2024-11-19 23:45:19 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏
The Ngioweb botnet, which supplies most of the 35,000 bots in the cybercriminal NSOCKS proxy service, is being disrupted as security companies block traffic to and from the two networks.
Following an investigation of more than one year, researchers identified the complete architecture and traffic of the Ngioweb botnet proxy server, which was first observed in 2017.
Ngioweb supplying 80% of NSOCKS proxies
Since late 2022, the proxy service at nsocks[.]net has been providing residential gateways for malicious activity under the NSOCKS name.
Multiple cybersecurity companies have reported that many of the proxies offered by NSOCKS were from the Ngioweb botnet but not all its command-and-control (C2) nodes were discovered.
In a report today, researchers at Lumen’s Black Lotus Labs tracked both active and historical C2 nodes and the architecture they form.
They note that NSOCKS[.] net “users route their traffic through over 180 “backconnect” C2 nodes that serve as entry/exit points” to hide their identity.
According to the report, the Ngioweb botnet provides at least 80% of the 35,000 proxies provided by NSOCKS, which are scattered across 180 countries.
![Bots provided by the cybercriminal nsocks[.]net proxy service](https://www.bleepstatic.com/images/news/u/1100723/NSOCKS_net_bots.png)
source: BleepingComputer
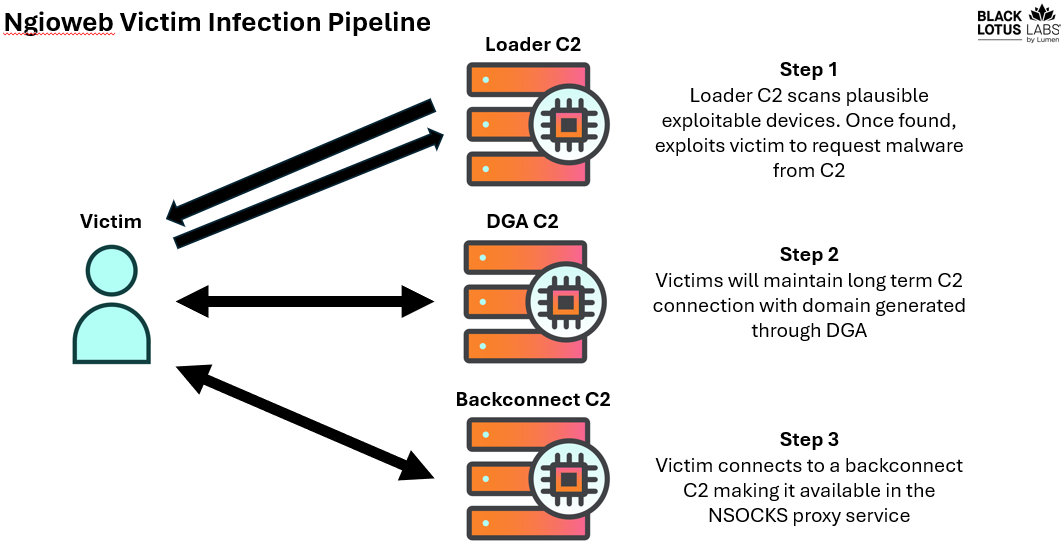
The botnet has a loader network that redirects infected devices to a C2 server to fetch and execute the ngioweb malware.
Although it is unclear how initial access occurs, Black Lotus Labs believes the threat actor relies on around 15 exploits for various n-day vulnerabilities.
In the second stage, the compromised device contacts C2 domains created using a domain generation algorithm (DGA), and determine if the bot is usable for the proxy network.
These management C2s monitor and check the bot’s capacity for traffic and also connect them to a “backconnect” server that makes them available for the NSOCKS proxy service.

source: Lumen
According to the researchers, recent samples of the ngioweb malware suffered few modifications compared to older variants analyzed in 2019, one difference being the switch from hardcoded C2 URLs to the DGA-created domains.
Black Lotus Labs told BleepingComputer that another variance is the use of DNS TXT records to prevent sinkholing or losing control of the DGA domains.
Ngioweb targets devices with vulnerable or discontinued web application libraries and includes products from Zyxel, Reolink, and Alpha Technologies.
Recently, the researchers observed an increase in Netgear routers being added to the Ngioweb botnet to a degree that 10% of the bots show the certificate for this particular brand.
It is worth noting that 45% of the bots in Ngioweb are sold to NSOCKS through the Shopsocks5 network.
While Ngioweb is built on an intricate architecture that allows filtering the devices based on the capabilities they offer, Black Lotus Labs says that the actor behind the botnet failed to properly secure their infected devices.
As the researchers discovered, Ngioweb devices were also abused by nation-state hackers (APT28/Fancy Bear/Pawn Storm/Forest Blizzard), who could conveniently mix espionage-related traffic with cybercriminal activities.
Open proxies used for DDoS attacks
The NSOCKS[.]net proxy network also has inadequate security that allows exploitation my multiple actors, even those that don’t pay for the service.
It should be noted that there is another proxy service with the same name at NSOCKS[.]com, which did not make the object of this investigation.
Black Lotus Labs explains that the IP address and port number that NSOCKS proxy buyer gets have no authentication mechanism and could be used by other actors finding them.
“According to public reporting, most of these IPs appear on free proxy lists. These lists are routinely abused by threat actors, and the proxies therein are often used in various malware samples, such as Agent Tesla, to proxy traffic” - Lumen’s Black Lotus Labs
These open proxies have been used to amplify distributed denial-of-service (DDoS) attacks by various threat actors [1, 2].
Additionally, the network is currently used to support various types of malicious activity ranging from hiding malware traffic to credential stuffing and phishing.
At the moment, both the Ngioweb and the NSOCKS[.net] service are being severely disrupted as Lumen has identified the botnet’s architecture and traffic. Along with industry partners such as The ShadowServer Foundation, the company is blocking traffic to and from the known C2 nodes associated with the two networks.
Lumen provides a list of indicators of compromise that could help other companies identify malicious bots and further disrupts the two operations.
如有侵权请联系:admin#unsafe.sh