2024-12-13 04:30:0 Author: securityboulevard.com(查看原文) 阅读量:14 收藏
Over the past several years, US Federal Agencies and private sector companies have observed China-based threat actors targeting network and telecommunication critical infrastructure. A wave of recent reports have disclosed that these attacks have succeeded in compromising government and industry targets to a far greater extent than previously thought. As a result, CISA has issued new guidance for telecommunications companies to secure their infrastructure, and the U.S. Federal Communications Commission (FCC) has drafted new, stricter cybersecurity regulations to require telcos to “secure their networks against unlawful access and interception.”
The threat activity by these groups goes back at least half a decade. As far back as 2020 the following threat actor groups, including Salt Typhoon, have been observed, with solid evidence of operations based in China that are state-sponsored:

Salt Typhoon
Leveraging malware such as GhostSpider, SnappyBee, and Masol RAT

Flax Typhoon
Responsible for the Raptor Train Botnet
Personal Panda leveraging malware such as Winnti-T, Asnarok, and Pygmy Goat
These campaigns have leveraged a wide variety of vulnerabilities and sophisticated tools, including 0-day vulnerabilities. The TTPs (Tactics, Techniques, and Procedures) have also leveraged commodity tools (such as Mirai botnet code) as well as more sophisticated malware with capabilities such as firmware backdoors and UEFI implants.
Known Exploited Vulnerabilities in the Network Device Supply Chain
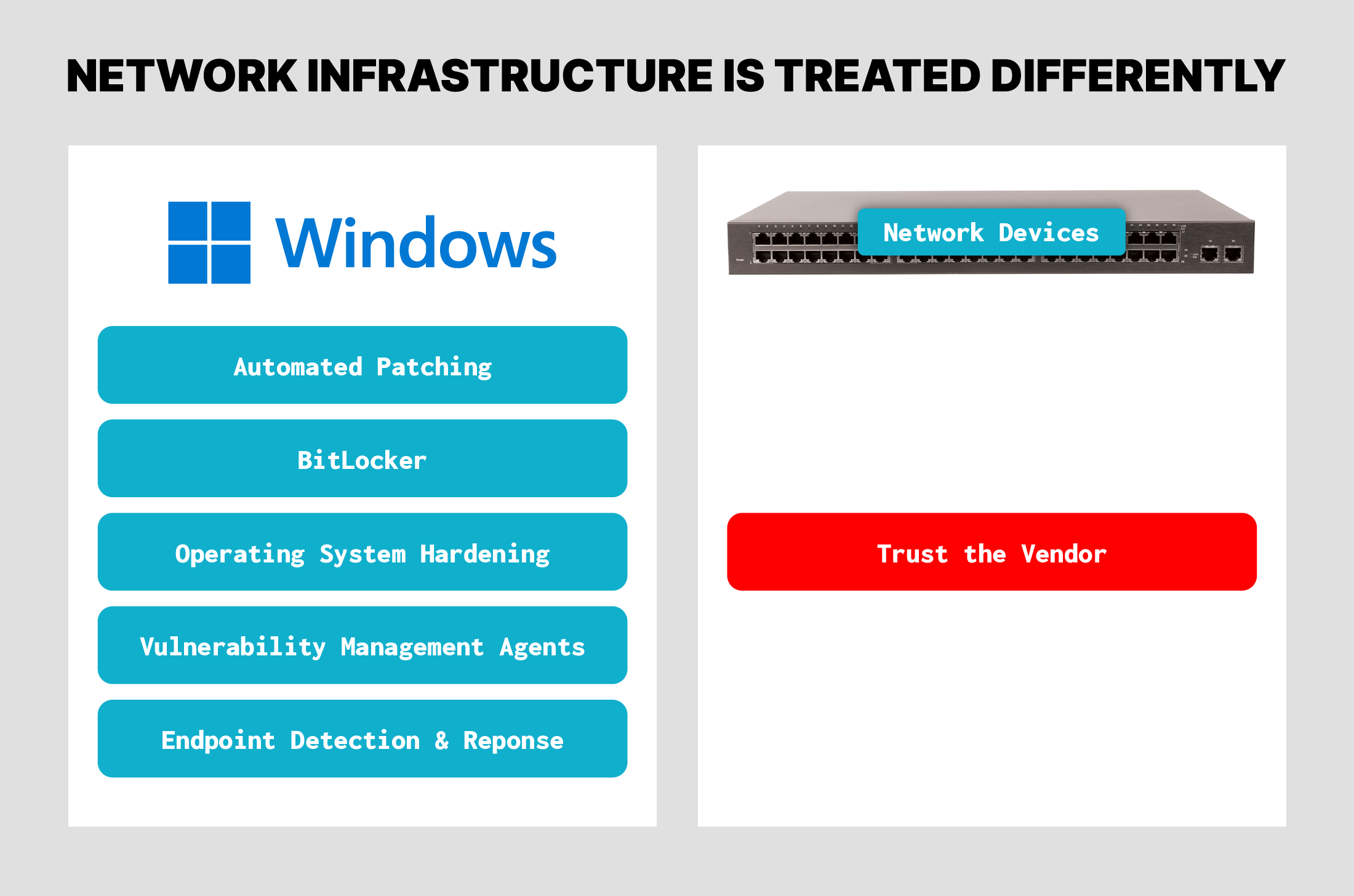
A key element of this unfolding story is that most of the CVEs exploited by these attackers are listed in CISA’s Known Exploited Vulnerabilities catalog, and some were also listed in the top 42 most routinely exploited vulnerabilities of 2023, also published by CISA. Furthermore, many of the vulnerabilities exist inside network devices, and even security devices that the targeted organizations purchase from vendors they trust to provide secure equipment. The supply chain of network infrastructure devices is far less secure than it should be.
