2024-11-22 23:45:43 Author: therecord.media(查看原文) 阅读量:1 收藏
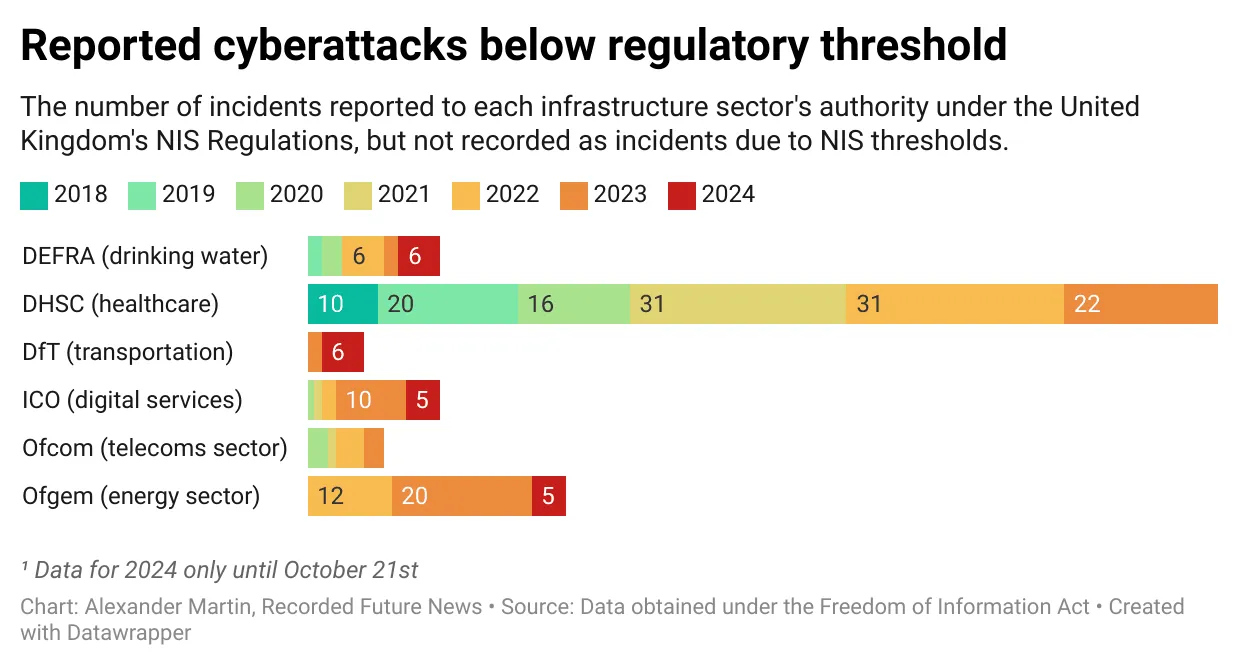
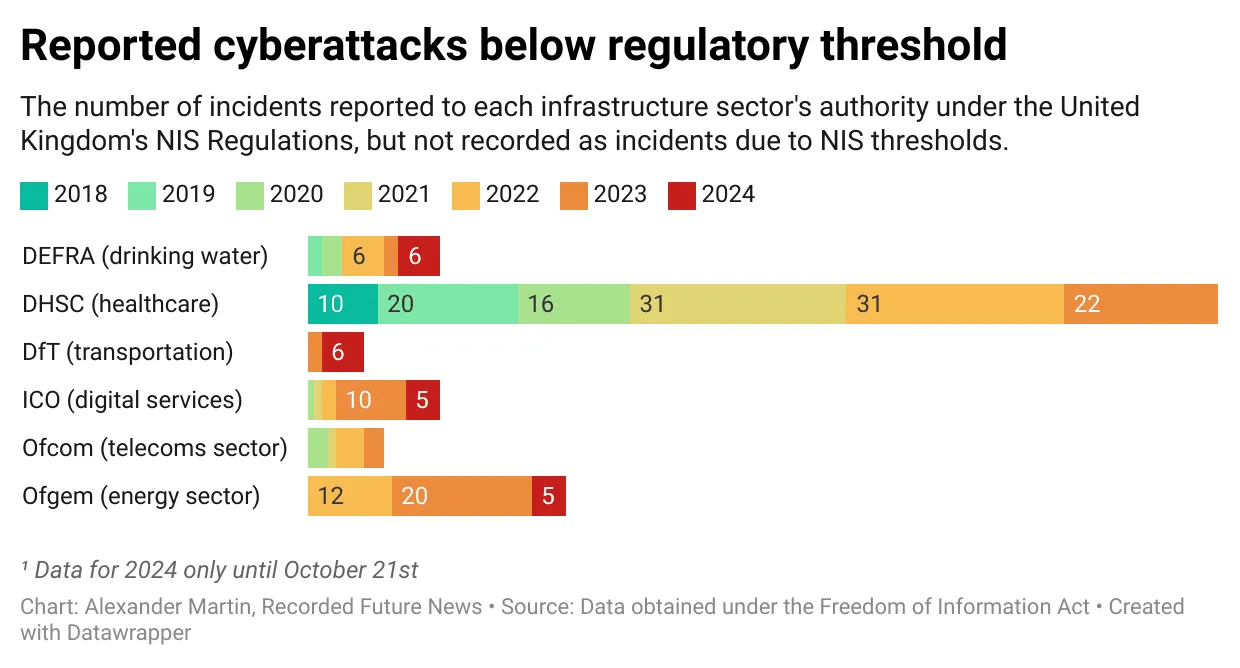
A record number of cyber incidents impacted Britain’s critical drinking water supplies this year without being publicly disclosed, according to information obtained by Recorded Future News. The exact nature of these incidents is unclear, and they may include operational failures as well as attacks. Under British cybersecurity laws — known as the NIS Regulations — critical infrastructure companies are required to report “significant incidents” to the government within three days or face a fine of up to £17 million ($21 million). Across all regulated critical national infrastructure sectors, more NIS incidents have been reported this year than ever before, with the transport and drinking water sectors the most impacted. In 2024, there were at least six incidents affecting drinking water infrastructure, according to data collected by Recorded Future News using the Freedom of Information (FOI) Act. In previous years there were no more than two. The record number of incidents follows the head of the National Cyber Security Centre (NCSC), Richard Horne, stating in October his agency had “already responded to 50% more nationally significant incidents compared to last year.” Under the NIS Regulations, cyber incidents affecting drinking water supply are reported to the Department for Environment Food & Rural Affairs (Defra). The department initially declined to respond to an FOI request about these reports, claiming the information “if disclosed, could [make the services] more vulnerable to both physical and cyberattacks by persons or organizations with nefarious intent.” Defra withdrew this argument after Recorded Future News appealed and argued the department could not demonstrate how statistical data might make services more vulnerable. The six incidents were reported to Defra between