
2020-09-03 14:56:32 Author: blog.elcomsoft.com(查看原文) 阅读量:188 收藏
Last year, we have developed an innovative way to extract iPhone data without a jailbreak. The method’s numerous advantages were outweighed with a major drawback: an Apple ID enrolled in the paid Apple’s Developer program was required to sign the extraction binary. This is no longer an issue on Mac computers with the improved sideloading technique.
What’s this all about
When extracting an iOS device (pulling the file system and decrypting the keychain), one needs low-level access to the device. Traditionally, we’ve been using public jailbreaks for privilege escalation, yet recently we switched to a new method that does not require a jailbreak. Jailbreak-free extraction utilizes an Elcomsoft-developed extraction agent. Agent-based extraction provides tangible benefits over the traditional extraction method based on jailbreaking the device, being a safer, faster, and more robust alternative. Until today, agent-based extraction had a major drawback: in order to have the extraction binary signed, it required an Apple account registered in the Apple Developer program. We’ve circumvented this restriction in the latest release of iOS Forensic Toolkit for Mac. Users of the Windows edition still need the Developer account to perform the extraction.
A bit of history
Apple has a tight grip on the iOS ecosystem. In Apple dreams, everyone must pay for accessing the app ecosystem. Developers must purchase Apple hardware and Apple development tools; they must also purchase membership in the paid Apple Developer program. There is a separate recurring fee for publishing apps in the App Store, but even that fee does not guarantee the acceptance.
Users who wanted to install a non-approved app from a channel other than the official App Store had several choices. They could jailbreak the device and use one of the alternative app stores. They could pay Apple for the privilege by registering as a Developer. Finally, they could install a limited number of apps to their device and keep them for as long as 7 days without paying a dime. This process is called “sideloading”, and this is the same process that was used by forensic experts to install extraction software for imaging devices.
Historically, iOS users and forensic experts had been able to sideload third-party apps by using an ordinary, often throwaway Apple ID for signing the binaries. Cydia Impactor is a free tool often used for the purpose, but alternatives also exist. In November 2019, Apple made an abrupt change to their provisioning service, effectively blocking the sideloading mechanism for all but the users of a paid Apple Developer accounts. Saurik, the developer of Cydia Impactor, twitted about the issue. Since then, nothing but a paid Apple Developer account could be used to sign the binaries. Officially, this is still the case today. Unofficially, around the same time last year many users started having problems registering a personal Apple Developer account.
Developer or throwaway Apple ID for iPhone extraction?
A subscription to become a registered developer is affordable; it’s a tiny fraction of the cost of tools one needs to extract the iPhone. Using a developer account for sideloading the extraction software has tangible benefits over using a regular or anonymous (throwaway) Apple ID. We created a blog article explaining the benefits of the developer account compared to a throwaway Apple ID for the purpose of iOS extraction. In a word, utilizing an Apple account registered in the Developer program allows signing and sideloading apps, and bypassing the on-device certificate verification, which would otherwise require an Internet connection on the device with all the risks of exposing the device to remote lock/erase.
However, a large number of experts working for the law enforcement were and remain hesitant to obtain such accounts for various non-financial reasons. Registering for a personal Developer Account with Apple had become particularly challenging in the recent months, with Apple rejecting numerous applications with no explanation and no resolution through their support service. If you are seeing the “Your enrollment could not be completed” message, check out this thread for suggestions.
As a result, we’ve felt the urge to develop a working solution allowing experts to use regular or anonymous (throwaway) Apple IDs for signing the extraction software and performing the imaging.
Our work
We have discovered a way to enable the use of regular and disposable Apple ID’s for the purpose of agent-based data extraction. All you need is the latest build of iOS Forensic Toolkit, a Mac computer, and a cable to connect the iPhone to the Mac. In this guide, we’ll demonstrate how to image an iOS device with a disposable Apple ID.
Compatibility, pre-requisites and restrictions
In order to launch the attack, you will need all of the following.
- A compatible iPhone model running a supported version of iOS. The list of supported devices is available below. At this time, agent-based extraction is supported for all models ranging from the iPhone 5s through 11 Pro Max with iOS 9.0 through 13.5.
