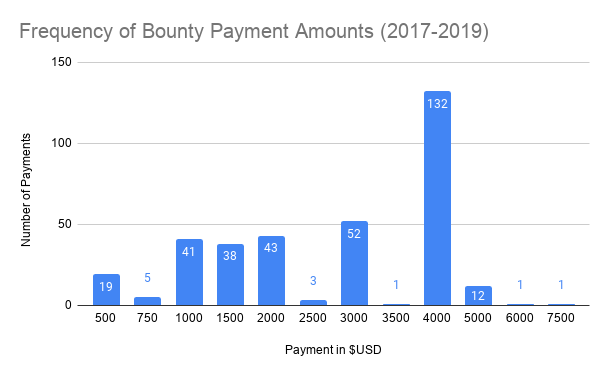
Firefox has one of the oldest security bug bounties on the internet, dating back to 2004. From 2017-2019, we paid out $965,750 to researchers across 348 bugs, making the average payout $2,775 – but as you can see in the graph below, our most common payout was actually $4,000!
After adding a new static analysis bounty late last year, we’re excited to further expand our bounty program in the coming year, as well as provide an on-ramp for more participants. We’re updating our bug bounty policy and payouts to make it more appealing to researchers and reflect the more hardened security stance we adopted after moving to a multi-process, sandboxed architecture. Additionally, we’ll be publishing more posts about how to get started testing Firefox – which is something we began by talking about the HTML Sanitization we rely on to prevent UXSS . By following the instructions there you can immediately start trying to bypass our sanitizer using your existing Firefox installation in less than a minute.
Firstly, we’re amending our current policy to be more friendly and allowing duplicate submissions. Presently, we have a ‘first reporter wins’ policy, which can be very frustrating if you are fuzzing our Nightly builds (which we encourage you to do!) and you find and report a bug mere hours after another reporter. From now on, we will split the bounty between all duplicates submitted within 72 hours of the first report; with prorated amounts for higher quality reports. We hope this will encourage more people to fuzz our Nightly ASAN builds.
Besides rewarding duplicate submissions, we’re clarifying our payout criteria and raising the payouts for higher impact bugs. Now, sandbox escapes and related bugs will be eligible for a baseline $8,000, with a high quality report up to $10,000. Additionally, proxy bypass bugs are eligible for a baseline of $3,000, with a high quality report up to $5,000. And most submissions are above baseline: previously the typical range for high impact bugs was $3,000 – $5,000 but as you can see in the graphic above, the most common payout for those bugs was actually $4,000! You can find full details of the criteria and amounts on our Client Bug Bounty page.
Again, we want to emphasize – if it wasn’t already – that a bounty amount is not determined based on your initial submission, but rather on the outcome of the discussion with developers. So improving test cases post-submission, figuring out if an engineer’s speculation is founded or not, or other assistance that helps resolve the issue will increase your bounty payout.
And if you’re inclined, you are able to donate your bounty to charity – if you wish to do so and have payment info on file, please indicate this in new bugs you file and we will contact you.
Lastly, we would like to let you know that we have cross-posted this to our new Attack & Defense blog. This new blog is a vehicle for tailored content specifically for engineers, security researchers, and Firefox bug bounty participants. We’ll be highlighting improvements to the bug bounty program (which will often be posted to this Security blog also) – but also posting guides on how to test different parts of Firefox. You can follow us via RSS or Twitter, where we’ll be boosting tweets relevant to browser security: exploitation walkthroughs, conference talks, and the like.