January 1 and October 21. According to the NIS Regulations, these reports related to a cyberattack or operational failure that “directly impacts on the production and delivery of wholesome water, irrespective of whether or not customers are directly affected.” While the substance of these incidents remains confidential, they come as the top cybersecurity agency in the United States — which faces many of the adversaries in cyberspace as the United Kingdom — has recently repeatedly highlighted cyberattacks against the water sector and issued stark warnings about its need to improve its defenses. The British approach may be about to change. A consultation survey for the Cyber Security and Resilience Bill — which intends to update the 2018 cybersecurity laws after the previous government failed to do so — informs organizations working in critical infrastructure that new disclosure obligations are on the table. “We are considering introducing a transparency requirement which will ensure customers are notified of incidents which significantly compromise the integrity of a digital service upon which they rely,” the survey states of the law, which is expected to be introduced to Parliament next year. The move would, for instance, help the public establish whether the incidents being reported under the NIS Regulations are cyberattacks or operational technology issues. Ciaran Martin, the former head of the NCSC, told Recorded Future News there was a need to weigh the value of public disclosures against the risks involved when potentially revealing additional details that could assist an adversary. “In general, transparency around major cyber incidents is helpful, but there will be times when secrecy is operationally crucial. The forthcoming legislation is an opportunity to try and get this difficult balance right,” said Martin. “Critical infrastructure providers have an obligation to secure the services they provide and the personal data we entrust to them,” said David Ferbrache, the managing director of Beyond Blue and former head of cyber at the Ministry of Defence. “Transparency around how they deal with cyber risks and incidents is key to maintaining our confidence in those providers. We expect and have that in other areas such as service levels and safety incidents, perhaps we should expect the same of cyber security incidents too,” said Febrache. The Cyber Security and Resilience Bill is also expected to increase the number of incidents being reported. As previously covered by Recorded Future News, a large number of cyberattacks are not recorded as NIS incidents due to the current thresholds set by the legislation. These thresholds are based on the impact of a cybersecurity incident on the provision of the essential service — for instance, whether an attack disrupted energy production at a power plant or prevented a train company from running a number of services. As the thresholds do not measure the depth of the attackers’ computer network access, nor whether the threat actors had the capability to disrupt any essential services, they risk leaving government authorities without any effective visibility into how targeted their sectors are. “We are proposing to change the definition of a reportable incident to ensure that a wider range of incidents are captured, including incidents capable of resulting in a significant impact to service continuity and incidents that compromise the integrity of a network and information system,” the government survey informs industry, adding that it may reduce the reporting period from three days to 24 hours. 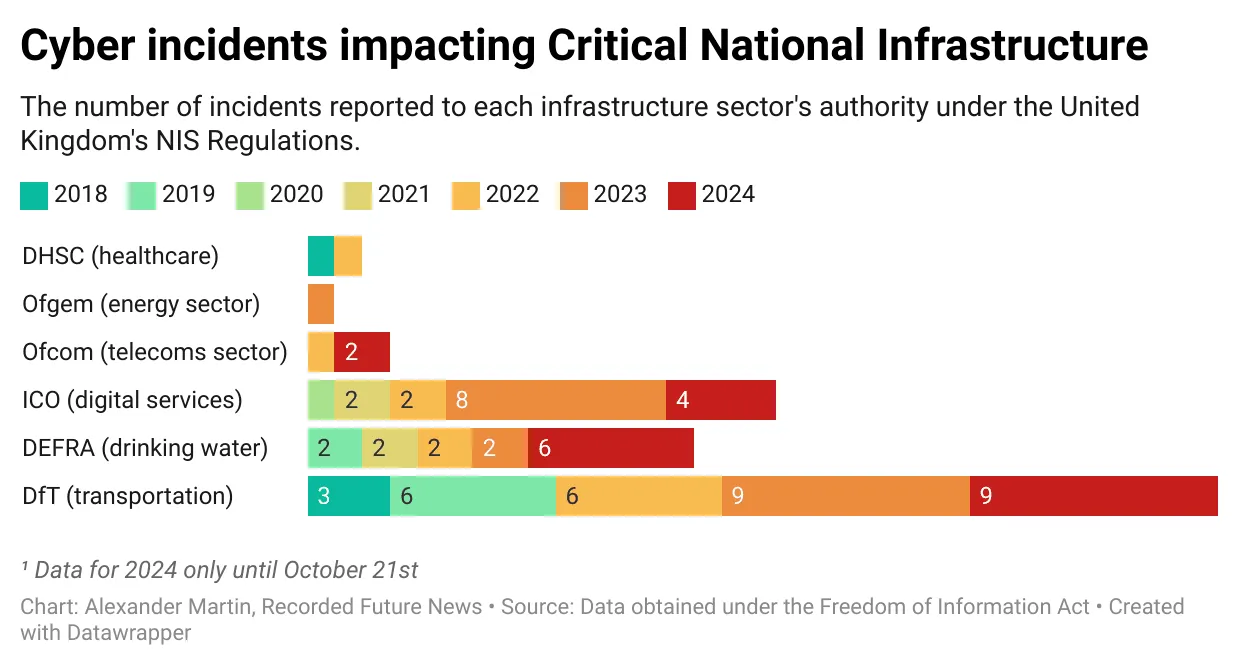
Get more insights with the
Recorded Future
Intelligence Cloud.
No previous article
No new articles
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and is also a fellow at the European Cyber Conflict Research Initiative.
如有侵权请联系:admin#unsafe.sh
