![]()
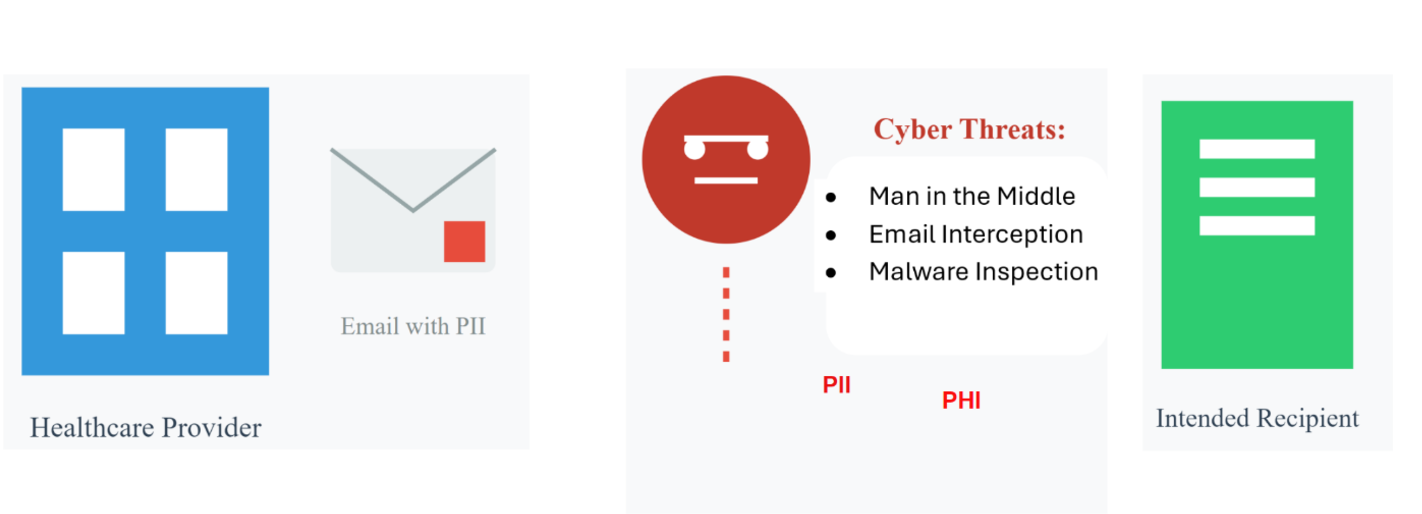
In an increasingly digital world, the healthcare sector has become a prime target for cybercriminals seeking to exploit vulnerabilities in email communications. One of the most alarming methods of attack involves intercepting email attachments during transit, resulting in the theft of personally identifiable information (PII) and other sensitive data. It poses significant risks, especially in the healthcare domain, where medical records and personal information are frequently shared via email. This article examines recent cases of such fraud and discusses potential solutions, including the utilization of libraries like PyMinizip, to enhance data security.
Recent Email Fraud Examples
NHS Wales Email Breach (2023)
In a cyberattack targeting the National Health Service (NHS) in Wales, hackers intercepted email attachments containing patient health records during transit between healthcare providers and external labs. Personal health records of thousands of patients were accessed, exposing sensitive information such as diagnostic results, personal details and insurance data. This data was later found for sale on the dark web. A combination of phishing and unencrypted email transmissions allowed hackers to access email attachments containing sensitive healthcare data.
Florida Orthopedic Institute Breach (2020)
Hackers launched an attack targeting emails sent between the Florida Orthopedic Institute and its patients. The attackers intercepted attachments containing health information and insurance details, compromising nearly 640,000 patients’ data. The breach exposed PII such as names, birthdates, insurance information and clinical data related to patient treatment plans. This led to lawsuits and regulatory scrutiny. The attackers exploited vulnerabilities in the email system and intercepted unencrypted email attachments.
Threat Mitigation: Technical Steps
Email attachments have become prime targets for cybercriminals due to the high value of personal data, which can be exploited for identity theft, insurance fraud and other illegal activities. As healthcare organizations move toward digital records and communication, their exposure to email interception and cyber threats grows, particularly if they lack comprehensive cybersecurity protocols. Many institutions still face challenges in fully meeting regulatory standards, such as those outlined in the Personal Data Protection Bill (PDP), leaving sensitive information at risk.
In response, this article outlines two layers of security that can be implemented using AWS services and Python libraries to prevent such fraud and secure email communications effectively.
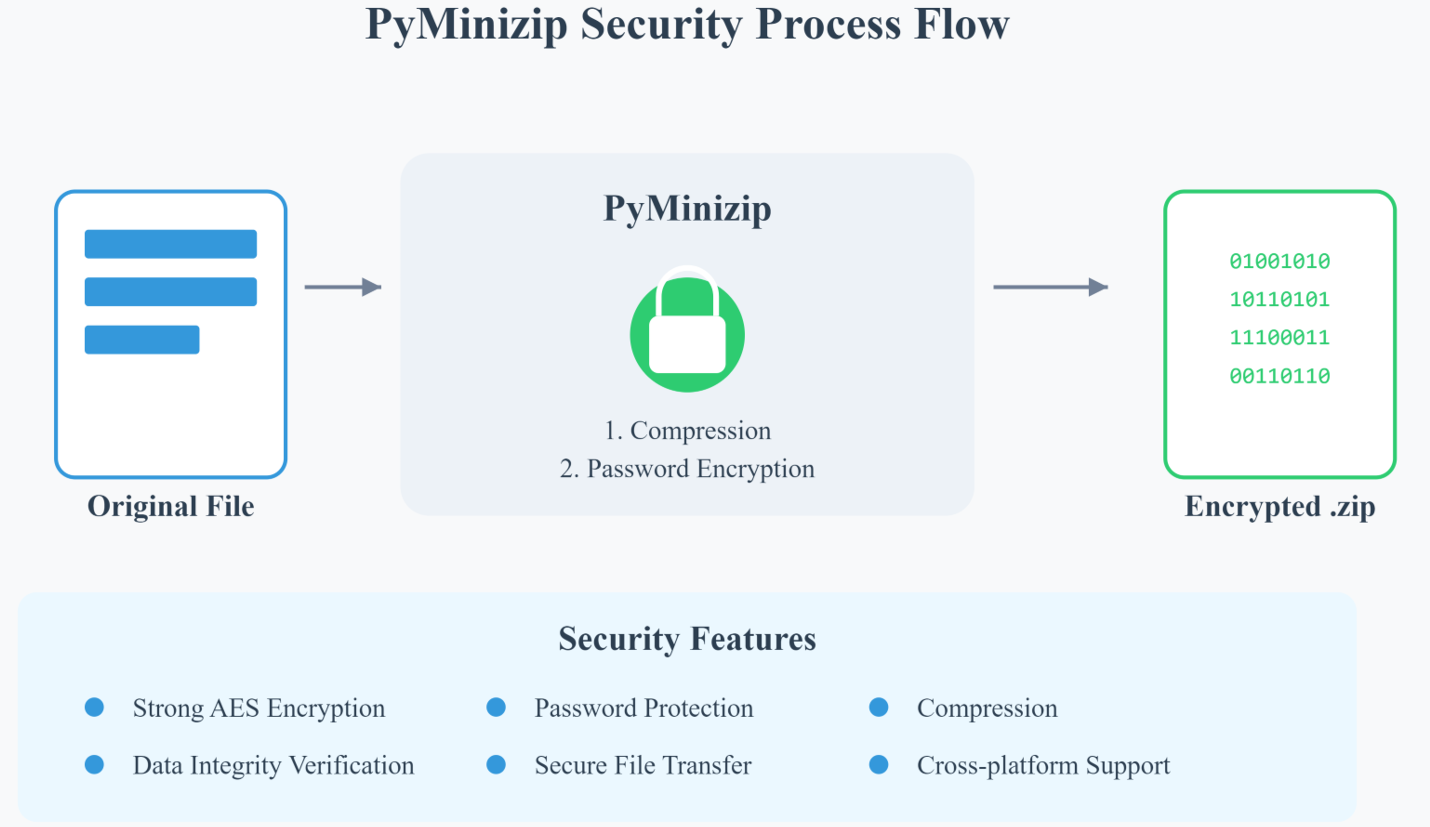
- Securing Attachments with Password Protection— Open-source Python libraries, such as pyminizip, allow for straightforward encryption of attachments with a password known only to the intended recipient. These passwords can be kept as the receiver’s personal information like their last four digits of SSN, cell number and username which only they are aware of and any such decided pattern can be included in the same email in plain English language hence no need to transmit. For example, please provide a password as your DateOfBirth_LastFourDigitsofSSN. This personalized approach simplifies the process for recipients, as they are already familiar with the password, reducing the need for additional support or password recovery requests. This approach provides two key benefits: first, only the authorized receiver has access to the password, ensuring confidentiality. Secondly, it eliminates the need to hardcode the password in the email, thereby avoiding the transmission of sensitive information within email communications. This method not only strengthens security but also enhances the user experience by seamlessly integrating privacy into communication workflows.
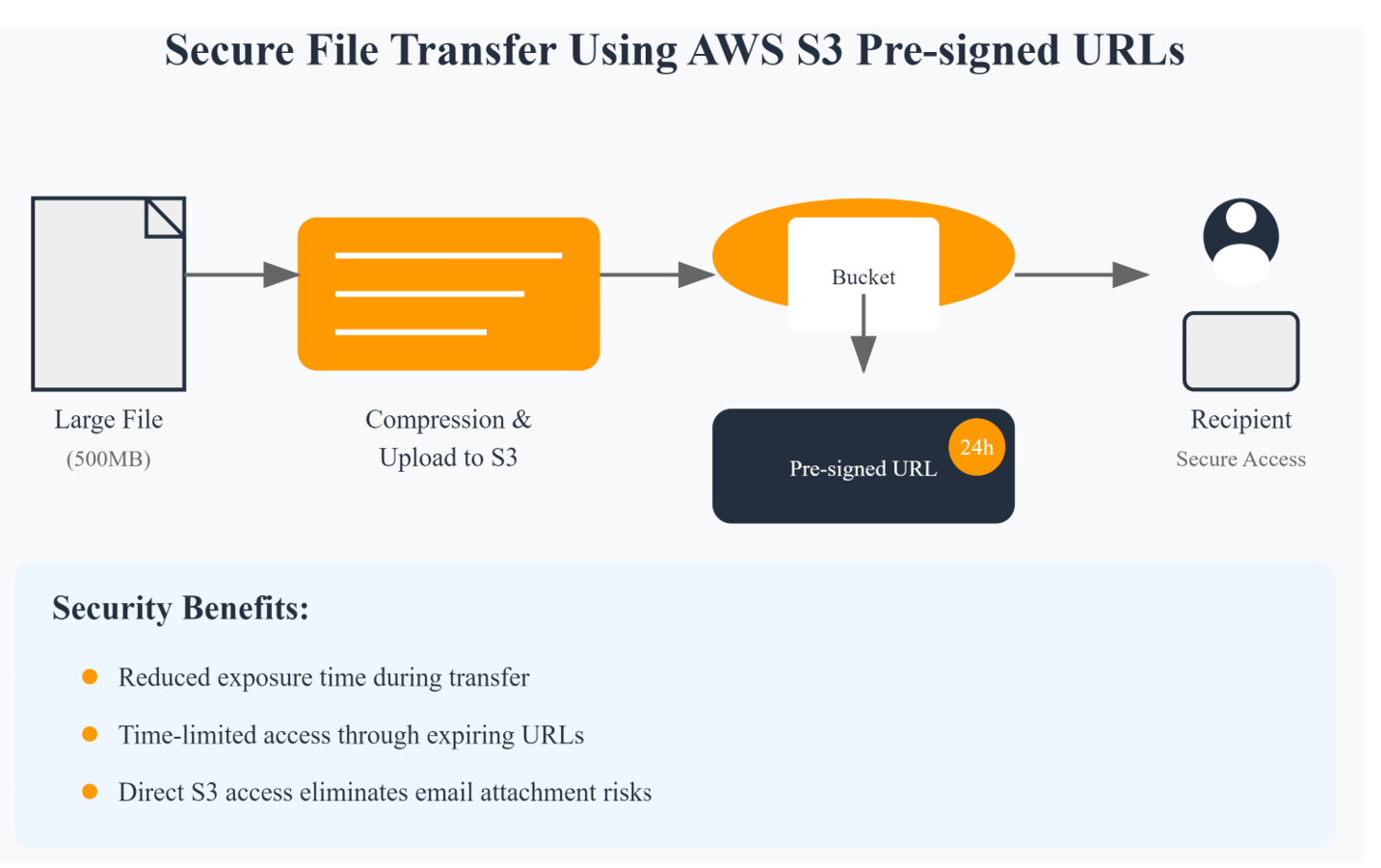
- Attachment-Free Sharing — Using S3-signed URLs in place of traditional file attachments minimizes email size, resulting in quicker email delivery and reduced strain on email servers. Also, this link is valid for a specific number of days and after that you will not be able to download files, adding an additional layer of security. Now even if emails with s3 signed URLs are intercepted while in transaction or are being forwarded by mistake then also recipients will not know the password to download the attachments. Since the actual password Is not shared in the email but only the pattern it would be only known to the authorized recipient who has the detail to fill in the pattern.
Conclusion
As cyber threats continue to evolve, healthcare organizations need to take proactive measures to protect sensitive information shared via email. By utilizing tools like PyMinizip for encryption and implementing comprehensive security protocols, organizations can significantly reduce the risk of email attachment fraud. Protecting PII and other sensitive data is not just a regulatory requirement; it is a critical responsibility to safeguard patients’ privacy and maintain trust in the healthcare system.
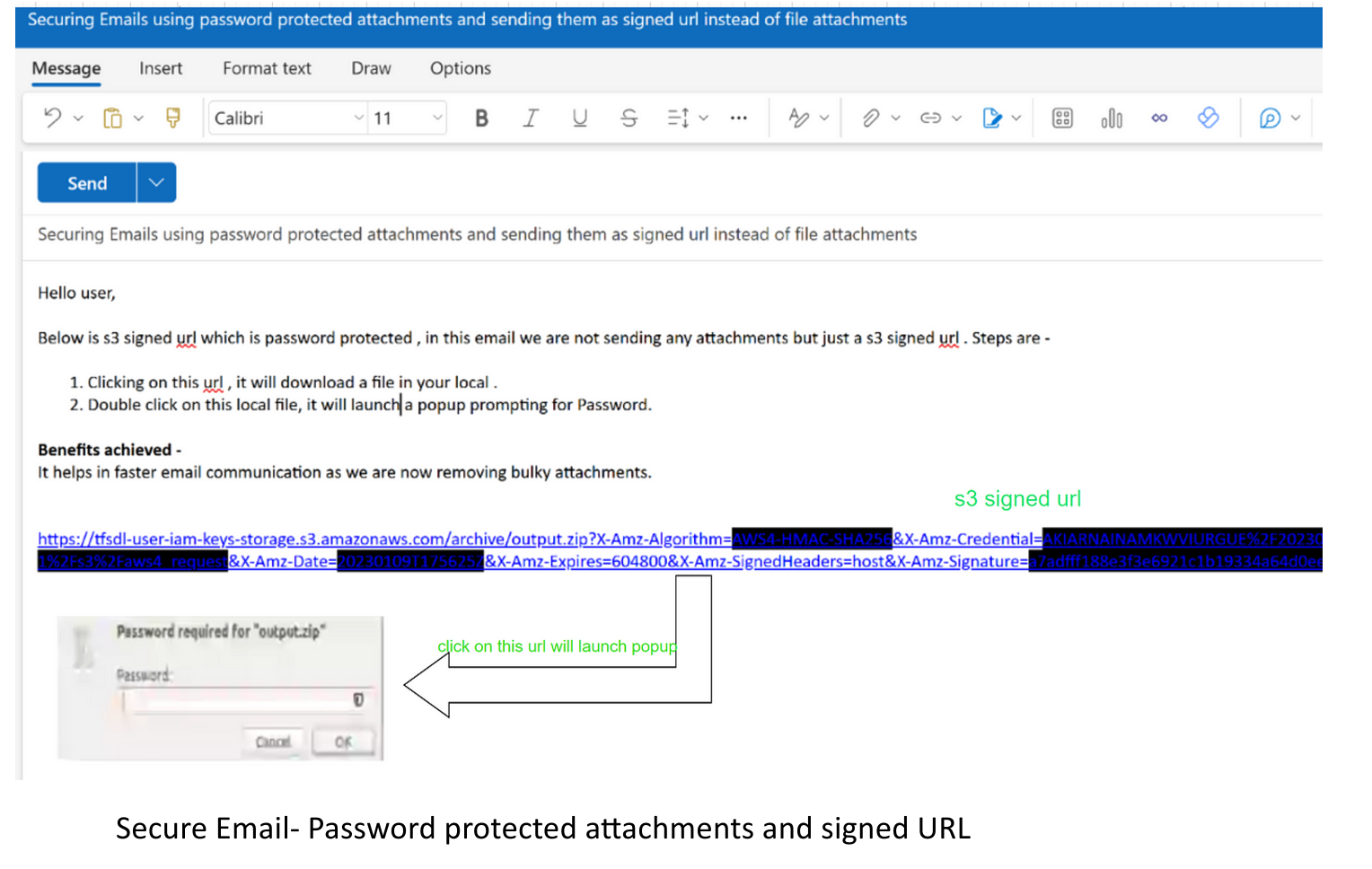
Post this technical implementation, emails received will not have any actual attachments as depicted in the below image. For attachments, a clickable URL will be shared which will download a folder only if the correct password is provided.