2024-12-11 15:11:27 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
When it comes to securing your customers’ data and earning their trust, there aren’t many things more important than SOC 2 compliance. But let’s face it, it’s not always that straightforward. Policies can feel like a maze of jargon and to-dos, but don’t worry – we’ve got your back.
Let’s dive into everything you need to know about SOC 2 policies, helping you understand what they should include, why they matter, and how to make them work for your business.
Understanding SOC 2 Compliance
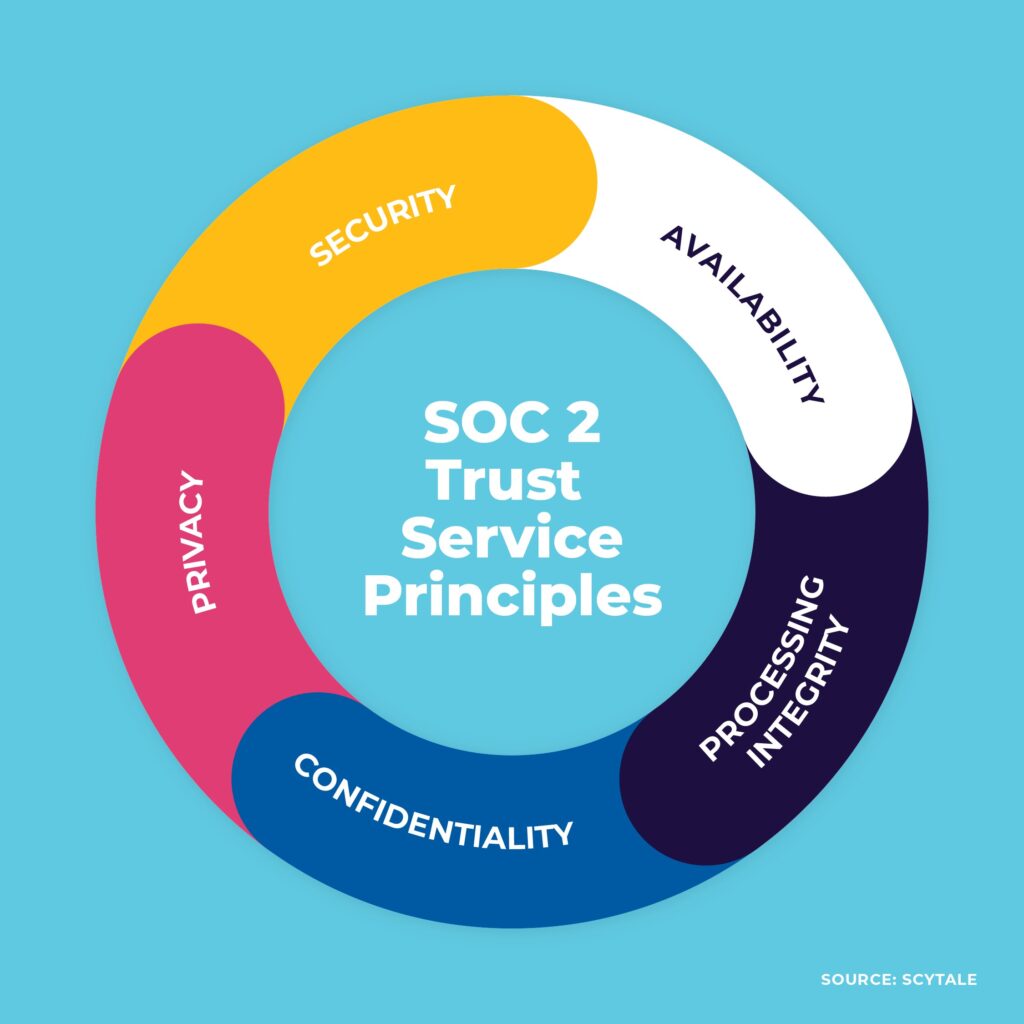
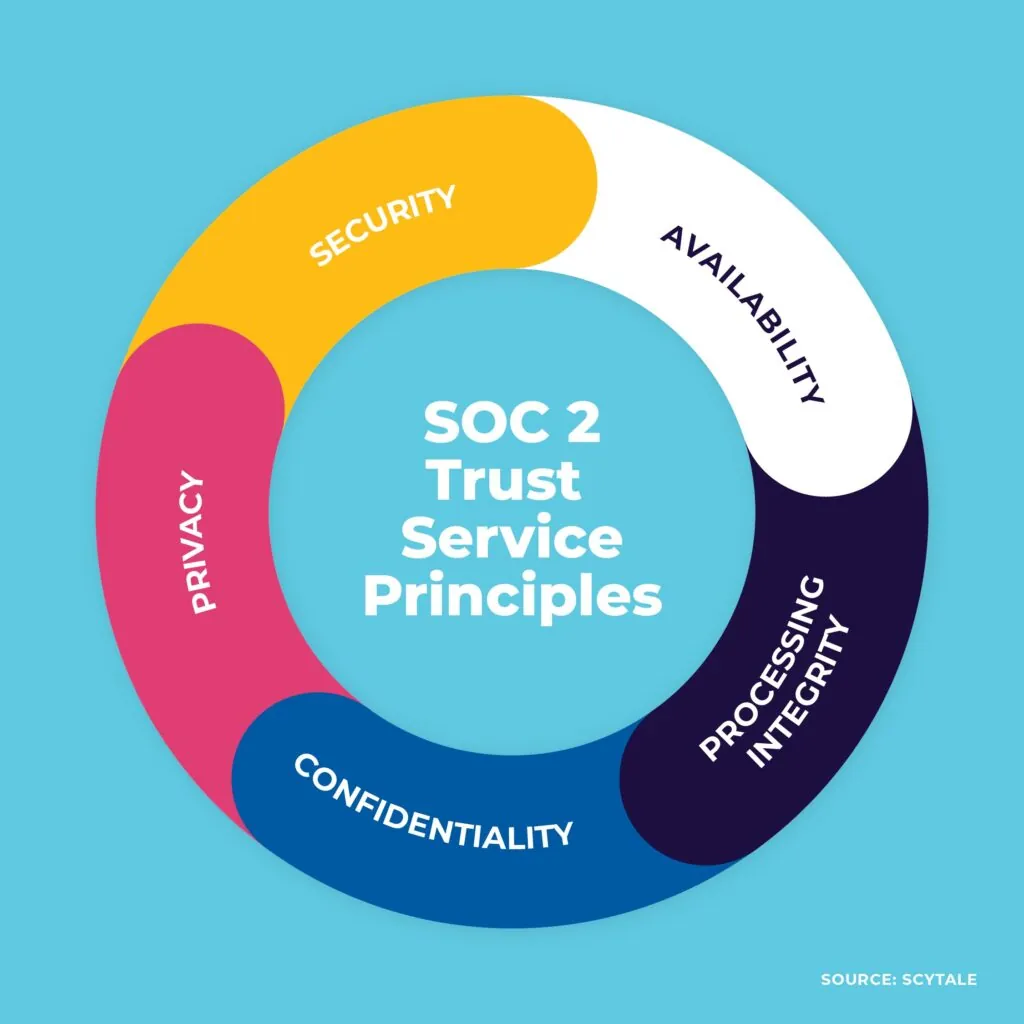
At its core, SOC 2 compliance is all about showing your customers that their data is safe with you. It’s built around five key Trust Service Principles: security, availability, processing integrity, confidentiality, and privacy. These principles shape how your organization manages and protects data.
But SOC 2 isn’t just about earning that shiny attestation report – it’s about working from the inside out to create systems and policies that reflect a true culture of security. Done right, SOC 2 compliance becomes an invaluable trust signal, helping you win big clients and stand out in a competitive SaaS market.
The Role of Policies in SOC 2 Compliance
Policies are the backbone of SOC 2 compliance, guiding your organization on protecting sensitive data and getting audit-ready. Without them, compliance is like building a house without blueprints. SOC 2 policies provide structure, ensuring your team knows exactly what’s expected and your organization has a clear path to follow in any scenario.
These policies form the basis of your SOC 2 control list, which auditors review to confirm you’re meeting requirements. Beyond compliance, strong SOC 2 policies demonstrate your commitment to security, helping you build trust with customers, partners, and stakeholders while also achieving a significant competitive edge.
