One of the options available in Privileges 2.x is the capability of running an action once admin rights have been granted or removed.

This action can be launching an app or running a script and is set by the Run after privilege change setting.

This action can be further customized by choosing to only run the action once admin rights have been granted. This can be set by the Run only if administrator privileges have been granted setting.

Something to be aware of is that when using an action is that the script or application in question will be run within the context of the logged-in user. This means it will have the same level of access rights that the logged-in user currently has (standard versus admin.) This may be important if running the script or launching the application includes functionality which works for a user with admin rights but not for a user with standard rights. An example of this is running the following command using the log command line tool:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
If the logged-in user has admin rights, the log command shown above runs without issues and without requesting authentication.

If the logged-in user has standard rights, you get an error that the log command operation is not permitted.

Privileges 2.x includes management options for setting post-actions, so that their operation and configuration can be set using configuration profiles. For more details, please see below the jump.
The relevant preference domain and key values are listed below:
- Preference domain: corp.sap.privileges
- Key: PostChangeExecutablePath
- Value: String containing the absolute filesystem path to an application or script
- Preference domain: corp.sap.privileges
- Key: PostChangeActionOnGrantOnly
- Value: Boolean
Here’s how the settings would appear in the following example:
- The App Store app is launched as a post action.
- The action is run once admin rights have been granted or removed.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <?xml version="1.0" encoding="UTF-8"?> | |
| <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> | |
| <plist version="1.0"> | |
| <dict> | |
| <key>PostChangeActionOnGrantOnly</key> | |
| <false/> | |
| <key>PostChangeExecutablePath</key> | |
| <string>/System/Applications/App Store.app</string> | |
| </dict> | |
| </plist> |
Here’s how the settings would appear in the following example:
- A script named privileges_teams_report.sh located in the /usr/local/bin directory is launched as a post action.
- The action is run only when admin rights have been granted.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <?xml version="1.0" encoding="UTF-8"?> | |
| <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> | |
| <plist version="1.0"> | |
| <dict> | |
| <key>PostChangeActionOnGrantOnly</key> | |
| <true/> | |
| <key>PostChangeExecutablePath</key> | |
| <string>/usr/local/bin/privileges_teams_report.sh</string> | |
| </dict> | |
| </plist> |
One use case for a post action script would be sending a report to a Slack or Teams channel via webhook. While Privileges natively supports sending JSON output to a web hook, both Slack and Teams need to have the JSON being sent to it formatted in specific ways, or else the receiving end won’t be able to work with it. They’re also different formats, so sending to Slack using JSON formatted for Teams doesn’t work and vice-versa.
I’ve written a couple of example scripts which can be used with Privileges as a post action, which are designed to be run as follows:
- The reporting script is launched as a post action.
- The action is run only when admin rights have been granted.
Note: The reason why the reporting script should be run only when admin rights have been granted is that the log command line tool is used in the scripts. As discussed previously, these scripts will run in the context of the logged-in user and if the logged-in user has admin rights, the log command runs without issues and without requesting authentication. If the logged-in user has standard rights though, the log command will error.
privileges_slack_report.sh
When configured with a Slack webhook URL, the following script should send a report similar to the one below to the relevant Slack channel.

This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/bin/bash | |
| # This script will send a report to a Slack channel with information about the user who has been granted admin rights. | |
| # You'll need to set up a Slack webhook to receive the information being sent by the script. | |
| # If you need help with configuring a Slack webhook, please see the links below: | |
| # | |
| # https://api.slack.com/incoming-webhooks | |
| # https://get.slack.help/hc/en-us/articles/115005265063-Incoming-WebHooks-for-Slack | |
| # | |
| # Once a Slack webhook is available, the slack_webhook variable should look similar | |
| # to this: | |
| # slack_webhook="https://hooks.slack.com/services/XXXXXXXXX/YYYYYYYYY/ZZZZZZZZZZ" | |
| slack_webhook="" | |
| # That should be it for the necessary configuration part. | |
| # Nothing else should need to be edited below this line. | |
| name=$(hostname) | |
| logs=$(mktemp) | |
| logged_in_user=$(id -un) | |
| # Set script exit status | |
| exit_error=0 | |
| # Function for sending multi-line output to a Slack webhook. Original script from here: | |
| # | |
| # http://blog.getpostman.com/2015/12/23/stream-any-log-file-to-slack-using-curl/ | |
| SendToSlack(){ | |
| cat "$1" | while read LINE; do | |
| (echo "$LINE" | grep -e "$3") && curl -X POST –silent –data-urlencode "payload={\"text\": \"$(echo $LINE | sed "s/\"/'/g")\"}" "$2"; | |
| done | |
| } | |
| touch "$logs" | |
| echo "Administrator rights have been granted to $logged_in_user using Privileges.app on $name:" >> "$logs" | |
| /usr/bin/log show –style syslog –predicate 'process == "PrivilegesDaemon" && eventMessage BEGINSWITH "SAPCorp: U"' –last 1m | tail -1 >> "$logs" | |
| SendToSlack ${logs} ${slack_webhook} | |
| exit "$exit_error" |
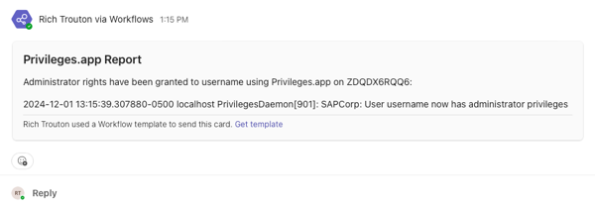
privileges_teams_report.sh
When configured with a Teams webhook URL, the following script should send a report similar to the one below to the relevant Teams channel.