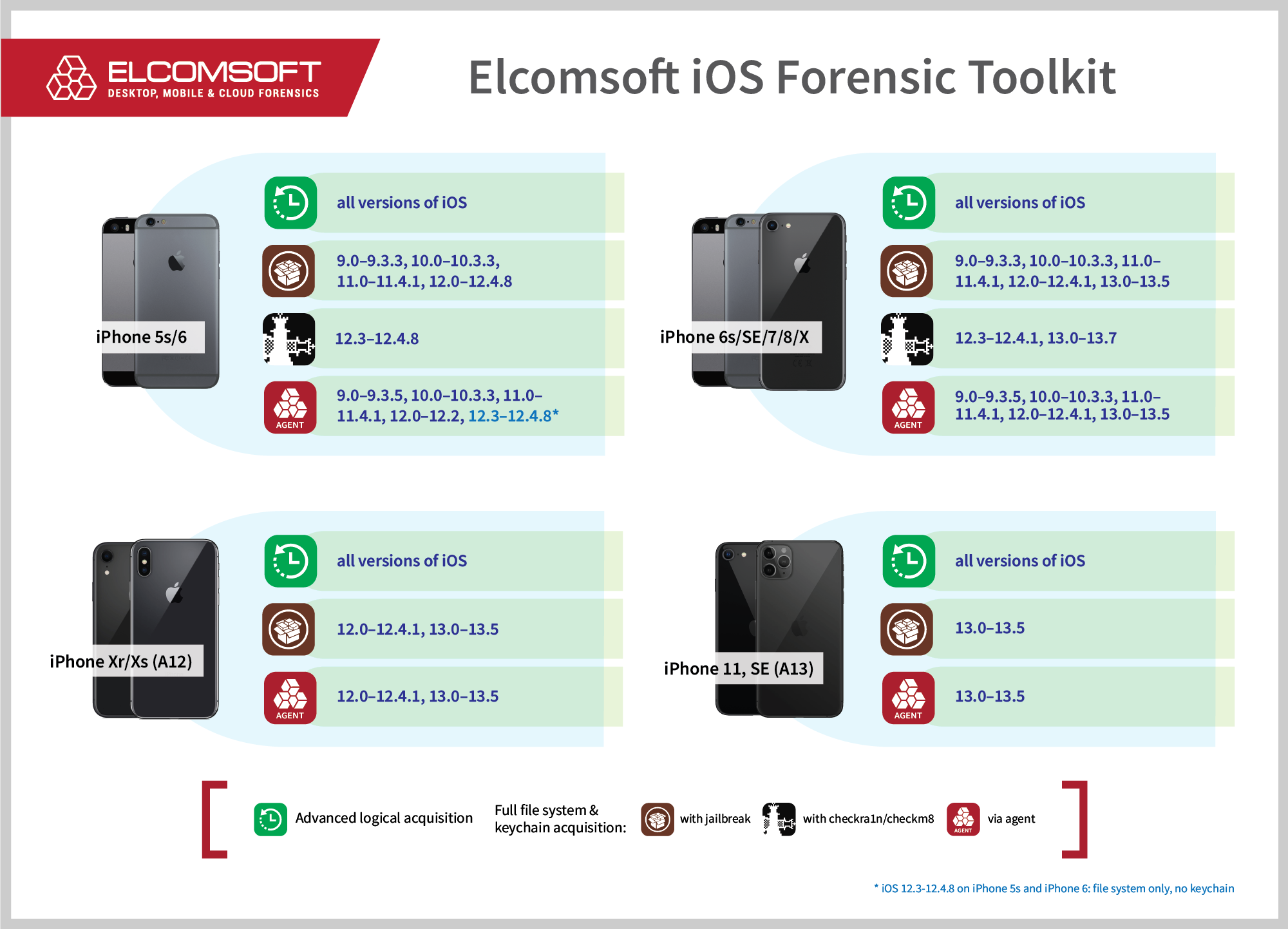
- A desktop or laptop computer with macOS 10.12 (Sierra) through 10.15 (Catalina).
- A Lightning cable.
- Apple ID (personal or disposable) with or without two-factor authentication.
- iOS Forensic Toolkit 6.50 or newer.
Compared to using a Developer account, signing the extraction agent with a regular or throwaway Apple ID has the following restrictions.
- The signing certificate is only valid for 7 days. This is normally not an issue as extractions should performed on the same day as sideloading the agent.
- A non-developer Apple ID can be only used to sign a handful of devices (it was 3 devices when we last checked). This is why many experts prefer creating throwaway Apple IDs for device extractions.
- You will need to pass two-factor authentication when signing in. The 2FA code will be pushed onto a trusted device (no SMS delivery), so you’ll need to have one ready. Note that you will not be prompted for the code if the Mac is already trusted (e.g. it is tied to the Apple ID you are about to use). We have not tested the tool with non-2FA accounts.
- You will need to approve (Trust) the signing certificate on the iOS device. This is only possible when the device is connected to the Internet, so you’ll have to break the “Airplane mode only” rule to avoid the possible remote lock or erase command.
Steps to extract
Important: if you are performing a forensic extraction (as opposed to extracting your own iPhone), set up a restricted Internet connection first, as described in the following article: Setting Up Restricted Internet Connection.
We strongly recommend extracting both the keychain and the file system as the content of the keychain could be used to decrypt certain app data (e.g. WhatsApp cloud backups, Signal and so on). The file system image can be analyzed in in Elcomsoft Phone Viewer or another forensic product.
Conclusion
Since November last year sideloading apps onto iOS devices had become more challenging. Apple made changes to its provisioning service, effectively breaking sideloading for all but the users of a paid Apple Developer account. We have discovered a way to enable the use of regular and disposable Apple ID’s for the purpose of agent-based data extraction. All you need is the latest build of iOS Forensic Toolkit, a Mac computer, and a cable to connect the iPhone to the Mac. In this guide, we’ll demonstrate how to image an iOS device with a disposable Apple ID.
iOS Forensic Toolkit for Mac circumvents the provisioning restriction that obliges users to use an Apple Developer account for imaging iOS devices. The Mac edition once again allows experts to use regular or throwaway Apple IDs for extracting the file system and decrypting the keychain from compatible iPhone and iPad devices. However, if one already has an Apple Developer account, we recommend continuing using that account to sideload the extraction binary due to the tangible benefits of this approach.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh