
2019-07-02 13:51:12 Author: pentestmag.com(查看原文) 阅读量:295 收藏

by Eliza May Austin
!= docker expert, just making the most of insomnia.
Examples ran on Ubuntu 16.04.6 and using Docker version 18.09.5
Basic Install:
sudo apt install docker.io
sudo systemctl start docker
sudo systemctl enable dockersudo apt install git -y
Install Benchmark Security:
git clone https://github.com/docker/docker-bench-security.git
From the benchmark directory run benchmark against your docker version
cd docker-bench-security/
sudo ./docker-bench-security.sh
The output should look something like the below:
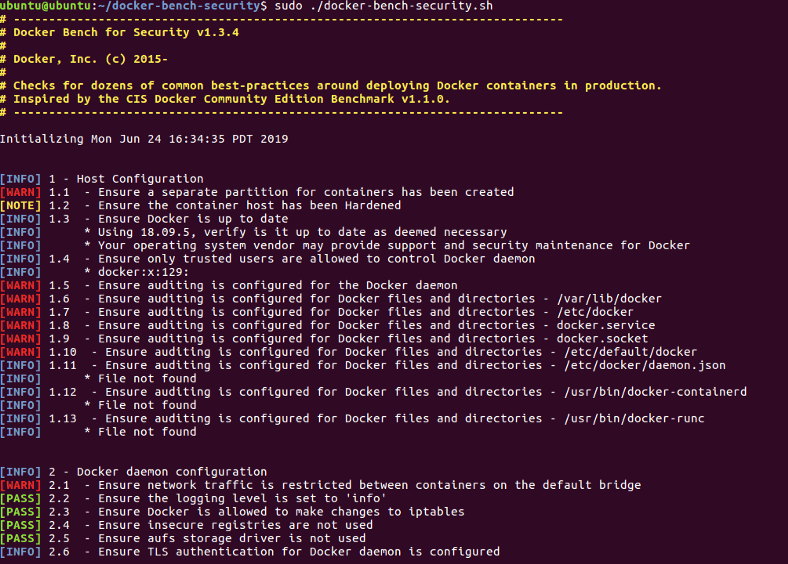
Note that “WARN” should be considered in the same way to critical vulnerabilities in any other vulnerability assessment tooling. Equally the “INFO” statements may be applicable dependent upon your environment, so do not ignore these.
It’s particularly important to secure the host that you are running docker on. To cut down the reams of output simply add the title in to the command you just ran to get more drilled down vulnerability information.
sudo ./docker-bench-security.sh -c host_configuration
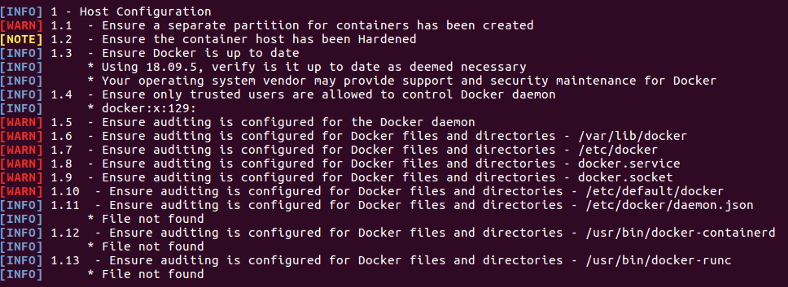
sudo apt install auditd -y
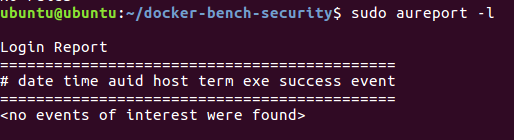
To check what rules you have set on your system already run the following command:
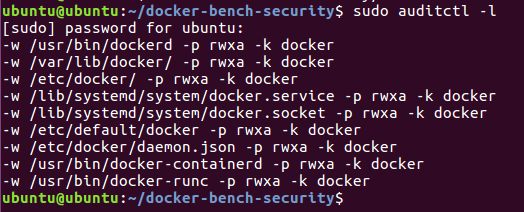
sudo auditctl -l
sudo aureport -l
Because we have not yet set any rules, we have no events. So the output should look like this
![]()
Lets set a quick rule, break the rule and witness the event report:
sudo auditctl -w /usr/bin/dockerd -k docker
This command is a general rule which is basically saying watch (-w) this path and file (/usr/bin/dockerd). In the event of a breach of this rule generate a uniq event ID (-k). Below we can rerun the auditctl utility and this shows our rule.
![]()
After running a few randomish commands to test the rule I could check the output with the following command:
sudo aureport -k
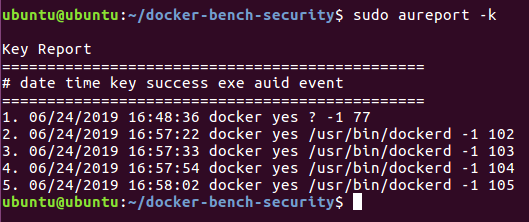
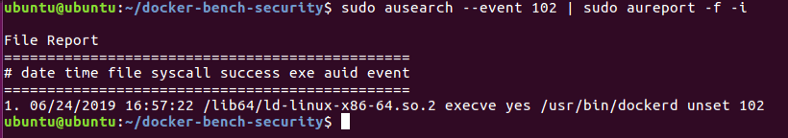
The number you see at the end of every event is its event ID.
To see information on the individual events run the following command:
sudo ausearch --event 102 | sudo aureport -f -i
Do the same for all of the following files by copying and pasting them in to /etc/audit/audit.rules:
/etc/docker | /etc/default/docker | /etc/docker/daemon.json| /var/lib/docker | docker.service | docker.socket | /usr/bin/dockerd | /usr/bin/docker-runc | /usr/bin/docker-containerd
These rules although applied in the right place and in working order are not static and will be removed upon a reboot, or a restarting of the audit daemon itself. Make the rules static.
sudo sh -c "auditctl -l >> /etc/audit/audit.rules"
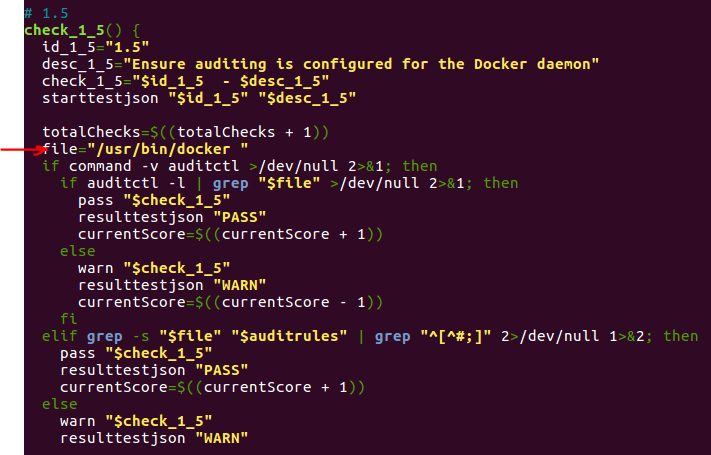
There is a strange issue with check 1.5, I have no idea why but simply adding in a letter ‘d’ in to the configuration file of bench-security sorts this out. See below:
nano tests/1_host_configuration.sh
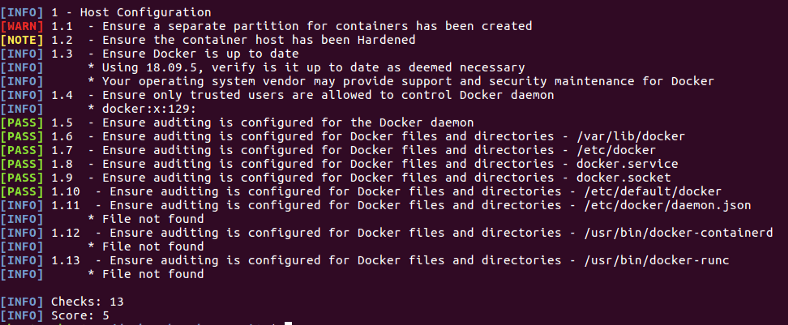
Re-run the Host configuration audit check and see the difference from the original audit.
sudo ./docker-bench-security.sh -c host_configuration
Docker security documentation: https://docs.docker.com/engine/security/security/
Benchmark documentation: https://github.com/docker/docker-bench-security
Play with docker tutorials: https://training.play-with-docker.com/alacart/
Can’t play with docker on your host machine? Play with docker in the browser: https://labs.play-with-docker.com/
About the Author
Eliza May Austin is the founder of LLHS (Ladies Of London Hacking Society), founder of TFTCyber (Tech For Troops Cyber), and BCS (British Computer Society) award winner in 2016.
The article has been originally published at: https://medium.com/@always0ddba1l/how-to-quickly-run-a-basic-security-audit-against-docker-secure-the-host-5e8bd907c12f
如有侵权请联系:admin#unsafe.sh