This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| #!/bin/bash | |
| # This script will send a report to a Teams channel with information about the user who has been granted admin rights. | |
| # You'll need to set up a Teams webhook to receive the information being sent by the script. | |
| # If you need help with configuring a Teams webhook, please see the links below: | |
| # | |
| # https://learn.microsoft.com/en-us/microsoftteams/platform/webhooks-and-connectors/how-to/add-incoming-webhook | |
| # | |
| # | |
| # Once a Teams webhook is available, the teams_webhook variable should look similar | |
| # to this: | |
| # teams_webhook="https://companyname.webhook.office.com/webhookb2/7ce853bd-a9e1-462f-ae32-d3d35ed5295d@7c155bae-5207-4bb5-8b58-c43228bc1bb7/IncomingWebhook/8155d8581864479287b68b93f89556ae/651e63f8-2d96-42ab-bb51-65cb05fc62aa" | |
| teams_webhook="" | |
| # That should be it for the necessary configuration part. | |
| # Nothing else should need to be edited below this line. | |
| name=$(hostname) | |
| logs=$(mktemp) | |
| logged_in_user=$(id -un) | |
| # Set script exit status | |
| exit_error=0 | |
| # Function for sending multi-line output to a Teams webhook. We add an extra Return to | |
| # each line of the log file ($1) to prevent Teams from showing the log on a single line. | |
| # The Teams Card format requires JSON to be sent to the Teams webhook ($2). | |
| # You can add a title to the Card by specifying it as a third argument. | |
| SendToTeams(){ | |
| LOG_TEXT=$( cat "$1" | sed "s/\"/'/g" | sed "s/$/\r\r/g" ) | |
| TEAMS_JSON='{ | |
| "type": "message", | |
| "attachments": [{ | |
| "contentType": "application/vnd.microsoft.card.adaptive", | |
| "contentUrl": null, | |
| "content": { | |
| "$schema": "http://adaptivecards.io/schemas/adaptive-card.json", | |
| "type": "AdaptiveCard", | |
| "version": "1.4", | |
| "msteams": {"width": "Full"}, | |
| "body": [ | |
| {"type": "TextBlock", "text": "'$3'", "weight": "bolder", "size": "large", "wrap": true}, | |
| {"type": "TextBlock", "text": "'$LOG_TEXT'", "wrap": true}, | |
| ] | |
| } | |
| }]}' | |
| /usr/bin/curl -H "Content-Type: application/json" -d "${TEAMS_JSON}" "$2" | |
| } | |
| touch "$logs" | |
| echo "Administrator rights have been granted to $logged_in_user using Privileges.app on $name:" >> "$logs" | |
| /usr/bin/log show –style syslog –predicate 'process == "PrivilegesDaemon" && eventMessage BEGINSWITH "SAPCorp: U"' –last 1m | tail -1 >> "$logs" | |
| SendToTeams ${logs} ${teams_webhook} "Privileges.app Report" | |
| exit "$exit_error" |
Example configuration profiles containing the PostChangeExecutablePath and PostChangeActionOnGrantOnly settings are available below:
ConfigurePrivilegesPostActionAppStore.mobileconfig
Settings:
- The App Store app is launched as a post action.
- The action is run once admin rights have been granted or removed.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <?xml version="1.0" encoding="UTF-8"?> | |
| <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> | |
| <plist version="1"> | |
| <dict> | |
| <key>PayloadUUID</key> | |
| <string>2857BC2F-FC70-4F9E-B5AE-F1DC56ECC79B</string> | |
| <key>PayloadType</key> | |
| <string>Configuration</string> | |
| <key>PayloadOrganization</key> | |
| <string>Company Name</string> | |
| <key>PayloadIdentifier</key> | |
| <string>2857BC2F-FC70-4F9E-B5AE-F1DC56ECC79B</string> | |
| <key>PayloadDisplayName</key> | |
| <string>Configure Privileges Post Action App Store</string> | |
| <key>PayloadDescription</key> | |