Key Components of SOC 2 Policies
SOC 2 policies are your “rules of the road” for handling data responsibly, ensuring your operations align with the relevant Trust Services Criteria (TSC) while keeping your business secure and your customers happy. The exact scope of your policies will depend on your organization’s size, the nature of your services, and the chosen TSC, but some components are essential for every business. By covering these areas, your list of IT policies and procedures will help ensure compliance and strengthen your systems.
Security Controls
Security controls are like bouncers at your digital nightclub. Their job? Keeping shady characters out. These controls include everything from encryption (locking your data with strong digital keys) to multi-factor authentication (because one password just isn’t enough). Regularly updating your SOC 2 security controls list helps prevent unauthorized access and ensures data integrity, making sure you’re always one step ahead of malicious actors.
Access Management
Who’s allowed backstage? Access management is all about making sure the right people have access to the right stuff – and only the right stuff. Policies must define role-based access, ensuring individuals only have permissions relevant to their responsibilities. It’s like giving your team VIP passes but keeping the cleaning crew out of the sound booth. Beyond defining roles, access management involves regularly reviewing access to sensitive data, revoking it as needed, and applying just-in-time and zero-trust principles for enhanced security.
Data Management
Handling data responsibly is non-negotiable. Policies should cover the entire data lifecycle – collection, storage, processing, and disposal. Think of it as handling something fragile: encrypt it (bubble wrap for data), store it safely (a locked vault), and dispose of it safely to minimize exposure risks (shred the hard drive).
