This post is a follow-up on a previous article: we have updated the Androsig plugin and the pre-generated set of library signatures.
Reminder: Androsig is a JEB plugin used to sign and match library code for Android applications.
The purpose of the plugin is to help deobfuscate lightly-obfuscated applications that perform name mangling and hierarchy flattening (such as Proguard and other common Java and Dalvik protectors). Using our collection of signatures for common libraries, library code can be recognized; methods and classes can be renamed; package hierarchies can be rebuilt.
Examples
Below, an example of what that looks like on a test app:
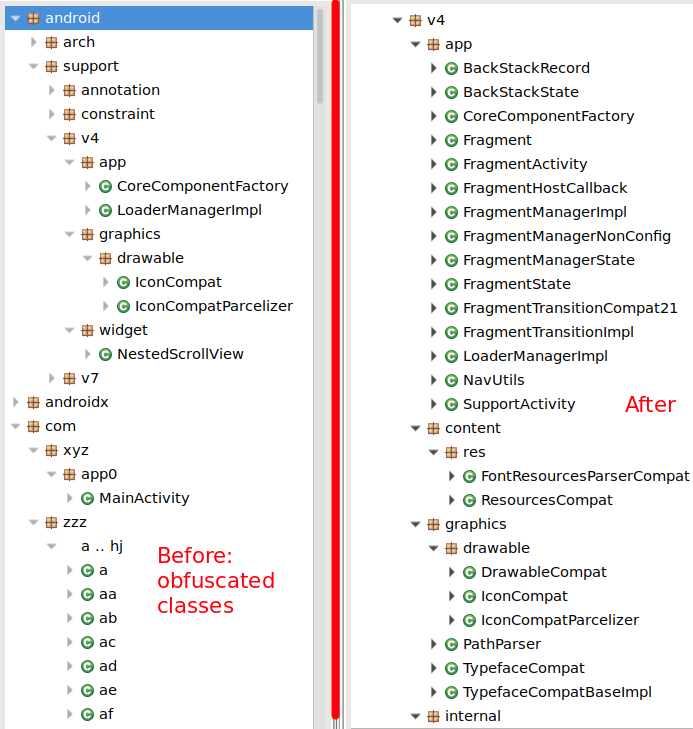
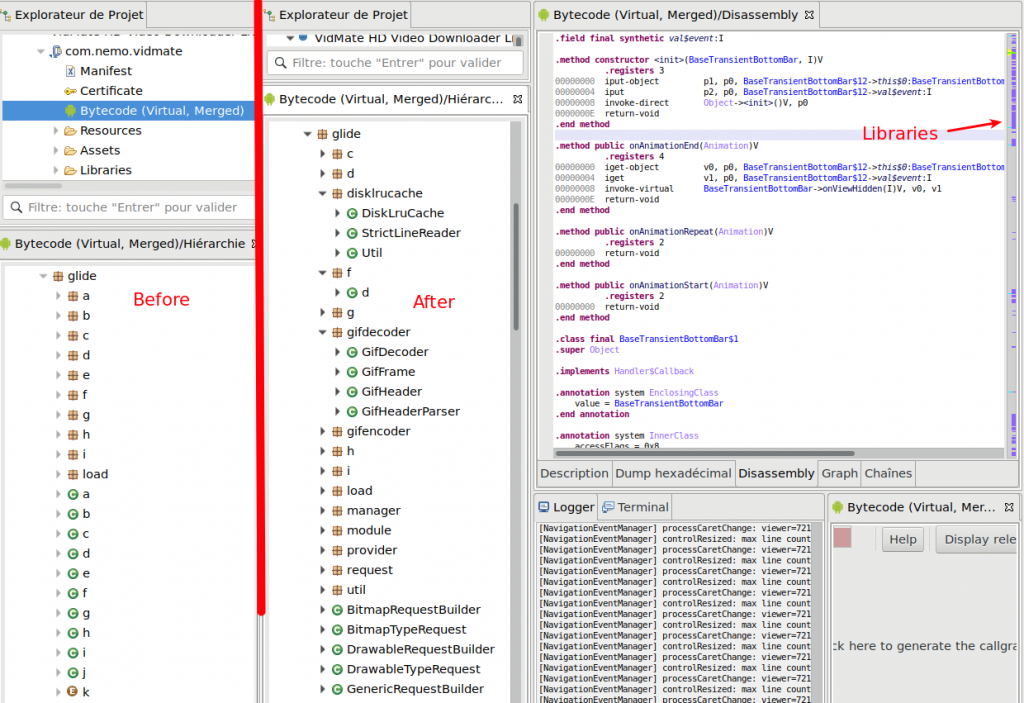
Another example: running Androsig on a large app (Vidmate 4.0809), see the reconstructed glide/… sub-packages below:
Installation
1) Download the latest version of the compiled binary plugin and drop it into the JEB coreplugins/ folder. If you are running JEB 3.4+, the plugin should come bundled with your .
Link: JebAndroidSigPlugin-1.1.x.jar
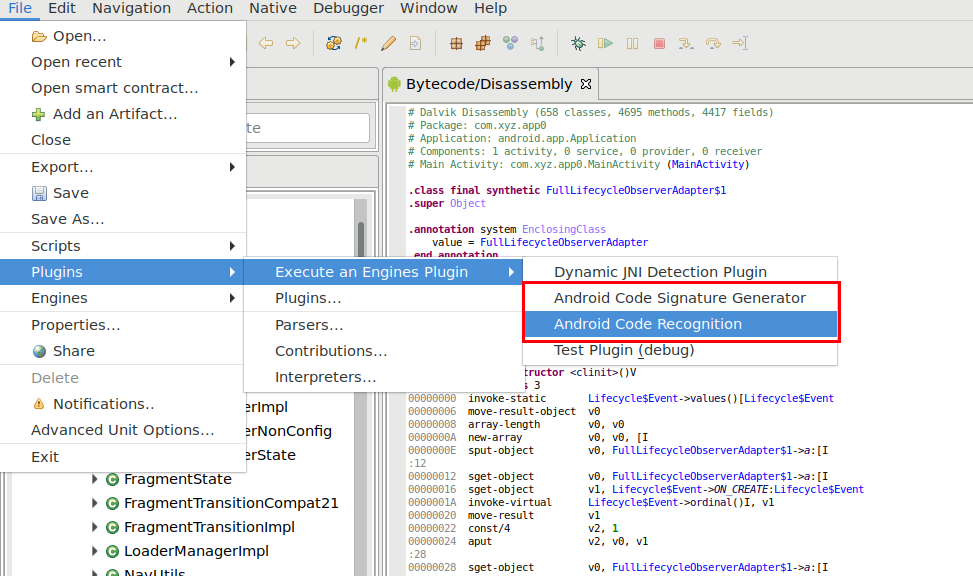
This single JAR offers two plugin entry-points, as can be seen in the picture below:
2) Then download and extract the latest signatures package to your [JEB]/coreplugins/android_sigs/ folder.
Link: androsig_1.1_db_20190515.zip
The user interface was unchanged so you can refer to previous article for matching, generating, results and parameters.