| <string>Configure Privileges to launch the Mac App Store as a post action.</string> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadEnabled</key> | |
| <true/> | |
| <key>PayloadRemovalDisallowed</key> | |
| <true/> | |
| <key>PayloadScope</key> | |
| <string>System</string> | |
| <key>PayloadContent</key> | |
| <array> | |
| <dict> | |
| <key>PayloadDisplayName</key> | |
| <string>Custom Settings</string> | |
| <key>PayloadIdentifier</key> | |
| <string>C667AE87-34F2-4CC4-B87E-70242EFD6E50</string> | |
| <key>PayloadOrganization</key> | |
| <string>Company Name</string> | |
| <key>PayloadType</key> | |
| <string>com.apple.ManagedClient.preferences</string> | |
| <key>PayloadUUID</key> | |
| <string>C667AE87-34F2-4CC4-B87E-70242EFD6E50</string> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadContent</key> | |
| <dict> | |
| <key>corp.sap.privileges</key> | |
| <dict> | |
| <key>Forced</key> | |
| <array> | |
| <dict> | |
| <key>mcx_preference_settings</key> | |
| <dict> | |
| <key>PostChangeActionOnGrantOnly</key> | |
| <false/> | |
| <key>PostChangeExecutablePath</key> | |
| <string>/System/Applications/App Store.app</string> | |
| </dict> | |
| </dict> | |
| </array> | |
| </dict> | |
| </dict> | |
| </dict> | |
| </array> | |
| </dict> | |
| </plist> |
ConfigurePrivilegesPostActionReportScript.mobileconfig
- A script named reporting_script.sh located in the /path/to directory is launched as a post action.
- The action is run only when admin rights have been granted.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <?xml version="1.0" encoding="UTF-8"?> | |
| <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> | |
| <plist version="1"> | |
| <dict> | |
| <key>PayloadUUID</key> | |
| <string>3DD0FB5F-F238-455D-AF43-843BB4111126</string> | |
| <key>PayloadType</key> | |
| <string>Configuration</string> | |
| <key>PayloadOrganization</key> | |
| <string>Company Name</string> | |
| <key>PayloadIdentifier</key> | |
| <string>3DD0FB5F-F238-455D-AF43-843BB4111126</string> | |
| <key>PayloadDisplayName</key> | |
| <string>Configure Privileges Post Action Report Script</string> | |
| <key>PayloadDescription</key> | |
| <string>Configure Privileges to launch a reporting script as a post action only when admin rights are granted.</string> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadEnabled</key> | |
| <true/> | |
| <key>PayloadRemovalDisallowed</key> | |
| <true/> | |
| <key>PayloadScope</key> | |
| <string>System</string> | |
| <key>PayloadContent</key> | |
| <array> | |
| <dict> | |
| <key>PayloadDisplayName</key> | |
| <string>Custom Settings</string> | |
| <key>PayloadIdentifier</key> | |
| <string>B4D8564A-217C-42E3-AD69-23967AF22B84</string> | |
| <key>PayloadOrganization</key> | |
| <string>Company Name</string> | |
| <key>PayloadType</key> | |
| <string>com.apple.ManagedClient.preferences</string> | |
| <key>PayloadUUID</key> | |
| <string>B4D8564A-217C-42E3-AD69-23967AF22B84</string> | |
| <key>PayloadVersion</key> | |
| <integer>1</integer> | |
| <key>PayloadContent</key> | |
| <dict> | |
| <key>corp.sap.privileges</key> | |
| <dict> | |
| <key>Forced</key> | |
| <array> | |
| <dict> | |
| <key>mcx_preference_settings</key> | |
| <dict> | |
| <key>PostChangeActionOnGrantOnly</key> | |
| <true/> | |
| <key>PostChangeExecutablePath</key> | |
| <string>/path/to/reporting_script.sh</string> | |
| </dict> | |
| </dict> | |
| </array> | |
| </dict> | |
| </dict> | |
| </dict> | |
| </array> | |
| </dict> | |
| </plist> |
如有侵权请联系:admin#unsafe.sh