Incident Response
When disaster strikes (and it might), you don’t want to be scrambling. Your incident response plan should outline what to do if something goes wrong, detailing steps for identifying, reporting, containing, and mitigating security incidents. It should also define roles to ensure a swift response. Practice makes perfect, so regularly conducting incident response drills and post-incident reviews will improve your organization’s readiness and resilience, ensuring your team knows exactly what to do when it’s go-time.
Change Management
Change is inevitable, but chaos isn’t. Although system and process changes pose inherent risks – from introducing vulnerabilities to disrupting workflows – having a solid change management policy in place minimizes these risks and ensures that when you update systems or processes, it’s done carefully and doesn’t break everything. Test new changes first, get them approved, document them thoroughly, and always have a backup plan to ensure continuity of operations just in case things go sideways.
GET SOC 2 COMPLIANT 90% FASTER
List of SOC 2 Policies
Here’s a list of 21 SOC 2 policies that auditors generally look for:
- Acceptable Use Policy: Rules for using company tech responsibly, covering devices, systems, and passwords.
- Access Control Policy: Defines who gets access to what and ensures regular reviews.
- Business Continuity Policy: Outlines plans to keep operations running during disruptions.
- Change Management Policy: Ensures updates and changes are approved, documented, and controlled.
- Confidentiality Policy: Guides handling of sensitive data.
- Code of Conduct Policy: Sets expectations for professional and respectful employee behavior.
- Data Classification Policy: Defines how to handle data based on its sensitivity and risk level.
- Disaster Recovery Policy: Details how to recover systems and data after a disaster.
- Email/Communication Policy: Outlines acceptable use of company communication tools.
- Encryption Policy: Specifies what data must be encrypted and how.
- Incident Response Policy: Lays out roles and actions for handling security breaches.
- Information Security Policy: Defines the organization’s approach to securing information.
- Backup Policy: Ensures regular data backups and quick recovery if needed.
- Logging and Monitoring Policy: Specifies what activities are tracked and how they’re monitored.
- Physical Security Policy: Covers securing physical spaces, like offices and servers.
- Password Policy: Sets rules for strong passwords, password managers, and regular updates.
- Remote Access Policy: Secures and monitors off-site connections for remote work.
- Risk Assessment and Mitigation Policy: Identifies risks and plans for avoiding or addressing them.
- Software Development Lifecycle (SDLC) Policy: Ensures secure coding, testing, and compliance in software development.
- Vendor Management Policy: Manages third-party risks to protect the business.
- Workstation Security Policy: Secures employee devices to prevent unauthorized access or data loss.
Developing and Implementing Effective SOC 2 Policies
Creating and rolling out SOC 2 policies might sound like a massive undertaking, but with the right approach, it’s totally manageable. Here’s your step-by-step guide to creating effective policies and putting them into practice:
1. Start with SOC 2 Policy Templates
Why reinvent the wheel? SOC 2 policy templates are like the cheat codes for compliance – they give you a structured starting point that you can tweak to fit your business.
2. Customize Them for Your Business
Every business is unique, so make sure your policies reflect your specific operations, risks, and systems. Generic policies won’t cut it when auditors start digging into your SOC 2 documentation.
3. Collaborate Across Teams
SOC 2 compliance isn’t just the IT department’s pet project. Involve stakeholders from HR to legal into the mix. Their insights ensure your policies are thorough and cover all the bases. Plus, teamwork makes the dream work!
4. Keep It Simple and Clear
Nobody likes trying to make sense of overly complicated technical jargon. Write policies that your entire team can understand and follow. Using clear, actionable language is essential for turning big ideas into practical daily habits.
5. Train Your Team
Your policies are only as strong as the people who follow them. Regular training sessions ensure everyone understands their role in maintaining SOC 2 compliance. Plus, it’s a great chance to answer questions and reinforce your security-first company culture.
6. Automate Where You Can
Compliance can get complicated fast, but tools like Scytale’s compliance automation platform make life so much easier. From implementing policies with auditor-approved policy templates to monitoring them in real time, automation helps you stay on top of things without the headache.
7. Review and Refresh
Just as SOC 2 compliance isn’t static, policies aren’t a “set it and forget it” deal. As your business grows and threats evolve, your policies need to adapt. Regular reviews ensure your procedures remain relevant and effective.
Taking the Stress Out of SOC 2 Compliance
SOC 2 compliance might seem complex, but with the right tools, policies, and team, it’s entirely manageable. Building and implementing strong SOC 2 policies ensures long-term security, success, and streamlined operations.
Ready to tackle SOC 2 compliance without losing sleep? Scytale makes the process easy with its compliance automation platform and a team of experts who know SOC 2 inside and out. From automating evidence collection to offering customized SOC 2 policy templates, Scytale helps you protect sensitive data, prove compliance, and simplify SOC 2 – whether you’re starting out or refining your approach.
The post SOC 2 Policies: What They Should Include and Why They Matter appeared first on Scytale.
*** This is a Security Bloggers Network syndicated blog from Blog | Scytale authored by Kyle Morris, Senior Compliance Success Manager, Scytale. Read the original post at: https://scytale.ai/resources/soc-2-policies/
如有侵权请联系:admin#unsafe.sh