End user workstations and endpoints are subjected to a huge battery of cybersecurity requirements, tests, scans, and regulations. In contrast, network devices like routers, switches, and even firewalls from vendors like Cisco, Sophos, Palo Alto, and more are assumed to be secure. The Salt Typhoon attacks and other PRC-sponsored adversaries show that security teams must update their assumptions and treat network devices as insecure until proven otherwise. Verifying the integrity of these devices before connecting them to critical infrastructure networks, and monitoring them continuously for updates, especially in firmware, is a crucial step in protecting critical telecommunications infrastructure against advanced adversaries.
Salt Typhoon, Flax Typhoon, and More APT Tactics Detected by Eclypsium
The Eclypsium team has been tracking this activity and developing detections for vulnerabilities and IoCs (Indicators of Compromise) across several platforms. We are constantly adding new detections to assure our customers get broad coverage of the TTPs used by these threat groups. Below is a sampling of CVEs related to Salt Typhoon, Flax Typhoon, Pacific Rim, Velvet Ant, and other Chinese APTs that can be detected by the Eclypsium platform.
This list is continuously growing as new detections are added to the Eclypsium platform. Eclypsium customers can contact their account representative for the most up-to-date list of vulnerabilities and IOCs detected by Eclypsium.
| CVE Identifier | Vulnerability Description | Associated Threat Groups & Campaigns |
|---|---|---|
| CVE-2019-11510 | Pulse Connect Secure VPN vulnerability | Sodinokibi |
| CVE-2019-19781 | Citrix ADC and Gateway vulnerability | Sodinokibi/REvil |
| CVE-2024-20399 | Cisco NX-OS vulnerability | Velvet Ant |
| CVE-2022-1388 | F5 BIG-IP vulnerability | Flax Typhoon, Velvet Ant |
| CVE-2021-1497 | Cisco HyperFlex HX vulnerability | Chinese state-sponsored actors |
| CVE-2020-12271 | Sophos XG Firewall vulnerability | Pacific Rim |
| CVE-2020-15069 | Sophos Firewall vulnerability | Pacific Rim |
| CVE-2020-29574 | Sophos Firewall vulnerability | Pacific Rim |
| CVE-2022-1040 | Sophos Firewall vulnerability | Pacific Rim |
| CVE-2022-3236 | Sophos Firewall vulnerability | Salt Typhoon, Pacific Rim |
| CVE-2023-46805 | Ivanti Connect Secure VPN vulnerability | Salt Typhoon, Volt Typhoon |
| CVE-2024-21887 | Ivanti Connect Secure VPN vulnerability | Salt Typhoon, Volt Typhoon |
| CVE-2024-21888 | Ivanti Connect Secure VPN vulnerability | Volt Typhoon |
| CVE-2024-21893 | Ivanti Connect Secure VPN vulnerability | Volt Typhoon |
| CVE-2022-42475 | FortiOS SSL-VPN vulnerability | Volt Typhoon |
| CVE-2021-44228 | Log4j | Flax Typhoon |
| CVE-2023-3519 | Citrix Netscaler – Unauthenticated Remote Code Execution (RCE) vulnerability | Flax Typhoon |
| No CVE | Raptor Train Botnet | Flax Typhoon |
Detecting Vulnerabilities is Only The Beginning
Detecting vulnerabilities is important, but preventing and protecting against attacker persistence and future intrusion is also critical. Eclypsium is able to verify the integrity of hardware, software, and firmware components in user endpoints and network devices. This reduces the necessity of trusting vendors, and enables telecommunications organizations to verify that their supply chain of network devices and software is not introducing new vulnerabilities into the environment that are subsequently targeted by adversaries. If you’re interested in getting a demonstration of how we can help you mitigate your risk from these APT tactics, please get in touch with us.
Further Reading
- Digital Supply Chain Security
- The Rise of Chinese APT Campaigns: Volt Typhoon, Salt Typhoon, Flax Typhoon, and Velvet Ant
- CISA: Over Half of Top Routinely Exploited Vulnerabilities in 2023 Affected Network Devices and Infrastructure
- Infographic: A History of Network Device Threats and What Lies Ahead
The post Holding Back Salt Typhoon + Other Chinese APT CVEs appeared first on Eclypsium | Supply Chain Security for the Modern Enterprise.
*** This is a Security Bloggers Network syndicated blog from Eclypsium | Supply Chain Security for the Modern Enterprise authored by Chris Garland. Read the original post at: https://eclypsium.com/blog/salt-typhoon/
如有侵权请联系:admin#unsafe.sh