerability allows local attackers to potentially elevate their privileges on affected systems, posing significant security risks.
CVE-2024-39205: A critical vulnerability affecting pyload-ng, versions 0.5.0b3.dev85 running under Python 3.11 or below. This vulnerability allows attackers to execute arbitrary code through crafted HTTP requests, which can lead to complete system compromise.
CVE-2024-40711: A critical vulnerability in Veeam Backup & Replication software classified as a deserialization of untrusted data issue. This vulnerability allows unauthenticated remote code execution (RCE), enabling attackers to execute arbitrary code on affected systems without requiring any authentication.
CVE-2024-0311: A cybersecurity vulnerability identified in the Skyhigh Client Proxy, this flaw allows a malicious insider to bypass existing security policies without needing a valid release code, which can potentially lead to unauthorized access to sensitive data or applications.
CVE-2024-20419: The critical vulnerability affecting Cisco’s Smart Software Manager On-Prem (SSM On-Prem) arises from improper validation in the password change functionality, allowing unauthenticated remote attackers to change user passwords without prior knowledge of the existing password.
Cyble researchers also observed zero-day vulnerabilities being offered for sale on dark web forums, including a remote code execution (RCE) vulnerability in Palo Alto’s PAN-OS, and a privilege escalation (LPE) vulnerability in Windows that a threat actor was asking US$200,000 to $400,000 for. Palo Alto issued an advisory stating that it is aware of the PAN-OS claim.
Cyble Recommendations
To protect against these vulnerabilities and exploits, organizations should implement the following best practices:
- To mitigate vulnerabilities and protect against exploits, regularly update all software and hardware systems with the latest patches from official vendors.
- Develop a comprehensive patch management strategy that includes inventory management, patch assessment, testing, deployment, and verification. Automate the process where possible to ensure consistency and efficiency.
- Divide your network into distinct segments to isolate critical assets from less secure areas. Use firewalls, VLANs, and access controls to limit access and reduce the attack surface exposed to potential threats.
- Create and maintain an incident response plan that outlines procedures for detecting, responding to, and recovering from security incidents. Regularly test and update the plan to ensure its effectiveness and alignment with current threats.
- Implement comprehensive monitoring and logging solutions to detect and analyze suspicious activities. Use SIEM (Security Information and Event Management) systems to aggregate and correlate logs for real-time threat detection and response.
- Subscribe to security advisories and alerts from official vendors, CERTs, and other authoritative sources. Regularly review and assess the impact of these alerts on your systems and take appropriate actions.
- Conduct regular vulnerability assessment and penetration testing (VAPT) exercises to identify and remediate vulnerabilities in your systems. Complement these exercises with periodic security audits to ensure compliance with security policies and standards.
Conclusion
These vulnerabilities highlight the urgent need for security teams to prioritize patching critical vulnerabilities in major products and those that could be weaponized as entry points for wider attacks. With increasing discussions of these exploits on dark web forums, organizations must stay vigilant and proactive. Implementing strong security practices is essential to protect sensitive data and maintain system integrity.
Related
如有侵权请联系:admin#unsafe.sh